UNCcontent.ie5
content.ie5 时间:2021-05-17 阅读:()
$STANDARD_INFORMATION$FILENAMEWindowsForensicAnalysisPOSTERYouCan'tProtectWhatYouDon'tKnowAboutdigital-forensics.
sans.
org$25.
00DFPS_FOR500_v4.
11_0121PosterCreatedbyRobLeewithsupportoftheSANSDFIRFaculty2021RobLee.
AllRightsReserved.
Modied–NoChangeCreation–NoChangeAccess–NoChangeMetadata–TimeofFileRenameFileRenameModied–NoChangeCreation–NoChangeAccess–NoChangeMetadata–NoChangeFileRenameModied–NoChangeCreation–NoChangeAccess–NoChangeMetadata–TimeofLocalFileMoveLocalFileMoveModied–NoChangeCreation–NoChangeAccess–NoChangeMetadata–NoChangeLocalFileMoveModied–InheritedfromOriginalMetadata–InheritedfromOriginalAccess–TimeofFileMoveviaCLICreation–TimeofFileMoveviaCLIVolumeFileMove(moveviaCLI)Modied–TimeofMoveviaCLIAccess–TimeofMoveviaCLIMetadata–TimeofMoveviaCLICreation–TimeofMoveviaCLIVolumeFileMove(moveviaCLI)Modied–InheritedfromOriginalMetadata–InheritedfromOriginalCreation–InheritedfromOriginalAccess–TimeofCut/PasteVolumeFileMove(cut/pasteviaExplorer)Access–TimeofCut/PasteCreation–TimeofCut/PasteModied–TimeofCut/PasteMetadata–TimeofCut/PasteVolumeFileMove(cut/pasteviaExplorer)Modied–InheritedfromOriginalAccess–TimeofFileCopyCreation–TimeofFileCopyMetadata–TimeofFileCopyFileCopyAccess–TimeofFileCopyCreation–TimeofFileCopyModied–TimeofFileCopyMetadata–TimeofFileCopyFileCopyModied–NoChangeMetadata–NoChangeAccess–TimeofAccess(NoChangeonNTFSVolumes>128GB)Creation–NoChangeFileAccessModied–NoChangeMetadata–NoChangeCreation–NoChangeAccess–NoChangeFileAccessModied–TimeofDataModicationMetadata–TimeofDataModicationCreation–NoChangeFileModicationAccess–NoChangeCreation–NoChangeModied–NoChangeMetadata–NoChangeFileModicationAccess–TimeofFileCreationAccess–TimeofDataModicationMetadata–TimeofFileCreationCreation–TimeofFileCreationModied–TimeofFileCreationFileCreationAccess–TimeofFileCreationMetadata–TimeofFileCreationCreation–TimeofFileCreationModied–TimeofFileCreationFileCreationModied–NoChangeMetadata–NoChangeAccess–NoChangeCreation–NoChangeFileDeletionModied–NoChangeMetadata–NoChangeAccess–NoChangeCreation–NoChangeFileDeletionWindowsArtifactAnalysis:Evidenceof.
.
.
UserAssistDescriptionGUI-basedprogramslaunchedfromthedesktoparetrackedinthelauncheronaWindowsSystem.
LocationNTUSER.
DATHIVE:NTUSER.
DAT\Software\Microsoft\Windows\Currentversion\Explorer\UserAssist\{GUID}\CountInterpretationAllvaluesareROT-13EncodedGUIDforXP-75048700ActiveDesktopGUIDforWin7/8/10-CEBFF5CDExecutableFileExecution-F4E57C4BShortcutFileExecutionWindows10TimelineDescriptionWin10recordsrecentlyusedapplicationsandlesina"timeline"accessibleviathe"WIN+TAB"key.
ThedataisrecordedinaSQLitedatabase.
LocationC:\Users\\AppData\Local\ConnectedDevicesPlatform\\ActivitiesCache.
dbInterpretationApplicationexecutionFocuscountperapplicationBAM/DAMDescriptionWindowsBackgroundActivityModerator(BAM)LocationWin10:SYSTEM\CurrentControlSet\Services\bam\UserSettings\{SID}SYSTEM\CurrentControlSet\Services\dam\UserSettings\{SID}InvestigativeNotesProvidesfullpathoftheexecutablelethatwasrunonthesystemandlastexecutiondate/timeShimcacheDescriptionWindowsApplicationCompatibilityDatabaseisusedbyWindowstoidentifypossibleapplicationcompatibilitychallengeswithexecutables.
Trackstheexecutableslename,lesize,lastmodiedtime,andinWindowsXPthelastupdatetimeLocationXP:SYSTEM\CurrentControlSet\Control\SessionManager\AppCompatibilityWin7/8/10:SYSTEM\CurrentControlSet\Control\SessionManager\AppCompatCacheInterpretationAnyexecutablerunontheWindowssystemcouldbefoundinthiskey.
Youcanusethiskeytoidentifysystemsthatspecicmalwarewasexecutedon.
Inaddition,basedontheinterpretationofthetime-baseddatayoumightbeabletodeterminethelasttimeofexecutionoractivityonthesystem.
WindowsXPcontainsatmost96entries-LastUpdateTimeisupdatedwhenthelesareexecutedWindows7containsatmost1,024entries-LastUpdateTimedoesnotexistonWin7systemsAmcache.
hveDescriptionProgramDataUpdater(ataskassociatedwiththeApplicationExperienceService)usestheregistryleAmcache.
hvetostoredataduringprocesscreationLocationWin7/8/10:C:\Windows\AppCompat\Programs\Amcache.
hveInterpretationAmcache.
hve–Keys=Amcache.
hve\Root\File\{VolumeGUID}Entryforeveryexecutablerun,fullpathinformation,File's$StandardInfoLastModicationTime,andDiskvolumetheexecutablewasrunfromFirstRunTime=LastModicationTimeofKeySHA1hashofexecutablealsocontainedinthekeySystemResourceUsageMonitor(SRUM)DescriptionRecords30to60daysofhistoricalsystemperformance.
Applicationsrun,useraccountresponsibleforeach,andapplicationandbytessent/receivedperapplicationperhour.
LocationSOFTWARE\Microsoft\WindowsNT\CurrentVersion\SRUM\Extensions{d10ca2fe-6fcf-4f6d-848e-b2e99266fa89}=ApplicationResourceUsageProviderC:\Windows\System32\SRU\InterpretationUsetoolsuchassrum_dump.
exetocrosscorrelatethedatabetweentheregistrykeysandtheSRUMESEDatabase.
JumpListsDescriptionTheWindows7taskbar(JumpList)isengineeredtoallowusersto"jump"oraccessitemstheyhavefrequentlyorrecentlyusedquicklyandeasily.
Thisfunctionalitycannotonlyincluderecentmediales;itmustalsoincluderecenttasks.
ThedatastoredintheAutomaticDestinationsfolderwilleachhaveauniqueleprependedwiththeAppIDoftheassociatedapplication.
LocationWin7/8/10:C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinationsInterpretationFirsttimeofexecutionofapplication.
-CreationTime=FirsttimeitemaddedtotheAppIDle.
Lasttimeofexecutionofapplicationw/leopen.
-ModicationTime=LasttimeitemaddedtotheAppIDle.
ListofJumpListIDs->https://dr.
to/EZJumpListLast-VisitedMRUDescriptionTracksthespecicexecutableusedbyanapplicationtoopenthelesdocumentedintheOpenSaveMRUkey.
Inaddition,eachvaluealsotracksthedirectorylocationforthelastlethatwasaccessedbythatapplication.
Example:Notepad.
exewaslastrunusingtheC:\%USERPROFILE%\DesktopfolderLocationXP:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRUWin7/8/10:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRUInterpretationTrackstheapplicationexecutablesusedtoopenlesinOpenSaveMRUandthelastlepathused.
PrefetchDescriptionIncreasesperformanceofasystembypre-loadingcodepagesofcommonlyusedapplications.
CacheManagermonitorsalllesanddirectoriesreferencedforeachapplicationorprocessandmapsthemintoa.
pfle.
Utilizedtoknowanapplicationwasexecutedonasystem.
Limitedto128lesonXPandWin7Limitedto1024lesonWin8(exename)-(hash).
pfLocationWinXP/7/8/10:C:\Windows\PrefetchInterpretationEach.
pfwillincludelasttimeofexecution,numberoftimesrun,anddeviceandlehandlesusedbytheprogramDate/Timelebythatnameandpathwasrstexecuted-CreationDateof.
pfle(-10seconds)Date/Timelebythatnameandpathwaslastexecuted-Embeddedlastexecutiontimeof.
pfle-Lastmodicationdateof.
pfle(-10seconds)-Win8-10willcontainlast8timesofexecutionProgramExecutionXPSearch–ACMRUDescriptionYoucansearchforawiderangeofinformationthroughthesearchassistantonaWindowsXPmachine.
Thesearchassistantwillrememberauser'ssearchtermsforlenames,computers,orwordsthatareinsideale.
Thisisanexampleofwhereyoucanndthe"SearchHistory"ontheWindowssystem.
LocationNTUSER.
DATHIVENTUSER.
DAT\Software\Microsoft\SearchAssistant\ACMru\####InterpretationSearchtheInternet–####=5001Allorpartofadocumentname–####=5603Awordorphraseinale–####=5604Printers,ComputersandPeople–####=5647ThumbcacheDescriptionThumbnailsofpictures,ofcedocuments,andfoldersexistinadatabasecalledthethumbcache.
Eachuserwillhavetheirowndatabasebasedonthethumbnailsizesviewedbytheuser(small,medium,large,andextra-larger)LocationC:\%USERPROFILE%\AppData\Local\Microsoft\Windows\ExplorerInterpretationThesearecreatedwhenauserswitchesafoldertothumbnailmodeorviewspicturesviaaslideshow.
Asitwere,ourthumbsarenowstoredinseparatedatabaseles.
Win7+has4sizesforthumbnailsandthelesinthecachefolderreectthis:-32->small-96->medium-256->large-1024->extralargeThethumbcachewillstorethethumbnailcopyofthepicturebasedonthethumbnailsizeinthecontentoftheequivalentdatabasele.
Thumbs.
dbDescriptionHiddenleindirectorywhereimagesonmachineexiststoredinasmallerthumbnailgraphics.
thumbs.
dbcatalogspicturesinafolderandstoresacopyofthethumbnailevenifthepicturesweredeleted.
LocationWinXP/Win8|8.
1AutomaticallycreatedanywherewithhomegroupenabledWin7/8/10AutomaticallycreatedanywhereandaccessedviaaUNCPath(localorremote)InterpretationInclude:ThumbnailPictureofOriginalPictureDocumentThumbnail–EvenifDeletedLastModicationTime(XPOnly)OriginalFilename(XPOnly)IE|Edgele://DescriptionAlittle-knownfactabouttheIEHistoryisthattheinformationstoredinthehistorylesisnotjustrelatedtoInternetbrowsing.
Thehistoryalsorecordslocalandremote(vianetworkshares)leaccess,givingusanexcellentmeansfordeterminingwhichlesandapplicationswereaccessedonthesystem,daybyday.
LocationInternetExplorer:IE6-7%USERPROFILE%\LocalSettings\History\History.
IE5IE8-9%USERPROFILE%\AppData\Local\Microsoft\WindowsHistory\History.
