typespartnersonline
partnersonline 时间:2021-03-19 阅读:()
87Chapter7ANewSecurityArchitecturetoImproveBusinessAgilityRealityandRhetoricAnorganization'sabilitytolearn,andtranslatethatlearningintoactionrapidly,istheultimatecompetitiveadvantage.
—JackWelchSomeStarTrekepisodesfeaturesuspense-filledbattlesinwhichadversariesusesophisticatedphase-shiftingweaponsthatcanberapidlyadjusteduntiltheyfindawaytopenetratestaticforce-fielddefenses.
Forabeleagueredstarship,theonlyeffectiveresponseistousesimilarlyadaptableandfast-changingshields.
Asinformationsecurityprofessionals,wealsoneedextremelyagiledefensesthatcanbequicklyadaptedtomeetnewdemands.
Attackersarecontinuallyadapting,anddefendersalsoneedtocontinuallyadapt.
Butrapidlyevolvingthreatsareonlypartofthechallenge.
ThetechnologylandscapeischangingjustasfastduetotrendslikeITconsumerization.
AsIntel'sinformationriskandsecuritygroupconsidersthefuture,werealizethatweneedtoradicallychangeourapproachinordertofacethechallengesaheadandsupporttheProtecttoEnablemission.
Weneedamoreagilesecurityarchitecturethatcanquicklylearnandadapttonewchallengesastheyemerge.
Becausetheenvironmentischangingsoquickly,inwayswecannotcontrol,it'simpossibletopredictallthefuturechallengeswe'llneedtoface.
Weneedanarchitecturethatcanlearntomanagewhatwedon'tknow.
Thisflexibilitywillhelpthebusinessmovemorequickly,byenablingustorapidlyadoptnewtechnologiesandemergingusagemodelswhilecontinuingtoprovidesecurityintheever-evolvingthreatlandscape.
Alearningsystemishardertodefeatbecauseitcanmorequicklyadaptinresponsetonewattacks.
Afterintensebrainstormingsessions,ourinformationriskandsecurityteamdevisedanewsecurityarchitecture.
ThisarchitectureisourimplementationoftheProtecttoEnablestrategy.
Inthischapter,I'llprovideahigh-leveloverviewofthearchitectureanddescribehowitmeetssomekeysecuritychallenges.
ThoughtheoverviewisbasedonourworkatIntel,IbelievethatthisisanovelapproachtoenterprisesecuritythatmaybevaluableChapter7ANewSecurityArchitecturetoImproveBusinessAgility88tomanyotherorganizationsfacingtheseuniversalchallenges.
Myconversationswithpeersatothercompanieshavevalidatedthisview.
Manyofthemareconsideringsimilarstrategiesandinsomecaseshavebegunimplementingthem.
WeareimplementingthisarchitectureacrossIntel'sITenvironmentinaradicalfive-yearredesignofourinformationsecuritytechnology.
Evenwhiletheimplementationisinprogress,thenewarchitecturehasalreadydeliveredresultsbyhelpingusprovideinnovativesolutionstochallengingusecaseswhileactuallyreducingrisk.
IntelIThaspublishedmoredetaileddescriptionscoveringseveralaspectsofthearchitecture(Ben-Shalometal.
2011,SunderlandandChandramouly2011,Gutierrezetal.
2012),andweexpecttocontinuetopublishinformationinthefuture.
Akeyaspectofthearchitectureisthatitprovidesmoreflexible,dynamic,andgranularsecuritycontrolsthantraditionalenterprisesecuritymodels.
Thishelpsusaccommodateusagemodelssuchasbring-your-own-device(BYOD).
Wecanprovideuserswithdifferentlevelsofaccessdependingonfactorssuchasthedevicestheyareusingandtheirlocation.
Toachievethis,thetechnologydynamicallyadjustsauser'saccessprivilegesasthelevelofriskchanges.
Forexample,anemployeeshouldhavemorelimitedaccesstooursystemswhenusingaless-securedevicethanwhenusingahardened,fullymanagedenterprise-classsystem.
Thenewarchitecturegreatlyimprovesthreatmanagement.
Asnewrisksappear,weneedtobeabletoquicklyrecognizewhichoneswecanmitigate,learnasmuchaswecan,andtakeactionasquicklyaspossible.
AtIntel,weusemanyinformationsourcestogainanunderstandingoftherisks.
Collectively,thesesourcesprovideacontinuousfeedofcollectiveintelligencethatwecanusetolearn,adapt,andevolve.
AsIdescribedinChapter6,weuseemergingthreatanalysistohelpusanticipatefuturerisks.
Butourarchitecturealsoassumesthatcompromiseisinevitableandfocusesheavilyonsurvivability.
Weareapplyingsecuritymonitoringandbusinessintelligencetoanalyzepatternsofbehavioranddetectanomaliesthataresymptomsofattacks.
Withthisknowledge,wecanfurtherinvestigateandapplymitigationwherenecessary.
Inthefuture,thisapproachcouldbeextendedbyautomaticallytakingcorrectiveactionwhereitmakessensetodoso.
BusinessTrendsandArchitectureRequirementsBeforedivingintothespecificsofthearchitecture,I'llrecapsomeofthekeybusinessandtechnologytrends,focusingonhowtheydrivetheneedforspecificcapabilitiesinsecuritytechnology.
ITConsumerizationAsIdiscussedinChapter5,consumerizationisamajorITthemewithever-broadeningimpact.
Itincludesseveraltrends,includingtheadoptionofnewapplicationsandsupportforconsumerdevices.
ManyofIntel'shighlymobileemployeeswanttousetheirownconsumerdevices,suchassmartphonesandtablets,forwork.
Thisincreasesproductivitybyenablingemployeestocollaborateandaccessinformationfromanywhere,atanytime.
TosupportChapter7ANewSecurityArchitecturetoImproveBusinessAgility89this,weprovideaccesstocorporatee-mailandotherapplicationsfromemployee-ownedsmartphonesandtablets.
Somepeoplebelievethatinthefuture,alldeviceswillbeconsumer-owned,andthatenterpriseswillnolongerpurchasedevicesfortheirusers.
Ibelievethismightbethecaseinsomeworkenvironments,butIdoubtthatitwillsuitallorganizations.
Foracompanyprovidingcallcenterservices,withmostemployeesworkingfromhome,itmightmakesensethatemployeesexclusivelyusetheirownpersonalsystemsforwork.
Butthisstrategywouldbemoreriskyforafinancialservicescompanywhoseemployeeshandlehighlysensitiveinformationthat'ssubjecttoextensiveregulatoryrequirements.
Nevertheless,theconsumerizationtrendcontinuestogrowatIntelandotherorganizations.
Accordingly,we'llneedtoprovideemployeeswithalevelofaccesstoIntelresourcesfromanexpandingcontinuumofclientdevices,someofwhichhavemuchweakersecuritycontrolsthantoday'senterpriseclients(seesidebar).
CONSUMERIZINGENTERPRISEITAND"ENTERPRISING"THECONSUMERDiscussionsofITconsumerizationtendtodrawaclearlinebetweenbusinessdevicesthatcanbemanagedandtrusted,andpersonalconsumerdevicesthatareessentiallyunmanagedanduntrusted.
However,notallconsumerdevicesarecreatedequal.
Fromasecuritystandpoint,itmaybemorevaluabletothinkaboutadevice'scapabilitiesthantocategorizeitbasedsolelyonwhetherit'smarketedasanenterprisedeviceorapersonaldevice.
Thesecurityofadevicedependsontheinherentfeaturesofthehardware,operatingsystem,andapplications,andonwhetheritenablesustoaddfurthersecurityandmanageabilitycapabilitiesthatmitigatetherisksofenterpriseuse.
Asthevarietyofconsumerdevices,suchassmartphones,continuestoexpand,usersmaychoosefromdozensofmodelswithdifferentlevelsofsecuritycapabilities.
GreatersecurityandmanageabilitymeansthatITcanplacegreatertrustinthedeviceandprovideacorrespondinglygreaterlevelofaccesstoenterpriseresources.
Extendingthisideafurther,theinformationsecuritygroupcouldevaluatethesecurityofavailableconsumerdevicesandprovideguidanceaboutthelevelofenterpriseaccessthatuserswillbeallowedwitheachdevice.
Usersmayprefertobuyamoresecuredevicebecauseitwillprovidethemmoreaccess.
Withgreateraccess,theycanusethedeviceformoreoftheirdailyworkactivities.
Thisabilityinturnenablesthemtobemoreproductive.
Atthesametime,employeesincreasinglyexpecttohaveavailabletothematworkthetypesofconsumerservicesandcloudapplicationsthattheyuseintheirpersonallives.
Theseincludesocialcomputingapplicationssuchasblogsandwikis,video-sharingsites,andfile-sharingservices.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility90Weneedasecurityarchitecturethatenablesustomorequicklysupportnewdevicesandprovideaccesstoagreaterrangeofapplicationsanddata,withoutincreasingrisk.
Weneedtobeabletodynamicallyadjustthelevelsofaccessweprovideandthemonitoringweperform,dependingonthesecuritycontrolsoftheclientdevice.
NewBusinessNeedsNearlyallcompaniesnowrelyonagrowingnetworkofbusinesspartners,andconductmanyoftheirinteractionswiththosepartnersonline.
Intelisnoexception—wearedevelopinganincreasingnumberofsystemsforonlinecollaborationwithbusinesspartners.
