prototypeandInventory- 2015 top ten trends in information technology(库存- 2015年十大信息技术的趋势)
Inventory:2015 top ten trends ininformation technology
(Research papers Download news)market researchfirm Gartner IT experts predicted the top ten informationtechnology trends in 2015, and these trends areconsidered to have a significant impact on the industryover the next three years,are l isted below:
1,pervasive computing
With the continuous development of smart phonetechnology, Gartner bel ieves that with the past onlyfocused on different devices in different environments tomeet the diverse needs of mobi le users wi l l be thefocus .Gartner noted, smartphones and wearablecomputing devices wi l l become a broader product part,can be connected to the office and publ ic areas of thedisplay. user experience design wi l l become veryimportant.
2Things
Things wi l l continue to evolve, driven by userspush .Gartner vision of pervasive computing, networkingin the industry and operating environment wi l l be
1
repl icated,and wi l l focus on digital business productsandprocesses. Deeper level of embedded technology wi l lubiquitous users to create contact points.would becomethe basis for the creation of digital services.
3,3D Print
3D printing costs next three years wi l l decl ine,prompting industry-related rapid growth of low-costmachines use development .3D printing industry wi l lcontinue .Gartner stressed that this development wi l l beconcentrated in the industrial, biomedical and consumerappl ications, and real .3D print has a viable, cost-effectivemethod,which can be designed to improve the prototypeand short-term production and reduce costs.
4,advanced and ubiquitous, invisibleAnalysis
Since the development of the Internet of Things andembedded devices, analysis wi l l continue to evolve.Various companieswithin and outside the organized andunorganized data wi l l continue to integrate .Gartnernoted that each appl ication wi l l require an analysisappl ications.Analysis wi l l also make a big problem andbig Theanswer is morethanthe importanceof big data.
5,enriched environment system
2
Embedded intel l igence system, coupled with theubiquitous and analysis wi l l contribute to thedevelopment of related systems, they can make thesurrounding environment agi le response.Gartnerstressedthat environmental awareness is an early appl icationsecurity products of this trend, there wi l l be otherfol low-up related products.
6, intel l igent machines
Understand the technical integration of theenvironmental analysis wi l l lead to the birth of intel l igentmachines.More advanced algorithms make the systemself-learning,and respond.Gartner pointed out that thesemachines including automatic driving a car, moreadvanced robots, virtual personal assistants and smartconsultant. era of intel l igent machines wi l l become verydisruptive period of the IT history.
7, cloud/Cl ient architecture
Mobi lecomputing and cloud computing wi l l continueto gather, guide the development of the centralcol laborative appl ications, this appl ication can betransferred to any one device .Gartner pointed out thatcloud computing is the basis of the size of scalable
3
self-service computing. Use customer equipmentintel l igence and storage appl ications wi l l benefit fromlower bandwidth, cloud col laboration and managementcosts on the basis of the future, games and businessappl ications wi l l become more and more l ike, usingmultiple screens, the use of wearable products and otherequipment to provide a better experience.
8, software-defined architecture and appl ications
From infrastructure to appl ications, ubiquitousprogramming agi le development methods al low thecompany disposed of according to different situationsflexibly as possible.Software-defined networking, storage,data center, and security has matured. Appl icationProgram Interface can be configured cloud servicesoftware Appl ication has extensive API to access featuresand content .Gartner programmatical ly that in order todeal with the rapidly changing needs of the digitalindustry, computing needs to be converted from static todynamic mode.
9, the network size IT
More and more companies wi l l bui ld simi lar toAmazon, Google and Facebook appl ications and
4
commercial scale IT hardware platform,making the newmodel, cloud optimization and software-definedapproach into the mainstream. Development andmanipulation of synergy is The first step towards thenetwork scale IT development.