IE5IE10-11%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datInterpretationStoredinindex.
datas:file:///C:/directory/lename.
extDoesnotmeanlewasopenedinbrowserSearch–WordWheelQueryDescriptionKeywordssearchedforfromtheSTARTmenubaronaWindows7machine.
LocationWin7/8/10NTUSER.
DATHiveNTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\WordWheelQueryInterpretationKeywordsareaddedinUnicodeandlistedintemporalorderinanMRUlistWin7/8/10RecycleBinDescriptionTherecyclebinisaveryimportantlocationonaWindowslesystemtounderstand.
Itcanhelpyouwhenaccomplishingaforensicinvestigation,aseverylethatisdeletedfromaWindowsrecyclebinawareprogramisgenerallyrstputintherecyclebin.
LocationHiddenSystemFolderWin7/8/10C:\$Recycle.
binDeletedTimeandOriginalFilenamecontainedinseparatelesforeachdeletedrecoveryleInterpretationSIDcanbemappedtouserviaRegistryAnalysisWin7/8/10-FilesPrecededby$I######lescontainOriginalPATHandnameDeletionDate/Time-FilesPrecededby$R######lescontainRecoveryDataLast-VisitedMRUDescriptionTracksthespecicexecutableusedbyanapplicationtoopenthelesdocumentedintheOpenSaveMRUkey.
Inaddition,eachvaluealsotracksthedirectorylocationforthelastlethatwasaccessedbythatapplication.
LocationXPNTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRUWin7/8/10NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRUInterpretationTrackstheapplicationexecutablesusedtoopenlesinOpenSaveMRUandthelastlepathused.
XPRecycleBinDescriptionTherecyclebinisaveryimportantlocationonaWindowslesystemtounderstand.
Itcanhelpyouwhenaccomplishingaforensicinvestigation,aseverylethatisdeletedfromaWindowsrecyclebinawareprogramisgenerallyrstputintherecyclebin.
LocationHiddenSystemFolderWindowsXPC:\RECYCLER"2000/NT/XP/2003Subfolderiscreatedwithuser'sSIDHiddenleindirectorycalled"INFO2"INFO2ContainsDeletedTimeandOriginalFilenameFilenameinbothASCIIandUNICODEInterpretationSIDcanbemappedtouserviaRegistryAnalysisMapslenametotheactualnameandpathitwasdeletedfromDeletedFileorFileKnowledgeOpen/SaveMRUDescriptionInthesimplestterms,thiskeytrackslesthathavebeenopenedorsavedwithinaWindowsshelldialogbox.
Thishappenstobeabigdataset,notonlyincludingwebbrowserslikeInternetExplorerandFirefox,butalsoamajorityofcommonlyusedapplications.
LocationXP:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRUWin7/8/10:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePIDlMRUInterpretationThe"*"key–ThissubkeytracksthemostrecentlesofanyextensioninputinanOpenSavedialog.
(Threeletterextension)–ThissubkeystoresleinfofromtheOpenSavedialogbyspecicextensionEmailAttachmentsDescriptionTheemailindustryestimatesthat80%ofemaildataisstoredviaattachments.
Emailstandardsonlyallowtext.
AttachmentsmustbeencodedwithMIME/base64format.
LocationOutlookXP:%USERPROFILE%\LocalSettings\ApplicationData\Microsoft\OutlookWin7/8/10:%USERPROFILE%\AppData\Local\Microsoft\OutlookInterpretationMSOutlookdatalesfoundintheselocationsincludeOSTandPSTles.
OneshouldalsochecktheOLKandContent.
Outlookfolder,whichmightroamdependingonthespecicversionofOutlookused.
FormoreinformationonwheretondtheOLKfolderthislinkhasahandychart:http://www.
hancockcomputertech.
com/blog/2010/01/06/nd-the-microsoft-outlook-temporary-olk-folderSkypeHistoryDescriptionSkypehistorykeepsalogofchatsessionsandlestransferredfromonemachinetoanotherThisisturnedonbydefaultinSkypeinstallationsLocationXP:C:\DocumentsandSettings\\Application\Skype\Win7/8/10:C:\%USERPROFILE%\AppData\Roaming\Skype\InterpretationEachentrywillhaveadate/timevalueandaSkypeusernameassociatedwiththeaction.
BrowserArtifactsDescriptionNotdirectlyrelatedto"FileDownload".
Detailsstoredforeachlocaluseraccount.
Recordsnumberoftimesvisited(frequency).
LocationInternetExplorerIE8-9:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\IEDownloadHistory\index.
datIE10-11:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datFirefoxv3-25:%userprole%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\downloads.
sqlitev26+:%userprole%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\places.
sqliteTable:moz_annosChrome:Win7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\HistoryInterpretationManysitesinhistorywilllistthelesthatwereopenedfromremotesitesanddownloadedtothelocalsystem.
Historywillrecordtheaccesstotheleonthewebsitethatwasaccessedviaalink.
DownloadsDescriptionFirefoxandIEhasabuilt-indownloadmanagerapplicationwhichkeepsahistoryofeveryledownloadedbytheuser.
Thisbrowserartifactcanprovideexcellentinformationaboutwhatsitesauserhasbeenvisitingandwhatkindsoflestheyhavebeendownloadingfromthem.
LocationFirefox:XP:%userprole%\ApplicationData\Mozilla\Firefox\Proles\.
default\downloads.
sqliteWin7/8/10:%userprole%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\downloads.
sqliteInternetExplorer:IE8-9:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\IEDownloadHistory\IE10-11:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datInterpretationDownloadswillinclude:Filename,Size,andTypeDownloadfromandReferringPageFileSaveLocationApplicationUsedtoOpenFileDownloadStartandEndTimesADSZone.
IdentiferDescriptionStartingwithXPSP2whenlesaredownloadedfromthe"InternetZone"viaabrowsertoaNTFSvolume,analternatedatastreamisaddedtothele.
Thealternatedatastreamisnamed"Zone.
Identier.
"InterpretationFileswithanADSZone.
IdentierandcontainsZoneID=3weredownloadedfromtheInternetURLZONE_TRUSTED=ZoneID=2URLZONE_INTERNET=ZoneID=3URLZONE_UNTRUSTED=ZoneID=4FileDownloadThe"Evidenceof.
.
.
"categorieswereoriginallycreatedbySANSDigitalForensicsandIncidenceResponsefacultyfortheSANScourseFOR500:WindowsForensicAnalysis.
Thecategoriesmapaspecicartifacttotheanalysisquestionsthatitwillhelptoanswer.
Usethisposterasacheat-sheettohelpyourememberwhereyoucandiscoverkeyWindowsartifactsforcomputerintrusion,intellectualpropertytheft,andothercommoncybercrimeinvestigations.
SEC504HackerTools,Techniques,Exploits,andIncidentHandlingGCIHFOR508AdvancedIncidentResponse,ThreatHunting,andDigitalForensicsGCFAFOR572AdvancedNetworkForensics:ThreatHunting,Analysis,andIncidentResponseGNFAFOR578CyberThreatIntelligenceGCTIFOR610REM:MalwareAnalysisGREMFOR498BattleeldForensics&DataAcquisitionGBFAFOR308DigitalForensicsEssentialsFOR518MacandiOSForensicAnalysisandIncidentResponseFOR500WindowsForensicsGCFEFOR585SmartphoneForensicAnalysisIn-DepthGASFOPERATINGSYSTEM&DEVICEINDEPTHINCIDENTRESPONSE&THREATHUNTING11WindowsTimeRulesbasedoffoftestingonWindows10Releaseversion1903sansforensics@sansforensicsdr.
to/MAIL-LISTTimezoneDescriptionIdentiesthecurrentsystemtimezone.
LocationSYSTEMHive:SYSTEM\CurrentControlSet\Control\TimeZoneInformationInterpretationTimeactivityisincrediblyusefulforcorrelationofactivityInternalloglesanddate/timestampswillbebasedonthesystemtimezoneinformationYoumighthaveothernetworkdevicesandyouwillneedtocorrelateinformationtothetimezoneinformationcollectedhere.
CookiesDescriptionCookiesgiveinsightintowhatwebsiteshavebeenvisitedandwhatactivitiesmayhavetakenplacethere.
LocationInternetExplorerIE6-8:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\CookiesIE10:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\CookiesIE11:%USERPROFILE%\AppData\Local\Microsoft\Windows\INetCookiesFirefoxXP:%USERPROFILE%\ApplicationData\Mozilla\Firefox\Proles\.
default\cookies.
sqliteWin7/8/10:%USERPROFILE%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\cookies.
sqliteChromeXP:%USERPROFILE%\LocalSettings\ApplicationData\Google\Chrome\UserData\Default\LocalStorageWin7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\LocalStorageNetworkHistoryDescriptionIdentifynetworksthatthecomputerhasbeenconnectedtoNetworkscouldbewirelessorwiredIdentifydomainname/intranetnameIdentifySSIDIdentifyGatewayMACAddressLocationWin7/8/10SOFTWAREHIVE:SOFTWARE\Microsoft\WindowsNT\CurrentVersion\NetworkList\Signatures\UnmanagedSOFTWARE\Microsoft\WindowsNT\CurrentVersion\NetworkList\Signatures\ManagedSOFTWARE\Microsoft\WindowsNT\CurrentVersion\NetworkList\Nla\CacheInterpretationIdentifyingintranetsandnetworksthatacomputerhasconnectedtoisincrediblyimportantNotonlycanyoudeterminetheintranetname,youcandeterminethelasttimethenetworkwasconnectedtoitbasedonthelastwritetimeofthekeyThiswillalsolistanynetworksthathavebeenconnectedtoviaaVPNMACAddressofSSIDforGatewaycouldbephysicallytriangulatedWLANEventLogDescriptionDeterminewhatwirelessnetworksthesystemassociatedwithandidentifynetworkcharacteristicstondlocationRelevantEventIDs11000–Wirelessnetworkassociationstarted8001–Successfulconnectiontowirelessnetwork8002–Failedconnectiontowirelessnetwork8003–Disconnectfromwirelessnetwork6100–Networkdiagnostics(Systemlog)LocationMicrosoft-Windows-WLAN-AutoCongOperational.
evtxInterpretationShowshistoricalrecordofwirelessnetworkconnectionsContainsSSIDandBSSID(MACaddress),whichcanbeusedtogeolocatewirelessaccesspoint*(noBSSIDonWin8+)BrowserSearchTermsDescriptionRecordswebsitesvisitedbydateandtime.
Detailsstoredforeachlocaluseraccount.
Recordsnumberoftimesvisited(frequency).
Alsotracksaccessoflocalsystemles.
Thiswillalsoincludethewebsitehistoryofsearchtermsinsearchengines.
LocationInternetExplorerIE6-7:%USERPROFILE%\LocalSettings\History\History.
IE5IE8-9:%USERPROFILE%\AppData\Local\Microsoft\Windows\History\History.
IE5IE10-11:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datFirefoxXP:%userprole%\ApplicationData\Mozilla\Firefox\Proles\.
default\places.
sqliteWin7/8/10:%userprole%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\places.
sqliteSystemResourceUsageMonitor(SRUM)DescriptionRecords30to60daysofhistoricalsystemperformance.
Applicationsrun,useraccountresponsibleforeach,andapplicationandbytessent/receivedperapplicationperhour.