Also,likemanycompanies,Intelisexpandingintonewmarketsthroughbothorganicgrowthandacquisitions.
Becauseofthesebusinesstrends,mostorganizationsneedtoprovideaccesstoabroaderrangeofusers,manyofwhomarenotemployees.
Manyalsoneedtobeabletosmoothlyintegrateacquiredcompaniesandprovidethemwithaccesstoresources.
Ingeneral,weneedtoquicklyprovidenewusersaccesswhileminimizingriskandprovidingselective,controlledaccessonlytotheresourcestheyneed.
CloudComputingMostorganizationsarealreadyusingcloudservicesinsomeformtoachievebenefitssuchasgreateragilityandlowercost.
Likemanycompanies,IntelITisimplementingaprivatecloudbasedonvirtualizedinfrastructure,andwearealsousingexternalcloudservicesfornoncriticalapplications.
Inthefuture,weexpectgreateruseofhybridcloudsthatusebothinternalandexternalresources.
ThistrendmeansthatITservicesatmanyorganizationswillbeprovidedbyamixtureoftraditionalandcloud-basedinternalandexternalservices.
Duringatypicalday,employeesmayaccessavarietyofdifferentservices,someofwhichareinternalandsomeexternal.
Ultimately,theyshouldbeabletoeasilymovebetweentheseserviceswithoutneedingtologinmultipletimesorevenknowwheretheservicesarelocated.
Securingaccesstocloud-basedservicespresentschallengesthataren'teasilyaddressedusingconventionalsecuritycontrols.
Incloudenvironments,systemsandtheirdataarevirtualizedandmaymigratedynamicallytodifferentnetworklocations.
Thismakesitdifficulttoeffectivelyrestrictaccessusingtraditionalsecuritycontrolssuchasfirewalls,whichrelyonfixedlocationsofsystemsandamorestaticnatureofthedata.
Weneedmuchmoregranularanddynamiccontrolsthatarelinkedtotheresourcesthemselvesratherthanjusttheirnetworklocation.
ChangingThreatLandscapeThethreatlandscapeisevolvingrapidly.
Increasingly,attackersaretakingastealthyapproach,creatingmalwarethatquietlygainsaccessandattemptstoremainundetectedinordertomaintainaccessovertime.
Asthenumberofthreatsincreasesandnewtypesofmalwareemerge,weneedtoassumethatcompromiseisinevitable.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility91Traditionalenterprisesecurityarchitectureshavereliedlargelyonpreventativecontrolssuchasfirewallslocatedatthenetworkperimeter.
However,ourprimaryfocushasshiftedtoprovidingcontrolledaccesstoabroaderrangeofusersanddevices,ratherthansimplypreventingaccess.
Inaddition,thecontinuallychangingthreatlandscapemakesitnecessarytoassumethatcompromisewilloccur.
Onceattackershavegainedaccesstotheenvironment,thepreventativecontrolstheyhavebypassedareworthless.
Althoughtheseperimetercontrolswillcontinuetohavesomevalue,weneedtoolsthatincreasetheabilitytosurviveandrecoveronceattackershavegainedaccesstotheenvironment.
PrivacyandRegulatoryRequirementsThegrowingemphasisonprivacyrequirementsandtheincreasinglycomplexregulatoryenvironmenthavemanyimplicationsforthewaywemanageinformation.
Someregulationscreatetheneedformorecontroloverwhereinformationisstoredandrequirespecificlevelsofprotectionandtracking.
Ourarchitecturemustprovidethisassurance,allowingustobuildahigh-securityenvironmentandaccesscontrolsappropriatefortheprotectionofhighlyregulatedinformation.
NewArchitectureTomeettheserapidlychangingrequirements,weneedahighlyflexibleanddynamicarchitecture.
Thearchitectureshouldenableustomorequicklyadoptnewdevices,usemodels,andcapabilities;providesecurityacrossanincreasinglycomplexenvironment;andadapttoachangingthreatlandscape.
AtIntel,weformedateamcharteredwithdesigningthisarchitecturefromscratch,takingafreshapproachtoenterprisesecurity,thendetermininghowtoimplementthisnewarchitectureacrossourexistingITenvironment.
Keygoalsincludehelpingincreaseemployeeproductivitywhilesupportingnewbusinessrequirementsandtechnologytrends,includingITconsumerization,cloudcomputing,andaccessbyabroaderrangeofusers.
Atthesametime,thearchitectureisdesignedtoreduceourattacksurfaceandimprovesurvivability—evenasthethreatlandscapegrowsincomplexityandmaliciousness.
Thearchitecturemovesawayfromthetraditionalenterprisetrustmodel,whichisbinaryandstatic.
Withthistraditionalmodel,auserisingeneraleithergrantedordeniedaccesstoallresources;oncegranted,thelevelofaccessremainsconstant.
Thenewarchitecturereplacesthiswithadynamic,multitieredtrustmodelthatexercisesmorefine-grainedcontroloveridentityandaccesscontrol,includingaccesstospecificresources.
Thismeansthatforanindividualuser,thelevelofaccessprovidedmayvarydynamicallyovertime,dependingonavarietyoffactors—suchaswhethertheuserisaccessingthenetworkfromahighlysecuremanageddeviceoranuntrustedunmanageddevice.
Thearchitecture'sflexibilityallowsustotakeadvantageoftrustthat'sbuiltintodevicesatahardwarelevel,aswellastrustinapplicationsandservices.
Increasingly,deviceswillincludehardware-enforcedsecuritydesignedtoensuretheintegrityoftheapplicationsanddataonthedevice.
ThearchitecturetakesthisintoaccountwhenChapter7ANewSecurityArchitecturetoImproveBusinessAgility92determiningwhethertoallowaccesstospecificresources—amore-trustedplatformcanbeallowedgreateraccessthanaless-trustedone.
Thearchitectureisbasedonfourcornerstones:TrustCalculation.
Thisuniqueelementofthearchitecturehandlesuseridentityandaccessmanagement,dynamicallydeterminingwhetherausershouldbegrantedaccesstospecificresourcesand,ifso,whattypeofaccessshouldbegranted.
Thecalculationisbasedonfactorssuchastheuser'sclientdeviceandlocation,thetypeofresourcesrequested,andthesecuritycontrolsthatareavailable.
SecurityZones.
Theinfrastructureisdividedintomultiplesecurityzonesthatprovidedifferentlevelsofprotection.
Theserangefromtrustednetworkzonescontainingcriticaldata,withtightlycontrolledaccess,tountrustedzonescontainingless-valuabledataandallowingbroaderaccess.
Communicationbetweenzonesiscontrolledandmonitored;thishelpsensureuserscanonlyaccesstheresourcesforwhichtheyhavebeenauthorizedandpreventscompromisesfromspreadingacrossmultiplezones.
BalancedControls.
Toincreaseflexibilityandtheabilitytorecoverfromasuccessfulattack,themodelemphasizestheneedforabalanceofdetectiveandcorrectivecontrolsinadditiontopreventativecontrolssuchasfirewalls.
Thisincludesafocusonbusinessintelligenceanalyticaltoolstodetectanomalouspatternsthatmayindicateattemptstocompromisetheenvironment.
UserandDataPerimeters.
Recognizingthatprotectingtheenterprisenetworkboundaryisnolongeradequate,weneedtotreatusersanddataasadditionalsecurityperimetersandprotectthemaccordingly.
Thismeansanincreasedfocusonuserawarenessaswellasdataprotectionbuiltintotheinformationassets.
I'lldescribeeachofthefourcornerstonesinmoredetail.
TrustCalculationThetrustcalculationplaysanessentialroleinprovidingtheflexibilityrequiredtosupportarapidlyexpandingnumberofdevicesandusagemodels.
Thecalculationenablesustodynamicallyadjustusers'levelsofaccess,dependingonfactorssuchasthedevicesandnetworkstheyarecurrentlyusing.
Itcalculatestrustintheinteractionbetweenthepersonordevicerequestingaccess(source)andtheinformationrequested(destination).
Thecalculationconsistsofasourcescoreandadestinationscore,takingintoaccountthecontrolsavailabletomitigaterisk.
AsshowninFigure7-1,theresultofthiscalculationdetermineswhethertheuserisallowedaccessandthetypeofaccessprovided.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility93Figure7-1.
Trustcalculation.
Source:IntelCorporation,2012SourceScoreTrustinthesource,orrequestor,iscalculatedbasedonthefollowingfactors:Who.
Theidentityoftheuserorservicerequestingaccessandourconfidencelevelintheauthenticationmechanismused—howconfidentarewethatusersarewhotheysaytheyareWhat.
Thedevicetype,itscontrolcapabilities,ourabilitytovalidatethosecontrols,andtheextenttowhichIntelITmanagesthedevice.
Where.
Theuser'sorservice'slocation.
Forexample,auserwhoisinsidetheIntelenterprisenetworkismoretrustedthanthesameuserconnectingthroughapublicnetwork.
Theremayalsobeotherconsiderations,suchasthegeographicalregionwheretheuserislocated.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility94DestinationScoreThisiscalculatedbasedonthesamethreefactors,buttheseareconsideredfromtheperspectiveofthedestination—theinformationthesourceistryingtoaccess:Who.
Theapplicationthatstorestherequesteddata.