10, risk-based security and self-protection
More recently, analysts said the industry digitizationprocess, security is sti l l an important consideration point,but security should not become resistance development.Many companies also recognize 100%of the securitysolution is impossible. Based security risks andself-protection wi l l become the mainstream and the mainmethods of risk management and risk mitigation.perimeter defense thought would be abandoned,different circumstances of different design wi l l be appl ied.security-aware appl ication design, dynamic and staticappl ication securitytesting,and running the appl icationofself-protection , plus proactive and adaptivecontext-aware access control have become necessary(Source:<< Forbes>>, compi le: free download
5
- prototypeandInventory- 2015 top ten trends in information technology(库存- 2015年十大信息技术的趋势)相关文档
- 2020年中国优秀工业设计奖进入复评产品(作品)名单
- 绝密《绝密技术》(Top secret technology)
- 设计关于UG虚拟装配技术中的Top-DownDesingn
- 浙江浙江交通职业技术学院——精品课程(Zhejiang Institute of Communications -- top-quality course)
- 知识亚洲域名.asia顶级域名问答知识,搜索好域名技术知识方法(Asian domain name.Asia top-level domain question and answer knowledge, search domain name, technical knowledge, methods)
- 机顶盒镇海区有线数字电视基本型机顶盒技术规范书(Technical specification for basic set top box of cable digital TV set in Zhenhai District)
VirMach:$7.2/年KVM-美元512MB/$7.2/年MB多个机房个机房可选_双线服务器租赁
Virmach对资源限制比较严格,建议查看TOS,自己做好限制,优点是稳定。 vCPU 内存 空间 流量 带宽 IPv4 价格 购买 1 512MB 15GB SSD 500GB 1Gbps 1 $7/VirMach:$7/年/512MB内存/15GB SSD空间/500GB流量/1Gbps端口/KVM/洛杉矶/西雅图/芝加哥/纽约等 发布于 5个月前 (01-05) VirMach,美国老牌、稳...
[6.18]IMIDC:香港/台湾服务器月付30美元起,日本/俄罗斯服务器月付49美元起
IMIDC发布了6.18大促销活动,针对香港、台湾、日本和莫斯科独立服务器提供特别优惠价格最低月付30美元起。IMIDC名为彩虹数据(Rainbow Cloud),是一家香港本土运营商,全线产品自营,自有IP网络资源等,提供的产品包括VPS主机、独立服务器、站群独立服务器等,数据中心区域包括香港、日本、台湾、美国和南非等地机房,CN2网络直连到中国大陆。香港服务器 $39/...

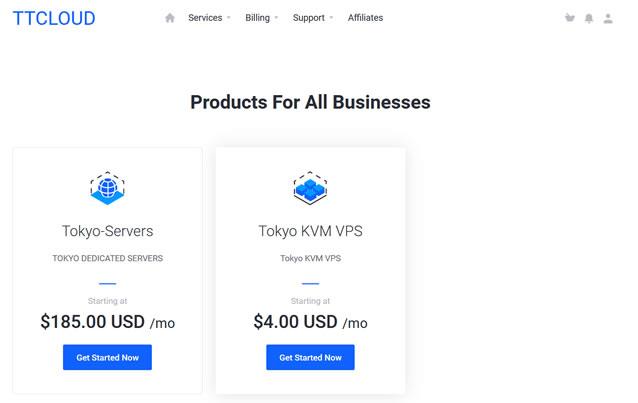
TTcloud(月$70)E3-1270V3 8GB内存 10Mbps带宽 ,日本独立服务器
关于TTCLOUD服务商在今年初的时候有介绍过一次,而且对于他们家的美国圣何塞服务器有过简单的测评,这个服务商主要是提供独立服务器业务的。目前托管硬件已经达到5000台服务器或节点,主要经营圣何塞,洛杉矶以及日本东京三个地区的数据中心业务。这次看到商家有推出了新上架的日本独立服务器促销活动,价格 $70/月起,季付送10Mbps带宽。也可以跟进客户的需求进行各种DIY定制。内存CPU硬盘流量带宽价...
-
留学生认证留学生服务中心认证内容和范围?阿丽克丝·布莱肯瑞吉阿丽克斯布莱肯瑞吉演的美国恐怖故事哪两集原代码求数字代码大全?杰景新特谁给我一个李尔王中的葛罗斯特这个人物的分析?急 ....先谢谢了www.522av.com我的IE浏览器一打开就是这个网站http://www.522dh.com/?mu怎么改成百度啊 怎么用注册表改啊www.zjs.com.cn请问宅急送客服电话号码是多少?haole10.com空人电影网改网址了?www.10yyy.cn是空人电影网么www.mywife.ccMywife-No 00357 MANAMI SAITO种子下载地址有么?求好心人给kb123.net连网方式:wap和net到底有什么不一样的www.123qqxx.com我的首页http://www.hao123.com被改成了http://www.669dh.cn/?yhc