LocationSOFTWARE\Microsoft\WindowsNT\CurrentVersion\SRUM\Extensions{973F5D5C-1D90-4944-BE8E-24B94231A174}=WindowsNetworkDataUsageMonitor{DD6636C4-8929-4683-974E-22C046A43763}=WindowsNetworkConnectivityUsageMonitorSOFTWARE\Microsoft\WlanSvc\Interfaces\C:\Windows\System32\SRU\InterpretationUsetoolsuchassrum_dump.
exetocrosscorrelatethedatabetweentheregistrykeysandtheSRUMESEDatabase.
NetworkActivity/PhysicalLocationOpen/SaveMRUDescriptionInthesimplestterms,thiskeytrackslesthathavebeenopenedorsavedwithinaWindowsshelldialogbox.
Thishappenstobeabigdataset,notonlyincludingwebbrowserslikeInternetExplorerandFirefox,butalsoamajorityofcommonlyusedapplications.
LocationXP:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRUWin7/8/10:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePIDlMRUInterpretationThe"*"key–ThissubkeytracksthemostrecentlesofanyextensioninputinanOpenSavedialog.
(Threeletterextension)–ThissubkeystoresleinfofromtheOpenSavedialogbyspecicextensionRecentFilesDescriptionRegistryKeythatwilltrackthelastlesandfoldersopenedandisusedtopopulatedatain"Recent"menusoftheStartmenu.
LocationNTUSER.
DAT:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocsInterpretationRecentDocs–Overallkeywilltracktheoverallorderofthelast150lesorfoldersopened.
MRUlistwillkeeptrackofthetemporalorderinwhicheachle/folderwasopened.
Thelastentryandmodicationtimeofthiskeywillbethetimeandlocationthelastleofaspecicextensionwasopened.
Thissubkeystoresthelastleswithaspecicextensionthatwereopened.
MRUlistwillkeeptrackofthetemporalorderinwhicheachlewasopened.
Thelastentryandmodicationtimeofthiskeywillbethetimewhenandlocationwherethelastleofaspecicextensionwasopened.
Folder–Thissubkeystoresthelastfoldersthatwereopened.
MRUlistwillkeeptrackofthetemporalorderinwhicheachfolderwasopened.
Thelastentryandmodicationtimeofthiskeywillbethetimeandlocationofthelastfolderopened.
JumpListsDescriptionTheWindows7taskbar(JumpList)isengineeredtoallowusersto"jump"oraccessitemshavefrequentlyorrecentlyusedquicklyandeasily.
Thisfunctionalitycannotonlyincluderecentmediales;itmustalsoincluderecenttasks.
ThedatastoredintheAutomaticDestinationsfolderwilleachhaveauniqueleprependedwiththeAppIDoftheassociationapplicationandembeddedwithLNKlesineachstream.
LocationWin7/8/10:C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinationsInterpretationUsingtheStructuredStorageViewer,openuponeoftheAutomaticDestinationjumplistles.
EachoneoftheselesisaseparateLNKle.
Theyarealsostorednumericallyinorderfromtheearliestone(usually1)tothemostrecent(largestintegervalue).
ShellBagsDescriptionWhichfolderswereaccessedonthelocalmachine,thenetwork,and/orremovabledevices.
Evidenceofpreviouslyexistingfoldersafterdeletion/overwrite.
Whencertainfolderswereaccessed.
LocationExplorerAccess:USRCLASS.
DAT\LocalSettings\Software\Microsoft\Windows\Shell\BagsUSRCLASS.
DAT\LocalSettings\Software\Microsoft\Windows\Shell\BagMRUDesktopAccess:NTUSER.
DAT\Software\Microsoft\Windows\Shell\BagMRUNTUSER.
DAT\Software\Microsoft\Windows\Shell\BagsInterpretationStoresinformationaboutwhichfoldersweremostrecentlybrowsedbytheuser.
Shortcut(LNK)FilesDescriptionShortcutFilesautomaticallycreatedbyWindows-RecentItems-Openinglocalandremotedatalesanddocumentswillgenerateashortcutle(.
lnk)LocationXP:C:\%USERPROFILE%\RecentWin7/8/10:C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\C:\%USERPROFILE%\AppData\Roaming\Microsoft\Oce\Recent\NotetheseareprimarylocationsofLNKles.
Theycanalsobefoundinotherlocations.
InterpretationDate/Timeleofthatnamewasrstopened-CreationDateofShortcut(LNK)FileDate/Timeleofthatnamewaslastopened-LastModicationDateofShortcut(LNK)FileLNKTargetFile(InternalLNKFileInformation)Data:-Modied,Access,andCreationtimesofthetargetle-VolumeInformation(Name,Type,SerialNumber)-NetworkShareinformation-OriginalLocation-NameofSystemPrefetchDescriptionIncreasesperformanceofasystembypre-loadingcodepagesofcommonlyusedapplications.
CacheManagermonitorsalllesanddirectoriesreferencedforeachapplicationorprocessandmapsthemintoa.
pfle.
Utilizedtoknowanapplicationwasexecutedonasystem.
Limitedto128lesonXPandWin7Limitedto1024lesonWin8-10(exename)-(hash).
pfLocationWinXP/7/8/10:C:\Windows\PrefetchInterpretationCanexamineeach.
pfletolookforlehandlesrecentlyusedCanexamineeach.
pfletolookfordevicehandlesrecentlyusedLast-VisitedMRUDescriptionTracksthespecicexecutableusedbyanapplicationtoopenthelesdocumentedintheOpenSaveMRUkey.
Inaddition,eachvaluealsotracksthedirectorylocationforthelastlethatwasaccessedbythatapplication.
Example:Notepad.
exewaslastrunusingtheC:\Users\Rob\DesktopfolderLocationXP:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRUWin7/8/10:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRUInterpretationTrackstheapplicationexecutablesusedtoopenlesinOpenSaveMRUandthelastlepathused.
IE|Edgele://DescriptionAlittleknownfactabouttheIEHistoryisthattheinformationstoredinthehistorylesisnotjustrelatedtoInternetbrowsing.
Thehistoryalsorecordslocal,removable,andremote(vianetworkshares)leaccess,givingusanexcellentmeansfordeterminingwhichlesandapplicationswereaccessedonthesystem,daybyday.
LocationInternetExplorer:IE6-7:%USERPROFILE%\LocalSettings\History\History.
IE5IE8-9:%USERPROFILE%\AppData\Local\Microsoft\Windows\History\History.
IE5IE10-11:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datInterpretationStoredinindex.
datas:le:///C:/directory/lename.
extDoesnotmeanlewasopenedinbrowserOfceRecentFilesDescriptionMSOfceprogramswilltracktheirownRecentFileslisttomakeiteasierforuserstorememberthelastletheywereediting.
LocationNTUSER.
DAT\Software\Microsoft\Oce\VERSION14.
0=Ofce201011.
0=Ofce200312.
0=Ofce200710.
0=OfceXPNTUSER.
DAT\Software\Microsoft\Oce\VERSION\UserMRU\LiveID_####\FileMRU15.
0=Ofce365InterpretationSimilartotheRecentFiles,thiswilltrackthelastlesthatwereopenedbyeachMSOfceapplication.
Thelastentryadded,pertheMRU,willbethetimethelastlewasopenedbyaspecicMSOfceapplication.
File/FolderOpeningBrowserUsageLastLoginDescriptionListsthelocalaccountsofthesystemandtheirequivalentsecurityidentiers.
LocationC:\windows\system32\cong\SAMSAM\Domains\Account\UsersInterpretationOnlythelastlogintimewillbestoredintheregistrykeyLastPasswordChangeDescriptionListsthelasttimethepasswordofaspeciclocaluserhasbeenchanged.
LocationC:\windows\system32\cong\SAMSAM\Domains\Account\UsersInterpretationOnlythelastpasswordchangetimewillbestoredintheregistrykeyRDPUsageDescriptionTrackRemoteDesktopProtocollogonstotargetmachines.
LocationSecurityLogWin7/8/10:%SYSTEMROOT%\System32\winevt\logs\Security.
evtxInterpretationWin7/8/10–Interpretation-EventID4778–SessionConnected/Reconnected-EventID4779–SessionDisconnectedEventlogprovideshostnameandIPaddressofremotemachinemakingtheconnectionOnworkstationsyouwilloftenseecurrentconsolesessiondisconnected(4779)followedbyRDPconnection(4778)ServicesEventsDescriptionAnalyzelogsforsuspiciousservicesrunningatboottimeReviewservicesstartedorstoppedaroundthetimeofasuspectedcompromiseLocationAllEventIDsreferencetheSystemLog7034–Servicecrashedunexpectedly7035–ServicesentaStart/Stopcontrol7036–Servicestartedorstopped7040–Starttypechanged(Boot|OnRequest|Disabled)7045–Aservicewasinstalledonthesystem(Win2008R2+)4697–Aservicewasinstalledonthesystem(fromSecuritylog)InterpretationAllEventIDsexcept4697referencetheSystemLogAlargeamountofmalwareandwormsinthewildutilizeServicesServicesstartedonbootillustratepersistence(desirableinmalware)ServicescancrashduetoattackslikeprocessinjectionLogonTypesDescriptionLogonEventscangiveusveryspecicinformationregardingthenatureofaccountauthorizationsonasystemifweknowwheretolookandhowtodecipherthedatathatwend.
Inadditiontotellingusthedate,time,username,hostname,andsuccess/failurestatusofalogon,LogonEventsalsoenablesustodeterminebyexactlywhatmeansalogonwasattempted.
LocationWin7/8/10:EventID4624InterpretationLogonTypeExplanation2Logonviaconsole3NetworkLogon4BatchLogon5WindowsServiceLogon7Credentialsusedtounlockscreen8Networklogonsendingcredentials(cleartext)9Differentcredentialsusedthanloggedonuser10Remoteinteractivelogon(RDP)11Cachedcredentialsusedtologon12Cachedremoteinteractive(similartoType10)13Cachedunlock(similartoType7)AuthenticationEventsDescriptionAuthenticationmechanismsLocationRecordedonsystemthatauthenticatedcredentialsLocalAccount/Workgroup=onworkstationDomain/ActiveDirectory=ondomaincontrollerWin7/8/10:%SYSTEMROOT%\System32\winevt\logs\Security.
evtxInterpretationEventIDCodes(NTLMprotocol)4776:Successful/FailedaccountauthenticationEventIDCodes(Kerberosprotocol)4768:TicketGrantingTicketwasgranted(successfullogon)4769:ServiceTicketrequested(accesstoserverresource)4771:Pre-authenticationfailed(failedlogon)Success/FailLogonsDescriptionDeterminewhichaccountshavebeenusedforattemptedlogons.
Trackaccountusageforknowncompromisedaccounts.
LocationWin7/8/10:%systemroot%\System32\winevt\logs\Security.
evtxInterpretationWin7/8/10–Interpretation4624–SuccessfulLogon4625–FailedLogon4634|4647–SuccessfulLogoff4648–Logonusingexplicitcredentials(Runas)4672–Accountlogonwithsuperuserrights(Administrator)4720–AnaccountwascreatedAccountUsageKeyIdenticationDescriptionTrackUSBdevicespluggedintoamachine.