Someapplicationscanenforcegreatercontrols,suchasenterpriserightsmanagement(ERM),andthereforeprovideahigherleveloftrust.
What.
Thesensitivityoftheinformationbeingrequestedandotherconsiderations,suchasourabilitytorecoveritifcompromiseoccurs.
Where.
Thesecurityzoneinwhichthedataresides.
AvailableControlsThetrustcalculationalsotakesintoaccountthesecuritycontrolsavailableforthezone.
Iftheonlycontrolsavailablearecontrolsthatsimplyblockorallowaccess,wemightdenyaccessduetolackofotheroptions.
However,ifwehaveextensivepreventativecontrolswithhighlygranularlevelsofaccess,detailedlogs,andhighlytunedsecuritymonitoring—aswellastheabilitytorecoverfromorcorrectproblems—thenwecanallowaccesswithoutcreatingadditionalrisk.
CalculatingTrustThetrustcalculationaddsthesourcescoreandthedestinationscoretoarriveataninitialtrustlevel.
Theavailablecontrolsarethenconsideredtomakeafinaldecisionaboutwhetheraccessisallowedand,ifso,how.
Thiscalculationisperformedbyalogicalentitycalledapolicydecisionpoint(PDP),whichispartoftheauthenticationinfrastructureandmakesaccesscontroldecisionsbasedonasetofpolicies.
Basedontheresultsofthiscalculation,thePDPmakesadecision,allocatingatrustlevelthatdetermineswhethertheusercanaccesstherequestedresourceandthetypeofaccessthatisallowed.
Broadly,thedecisionwillfallintooneofthefollowingcategories:AllowaccessDenyaccessAllowaccesswithlimitationsormitigationThistrustcalculationthereforeallowsustodynamicallyapplygranularcontroloveraccesstospecificresources.
Forexample,employeesusingIT-manageddeviceswithadditionalhardwarefeaturessuchasatrustedplatformmodule(TPM),globalpositioningsystem(GPS),andfulldiskencryptionwouldbeallowedaccesstomoreresourcesthanwhenusingdevicesthatlackthosefeatures.
EmployeesdirectlyconnectedtotheIntelnetworktypicallygetgreateraccessthanwhenusingapublicnetwork.
Ifweareunabletoverifythelocationofahigh-securitydevicesuchasamanagedPC,wewouldallowlessaccess.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility95Thetrustcalculationalsocanbeusedformorefine-graineddistinctionsbetweendifferentdevicemodels.
Forexample,wecouldprovidedifferentlevelsofaccessbasedonsmartphonemanageability,hardware-enabledauthenticationandencryption,andinstalledapplications.
Weanticipatesituationsinwhichthetrustlevelisnotadequatetoallowanyaccess,butthereisstillabusinessrequirementtoallowaconnectionortransactiontooccur.
Intheseconditions,theresultofthetrustcalculationcouldbeadecisiontoallowaccesswithlimitationsorwithcompensatingcontrolsthatmitigatetherisk.
Forexample,ausermightbeallowedread-onlyaccessormightbepermittedaccessonlyifadditionalmonitoringcontrolsareinplace.
We'reimplementingthistrustcalculationacrossIntel'senvironment.
Today,thetrustcalculationmakesdecisionsbasedoninformationgatheredfromcomponentsatmultiplelevelsoftheinfrastructure,suchasnetworkgateways,accesspoints,anduserdevices.
Oncethetrustcalculationmechanismisinplace,wecanextendittoincludeinformationfromabroaderrangeofsources.
Forexample,thecalculationmighttakeintoaccountthelevelofhardware-enforcedsecurityfeaturesbuiltintotheuser'sdevice.
Thiswouldallowustoprovidegreateraccesstouserswhohavemore-trusteddevices.
Thetrustcalculationcanbeusedtodetermineaccesstointernalsystemsbybusinesspartnersaswellasemployees.
Let'ssaywe'recollaboratingwithanothercompanyonthedesignofanewproduct.
Anengineeratthatcompanywantsaccesstoaspecificdocument.
Wecanaddavarietyofcriteriatothetrustcalculationfordecidingwhethertograntaccess.
Didtheengineer'srequestoriginatewithinthebusinesspartner'senterprisenetworkIsitconsistentwiththetypeofrequestthatwe'dexpectfromanengineerIfso,wehaveahigherleveloftrustintherequestor.
Ifwecannotestablishanadequateleveloftrustintheuser'sdevice,butotherfactorsprovideenoughconfidencetograntaccess,wemightprovideone-timeaccessforaspecificjob.
Wecoulddothisbyallowingadocumenttobedownloaded,butonlywithinacontainerthatensuresthedocumentiscompletelyremovedfromtheuser'sdeviceoncethejobiscompleted.
Longerterm,thetrustcalculationcouldbecomeamechanismthatisusedtodetermineaccesstobothinternalandexternalresources.
IntelIT,likemanycompanies,isusingsomeexternalcloud-basedapplications,whiledevelopinganinternalprivatecloudformostapplications.
Inthefuture,weanticipategreateruseofahybrid-cloudapproach.
Thetrustcalculationcouldbeusedtomanageidentityandaccessforboth.
SecurityZonesThearchitecturedividestheITenvironmentintomultiplesecurityzones.
Theserangefromuntrustedzonesthatprovideaccesstolessvaluabledataandlessimportantsystemstotrustedzonescontainingcriticaldataandresources.
Becausethehigher-trustzonescontainmorevaluableassets,theyareprotectedwithagreaterdepthandrangeofcontrols,andwerestrictaccesstofewertypesofdevicesandapplications,asshowninFigure7-2.
However,devicesallowedaccesstohigher-trustzonesalsohavemorepower—theymaybeabletoperformactionsthatarenotallowedwithinlower-trustzones,suchascreatingormodifyingenterprisedata.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility96Aligningtheinfrastructureinthisfashionprovidesanexcellentwaytoright-sizesecuritycontrolssothatsecurityresourcesareutilizedeffectively.
Italsohelpsimprovetheuserexperiencebyenablingemployeestochoosefromawiderrangeofdevices,suchassmartphones,forlower-riskactivities.
Accesstozonesisdeterminedbytheresultsofthetrustcalculationandiscontrolledbypolicyenforcementpoints(PEPs).
PEPsmayincludearangeofcontrols,includingfirewalls,applicationproxies,intrusiondetectionandpreventionsystems,authenticationsystems,andloggingsystems.
Communicationbetweenzonesistightlyrestricted,monitored,andcontrolled.
WeseparatezonesbylocatingthemondifferentphysicalorvirtualLANs;PEPscontrolcommunicationbetweenzones.
Thismeansthatifonezoneiscompromised,wecanpreventtheproblemfromspreadingtootherzonesorincreaseourchancesofdetectionifitdoesspread.
Inaddition,wecanusePEPcontrols,suchasapplicationproxies,toprovidedevicesandapplicationsinlower-trustzoneswithlimited,controlledaccesstospecificresourcesinhigher-trustzoneswhenrequired.
Thearchitectureincludesthreeprimarycategoriesofsecurityzone:untrusted,selective,andtrusted.
Withinthezones,therearemultiplesubzones.
UntrustedZonesThesezoneshostdataandservices(ortheinterfacestothem)thatcanbeexposedtountrustedentities.
Thisallowsustoprovidewidespreadaccesstoalimitedsetofresourcesfromnon-managedconsumerdevices,withoutincreasingtherisktohigher-valueresourceslocatedinotherzones.
Untrustedzonesmightprovideaccesstoenterpriseresources,suchascorporatee-mailandcalendars,ortheymightsimplyprovideInternetaccess.
Figure7-2.
Asthevalueofanassetincreases,thedepthandspanofcontrolsincrease,whilethenumberofalloweddevices,applications,andlocationsdecrease.
Source:IntelCorporation,2012Chapter7ANewSecurityArchitecturetoImproveBusinessAgility97Thesezonesareregardedas"sharktanks,"withahighriskofattackandcompromise.
Therefore,detectiveandcorrectivecontrolsareneededtomitigatethisrisk.
Thesecontrolsmightincludeahighlevelofmonitoringtodetectsuspectactivityandcorrectioncapabilitiessuchasdynamicremovalofuserprivilege.
Weanticipateaneedtoprovidecontrolledaccessfromthesezonestoresourcesinhigher-trustzones.
Forexample,anemployeeusinganuntrusteddevicemightbeallowedlimited,read-onlyaccesstocustomerdatalocatedinatrustedzone;ortheirdevicemightneedaccesstoadirectoryserverinatrustedzonetosende-mail.
Weexpecttoprovidethiscontrolledaccessusingapplicationproxies.
Theseproxiesactassecureintermediaries—evaluatingtherequestfromthedevice,gatheringtheinformationfromtheresourceinatrustedzone,andpassingittothedevice.
SelectiveZonesSelectivezonesprovidemoreprotectionthanuntrustedzones.
Examplesofservicesinthesezonesincludeapplicationsanddataaccessedbycontractors,businesspartners,andemployees,usingclientdevicesthataremanagedorotherwiseprovidealeveloftrust.
Selectivezonesdonotcontaincriticaldataorhigh-valueIntelintellectualproperty.
Severalselectivesubzonesprovideaccesstodifferentservicesorusers.
TrustedZonesTrustedzoneshostcriticalservices,data,andinfrastructure.
Theyarehighlysecuredandlockeddown.
Examplesofserviceswithinthesezonesareadministrativeaccesstodatacenterserversandnetworkinfrastructure,factorynetworksanddevices,enterpriseresourceplanning(ERP)applications,anddesignengineeringsystemscontainingintellectualproperty.
Accordingly,wemightonlyallowdirectaccesstotheseresourcesfromtrustedsystemslocatedwithintheenterprisenetwork,andallaccesswouldbemonitoredcloselytodetectanomalousbehavior.
AtIntel,wehaveimplementedsecurehigh-trustzonesaspartofourtransitiontoanenterpriseprivatecloud.
Implementingthesezoneswasakeystepinallowingustomoveseveralcategoriesofapplicationontovirtualizedcloudinfrastructure,includinginternalapplicationsrequiringhighsecurity,aswellasexternallyfacingapplicationsusedtocommunicatewithbusinesspartners.
Thesecurityfeaturesinthesetrustedzonesincludeapplicationhardeningandincreasedmonitoring.
Wecontinuetoaddfurthersecuritycapabilitiesovertime.
NEWSECURITYARCHITECTUREINACTION:ADAYINTHELIFEOFANEMPLOYEEThisexample(illustratedinFigure7-3)describeshowthenewsecurityarchitectureenablestheIntelsalesforcetoaccesstheinformationtheyneedinthecourseofaday.
Atthesametime,thearchitectureprotectsIntel'ssecuritybydynamicallyadjustingthelevelofaccessprovided,basedontheuser'sdeviceandlocation,andbymonitoringforanomalousbehavior.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility98Theemployeetravelstoacustomersite.
Theemployeeisusingapersonalsmartphonewithlimitedsecurityfeaturesandsoisallowedaccessonlytoservicesinuntrustedzones.
Fromhere,theemployeecanviewlimitedcustomerinformation,includingrecentorders,extractedfromanenterpriseresourceplanning(ERP)systeminatrustedzone—butonlythroughanapplicationproxyserver,whichprotectsthetrustedzonebyactingasanintermediary,evaluatinginformationrequests,accessingtheERPsystem,andrelayingtheinformationtotheuser.
Ifasmartphonerequestsanabnormallylargenumberofcustomerrecords—anindicationthatitmayhavebeenstolen—furtheraccessfromthesmartphoneisblocked.
Tohelpunderstandthereasonfortheanomalousaccess,thereisincreasedmonitoringoftheemployee'sattemptstoaccessthesystemfromanydevice.
Theemployeereachesthecustomersiteandlogsintotheenterprisenetworkfromacompany-ownedmobilebusinessPC.
Becausethisdeviceismoretrusted,theemployeenowhasaccesstoadditionalcapabilitiesavailableinselectivezones,suchastheabilitytoviewpricingandcreateordersthatarerelayedbyanapplicationproxytotheERPsysteminatrustedzone.
Figure7-3.
Thenewsecurityarchitecturedynamicallyadjuststheuser'saccesstoinformation,basedonfactorssuchastheuser'sdeviceandlocation.
Source:IntelCorporation,2012Chapter7ANewSecurityArchitecturetoImproveBusinessAgility99Theemployeereturnstothecompany'sofficeandconnectstothecorporatenetwork.
NowtheemployeeisusingatrusteddevicefromatrustedlocationandhasdirectaccesstotheERPsysteminatrustedzone.
BalancedControlsOverthepastdecade,enterprisesecurityhasfocusedheavilyonpreventativecontrolssuchasfirewallsandintrusionpreventionsystems.
Thisapproachoffersclearbenefits:itislessexpensivetopreventanattackthantocorrectproblemsafteronehasoccurred,anditiseasytoseewhenfirewallshavesuccessfullypreventedanattemptedcompromise.
However,thenewsecuritymodelrequiresthatwebalancepreventativecontrolswithdetective(monitoring)andcorrectivecontrols,forseveralreasons.
First,thefocusofthenewmodelisonenablingandcontrollingaccessfromawiderrangeofusersanddevices,ratherthanonpreventingaccess.
Second,thecontinuallychangingthreatlandscapemakesitnecessarytoassumethatcompromisewilloccur;allpreventativecontrolswilleventuallyfail.
Onceattackershavegainedaccesstotheenvironment,thepreventativecontrolstheyhavebypassedareworthless.
Byincreasingtheuseofdetectivecontrolsandimplementingmoreaggressivecorrectivecontrols,wecanmitigatetheriskofallowingbroaderaccess.
Thesecontrolsalsoincreaseourabilitytosurviveandrecoverfromasuccessfulattack.
USINGSECURITYBUSINESSINTELLIGENCETODETECTSUSPICIOUSBEHAVIORLikeanylargeorganization,Intelhasexperiencedsecurityissuesinvolvingbothexternalattackersandinsiders,includingattemptstostealintellectualproperty.
Aswe'veinvestigated,wehaveidentifiedmarkersandindicatorsthatarefrequentlyassociatedwiththeseevents.
Werealizedthatifwehadbeenabletospottheseindicatorssooner,wecouldhaverespondedandmitigatedthethreatsmorequickly.
Securitybusinessintelligenceisakeytechnologythatwecanusetodetectsuspiciousbehaviorastheenvironmentbecomesmorecomplexandattackersbecomemoreadeptatconcealingcompromises.
Analyticaltoolsautomatetheprocessofanalyzinglargevolumesofdatatodetectandmonitoranomalousactivity,allowingustodetectproblemsthatwemightotherwisemiss.
Thesecapabilitiesaresimilartothosealreadyimplementedbyfinancialinstitutionstopreventfraudulentcredit-cardtransactions,andbyonlineconsumerservicestopreventtheftofuserdata.
Banksmonitoraccessattemptsandonlinetransactionstodeterminewhethertotrusttheuser'sidentityandwhethertoallowtheuser'sactivity.
Iftheuseristryingtotransferalargesumtoanexternalaccount,thebank'ssystemsmaycomparethetransactionwiththeuser'spreviousbehaviortoseeifitappearstobeabnormal.
Tomitigaterisk,thebankmaydelaylargetransferssoitcanperformadditionalanalysisandinformtheaccountownerbye-mail.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility100Inasimilarway,wecanusesecuritybusinessintelligence—analysisandcorrelationofdatagatheredbymonitoring—toanalyzepatternsofbehavior.
Thiscandetectandthwartpossibleattacks.
Onalargescale,loggingdatageneratedbyserversandsensorsacrossthenetworkcanbecollectedintoadatabaseforanalysis.
AtIntel,weareusinganalytictoolstocorrelatethisaggregateddataandflaganomaliesforfurtherinvestigation.
Forexample,iftrafficwithinaserverclusterbecomesabnormallyhigh,itmightindicatethatabotnetisexploitingoneoftheserverstobroadcasttrafficacrosstheWeb.
Securitybusinessintelligencecanalsobeappliedatthelevelofindividualusersanddevices.
AtIntel,we'reimplementingmonitoringtechnologythattracksusers'loginsandaccessattempts,asIdescribedinChapter5.
Ourstrategyistomakelogininformationavailabletouserssothattheycanhelptospotunauthorizedaccessattempts.
Inthefuture,Ienvisagethatthesystemcouldanalyzeusers'historicalbehaviorpatternstodeterminehowtorespondwhenusersrequestaccesstoresources.
Thesystemcouldcomparetherequestwiththeuser'spreviousactions:whathaveyoudonebefore,andisthisrequestconsistentwiththosebehaviorsorisitananomalyandthereforesuspiciousIftherequestappearsconsistentwithpreviousbehavior,thesystemwouldpasstherequesttothetrustcalculation;ifitappearsanomalous,thesystemmightdenytherequestandalertthesecurityteam.
WithinIntel,wehavealsodeployedadashboardthatprovidesgranularinformationaboutinfectedclientsandservers,boostingourabilitytointervenequicklyandaccurately.
Duetooureffortstodetectandremovemalwarebeforeinfectionsoccur,weachieveda33percentreductioninmalwareimpactsin2011,despiteexperiencinga50percentincreaseinthenumberofvariants(Intel2012a).
Wealsoplantoaddapredictiveenginethatenablesproactiveprotectionandsimulationsthatcanimproveourabilitytorespondtothreats.
Thebalancebetweenpreventative,detective,andcorrectivecontrolswillvary,dependingonthesecurityzone.
Inhigh-trustzones,weimplementextensivemonitoringtodetectpossibleattemptstostealdataorcompromisecriticalsystems.
Redundancywithineachtypeofcontrolcanbeusedtoprovideadditionalprotection.
Thefollowingincludespossibleexamplesofusingdetectiveandpreventativecontrols:AnIntelemployeeattemptstosendaconfidentialdocumenttoanon-Intele-mailaddress.
Monitoringsoftwaredetectstheattempt,preventsthedocumentfrombeingsentoutsidethefirewall,andaskstheIntelemployeeifheorshereallyintendedtodothis.
Iftheemployeeconfirmsthatthiswasintended,thedocumentmaybetransmitted—orifthedocumentishighlysensitive,aredactedversionmaybesent.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility101Inappropriateuseofadocumentprotectedwithenterpriserightsmanagementtechnologyresultsinrevocationofaccesstothedocument.
Thesystemallowsaccesstospecificdocumentsbuttrackstheactivity.
Ausercandownloadafewdocumentswithoutcausingconcerns.