LocationSYSTEM\CurrentControlSet\Enum\USBSTORSYSTEM\CurrentControlSet\Enum\USBInterpretationIdentifyvendor,product,andversionofaUSBdevicepluggedintoamachineIdentifyauniqueUSBdevicepluggedintothemachineDeterminethetimeadevicewaspluggedintothemachineDevicesthatdonothaveauniqueserialnumberwillhavean"&"inthesecondcharacteroftheserialnumber.
First/LastTimesDescriptionDeterminetemporalusageofspecicUSBdevicesconnectedtoaWindowsMachine.
LocationFirstTimePlugandPlayLogFilesXP:C:\Windows\setupapi.
logWin7/8/10:C:\Windows\inf\setupapi.
dev.
logInterpretationSearchforDeviceSerialNumberLogFiletimesaresettolocaltimezoneLocationFirst,Last,andRemovalTimes(Win7/8/10Only)SystemHive:\CurrentControlSet\Enum\USBSTOR\Ven_Prod_Version\USBSerial#\Properties\{83da6326-97a6-4088-9453-a19231573b29}\####0064=FirstInstall(Win7-10)0066=LastConnected(Win8-10)0067=LastRemoval(Win8-10)UserDescriptionFindUserthatusedtheUniqueUSBDevice.
LocationLookforGUIDfromSYSTEM\MountedDevicesNTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2InterpretationThisGUIDwillbeusednexttoidentifytheuserthatpluggedinthedevice.
Thelastwritetimeofthiskeyalsocorrespondstothelasttimethedevicewaspluggedintothemachinebythatuser.
Thenumberwillbereferencedintheuser'spersonalmountpointskeyintheNTUSER.
DATHive.
ExternalDevice/USBUsageHistoryDescriptionRecordswebsitesvisitedbydateandtime.
Detailsstoredforeachlocaluseraccount.
Recordsnumberoftimesvisited(frequency).
Alsotracksaccessoflocalsystemles.
LocationInternetExplorerIE6-7:%USERPROFILE%\LocalSettings\History\History.
IE5IE8-9:%USERPROFILE%\AppData\Local\Microsoft\Windows\History\History.
IE5IE10,11,Edge:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datFirefoxXP:%USERPROFILE%\ApplicationData\Mozilla\Firefox\Proles\.
default\places.
sqliteWin7/8/10:%USERPROFILE%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\places.
sqliteChromeXP:%USERPROFILE%\LocalSettings\ApplicationData\Google\Chrome\UserData\Default\HistoryWin7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\HistoryCookiesDescriptionCookiesgiveinsightintowhatwebsiteshavebeenvisitedandwhatactivitiesmayhavetakenplacethere.
LocationInternetExplorerIE8-9:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\CookiesIE10:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\CookiesIE11:%USERPROFILE%\AppData\Local\Microsoft\Windows\INetCookiesEdge:%USERPROFILE%\AppData\Local\Packages\microsoft.
microsoftedge_\AC\MicrosoftEdge\CookiesFirefoxXP:%USERPROFILE%\ApplicationData\Mozilla\Firefox\Proles\.
default\cookies.
sqliteWin7/8/10:%USERPROFILE%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\cookies.
sqliteChromeXP:%USERPROFILE%\LocalSettings\ApplicationData\Google\Chrome\UserData\Default\LocalStorage\Win7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\LocalStorage\CacheDescriptionThecacheiswherewebpagecomponentscanbestoredlocallytospeedupsubsequentvisitsGivestheinvestigatora"snapshotintime"ofwhatauserwaslookingatonline-Identieswebsiteswhichwerevisited-Providestheactuallestheuserviewedonagivenwebsite-Cachedlesaretiedtoaspeciclocaluseraccount-TimestampsshowwhenthesitewasrstsavedandlastviewedLocationInternetExplorerIE8-9:%USERPROFILE%\AppData\Local\Microsoft\Windows\TemporaryInternetFiles\Content.
IE5IE10:%USERPROFILE%\AppData\Local\Microsoft\Windows\TemporaryInternetFiles\Content.
IE5IE11:%USERPROFILE%\AppData\Local\Microsoft\Windows\INetCache\IEEdge:%USERPROFILE%\AppData\Local\Packages\microsoft.
microsoftedge_\AC\MicrosoftEdge\CacheFirefoxXP:%USERPROFILE%\LocalSettings\ApplicationData\Mozilla\Firefox\Proles\.
default\CacheWin7/8/10:%USERPROFILE%\AppData\Local\Mozilla\Firefox\Proles\.
default\CacheChromeXP:%USERPROFILE%\LocalSettings\ApplicationData\Google\Chrome\UserData\Default\Cache-data_#andf_######Win7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\Cache\-data_#andf_######Flash&SuperCookiesDescriptionLocalStoredObjects(LSOs),orFlashCookies,havebecomeubiquitousonmostsystemsduetotheextremelyhighpenetrationofFlashapplicationsacrosstheInternet.
Theytendtobemuchmorepersistentbecausetheydonotexpire,andthereisnobuilt-inmechanismwithinthebrowsertoremovethem.
Infact,manysiteshavebegunusingLSOsfortheirtrackingmechanismsbecausetheyrarelygetclearedliketraditionalcookies.
LocationWin7/8/10:%APPDATA%\Roaming\Macromedia\FlashPlayer\#SharedObjects\InterpretationWebsitesvisitedUseraccountusedtovisitthesiteWhencookiewascreatedandlastaccessedSessionRestoreDescriptionAutomaticCrashRecoveryfeaturesbuiltintothebrowser.
LocationInternetExplorerWin7/8/10:%USERPROFILE%/AppData/Local/Microsoft/InternetExplorer/RecoveryFirefoxWin7/8/10:%USERPROFILE%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\sessionstore.
jsChromeWin7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\Files=CurrentSession,CurrentTabs,LastSession,LastTabsInterpretationHistoricalwebsitesviewedineachtabReferringwebsitesTimesessionendedModiedtimeof.
datlesinLastActivefolderTimeeachtabopened(onlywhencrashoccurred)Creationtimeof.
datlesinActivefolderGoogleAnalyticsCookiesDescriptionGoogleAnalytics(GA)hasdevelopedanextremelysophisticatedmethodologyfortrackingsitevisits,useractivity,andpaidsearch.
SinceGAislargelyfree,ithasacommandingshareofthemarket,estimatedatover80%ofsitesusingtrafcanalysisandover50%ofallsites.
__utma–UniquevisitorsDomainHashVisitorIDCookieCreationTimeTimeof2ndmostrecentvisitTimeofmostrecentvisitNumberofvisits__utmb–SessiontrackingDomainhashPageviewsincurrentsessionOutboundlinkclicksTimecurrentsessionstarted__utmz–TrafcsourcesDomainHashLastUpdatetimeNumberofvisitsNumberofdifferenttypesofvisitsSourceusedtoaccesssiteGoogleAdwordscampaignnameAccessMethod(organic,referral,cpc,email,direct)Keywordusedtondsite(non-SSLonly)PnPEventsDescriptionWhenaPlugandPlaydriverinstallisattempted,theservicewillloganID20001eventandprovideaStatuswithintheevent.
ItisimportanttonotethatthiseventwilltriggerforanyPlugandPlay-capabledevice,includingbutnotlimitedtoUSB,Firewire,andPCMCIAdevices.
LocationSystemLogFileWin7/8/10:%systemroot%\System32\winevt\logs\System.
evtxInterpretationEventID:20001–PlugandPlaydriverinstallattemptedEventID20001TimestampDeviceinformationDeviceserialnumberStatus(0=noerrors)VolumeSerialNumberDescriptionDiscovertheVolumeSerialNumberoftheFilesystemPartitionontheUSB.
(NOTE:ThisisnottheUSBUniqueSerialNumber,whichishardcodedintothedevicermware.
)LocationSOFTWARE\Microsoft\WindowsNT\CurrentVersion\ENDMgmtUseVolumeNameandUSBUniqueSerialNumberto:-Findlastintegernumberinline-ConvertDecimalSerialNumberintoHexSerialNumberInterpretationKnowingboththeVolumeSerialNumberandtheVolumeName,youcancorrelatethedataacrossSHORTCUTFile(LNK)analysisandtheRECENTDOCskey.
TheShortcutFile(LNK)containstheVolumeSerialNumberandNameRecentDocsRegistryKey,inmostcases,willcontainthevolumenamewhentheUSBdeviceisopenedviaExplorerDriveLetterandVolumeNameDescriptionDiscoverthelastdriveletteroftheUSBDevicewhenitwaspluggedintothemachine.
LocationXP:FindParentIdPrex–SYSTEM\CurrentControlSet\Enum\USBSTORUsingParentIdPrexDiscoverLastMountPoint–SYSTEM\MountedDevicesWin7/8/10:SOFTWARE\Microsoft\WindowsPortableDevices\DevicesSYSTEM\MountedDevices-ExamineDriveLetterslookingatValueDataLookingforSerialNumberInterpretationIdentifytheUSBdevicethatwaslastmappedtoaspecicdriveletter.
Thistechniquewillonlyworkforthelastdrivemapped.
Itdoesnotcontainhistoricalrecordsofeverydrivelettermappedtoaremovabledrive.
Shortcut(LNK)FilesDescriptionShortcutlesautomaticallycreatedbyWindowsRecentItemsOpenlocalandremotedatalesanddocumentswillgenerateashortcutle(.
lnk)LocationXP:%USERPROFILE%\RecentWin7/8/10%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent%USERPROFILE%\AppData\Roaming\Microsoft\Oce\RecentInterpretationDate/Timeleofthatnamewasrstopened-CreationDateofShortcut(LNK)FileDate/Timeleofthatnamewaslastopened-LastModicationDateofShortcut(LNK)FileLNKTargetFile(InternalLNKFileInformation)Data:-Modied,Access,andCreationtimesofthetargetle-VolumeInformation(Name,Type,SerialNumber)-NetworkShareinformation-OriginalLocation-NameofSystem
sans.
org$25.
00DFPS_FOR500_v4.
11_0121PosterCreatedbyRobLeewithsupportoftheSANSDFIRFaculty2021RobLee.
AllRightsReserved.
Modied–NoChangeCreation–NoChangeAccess–NoChangeMetadata–TimeofFileRenameFileRenameModied–NoChangeCreation–NoChangeAccess–NoChangeMetadata–NoChangeFileRenameModied–NoChangeCreation–NoChangeAccess–NoChangeMetadata–TimeofLocalFileMoveLocalFileMoveModied–NoChangeCreation–NoChangeAccess–NoChangeMetadata–NoChangeLocalFileMoveModied–InheritedfromOriginalMetadata–InheritedfromOriginalAccess–TimeofFileMoveviaCLICreation–TimeofFileMoveviaCLIVolumeFileMove(moveviaCLI)Modied–TimeofMoveviaCLIAccess–TimeofMoveviaCLIMetadata–TimeofMoveviaCLICreation–TimeofMoveviaCLIVolumeFileMove(moveviaCLI)Modied–InheritedfromOriginalMetadata–InheritedfromOriginalCreation–InheritedfromOriginalAccess–TimeofCut/PasteVolumeFileMove(cut/pasteviaExplorer)Access–TimeofCut/PasteCreation–TimeofCut/PasteModied–TimeofCut/PasteMetadata–TimeofCut/PasteVolumeFileMove(cut/pasteviaExplorer)Modied–InheritedfromOriginalAccess–TimeofFileCopyCreation–TimeofFileCopyMetadata–TimeofFileCopyFileCopyAccess–TimeofFileCopyCreation–TimeofFileCopyModied–TimeofFileCopyMetadata–TimeofFileCopyFileCopyModied–NoChangeMetadata–NoChangeAccess–TimeofAccess(NoChangeonNTFSVolumes>128GB)Creation–NoChangeFileAccessModied–NoChangeMetadata–NoChangeCreation–NoChangeAccess–NoChangeFileAccessModied–TimeofDataModicationMetadata–TimeofDataModicationCreation–NoChangeFileModicationAccess–NoChangeCreation–NoChangeModied–NoChangeMetadata–NoChangeFileModicationAccess–TimeofFileCreationAccess–TimeofDataModicationMetadata–TimeofFileCreationCreation–TimeofFileCreationModied–TimeofFileCreationFileCreationAccess–TimeofFileCreationMetadata–TimeofFileCreationCreation–TimeofFileCreationModied–TimeofFileCreationFileCreationModied–NoChangeMetadata–NoChangeAccess–NoChangeCreation–NoChangeFileDeletionModied–NoChangeMetadata–NoChangeAccess–NoChangeCreation–NoChangeFileDeletionWindowsArtifactAnalysis:Evidenceof.