However,iftheuserattemptstodownloadhundredsofdocuments,thesystemslowsdownthespeedofdelivery(forinstance,onlyallowingtentobecheckedoutatatime)andalertstheuser'smanager.
Ifthemanagerapproves,theuserisgivenfasteraccess.
Thedetectionofaninfectedsystemplacesthesystemonaremediationnetwork,isolatingthesystemandrestrictingaccesstoenterpriseinformationandapplications.
Thesystemmayretainsomeabilitytoaccesscorporateassets,butallactivityiscloselyloggedtoenableincidentresponseifnecessary.
Whenasystemisfoundtobecompromised,weexamineallitsrecentactivitiesandinteractionswithothersystems.
Additionalmonitoringofthosesystemsisautomaticallyenabled.
UsersandData:TheNewPerimetersTheconceptofbalancedcontrolsalsoextendstotheprotectionofusersanddata.
Traditionalnetworksecurityboundariesaredissolvingwiththeproliferationofnewdevicesandusers'expectationsthattheyshouldbeabletoaccessinformationfromanywhereatanytime.
Usersareunderdirectassaultfromabarrageofattacksdesignedtotrickthemintotakingactionsthatcancompromisetheinformationontheirdevicesoronenterprisesystems.
Thesetrendsmeanthatweneedtothinkmorebroadlyabouthowweprotectinformation,aswellastheusersofthisinformation.
Whilewecontinuetoimplemententerprisenetworkcontrols,suchasperimeterdefensesandthedetectivecontrolsdescribedearlier,weneedtosupplementthesecontrolswithafocusontheusersandontheprimaryassetswearetryingtoprotectsuchasintellectualproperty.
Thenewarchitecturethereforeexpandsourdefensestotwoadditionalperimeters:thedataitselfandtheuserswhohaveaccesstothedata.
DataPerimeterImportantdatashouldbeprotectedatalltimes—whenitiscreated,stored,andtransmitted.
Thisbecomesincreasinglychallengingaswemovedatatomoreandmoredevicesandletmorepeopleaccessit.
Howdoweprotectinformationwhenit'slocatedoutsidethephysicalperimeteronapersonaldeviceAtIntelIT,we'reimplementingtechnologiesthatcloselyintegrateprotectionwithhigh-valuedatasothatthedataremainsprotectedasitmovestodifferentdevicesandlocations.
Technologies,suchasenterpriserightsmanagementanddataleakprevention,canbeusedtowatermarkandtaginformationsothatwecantrackandmanageitsuse.
Withenterpriserightsmanagement,thecreatorofadocumentcandefineexactlywhoChapter7ANewSecurityArchitecturetoImproveBusinessAgility102hasaccessrightsthroughoutthelifeofthedocumentandcanrevokeaccessatanypoint.
Datalosspreventionisusedtotagdocuments,tracktheirmovements,andpreventtransferoutsidetheorganizationifnecessary.
UserPerimeterAsIdescribedinChapter5,peoplearepartofthesecurityperimeter,andweneedtotreatthemassuch.
Userscanbecomesecurityrisksforavarietyofreasons.
Theyaretargetedmorefrequentlyinsocialengineeringattacks,andtheyaremorevulnerabletotheseattacksbecausetheirpersonalinformationisoftenreadilyavailableonsocialnetworkingsites.
Theymayalsoclickmaliciouslinksine-mail,downloadmalware,orstoredataonportabledevicesthatthenarelost.
AtIntel,we'vefoundthatacombinationoftraining,incentives,andotheractivitiescanhelpinstillinformationsecurityandprivacyprotectionintothecorporatecultureandsuccessfullyencouragesemployeestoownresponsibilityforprotectingenterpriseandpersonalinformation.
We'veseenoureffortspayoff,withemployeescallingthehelpdeskorsendinge-mailalertswhentheynoticesomethingthatdoesn'tseemright.
Asdiscussedinthesidebar("UsingSecurityBusinessIntelligencetoDetectSuspiciousBehavior"),ourstrategyalsoincludesmakingaccountaccesslogsavailabletouserssothattheycanhelpspotunauthorizedaccessattempts.
ConclusionThischapterdescribesanewarchitecturedesignedtosupporttheProtecttoEnablemission.
Itsgoalistoallowfasteradoptionofnewservicesandcapabilitieswhileimprovingsurvivability.
AtIntel,webelievethatthisarchitecturecanbeusedtomeetabroadrangeofevolvingrequirements,includingnewusagemodelsandthreats.
Becauseofthis,weareworkingtoingrainthismodelintoallaspectsofIntelIT,fromdevelopmenttooperations.
We'vealreadyusedaspectsofthearchitecturetoprovidesolutionstochallengingusecases,whileactuallyreducingrisk.
Forexample,we'vebeenabletomoveimportantinternalandInternet-facingapplicationstoaprivatecloudbyutilizinghigh-trustzones.
We'vesuccessfullyusedvariousapproachestoprotecttheuseranddataperimeters.
Wealsousedbalancedcontrolsandtrustzonestoenablenetworkaccessfromemployee-owneddevices.
Insomecases,projectshaveseentheirsecurityoverheaddecreasebyadoptingthismodel.
Ibelievethatthearchitecturecouldprovidesimilarvaluetootherorganizationsfacingsimilarchallenges.
Bypublishinginformationaboutthearchitecture,wehopetoencourageotherstotakeadvantageofthisarchitecturewhereveritmeetstheirneeds.
Wealsohopethatmakingthisinformationavailablewillstimulatemorediscussionandideas,andthatotherswillbuildontheseconceptstocreatefurtherinnovationsthatbenefitallofus.
—JackWelchSomeStarTrekepisodesfeaturesuspense-filledbattlesinwhichadversariesusesophisticatedphase-shiftingweaponsthatcanberapidlyadjusteduntiltheyfindawaytopenetratestaticforce-fielddefenses.
Forabeleagueredstarship,theonlyeffectiveresponseistousesimilarlyadaptableandfast-changingshields.
Asinformationsecurityprofessionals,wealsoneedextremelyagiledefensesthatcanbequicklyadaptedtomeetnewdemands.
Attackersarecontinuallyadapting,anddefendersalsoneedtocontinuallyadapt.
Butrapidlyevolvingthreatsareonlypartofthechallenge.
ThetechnologylandscapeischangingjustasfastduetotrendslikeITconsumerization.
AsIntel'sinformationriskandsecuritygroupconsidersthefuture,werealizethatweneedtoradicallychangeourapproachinordertofacethechallengesaheadandsupporttheProtecttoEnablemission.
Weneedamoreagilesecurityarchitecturethatcanquicklylearnandadapttonewchallengesastheyemerge.
Becausetheenvironmentischangingsoquickly,inwayswecannotcontrol,it'simpossibletopredictallthefuturechallengeswe'llneedtoface.
Weneedanarchitecturethatcanlearntomanagewhatwedon'tknow.
Thisflexibilitywillhelpthebusinessmovemorequickly,byenablingustorapidlyadoptnewtechnologiesandemergingusagemodelswhilecontinuingtoprovidesecurityintheever-evolvingthreatlandscape.
Alearningsystemishardertodefeatbecauseitcanmorequicklyadaptinresponsetonewattacks.
Afterintensebrainstormingsessions,ourinformationriskandsecurityteamdevisedanewsecurityarchitecture.
ThisarchitectureisourimplementationoftheProtecttoEnablestrategy.
Inthischapter,I'llprovideahigh-leveloverviewofthearchitectureanddescribehowitmeetssomekeysecuritychallenges.
ThoughtheoverviewisbasedonourworkatIntel,IbelievethatthisisanovelapproachtoenterprisesecuritythatmaybevaluableChapter7ANewSecurityArchitecturetoImproveBusinessAgility88tomanyotherorganizationsfacingtheseuniversalchallenges.
Myconversationswithpeersatothercompanieshavevalidatedthisview.
Manyofthemareconsideringsimilarstrategiesandinsomecaseshavebegunimplementingthem.
WeareimplementingthisarchitectureacrossIntel'sITenvironmentinaradicalfive-yearredesignofourinformationsecuritytechnology.
Evenwhiletheimplementationisinprogress,thenewarchitecturehasalreadydeliveredresultsbyhelpingusprovideinnovativesolutionstochallengingusecaseswhileactuallyreducingrisk.
IntelIThaspublishedmoredetaileddescriptionscoveringseveralaspectsofthearchitecture(Ben-Shalometal.
2011,SunderlandandChandramouly2011,Gutierrezetal.
2012),andweexpecttocontinuetopublishinformationinthefuture.
Akeyaspectofthearchitectureisthatitprovidesmoreflexible,dynamic,andgranularsecuritycontrolsthantraditionalenterprisesecuritymodels.
Thishelpsusaccommodateusagemodelssuchasbring-your-own-device(BYOD).
Wecanprovideuserswithdifferentlevelsofaccessdependingonfactorssuchasthedevicestheyareusingandtheirlocation.
Toachievethis,thetechnologydynamicallyadjustsauser'saccessprivilegesasthelevelofriskchanges.
Forexample,anemployeeshouldhavemorelimitedaccesstooursystemswhenusingaless-securedevicethanwhenusingahardened,fullymanagedenterprise-classsystem.
Thenewarchitecturegreatlyimprovesthreatmanagement.
Asnewrisksappear,weneedtobeabletoquicklyrecognizewhichoneswecanmitigate,learnasmuchaswecan,andtakeactionasquicklyaspossible.
AtIntel,weusemanyinformationsourcestogainanunderstandingoftherisks.
Collectively,thesesourcesprovideacontinuousfeedofcollectiveintelligencethatwecanusetolearn,adapt,andevolve.
AsIdescribedinChapter6,weuseemergingthreatanalysistohelpusanticipatefuturerisks.
Butourarchitecturealsoassumesthatcompromiseisinevitableandfocusesheavilyonsurvivability.
Weareapplyingsecuritymonitoringandbusinessintelligencetoanalyzepatternsofbehavioranddetectanomaliesthataresymptomsofattacks.
Withthisknowledge,wecanfurtherinvestigateandapplymitigationwherenecessary.
Inthefuture,thisapproachcouldbeextendedbyautomaticallytakingcorrectiveactionwhereitmakessensetodoso.
BusinessTrendsandArchitectureRequirementsBeforedivingintothespecificsofthearchitecture,I'llrecapsomeofthekeybusinessandtechnologytrends,focusingonhowtheydrivetheneedforspecificcapabilitiesinsecuritytechnology.
ITConsumerizationAsIdiscussedinChapter5,consumerizationisamajorITthemewithever-broadeningimpact.
Itincludesseveraltrends,includingtheadoptionofnewapplicationsandsupportforconsumerdevices.
ManyofIntel'shighlymobileemployeeswanttousetheirownconsumerdevices,suchassmartphonesandtablets,forwork.
Thisincreasesproductivitybyenablingemployeestocollaborateandaccessinformationfromanywhere,atanytime.
TosupportChapter7ANewSecurityArchitecturetoImproveBusinessAgility89this,weprovideaccesstocorporatee-mailandotherapplicationsfromemployee-ownedsmartphonesandtablets.
Somepeoplebelievethatinthefuture,alldeviceswillbeconsumer-owned,andthatenterpriseswillnolongerpurchasedevicesfortheirusers.
Ibelievethismightbethecaseinsomeworkenvironments,butIdoubtthatitwillsuitallorganizations.
Foracompanyprovidingcallcenterservices,withmostemployeesworkingfromhome,itmightmakesensethatemployeesexclusivelyusetheirownpersonalsystemsforwork.
Butthisstrategywouldbemoreriskyforafinancialservicescompanywhoseemployeeshandlehighlysensitiveinformationthat'ssubjecttoextensiveregulatoryrequirements.
Nevertheless,theconsumerizationtrendcontinuestogrowatIntelandotherorganizations.
Accordingly,we'llneedtoprovideemployeeswithalevelofaccesstoIntelresourcesfromanexpandingcontinuumofclientdevices,someofwhichhavemuchweakersecuritycontrolsthantoday'senterpriseclients(seesidebar).
CONSUMERIZINGENTERPRISEITAND"ENTERPRISING"THECONSUMERDiscussionsofITconsumerizationtendtodrawaclearlinebetweenbusinessdevicesthatcanbemanagedandtrusted,andpersonalconsumerdevicesthatareessentiallyunmanagedanduntrusted.
However,notallconsumerdevicesarecreatedequal.
Fromasecuritystandpoint,itmaybemorevaluabletothinkaboutadevice'scapabilitiesthantocategorizeitbasedsolelyonwhetherit'smarketedasanenterprisedeviceorapersonaldevice.
Thesecurityofadevicedependsontheinherentfeaturesofthehardware,operatingsystem,andapplications,andonwhetheritenablesustoaddfurthersecurityandmanageabilitycapabilitiesthatmitigatetherisksofenterpriseuse.
Asthevarietyofconsumerdevices,suchassmartphones,continuestoexpand,usersmaychoosefromdozensofmodelswithdifferentlevelsofsecuritycapabilities.
GreatersecurityandmanageabilitymeansthatITcanplacegreatertrustinthedeviceandprovideacorrespondinglygreaterlevelofaccesstoenterpriseresources.
Extendingthisideafurther,theinformationsecuritygroupcouldevaluatethesecurityofavailableconsumerdevicesandprovideguidanceaboutthelevelofenterpriseaccessthatuserswillbeallowedwitheachdevice.
Usersmayprefertobuyamoresecuredevicebecauseitwillprovidethemmoreaccess.
Withgreateraccess,theycanusethedeviceformoreoftheirdailyworkactivities.
Thisabilityinturnenablesthemtobemoreproductive.
Atthesametime,employeesincreasinglyexpecttohaveavailabletothematworkthetypesofconsumerservicesandcloudapplicationsthattheyuseintheirpersonallives.
Theseincludesocialcomputingapplicationssuchasblogsandwikis,video-sharingsites,andfile-sharingservices.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility90Weneedasecurityarchitecturethatenablesustomorequicklysupportnewdevicesandprovideaccesstoagreaterrangeofapplicationsanddata,withoutincreasingrisk.
Weneedtobeabletodynamicallyadjustthelevelsofaccessweprovideandthemonitoringweperform,dependingonthesecuritycontrolsoftheclientdevice.
NewBusinessNeedsNearlyallcompaniesnowrelyonagrowingnetworkofbusinesspartners,andconductmanyoftheirinteractionswiththosepartnersonline.
Intelisnoexception—wearedevelopinganincreasingnumberofsystemsforonlinecollaborationwithbusinesspartners.
Also,likemanycompanies,Intelisexpandingintonewmarketsthroughbothorganicgrowthandacquisitions.
Becauseofthesebusinesstrends,mostorganizationsneedtoprovideaccesstoabroaderrangeofusers,manyofwhomarenotemployees.
Manyalsoneedtobeabletosmoothlyintegrateacquiredcompaniesandprovidethemwithaccesstoresources.
Ingeneral,weneedtoquicklyprovidenewusersaccesswhileminimizingriskandprovidingselective,controlledaccessonlytotheresourcestheyneed.
CloudComputingMostorganizationsarealreadyusingcloudservicesinsomeformtoachievebenefitssuchasgreateragilityandlowercost.
Likemanycompanies,IntelITisimplementingaprivatecloudbasedonvirtualizedinfrastructure,andwearealsousingexternalcloudservicesfornoncriticalapplications.
Inthefuture,weexpectgreateruseofhybridcloudsthatusebothinternalandexternalresources.
ThistrendmeansthatITservicesatmanyorganizationswillbeprovidedbyamixtureoftraditionalandcloud-basedinternalandexternalservices.
Duringatypicalday,employeesmayaccessavarietyofdifferentservices,someofwhichareinternalandsomeexternal.
Ultimately,theyshouldbeabletoeasilymovebetweentheseserviceswithoutneedingtologinmultipletimesorevenknowwheretheservicesarelocated.
Securingaccesstocloud-basedservicespresentschallengesthataren'teasilyaddressedusingconventionalsecuritycontrols.
Incloudenvironments,systemsandtheirdataarevirtualizedandmaymigratedynamicallytodifferentnetworklocations.
Thismakesitdifficulttoeffectivelyrestrictaccessusingtraditionalsecuritycontrolssuchasfirewalls,whichrelyonfixedlocationsofsystemsandamorestaticnatureofthedata.
Weneedmuchmoregranularanddynamiccontrolsthatarelinkedtotheresourcesthemselvesratherthanjusttheirnetworklocation.
ChangingThreatLandscapeThethreatlandscapeisevolvingrapidly.
Increasingly,attackersaretakingastealthyapproach,creatingmalwarethatquietlygainsaccessandattemptstoremainundetectedinordertomaintainaccessovertime.
Asthenumberofthreatsincreasesandnewtypesofmalwareemerge,weneedtoassumethatcompromiseisinevitable.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility91Traditionalenterprisesecurityarchitectureshavereliedlargelyonpreventativecontrolssuchasfirewallslocatedatthenetworkperimeter.
However,ourprimaryfocushasshiftedtoprovidingcontrolledaccesstoabroaderrangeofusersanddevices,ratherthansimplypreventingaccess.
Inaddition,thecontinuallychangingthreatlandscapemakesitnecessarytoassumethatcompromisewilloccur.
Onceattackershavegainedaccesstotheenvironment,thepreventativecontrolstheyhavebypassedareworthless.
Althoughtheseperimetercontrolswillcontinuetohavesomevalue,weneedtoolsthatincreasetheabilitytosurviveandrecoveronceattackershavegainedaccesstotheenvironment.
PrivacyandRegulatoryRequirementsThegrowingemphasisonprivacyrequirementsandtheincreasinglycomplexregulatoryenvironmenthavemanyimplicationsforthewaywemanageinformation.
Someregulationscreatetheneedformorecontroloverwhereinformationisstoredandrequirespecificlevelsofprotectionandtracking.
Ourarchitecturemustprovidethisassurance,allowingustobuildahigh-securityenvironmentandaccesscontrolsappropriatefortheprotectionofhighlyregulatedinformation.
NewArchitectureTomeettheserapidlychangingrequirements,weneedahighlyflexibleanddynamicarchitecture.
Thearchitectureshouldenableustomorequicklyadoptnewdevices,usemodels,andcapabilities;providesecurityacrossanincreasinglycomplexenvironment;andadapttoachangingthreatlandscape.
AtIntel,weformedateamcharteredwithdesigningthisarchitecturefromscratch,takingafreshapproachtoenterprisesecurity,thendetermininghowtoimplementthisnewarchitectureacrossourexistingITenvironment.