.
.
UserAssistDescriptionGUI-basedprogramslaunchedfromthedesktoparetrackedinthelauncheronaWindowsSystem.
LocationNTUSER.
DATHIVE:NTUSER.
DAT\Software\Microsoft\Windows\Currentversion\Explorer\UserAssist\{GUID}\CountInterpretationAllvaluesareROT-13EncodedGUIDforXP-75048700ActiveDesktopGUIDforWin7/8/10-CEBFF5CDExecutableFileExecution-F4E57C4BShortcutFileExecutionWindows10TimelineDescriptionWin10recordsrecentlyusedapplicationsandlesina"timeline"accessibleviathe"WIN+TAB"key.
ThedataisrecordedinaSQLitedatabase.
LocationC:\Users\\AppData\Local\ConnectedDevicesPlatform\\ActivitiesCache.
dbInterpretationApplicationexecutionFocuscountperapplicationBAM/DAMDescriptionWindowsBackgroundActivityModerator(BAM)LocationWin10:SYSTEM\CurrentControlSet\Services\bam\UserSettings\{SID}SYSTEM\CurrentControlSet\Services\dam\UserSettings\{SID}InvestigativeNotesProvidesfullpathoftheexecutablelethatwasrunonthesystemandlastexecutiondate/timeShimcacheDescriptionWindowsApplicationCompatibilityDatabaseisusedbyWindowstoidentifypossibleapplicationcompatibilitychallengeswithexecutables.
Trackstheexecutableslename,lesize,lastmodiedtime,andinWindowsXPthelastupdatetimeLocationXP:SYSTEM\CurrentControlSet\Control\SessionManager\AppCompatibilityWin7/8/10:SYSTEM\CurrentControlSet\Control\SessionManager\AppCompatCacheInterpretationAnyexecutablerunontheWindowssystemcouldbefoundinthiskey.
Youcanusethiskeytoidentifysystemsthatspecicmalwarewasexecutedon.
Inaddition,basedontheinterpretationofthetime-baseddatayoumightbeabletodeterminethelasttimeofexecutionoractivityonthesystem.
WindowsXPcontainsatmost96entries-LastUpdateTimeisupdatedwhenthelesareexecutedWindows7containsatmost1,024entries-LastUpdateTimedoesnotexistonWin7systemsAmcache.
hveDescriptionProgramDataUpdater(ataskassociatedwiththeApplicationExperienceService)usestheregistryleAmcache.
hvetostoredataduringprocesscreationLocationWin7/8/10:C:\Windows\AppCompat\Programs\Amcache.
hveInterpretationAmcache.
hve–Keys=Amcache.
hve\Root\File\{VolumeGUID}Entryforeveryexecutablerun,fullpathinformation,File's$StandardInfoLastModicationTime,andDiskvolumetheexecutablewasrunfromFirstRunTime=LastModicationTimeofKeySHA1hashofexecutablealsocontainedinthekeySystemResourceUsageMonitor(SRUM)DescriptionRecords30to60daysofhistoricalsystemperformance.
Applicationsrun,useraccountresponsibleforeach,andapplicationandbytessent/receivedperapplicationperhour.
LocationSOFTWARE\Microsoft\WindowsNT\CurrentVersion\SRUM\Extensions{d10ca2fe-6fcf-4f6d-848e-b2e99266fa89}=ApplicationResourceUsageProviderC:\Windows\System32\SRU\InterpretationUsetoolsuchassrum_dump.
exetocrosscorrelatethedatabetweentheregistrykeysandtheSRUMESEDatabase.
JumpListsDescriptionTheWindows7taskbar(JumpList)isengineeredtoallowusersto"jump"oraccessitemstheyhavefrequentlyorrecentlyusedquicklyandeasily.
Thisfunctionalitycannotonlyincluderecentmediales;itmustalsoincluderecenttasks.
ThedatastoredintheAutomaticDestinationsfolderwilleachhaveauniqueleprependedwiththeAppIDoftheassociatedapplication.
LocationWin7/8/10:C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinationsInterpretationFirsttimeofexecutionofapplication.
-CreationTime=FirsttimeitemaddedtotheAppIDle.
Lasttimeofexecutionofapplicationw/leopen.
-ModicationTime=LasttimeitemaddedtotheAppIDle.
ListofJumpListIDs->https://dr.
to/EZJumpListLast-VisitedMRUDescriptionTracksthespecicexecutableusedbyanapplicationtoopenthelesdocumentedintheOpenSaveMRUkey.
Inaddition,eachvaluealsotracksthedirectorylocationforthelastlethatwasaccessedbythatapplication.
Example:Notepad.
exewaslastrunusingtheC:\%USERPROFILE%\DesktopfolderLocationXP:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRUWin7/8/10:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRUInterpretationTrackstheapplicationexecutablesusedtoopenlesinOpenSaveMRUandthelastlepathused.
PrefetchDescriptionIncreasesperformanceofasystembypre-loadingcodepagesofcommonlyusedapplications.
CacheManagermonitorsalllesanddirectoriesreferencedforeachapplicationorprocessandmapsthemintoa.
pfle.
Utilizedtoknowanapplicationwasexecutedonasystem.
Limitedto128lesonXPandWin7Limitedto1024lesonWin8(exename)-(hash).
pfLocationWinXP/7/8/10:C:\Windows\PrefetchInterpretationEach.
pfwillincludelasttimeofexecution,numberoftimesrun,anddeviceandlehandlesusedbytheprogramDate/Timelebythatnameandpathwasrstexecuted-CreationDateof.
pfle(-10seconds)Date/Timelebythatnameandpathwaslastexecuted-Embeddedlastexecutiontimeof.
pfle-Lastmodicationdateof.
pfle(-10seconds)-Win8-10willcontainlast8timesofexecutionProgramExecutionXPSearch–ACMRUDescriptionYoucansearchforawiderangeofinformationthroughthesearchassistantonaWindowsXPmachine.
Thesearchassistantwillrememberauser'ssearchtermsforlenames,computers,orwordsthatareinsideale.
Thisisanexampleofwhereyoucanndthe"SearchHistory"ontheWindowssystem.
LocationNTUSER.
DATHIVENTUSER.
DAT\Software\Microsoft\SearchAssistant\ACMru\####InterpretationSearchtheInternet–####=5001Allorpartofadocumentname–####=5603Awordorphraseinale–####=5604Printers,ComputersandPeople–####=5647ThumbcacheDescriptionThumbnailsofpictures,ofcedocuments,andfoldersexistinadatabasecalledthethumbcache.
Eachuserwillhavetheirowndatabasebasedonthethumbnailsizesviewedbytheuser(small,medium,large,andextra-larger)LocationC:\%USERPROFILE%\AppData\Local\Microsoft\Windows\ExplorerInterpretationThesearecreatedwhenauserswitchesafoldertothumbnailmodeorviewspicturesviaaslideshow.
Asitwere,ourthumbsarenowstoredinseparatedatabaseles.
Win7+has4sizesforthumbnailsandthelesinthecachefolderreectthis:-32->small-96->medium-256->large-1024->extralargeThethumbcachewillstorethethumbnailcopyofthepicturebasedonthethumbnailsizeinthecontentoftheequivalentdatabasele.
Thumbs.
dbDescriptionHiddenleindirectorywhereimagesonmachineexiststoredinasmallerthumbnailgraphics.
thumbs.
dbcatalogspicturesinafolderandstoresacopyofthethumbnailevenifthepicturesweredeleted.
LocationWinXP/Win8|8.
1AutomaticallycreatedanywherewithhomegroupenabledWin7/8/10AutomaticallycreatedanywhereandaccessedviaaUNCPath(localorremote)InterpretationInclude:ThumbnailPictureofOriginalPictureDocumentThumbnail–EvenifDeletedLastModicationTime(XPOnly)OriginalFilename(XPOnly)IE|Edgele://DescriptionAlittle-knownfactabouttheIEHistoryisthattheinformationstoredinthehistorylesisnotjustrelatedtoInternetbrowsing.
Thehistoryalsorecordslocalandremote(vianetworkshares)leaccess,givingusanexcellentmeansfordeterminingwhichlesandapplicationswereaccessedonthesystem,daybyday.
LocationInternetExplorer:IE6-7%USERPROFILE%\LocalSettings\History\History.
IE5IE8-9%USERPROFILE%\AppData\Local\Microsoft\WindowsHistory\History.
IE5IE10-11%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datInterpretationStoredinindex.
datas:file:///C:/directory/lename.
extDoesnotmeanlewasopenedinbrowserSearch–WordWheelQueryDescriptionKeywordssearchedforfromtheSTARTmenubaronaWindows7machine.
LocationWin7/8/10NTUSER.
DATHiveNTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\WordWheelQueryInterpretationKeywordsareaddedinUnicodeandlistedintemporalorderinanMRUlistWin7/8/10RecycleBinDescriptionTherecyclebinisaveryimportantlocationonaWindowslesystemtounderstand.
Itcanhelpyouwhenaccomplishingaforensicinvestigation,aseverylethatisdeletedfromaWindowsrecyclebinawareprogramisgenerallyrstputintherecyclebin.
LocationHiddenSystemFolderWin7/8/10C:\$Recycle.
binDeletedTimeandOriginalFilenamecontainedinseparatelesforeachdeletedrecoveryleInterpretationSIDcanbemappedtouserviaRegistryAnalysisWin7/8/10-FilesPrecededby$I######lescontainOriginalPATHandnameDeletionDate/Time-FilesPrecededby$R######lescontainRecoveryDataLast-VisitedMRUDescriptionTracksthespecicexecutableusedbyanapplicationtoopenthelesdocumentedintheOpenSaveMRUkey.
Inaddition,eachvaluealsotracksthedirectorylocationforthelastlethatwasaccessedbythatapplication.
LocationXPNTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRUWin7/8/10NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRUInterpretationTrackstheapplicationexecutablesusedtoopenlesinOpenSaveMRUandthelastlepathused.
XPRecycleBinDescriptionTherecyclebinisaveryimportantlocationonaWindowslesystemtounderstand.