Keygoalsincludehelpingincreaseemployeeproductivitywhilesupportingnewbusinessrequirementsandtechnologytrends,includingITconsumerization,cloudcomputing,andaccessbyabroaderrangeofusers.
Atthesametime,thearchitectureisdesignedtoreduceourattacksurfaceandimprovesurvivability—evenasthethreatlandscapegrowsincomplexityandmaliciousness.
Thearchitecturemovesawayfromthetraditionalenterprisetrustmodel,whichisbinaryandstatic.
Withthistraditionalmodel,auserisingeneraleithergrantedordeniedaccesstoallresources;oncegranted,thelevelofaccessremainsconstant.
Thenewarchitecturereplacesthiswithadynamic,multitieredtrustmodelthatexercisesmorefine-grainedcontroloveridentityandaccesscontrol,includingaccesstospecificresources.
Thismeansthatforanindividualuser,thelevelofaccessprovidedmayvarydynamicallyovertime,dependingonavarietyoffactors—suchaswhethertheuserisaccessingthenetworkfromahighlysecuremanageddeviceoranuntrustedunmanageddevice.
Thearchitecture'sflexibilityallowsustotakeadvantageoftrustthat'sbuiltintodevicesatahardwarelevel,aswellastrustinapplicationsandservices.
Increasingly,deviceswillincludehardware-enforcedsecuritydesignedtoensuretheintegrityoftheapplicationsanddataonthedevice.
ThearchitecturetakesthisintoaccountwhenChapter7ANewSecurityArchitecturetoImproveBusinessAgility92determiningwhethertoallowaccesstospecificresources—amore-trustedplatformcanbeallowedgreateraccessthanaless-trustedone.
Thearchitectureisbasedonfourcornerstones:TrustCalculation.
Thisuniqueelementofthearchitecturehandlesuseridentityandaccessmanagement,dynamicallydeterminingwhetherausershouldbegrantedaccesstospecificresourcesand,ifso,whattypeofaccessshouldbegranted.
Thecalculationisbasedonfactorssuchastheuser'sclientdeviceandlocation,thetypeofresourcesrequested,andthesecuritycontrolsthatareavailable.
SecurityZones.
Theinfrastructureisdividedintomultiplesecurityzonesthatprovidedifferentlevelsofprotection.
Theserangefromtrustednetworkzonescontainingcriticaldata,withtightlycontrolledaccess,tountrustedzonescontainingless-valuabledataandallowingbroaderaccess.
Communicationbetweenzonesiscontrolledandmonitored;thishelpsensureuserscanonlyaccesstheresourcesforwhichtheyhavebeenauthorizedandpreventscompromisesfromspreadingacrossmultiplezones.
BalancedControls.
Toincreaseflexibilityandtheabilitytorecoverfromasuccessfulattack,themodelemphasizestheneedforabalanceofdetectiveandcorrectivecontrolsinadditiontopreventativecontrolssuchasfirewalls.
Thisincludesafocusonbusinessintelligenceanalyticaltoolstodetectanomalouspatternsthatmayindicateattemptstocompromisetheenvironment.
UserandDataPerimeters.
Recognizingthatprotectingtheenterprisenetworkboundaryisnolongeradequate,weneedtotreatusersanddataasadditionalsecurityperimetersandprotectthemaccordingly.
Thismeansanincreasedfocusonuserawarenessaswellasdataprotectionbuiltintotheinformationassets.
I'lldescribeeachofthefourcornerstonesinmoredetail.
TrustCalculationThetrustcalculationplaysanessentialroleinprovidingtheflexibilityrequiredtosupportarapidlyexpandingnumberofdevicesandusagemodels.
Thecalculationenablesustodynamicallyadjustusers'levelsofaccess,dependingonfactorssuchasthedevicesandnetworkstheyarecurrentlyusing.
Itcalculatestrustintheinteractionbetweenthepersonordevicerequestingaccess(source)andtheinformationrequested(destination).
Thecalculationconsistsofasourcescoreandadestinationscore,takingintoaccountthecontrolsavailabletomitigaterisk.
AsshowninFigure7-1,theresultofthiscalculationdetermineswhethertheuserisallowedaccessandthetypeofaccessprovided.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility93Figure7-1.
Trustcalculation.
Source:IntelCorporation,2012SourceScoreTrustinthesource,orrequestor,iscalculatedbasedonthefollowingfactors:Who.
Theidentityoftheuserorservicerequestingaccessandourconfidencelevelintheauthenticationmechanismused—howconfidentarewethatusersarewhotheysaytheyareWhat.
Thedevicetype,itscontrolcapabilities,ourabilitytovalidatethosecontrols,andtheextenttowhichIntelITmanagesthedevice.
Where.
Theuser'sorservice'slocation.
Forexample,auserwhoisinsidetheIntelenterprisenetworkismoretrustedthanthesameuserconnectingthroughapublicnetwork.
Theremayalsobeotherconsiderations,suchasthegeographicalregionwheretheuserislocated.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility94DestinationScoreThisiscalculatedbasedonthesamethreefactors,buttheseareconsideredfromtheperspectiveofthedestination—theinformationthesourceistryingtoaccess:Who.
Theapplicationthatstorestherequesteddata.
Someapplicationscanenforcegreatercontrols,suchasenterpriserightsmanagement(ERM),andthereforeprovideahigherleveloftrust.
What.
Thesensitivityoftheinformationbeingrequestedandotherconsiderations,suchasourabilitytorecoveritifcompromiseoccurs.
Where.
Thesecurityzoneinwhichthedataresides.
AvailableControlsThetrustcalculationalsotakesintoaccountthesecuritycontrolsavailableforthezone.
Iftheonlycontrolsavailablearecontrolsthatsimplyblockorallowaccess,wemightdenyaccessduetolackofotheroptions.
However,ifwehaveextensivepreventativecontrolswithhighlygranularlevelsofaccess,detailedlogs,andhighlytunedsecuritymonitoring—aswellastheabilitytorecoverfromorcorrectproblems—thenwecanallowaccesswithoutcreatingadditionalrisk.
CalculatingTrustThetrustcalculationaddsthesourcescoreandthedestinationscoretoarriveataninitialtrustlevel.
Theavailablecontrolsarethenconsideredtomakeafinaldecisionaboutwhetheraccessisallowedand,ifso,how.
Thiscalculationisperformedbyalogicalentitycalledapolicydecisionpoint(PDP),whichispartoftheauthenticationinfrastructureandmakesaccesscontroldecisionsbasedonasetofpolicies.
Basedontheresultsofthiscalculation,thePDPmakesadecision,allocatingatrustlevelthatdetermineswhethertheusercanaccesstherequestedresourceandthetypeofaccessthatisallowed.
Broadly,thedecisionwillfallintooneofthefollowingcategories:AllowaccessDenyaccessAllowaccesswithlimitationsormitigationThistrustcalculationthereforeallowsustodynamicallyapplygranularcontroloveraccesstospecificresources.
Forexample,employeesusingIT-manageddeviceswithadditionalhardwarefeaturessuchasatrustedplatformmodule(TPM),globalpositioningsystem(GPS),andfulldiskencryptionwouldbeallowedaccesstomoreresourcesthanwhenusingdevicesthatlackthosefeatures.
EmployeesdirectlyconnectedtotheIntelnetworktypicallygetgreateraccessthanwhenusingapublicnetwork.
Ifweareunabletoverifythelocationofahigh-securitydevicesuchasamanagedPC,wewouldallowlessaccess.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility95Thetrustcalculationalsocanbeusedformorefine-graineddistinctionsbetweendifferentdevicemodels.
Forexample,wecouldprovidedifferentlevelsofaccessbasedonsmartphonemanageability,hardware-enabledauthenticationandencryption,andinstalledapplications.
Weanticipatesituationsinwhichthetrustlevelisnotadequatetoallowanyaccess,butthereisstillabusinessrequirementtoallowaconnectionortransactiontooccur.
Intheseconditions,theresultofthetrustcalculationcouldbeadecisiontoallowaccesswithlimitationsorwithcompensatingcontrolsthatmitigatetherisk.
Forexample,ausermightbeallowedread-onlyaccessormightbepermittedaccessonlyifadditionalmonitoringcontrolsareinplace.
We'reimplementingthistrustcalculationacrossIntel'senvironment.
Today,thetrustcalculationmakesdecisionsbasedoninformationgatheredfromcomponentsatmultiplelevelsoftheinfrastructure,suchasnetworkgateways,accesspoints,anduserdevices.
Oncethetrustcalculationmechanismisinplace,wecanextendittoincludeinformationfromabroaderrangeofsources.
Forexample,thecalculationmighttakeintoaccountthelevelofhardware-enforcedsecurityfeaturesbuiltintotheuser'sdevice.
Thiswouldallowustoprovidegreateraccesstouserswhohavemore-trusteddevices.
Thetrustcalculationcanbeusedtodetermineaccesstointernalsystemsbybusinesspartnersaswellasemployees.
Let'ssaywe'recollaboratingwithanothercompanyonthedesignofanewproduct.
Anengineeratthatcompanywantsaccesstoaspecificdocument.
Wecanaddavarietyofcriteriatothetrustcalculationfordecidingwhethertograntaccess.
Didtheengineer'srequestoriginatewithinthebusinesspartner'senterprisenetworkIsitconsistentwiththetypeofrequestthatwe'dexpectfromanengineerIfso,wehaveahigherleveloftrustintherequestor.