Itcanhelpyouwhenaccomplishingaforensicinvestigation,aseverylethatisdeletedfromaWindowsrecyclebinawareprogramisgenerallyrstputintherecyclebin.
LocationHiddenSystemFolderWindowsXPC:\RECYCLER"2000/NT/XP/2003Subfolderiscreatedwithuser'sSIDHiddenleindirectorycalled"INFO2"INFO2ContainsDeletedTimeandOriginalFilenameFilenameinbothASCIIandUNICODEInterpretationSIDcanbemappedtouserviaRegistryAnalysisMapslenametotheactualnameandpathitwasdeletedfromDeletedFileorFileKnowledgeOpen/SaveMRUDescriptionInthesimplestterms,thiskeytrackslesthathavebeenopenedorsavedwithinaWindowsshelldialogbox.
Thishappenstobeabigdataset,notonlyincludingwebbrowserslikeInternetExplorerandFirefox,butalsoamajorityofcommonlyusedapplications.
LocationXP:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRUWin7/8/10:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePIDlMRUInterpretationThe"*"key–ThissubkeytracksthemostrecentlesofanyextensioninputinanOpenSavedialog.
(Threeletterextension)–ThissubkeystoresleinfofromtheOpenSavedialogbyspecicextensionEmailAttachmentsDescriptionTheemailindustryestimatesthat80%ofemaildataisstoredviaattachments.
Emailstandardsonlyallowtext.
AttachmentsmustbeencodedwithMIME/base64format.
LocationOutlookXP:%USERPROFILE%\LocalSettings\ApplicationData\Microsoft\OutlookWin7/8/10:%USERPROFILE%\AppData\Local\Microsoft\OutlookInterpretationMSOutlookdatalesfoundintheselocationsincludeOSTandPSTles.
OneshouldalsochecktheOLKandContent.
Outlookfolder,whichmightroamdependingonthespecicversionofOutlookused.
FormoreinformationonwheretondtheOLKfolderthislinkhasahandychart:http://www.
hancockcomputertech.
com/blog/2010/01/06/nd-the-microsoft-outlook-temporary-olk-folderSkypeHistoryDescriptionSkypehistorykeepsalogofchatsessionsandlestransferredfromonemachinetoanotherThisisturnedonbydefaultinSkypeinstallationsLocationXP:C:\DocumentsandSettings\\Application\Skype\Win7/8/10:C:\%USERPROFILE%\AppData\Roaming\Skype\InterpretationEachentrywillhaveadate/timevalueandaSkypeusernameassociatedwiththeaction.
BrowserArtifactsDescriptionNotdirectlyrelatedto"FileDownload".
Detailsstoredforeachlocaluseraccount.
Recordsnumberoftimesvisited(frequency).
LocationInternetExplorerIE8-9:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\IEDownloadHistory\index.
datIE10-11:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datFirefoxv3-25:%userprole%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\downloads.
sqlitev26+:%userprole%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\places.
sqliteTable:moz_annosChrome:Win7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\HistoryInterpretationManysitesinhistorywilllistthelesthatwereopenedfromremotesitesanddownloadedtothelocalsystem.
Historywillrecordtheaccesstotheleonthewebsitethatwasaccessedviaalink.
DownloadsDescriptionFirefoxandIEhasabuilt-indownloadmanagerapplicationwhichkeepsahistoryofeveryledownloadedbytheuser.
Thisbrowserartifactcanprovideexcellentinformationaboutwhatsitesauserhasbeenvisitingandwhatkindsoflestheyhavebeendownloadingfromthem.
LocationFirefox:XP:%userprole%\ApplicationData\Mozilla\Firefox\Proles\.
default\downloads.
sqliteWin7/8/10:%userprole%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\downloads.
sqliteInternetExplorer:IE8-9:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\IEDownloadHistory\IE10-11:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datInterpretationDownloadswillinclude:Filename,Size,andTypeDownloadfromandReferringPageFileSaveLocationApplicationUsedtoOpenFileDownloadStartandEndTimesADSZone.
IdentiferDescriptionStartingwithXPSP2whenlesaredownloadedfromthe"InternetZone"viaabrowsertoaNTFSvolume,analternatedatastreamisaddedtothele.
Thealternatedatastreamisnamed"Zone.
Identier.
"InterpretationFileswithanADSZone.
IdentierandcontainsZoneID=3weredownloadedfromtheInternetURLZONE_TRUSTED=ZoneID=2URLZONE_INTERNET=ZoneID=3URLZONE_UNTRUSTED=ZoneID=4FileDownloadThe"Evidenceof.
.
.
"categorieswereoriginallycreatedbySANSDigitalForensicsandIncidenceResponsefacultyfortheSANScourseFOR500:WindowsForensicAnalysis.
Thecategoriesmapaspecicartifacttotheanalysisquestionsthatitwillhelptoanswer.
Usethisposterasacheat-sheettohelpyourememberwhereyoucandiscoverkeyWindowsartifactsforcomputerintrusion,intellectualpropertytheft,andothercommoncybercrimeinvestigations.
SEC504HackerTools,Techniques,Exploits,andIncidentHandlingGCIHFOR508AdvancedIncidentResponse,ThreatHunting,andDigitalForensicsGCFAFOR572AdvancedNetworkForensics:ThreatHunting,Analysis,andIncidentResponseGNFAFOR578CyberThreatIntelligenceGCTIFOR610REM:MalwareAnalysisGREMFOR498BattleeldForensics&DataAcquisitionGBFAFOR308DigitalForensicsEssentialsFOR518MacandiOSForensicAnalysisandIncidentResponseFOR500WindowsForensicsGCFEFOR585SmartphoneForensicAnalysisIn-DepthGASFOPERATINGSYSTEM&DEVICEINDEPTHINCIDENTRESPONSE&THREATHUNTING11WindowsTimeRulesbasedoffoftestingonWindows10Releaseversion1903sansforensics@sansforensicsdr.
to/MAIL-LISTTimezoneDescriptionIdentiesthecurrentsystemtimezone.
LocationSYSTEMHive:SYSTEM\CurrentControlSet\Control\TimeZoneInformationInterpretationTimeactivityisincrediblyusefulforcorrelationofactivityInternalloglesanddate/timestampswillbebasedonthesystemtimezoneinformationYoumighthaveothernetworkdevicesandyouwillneedtocorrelateinformationtothetimezoneinformationcollectedhere.
CookiesDescriptionCookiesgiveinsightintowhatwebsiteshavebeenvisitedandwhatactivitiesmayhavetakenplacethere.
LocationInternetExplorerIE6-8:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\CookiesIE10:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\CookiesIE11:%USERPROFILE%\AppData\Local\Microsoft\Windows\INetCookiesFirefoxXP:%USERPROFILE%\ApplicationData\Mozilla\Firefox\Proles\.
default\cookies.
sqliteWin7/8/10:%USERPROFILE%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\cookies.
sqliteChromeXP:%USERPROFILE%\LocalSettings\ApplicationData\Google\Chrome\UserData\Default\LocalStorageWin7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\LocalStorageNetworkHistoryDescriptionIdentifynetworksthatthecomputerhasbeenconnectedtoNetworkscouldbewirelessorwiredIdentifydomainname/intranetnameIdentifySSIDIdentifyGatewayMACAddressLocationWin7/8/10SOFTWAREHIVE:SOFTWARE\Microsoft\WindowsNT\CurrentVersion\NetworkList\Signatures\UnmanagedSOFTWARE\Microsoft\WindowsNT\CurrentVersion\NetworkList\Signatures\ManagedSOFTWARE\Microsoft\WindowsNT\CurrentVersion\NetworkList\Nla\CacheInterpretationIdentifyingintranetsandnetworksthatacomputerhasconnectedtoisincrediblyimportantNotonlycanyoudeterminetheintranetname,youcandeterminethelasttimethenetworkwasconnectedtoitbasedonthelastwritetimeofthekeyThiswillalsolistanynetworksthathavebeenconnectedtoviaaVPNMACAddressofSSIDforGatewaycouldbephysicallytriangulatedWLANEventLogDescriptionDeterminewhatwirelessnetworksthesystemassociatedwithandidentifynetworkcharacteristicstondlocationRelevantEventIDs11000–Wirelessnetworkassociationstarted8001–Successfulconnectiontowirelessnetwork8002–Failedconnectiontowirelessnetwork8003–Disconnectfromwirelessnetwork6100–Networkdiagnostics(Systemlog)LocationMicrosoft-Windows-WLAN-AutoCongOperational.
evtxInterpretationShowshistoricalrecordofwirelessnetworkconnectionsContainsSSIDandBSSID(MACaddress),whichcanbeusedtogeolocatewirelessaccesspoint*(noBSSIDonWin8+)BrowserSearchTermsDescriptionRecordswebsitesvisitedbydateandtime.
Detailsstoredforeachlocaluseraccount.
Recordsnumberoftimesvisited(frequency).
Alsotracksaccessoflocalsystemles.
Thiswillalsoincludethewebsitehistoryofsearchtermsinsearchengines.
LocationInternetExplorerIE6-7:%USERPROFILE%\LocalSettings\History\History.
IE5IE8-9:%USERPROFILE%\AppData\Local\Microsoft\Windows\History\History.
IE5IE10-11:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datFirefoxXP:%userprole%\ApplicationData\Mozilla\Firefox\Proles\.
default\places.
sqliteWin7/8/10:%userprole%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\places.
sqliteSystemResourceUsageMonitor(SRUM)DescriptionRecords30to60daysofhistoricalsystemperformance.
Applicationsrun,useraccountresponsibleforeach,andapplicationandbytessent/receivedperapplicationperhour.
LocationSOFTWARE\Microsoft\WindowsNT\CurrentVersion\SRUM\Extensions{973F5D5C-1D90-4944-BE8E-24B94231A174}=WindowsNetworkDataUsageMonitor{DD6636C4-8929-4683-974E-22C046A43763}=WindowsNetworkConnectivityUsageMonitorSOFTWARE\Microsoft\WlanSvc\Interfaces\C:\Windows\System32\SRU\InterpretationUsetoolsuchassrum_dump.
exetocrosscorrelatethedatabetweentheregistrykeysandtheSRUMESEDatabase.
NetworkActivity/PhysicalLocationOpen/SaveMRUDescriptionInthesimplestterms,thiskeytrackslesthathavebeenopenedorsavedwithinaWindowsshelldialogbox.
Thishappenstobeabigdataset,notonlyincludingwebbrowserslikeInternetExplorerandFirefox,butalsoamajorityofcommonlyusedapplications.
LocationXP:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRUWin7/8/10:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePIDlMRUInterpretationThe"*"key–ThissubkeytracksthemostrecentlesofanyextensioninputinanOpenSavedialog.
(Threeletterextension)–ThissubkeystoresleinfofromtheOpenSavedialogbyspecicextensionRecentFilesDescriptionRegistryKeythatwilltrackthelastlesandfoldersopenedandisusedtopopulatedatain"Recent"menusoftheStartmenu.
LocationNTUSER.
DAT:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocsInterpretationRecentDocs–Overallkeywilltracktheoverallorderofthelast150lesorfoldersopened.
MRUlistwillkeeptrackofthetemporalorderinwhicheachle/folderwasopened.
Thelastentryandmodicationtimeofthiskeywillbethetimeandlocationthelastleofaspecicextensionwasopened.
Thissubkeystoresthelastleswithaspecicextensionthatwereopened.
MRUlistwillkeeptrackofthetemporalorderinwhicheachlewasopened.
Thelastentryandmodicationtimeofthiskeywillbethetimewhenandlocationwherethelastleofaspecicextensionwasopened.
Folder–Thissubkeystoresthelastfoldersthatwereopened.
MRUlistwillkeeptrackofthetemporalorderinwhicheachfolderwasopened.
Thelastentryandmodicationtimeofthiskeywillbethetimeandlocationofthelastfolderopened.
JumpListsDescriptionTheWindows7taskbar(JumpList)isengineeredtoallowusersto"jump"oraccessitemshavefrequentlyorrecentlyusedquicklyandeasily.
Thisfunctionalitycannotonlyincluderecentmediales;itmustalsoincluderecenttasks.
ThedatastoredintheAutomaticDestinationsfolderwilleachhaveauniqueleprependedwiththeAppIDoftheassociationapplicationandembeddedwithLNKlesineachstream.
LocationWin7/8/10:C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinationsInterpretationUsingtheStructuredStorageViewer,openuponeoftheAutomaticDestinationjumplistles.
EachoneoftheselesisaseparateLNKle.
Theyarealsostorednumericallyinorderfromtheearliestone(usually1)tothemostrecent(largestintegervalue).
ShellBagsDescriptionWhichfolderswereaccessedonthelocalmachine,thenetwork,and/orremovabledevices.
Evidenceofpreviouslyexistingfoldersafterdeletion/overwrite.
Whencertainfolderswereaccessed.
LocationExplorerAccess:USRCLASS.
DAT\LocalSettings\Software\Microsoft\Windows\Shell\BagsUSRCLASS.
DAT\LocalSettings\Software\Microsoft\Windows\Shell\BagMRUDesktopAccess:NTUSER.
DAT\Software\Microsoft\Windows\Shell\BagMRUNTUSER.
DAT\Software\Microsoft\Windows\Shell\BagsInterpretationStoresinformationaboutwhichfoldersweremostrecentlybrowsedbytheuser.
Shortcut(LNK)FilesDescriptionShortcutFilesautomaticallycreatedbyWindows-RecentItems-Openinglocalandremotedatalesanddocumentswillgenerateashortcutle(.
lnk)LocationXP:C:\%USERPROFILE%\RecentWin7/8/10:C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\C:\%USERPROFILE%\AppData\Roaming\Microsoft\Oce\Recent\NotetheseareprimarylocationsofLNKles.
Theycanalsobefoundinotherlocations.
InterpretationDate/Timeleofthatnamewasrstopened-CreationDateofShortcut(LNK)FileDate/Timeleofthatnamewaslastopened-LastModicationDateofShortcut(LNK)FileLNKTargetFile(InternalLNKFileInformation)Data:-Modied,Access,andCreationtimesofthetargetle-VolumeInformation(Name,Type,SerialNumber)-NetworkShareinformation-OriginalLocation-NameofSystemPrefetchDescriptionIncreasesperformanceofasystembypre-loadingcodepagesofcommonlyusedapplications.
CacheManagermonitorsalllesanddirectoriesreferencedforeachapplicationorprocessandmapsthemintoa.
pfle.
Utilizedtoknowanapplicationwasexecutedonasystem.
Limitedto128lesonXPandWin7Limitedto1024lesonWin8-10(exename)-(hash).
pfLocationWinXP/7/8/10:C:\Windows\PrefetchInterpretationCanexamineeach.
pfletolookforlehandlesrecentlyusedCanexamineeach.
pfletolookfordevicehandlesrecentlyusedLast-VisitedMRUDescriptionTracksthespecicexecutableusedbyanapplicationtoopenthelesdocumentedintheOpenSaveMRUkey.
Inaddition,eachvaluealsotracksthedirectorylocationforthelastlethatwasaccessedbythatapplication.
Example:Notepad.
exewaslastrunusingtheC:\Users\Rob\DesktopfolderLocationXP:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRUWin7/8/10:NTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRUInterpretationTrackstheapplicationexecutablesusedtoopenlesinOpenSaveMRUandthelastlepathused.
IE|Edgele://DescriptionAlittleknownfactabouttheIEHistoryisthattheinformationstoredinthehistorylesisnotjustrelatedtoInternetbrowsing.
Thehistoryalsorecordslocal,removable,andremote(vianetworkshares)leaccess,givingusanexcellentmeansfordeterminingwhichlesandapplicationswereaccessedonthesystem,daybyday.
LocationInternetExplorer:IE6-7:%USERPROFILE%\LocalSettings\History\History.
IE5IE8-9:%USERPROFILE%\AppData\Local\Microsoft\Windows\History\History.
IE5IE10-11:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datInterpretationStoredinindex.
datas:le:///C:/directory/lename.
extDoesnotmeanlewasopenedinbrowserOfceRecentFilesDescriptionMSOfceprogramswilltracktheirownRecentFileslisttomakeiteasierforuserstorememberthelastletheywereediting.
LocationNTUSER.
DAT\Software\Microsoft\Oce\VERSION14.
0=Ofce201011.
0=Ofce200312.
0=Ofce200710.
0=OfceXPNTUSER.
DAT\Software\Microsoft\Oce\VERSION\UserMRU\LiveID_####\FileMRU15.
0=Ofce365InterpretationSimilartotheRecentFiles,thiswilltrackthelastlesthatwereopenedbyeachMSOfceapplication.
Thelastentryadded,pertheMRU,willbethetimethelastlewasopenedbyaspecicMSOfceapplication.
File/FolderOpeningBrowserUsageLastLoginDescriptionListsthelocalaccountsofthesystemandtheirequivalentsecurityidentiers.
LocationC:\windows\system32\cong\SAMSAM\Domains\Account\UsersInterpretationOnlythelastlogintimewillbestoredintheregistrykeyLastPasswordChangeDescriptionListsthelasttimethepasswordofaspeciclocaluserhasbeenchanged.
LocationC:\windows\system32\cong\SAMSAM\Domains\Account\UsersInterpretationOnlythelastpasswordchangetimewillbestoredintheregistrykeyRDPUsageDescriptionTrackRemoteDesktopProtocollogonstotargetmachines.
LocationSecurityLogWin7/8/10:%SYSTEMROOT%\System32\winevt\logs\Security.
evtxInterpretationWin7/8/10–Interpretation-EventID4778–SessionConnected/Reconnected-EventID4779–SessionDisconnectedEventlogprovideshostnameandIPaddressofremotemachinemakingtheconnectionOnworkstationsyouwilloftenseecurrentconsolesessiondisconnected(4779)followedbyRDPconnection(4778)ServicesEventsDescriptionAnalyzelogsforsuspiciousservicesrunningatboottimeReviewservicesstartedorstoppedaroundthetimeofasuspectedcompromiseLocationAllEventIDsreferencetheSystemLog7034–Servicecrashedunexpectedly7035–ServicesentaStart/Stopcontrol7036–Servicestartedorstopped7040–Starttypechanged(Boot|OnRequest|Disabled)7045–Aservicewasinstalledonthesystem(Win2008R2+)4697–Aservicewasinstalledonthesystem(fromSecuritylog)InterpretationAllEventIDsexcept4697referencetheSystemLogAlargeamountofmalwareandwormsinthewildutilizeServicesServicesstartedonbootillustratepersistence(desirableinmalware)ServicescancrashduetoattackslikeprocessinjectionLogonTypesDescriptionLogonEventscangiveusveryspecicinformationregardingthenatureofaccountauthorizationsonasystemifweknowwheretolookandhowtodecipherthedatathatwend.
Inadditiontotellingusthedate,time,username,hostname,andsuccess/failurestatusofalogon,LogonEventsalsoenablesustodeterminebyexactlywhatmeansalogonwasattempted.
LocationWin7/8/10:EventID4624InterpretationLogonTypeExplanation2Logonviaconsole3NetworkLogon4BatchLogon5WindowsServiceLogon7Credentialsusedtounlockscreen8Networklogonsendingcredentials(cleartext)9Differentcredentialsusedthanloggedonuser10Remoteinteractivelogon(RDP)11Cachedcredentialsusedtologon12Cachedremoteinteractive(similartoType10)13Cachedunlock(similartoType7)AuthenticationEventsDescriptionAuthenticationmechanismsLocationRecordedonsystemthatauthenticatedcredentialsLocalAccount/Workgroup=onworkstationDomain/ActiveDirectory=ondomaincontrollerWin7/8/10:%SYSTEMROOT%\System32\winevt\logs\Security.
evtxInterpretationEventIDCodes(NTLMprotocol)4776:Successful/FailedaccountauthenticationEventIDCodes(Kerberosprotocol)4768:TicketGrantingTicketwasgranted(successfullogon)4769:ServiceTicketrequested(accesstoserverresource)4771:Pre-authenticationfailed(failedlogon)Success/FailLogonsDescriptionDeterminewhichaccountshavebeenusedforattemptedlogons.
Trackaccountusageforknowncompromisedaccounts.
LocationWin7/8/10:%systemroot%\System32\winevt\logs\Security.
evtxInterpretationWin7/8/10–Interpretation4624–SuccessfulLogon4625–FailedLogon4634|4647–SuccessfulLogoff4648–Logonusingexplicitcredentials(Runas)4672–Accountlogonwithsuperuserrights(Administrator)4720–AnaccountwascreatedAccountUsageKeyIdenticationDescriptionTrackUSBdevicespluggedintoamachine.
LocationSYSTEM\CurrentControlSet\Enum\USBSTORSYSTEM\CurrentControlSet\Enum\USBInterpretationIdentifyvendor,product,andversionofaUSBdevicepluggedintoamachineIdentifyauniqueUSBdevicepluggedintothemachineDeterminethetimeadevicewaspluggedintothemachineDevicesthatdonothaveauniqueserialnumberwillhavean"&"inthesecondcharacteroftheserialnumber.
First/LastTimesDescriptionDeterminetemporalusageofspecicUSBdevicesconnectedtoaWindowsMachine.
LocationFirstTimePlugandPlayLogFilesXP:C:\Windows\setupapi.
logWin7/8/10:C:\Windows\inf\setupapi.
dev.
logInterpretationSearchforDeviceSerialNumberLogFiletimesaresettolocaltimezoneLocationFirst,Last,andRemovalTimes(Win7/8/10Only)SystemHive:\CurrentControlSet\Enum\USBSTOR\Ven_Prod_Version\USBSerial#\Properties\{83da6326-97a6-4088-9453-a19231573b29}\####0064=FirstInstall(Win7-10)0066=LastConnected(Win8-10)0067=LastRemoval(Win8-10)UserDescriptionFindUserthatusedtheUniqueUSBDevice.
LocationLookforGUIDfromSYSTEM\MountedDevicesNTUSER.
DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2InterpretationThisGUIDwillbeusednexttoidentifytheuserthatpluggedinthedevice.
Thelastwritetimeofthiskeyalsocorrespondstothelasttimethedevicewaspluggedintothemachinebythatuser.
Thenumberwillbereferencedintheuser'spersonalmountpointskeyintheNTUSER.
DATHive.
ExternalDevice/USBUsageHistoryDescriptionRecordswebsitesvisitedbydateandtime.
Detailsstoredforeachlocaluseraccount.
Recordsnumberoftimesvisited(frequency).
Alsotracksaccessoflocalsystemles.
LocationInternetExplorerIE6-7:%USERPROFILE%\LocalSettings\History\History.
IE5IE8-9:%USERPROFILE%\AppData\Local\Microsoft\Windows\History\History.
IE5IE10,11,Edge:%USERPROFILE%\AppData\Local\Microsoft\Windows\WebCache\WebCacheV*.
datFirefoxXP:%USERPROFILE%\ApplicationData\Mozilla\Firefox\Proles\.
default\places.
sqliteWin7/8/10:%USERPROFILE%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\places.
sqliteChromeXP:%USERPROFILE%\LocalSettings\ApplicationData\Google\Chrome\UserData\Default\HistoryWin7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\HistoryCookiesDescriptionCookiesgiveinsightintowhatwebsiteshavebeenvisitedandwhatactivitiesmayhavetakenplacethere.
LocationInternetExplorerIE8-9:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\CookiesIE10:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\CookiesIE11:%USERPROFILE%\AppData\Local\Microsoft\Windows\INetCookiesEdge:%USERPROFILE%\AppData\Local\Packages\microsoft.
microsoftedge_\AC\MicrosoftEdge\CookiesFirefoxXP:%USERPROFILE%\ApplicationData\Mozilla\Firefox\Proles\.
default\cookies.
sqliteWin7/8/10:%USERPROFILE%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\cookies.
sqliteChromeXP:%USERPROFILE%\LocalSettings\ApplicationData\Google\Chrome\UserData\Default\LocalStorage\Win7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\LocalStorage\CacheDescriptionThecacheiswherewebpagecomponentscanbestoredlocallytospeedupsubsequentvisitsGivestheinvestigatora"snapshotintime"ofwhatauserwaslookingatonline-Identieswebsiteswhichwerevisited-Providestheactuallestheuserviewedonagivenwebsite-Cachedlesaretiedtoaspeciclocaluseraccount-TimestampsshowwhenthesitewasrstsavedandlastviewedLocationInternetExplorerIE8-9:%USERPROFILE%\AppData\Local\Microsoft\Windows\TemporaryInternetFiles\Content.
IE5IE10:%USERPROFILE%\AppData\Local\Microsoft\Windows\TemporaryInternetFiles\Content.
IE5IE11:%USERPROFILE%\AppData\Local\Microsoft\Windows\INetCache\IEEdge:%USERPROFILE%\AppData\Local\Packages\microsoft.
microsoftedge_\AC\MicrosoftEdge\CacheFirefoxXP:%USERPROFILE%\LocalSettings\ApplicationData\Mozilla\Firefox\Proles\.
default\CacheWin7/8/10:%USERPROFILE%\AppData\Local\Mozilla\Firefox\Proles\.
default\CacheChromeXP:%USERPROFILE%\LocalSettings\ApplicationData\Google\Chrome\UserData\Default\Cache-data_#andf_######Win7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\Cache\-data_#andf_######Flash&SuperCookiesDescriptionLocalStoredObjects(LSOs),orFlashCookies,havebecomeubiquitousonmostsystemsduetotheextremelyhighpenetrationofFlashapplicationsacrosstheInternet.
Theytendtobemuchmorepersistentbecausetheydonotexpire,andthereisnobuilt-inmechanismwithinthebrowsertoremovethem.
Infact,manysiteshavebegunusingLSOsfortheirtrackingmechanismsbecausetheyrarelygetclearedliketraditionalcookies.
LocationWin7/8/10:%APPDATA%\Roaming\Macromedia\FlashPlayer\#SharedObjects\InterpretationWebsitesvisitedUseraccountusedtovisitthesiteWhencookiewascreatedandlastaccessedSessionRestoreDescriptionAutomaticCrashRecoveryfeaturesbuiltintothebrowser.
LocationInternetExplorerWin7/8/10:%USERPROFILE%/AppData/Local/Microsoft/InternetExplorer/RecoveryFirefoxWin7/8/10:%USERPROFILE%\AppData\Roaming\Mozilla\Firefox\Proles\.
default\sessionstore.
jsChromeWin7/8/10:%USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\Files=CurrentSession,CurrentTabs,LastSession,LastTabsInterpretationHistoricalwebsitesviewedineachtabReferringwebsitesTimesessionendedModiedtimeof.
datlesinLastActivefolderTimeeachtabopened(onlywhencrashoccurred)Creationtimeof.
datlesinActivefolderGoogleAnalyticsCookiesDescriptionGoogleAnalytics(GA)hasdevelopedanextremelysophisticatedmethodologyfortrackingsitevisits,useractivity,andpaidsearch.
SinceGAislargelyfree,ithasacommandingshareofthemarket,estimatedatover80%ofsitesusingtrafcanalysisandover50%ofallsites.
__utma–UniquevisitorsDomainHashVisitorIDCookieCreationTimeTimeof2ndmostrecentvisitTimeofmostrecentvisitNumberofvisits__utmb–SessiontrackingDomainhashPageviewsincurrentsessionOutboundlinkclicksTimecurrentsessionstarted__utmz–TrafcsourcesDomainHashLastUpdatetimeNumberofvisitsNumberofdifferenttypesofvisitsSourceusedtoaccesssiteGoogleAdwordscampaignnameAccessMethod(organic,referral,cpc,email,direct)Keywordusedtondsite(non-SSLonly)PnPEventsDescriptionWhenaPlugandPlaydriverinstallisattempted,theservicewillloganID20001eventandprovideaStatuswithintheevent.
ItisimportanttonotethatthiseventwilltriggerforanyPlugandPlay-capabledevice,includingbutnotlimitedtoUSB,Firewire,andPCMCIAdevices.
LocationSystemLogFileWin7/8/10:%systemroot%\System32\winevt\logs\System.
evtxInterpretationEventID:20001–PlugandPlaydriverinstallattemptedEventID20001TimestampDeviceinformationDeviceserialnumberStatus(0=noerrors)VolumeSerialNumberDescriptionDiscovertheVolumeSerialNumberoftheFilesystemPartitionontheUSB.
(NOTE:ThisisnottheUSBUniqueSerialNumber,whichishardcodedintothedevicermware.
)LocationSOFTWARE\Microsoft\WindowsNT\CurrentVersion\ENDMgmtUseVolumeNameandUSBUniqueSerialNumberto:-Findlastintegernumberinline-ConvertDecimalSerialNumberintoHexSerialNumberInterpretationKnowingboththeVolumeSerialNumberandtheVolumeName,youcancorrelatethedataacrossSHORTCUTFile(LNK)analysisandtheRECENTDOCskey.
TheShortcutFile(LNK)containstheVolumeSerialNumberandNameRecentDocsRegistryKey,inmostcases,willcontainthevolumenamewhentheUSBdeviceisopenedviaExplorerDriveLetterandVolumeNameDescriptionDiscoverthelastdriveletteroftheUSBDevicewhenitwaspluggedintothemachine.
LocationXP:FindParentIdPrex–SYSTEM\CurrentControlSet\Enum\USBSTORUsingParentIdPrexDiscoverLastMountPoint–SYSTEM\MountedDevicesWin7/8/10:SOFTWARE\Microsoft\WindowsPortableDevices\DevicesSYSTEM\MountedDevices-ExamineDriveLetterslookingatValueDataLookingforSerialNumberInterpretationIdentifytheUSBdevicethatwaslastmappedtoaspecicdriveletter.
Thistechniquewillonlyworkforthelastdrivemapped.
Itdoesnotcontainhistoricalrecordsofeverydrivelettermappedtoaremovabledrive.
Shortcut(LNK)FilesDescriptionShortcutlesautomaticallycreatedbyWindowsRecentItemsOpenlocalandremotedatalesanddocumentswillgenerateashortcutle(.
lnk)LocationXP:%USERPROFILE%\RecentWin7/8/10%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent%USERPROFILE%\AppData\Roaming\Microsoft\Oce\RecentInterpretationDate/Timeleofthatnamewasrstopened-CreationDateofShortcut(LNK)FileDate/Timeleofthatnamewaslastopened-LastModicationDateofShortcut(LNK)FileLNKTargetFile(InternalLNKFileInformation)Data:-Modied,Access,andCreationtimesofthetargetle-VolumeInformation(Name,Type,SerialNumber)-NetworkShareinformation-OriginalLocation-NameofSystem
- UNCcontent.ie5相关文档
- Sutcliffecontent.ie5
- Comparingcontent.ie5
- humancontent.ie5
- librarycontent.ie5
- Z52Svb2rcontent.ie5
- briskcontent.ie5
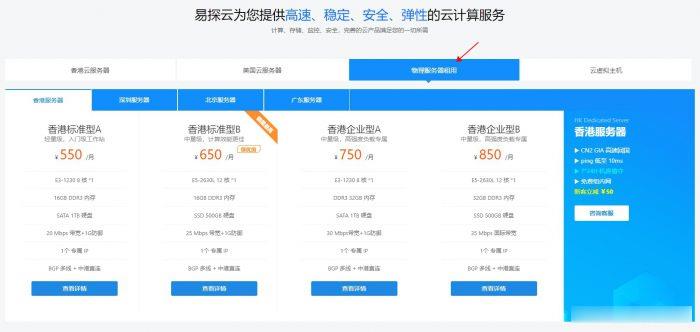
易探云:香港大带宽/大内存物理机服务器550元;20Mbps带宽!三网BGP线路
易探云怎么样?易探云隶属于纯乐电商旗下网络服务品牌,香港NTT Communications合作伙伴,YiTanCloud Limited旗下合作云计算品牌,数十年云计算行业经验。发展至今,我们已凝聚起港内领先的开发和运维团队,积累起4年市场服务经验,提供电话热线/在线咨询/服务单系统等多种沟通渠道,7*24不间断服务,3分钟快速响应。目前,易探云提供香港大带宽20Mbps、16G DDR3内存、...
印象云七夕促销,所有机器7折销售,美国CERA低至18元/月 年付217元!
印象云,成立于2019年3月的商家,公司注册于中国香港,国人运行。目前主要从事美国CERA机房高防VPS以及香港三网CN2直连VPS和美国洛杉矶GIA三网线路服务器销售。印象云香港三网CN2机房,主要是CN2直连大陆,超低延迟!对于美国CERA机房应该不陌生,主要是做高防服务器产品的,并且此机房对中国大陆支持比较友好,印象云美国高防VPS服务器去程是163直连、三网回程CN2优化,单IP默认给20...
建站选择网站域名和IP主机地址之间关系和注意要点
今天中午的时候有网友联系到在选择网站域名建站和主机的时候问到域名和IP地址有没有关联,或者需要注意的问题。毕竟我们在需要建站的时候,我们需要选择网站域名和主机,而主机有虚拟主机,包括共享和独立IP,同时还有云服务器、独立服务器、站群服务器等形式。通过这篇文章,简单的梳理关于网站域名和IP之间的关系。第一、什么是域名所谓网站域名,就是我们看到的类似"www.laozuo.org",我们可以通过直接记...

content.ie5为你推荐
-
甘肃中盛招标代理有限公司accessroute奶粉ios8支持ipad支持ipad模块iphone重庆网通重庆联通现在有哪些资费???photoshop技术ps几大关键技术?重庆宽带测速重庆市电信网速测试是哪个网站或ipwin7telnet怎样在win7下打开telnet 命令