Ifwecannotestablishanadequateleveloftrustintheuser'sdevice,butotherfactorsprovideenoughconfidencetograntaccess,wemightprovideone-timeaccessforaspecificjob.
Wecoulddothisbyallowingadocumenttobedownloaded,butonlywithinacontainerthatensuresthedocumentiscompletelyremovedfromtheuser'sdeviceoncethejobiscompleted.
Longerterm,thetrustcalculationcouldbecomeamechanismthatisusedtodetermineaccesstobothinternalandexternalresources.
IntelIT,likemanycompanies,isusingsomeexternalcloud-basedapplications,whiledevelopinganinternalprivatecloudformostapplications.
Inthefuture,weanticipategreateruseofahybrid-cloudapproach.
Thetrustcalculationcouldbeusedtomanageidentityandaccessforboth.
SecurityZonesThearchitecturedividestheITenvironmentintomultiplesecurityzones.
Theserangefromuntrustedzonesthatprovideaccesstolessvaluabledataandlessimportantsystemstotrustedzonescontainingcriticaldataandresources.
Becausethehigher-trustzonescontainmorevaluableassets,theyareprotectedwithagreaterdepthandrangeofcontrols,andwerestrictaccesstofewertypesofdevicesandapplications,asshowninFigure7-2.
However,devicesallowedaccesstohigher-trustzonesalsohavemorepower—theymaybeabletoperformactionsthatarenotallowedwithinlower-trustzones,suchascreatingormodifyingenterprisedata.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility96Aligningtheinfrastructureinthisfashionprovidesanexcellentwaytoright-sizesecuritycontrolssothatsecurityresourcesareutilizedeffectively.
Italsohelpsimprovetheuserexperiencebyenablingemployeestochoosefromawiderrangeofdevices,suchassmartphones,forlower-riskactivities.
Accesstozonesisdeterminedbytheresultsofthetrustcalculationandiscontrolledbypolicyenforcementpoints(PEPs).
PEPsmayincludearangeofcontrols,includingfirewalls,applicationproxies,intrusiondetectionandpreventionsystems,authenticationsystems,andloggingsystems.
Communicationbetweenzonesistightlyrestricted,monitored,andcontrolled.
WeseparatezonesbylocatingthemondifferentphysicalorvirtualLANs;PEPscontrolcommunicationbetweenzones.
Thismeansthatifonezoneiscompromised,wecanpreventtheproblemfromspreadingtootherzonesorincreaseourchancesofdetectionifitdoesspread.
Inaddition,wecanusePEPcontrols,suchasapplicationproxies,toprovidedevicesandapplicationsinlower-trustzoneswithlimited,controlledaccesstospecificresourcesinhigher-trustzoneswhenrequired.
Thearchitectureincludesthreeprimarycategoriesofsecurityzone:untrusted,selective,andtrusted.
Withinthezones,therearemultiplesubzones.
UntrustedZonesThesezoneshostdataandservices(ortheinterfacestothem)thatcanbeexposedtountrustedentities.
Thisallowsustoprovidewidespreadaccesstoalimitedsetofresourcesfromnon-managedconsumerdevices,withoutincreasingtherisktohigher-valueresourceslocatedinotherzones.
Untrustedzonesmightprovideaccesstoenterpriseresources,suchascorporatee-mailandcalendars,ortheymightsimplyprovideInternetaccess.
Figure7-2.
Asthevalueofanassetincreases,thedepthandspanofcontrolsincrease,whilethenumberofalloweddevices,applications,andlocationsdecrease.
Source:IntelCorporation,2012Chapter7ANewSecurityArchitecturetoImproveBusinessAgility97Thesezonesareregardedas"sharktanks,"withahighriskofattackandcompromise.
Therefore,detectiveandcorrectivecontrolsareneededtomitigatethisrisk.
Thesecontrolsmightincludeahighlevelofmonitoringtodetectsuspectactivityandcorrectioncapabilitiessuchasdynamicremovalofuserprivilege.
Weanticipateaneedtoprovidecontrolledaccessfromthesezonestoresourcesinhigher-trustzones.
Forexample,anemployeeusinganuntrusteddevicemightbeallowedlimited,read-onlyaccesstocustomerdatalocatedinatrustedzone;ortheirdevicemightneedaccesstoadirectoryserverinatrustedzonetosende-mail.
Weexpecttoprovidethiscontrolledaccessusingapplicationproxies.
Theseproxiesactassecureintermediaries—evaluatingtherequestfromthedevice,gatheringtheinformationfromtheresourceinatrustedzone,andpassingittothedevice.
SelectiveZonesSelectivezonesprovidemoreprotectionthanuntrustedzones.
Examplesofservicesinthesezonesincludeapplicationsanddataaccessedbycontractors,businesspartners,andemployees,usingclientdevicesthataremanagedorotherwiseprovidealeveloftrust.
Selectivezonesdonotcontaincriticaldataorhigh-valueIntelintellectualproperty.
Severalselectivesubzonesprovideaccesstodifferentservicesorusers.
TrustedZonesTrustedzoneshostcriticalservices,data,andinfrastructure.
Theyarehighlysecuredandlockeddown.
Examplesofserviceswithinthesezonesareadministrativeaccesstodatacenterserversandnetworkinfrastructure,factorynetworksanddevices,enterpriseresourceplanning(ERP)applications,anddesignengineeringsystemscontainingintellectualproperty.
Accordingly,wemightonlyallowdirectaccesstotheseresourcesfromtrustedsystemslocatedwithintheenterprisenetwork,andallaccesswouldbemonitoredcloselytodetectanomalousbehavior.
AtIntel,wehaveimplementedsecurehigh-trustzonesaspartofourtransitiontoanenterpriseprivatecloud.
Implementingthesezoneswasakeystepinallowingustomoveseveralcategoriesofapplicationontovirtualizedcloudinfrastructure,includinginternalapplicationsrequiringhighsecurity,aswellasexternallyfacingapplicationsusedtocommunicatewithbusinesspartners.
Thesecurityfeaturesinthesetrustedzonesincludeapplicationhardeningandincreasedmonitoring.
Wecontinuetoaddfurthersecuritycapabilitiesovertime.
NEWSECURITYARCHITECTUREINACTION:ADAYINTHELIFEOFANEMPLOYEEThisexample(illustratedinFigure7-3)describeshowthenewsecurityarchitectureenablestheIntelsalesforcetoaccesstheinformationtheyneedinthecourseofaday.
Atthesametime,thearchitectureprotectsIntel'ssecuritybydynamicallyadjustingthelevelofaccessprovided,basedontheuser'sdeviceandlocation,andbymonitoringforanomalousbehavior.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility98Theemployeetravelstoacustomersite.
Theemployeeisusingapersonalsmartphonewithlimitedsecurityfeaturesandsoisallowedaccessonlytoservicesinuntrustedzones.
Fromhere,theemployeecanviewlimitedcustomerinformation,includingrecentorders,extractedfromanenterpriseresourceplanning(ERP)systeminatrustedzone—butonlythroughanapplicationproxyserver,whichprotectsthetrustedzonebyactingasanintermediary,evaluatinginformationrequests,accessingtheERPsystem,andrelayingtheinformationtotheuser.
Ifasmartphonerequestsanabnormallylargenumberofcustomerrecords—anindicationthatitmayhavebeenstolen—furtheraccessfromthesmartphoneisblocked.
Tohelpunderstandthereasonfortheanomalousaccess,thereisincreasedmonitoringoftheemployee'sattemptstoaccessthesystemfromanydevice.
Theemployeereachesthecustomersiteandlogsintotheenterprisenetworkfromacompany-ownedmobilebusinessPC.
Becausethisdeviceismoretrusted,theemployeenowhasaccesstoadditionalcapabilitiesavailableinselectivezones,suchastheabilitytoviewpricingandcreateordersthatarerelayedbyanapplicationproxytotheERPsysteminatrustedzone.
Figure7-3.
Thenewsecurityarchitecturedynamicallyadjuststheuser'saccesstoinformation,basedonfactorssuchastheuser'sdeviceandlocation.
Source:IntelCorporation,2012Chapter7ANewSecurityArchitecturetoImproveBusinessAgility99Theemployeereturnstothecompany'sofficeandconnectstothecorporatenetwork.
NowtheemployeeisusingatrusteddevicefromatrustedlocationandhasdirectaccesstotheERPsysteminatrustedzone.
BalancedControlsOverthepastdecade,enterprisesecurityhasfocusedheavilyonpreventativecontrolssuchasfirewallsandintrusionpreventionsystems.
Thisapproachoffersclearbenefits:itislessexpensivetopreventanattackthantocorrectproblemsafteronehasoccurred,anditiseasytoseewhenfirewallshavesuccessfullypreventedanattemptedcompromise.
However,thenewsecuritymodelrequiresthatwebalancepreventativecontrolswithdetective(monitoring)andcorrectivecontrols,forseveralreasons.
First,thefocusofthenewmodelisonenablingandcontrollingaccessfromawiderrangeofusersanddevices,ratherthanonpreventingaccess.
Second,thecontinuallychangingthreatlandscapemakesitnecessarytoassumethatcompromisewilloccur;allpreventativecontrolswilleventuallyfail.
Onceattackershavegainedaccesstotheenvironment,thepreventativecontrolstheyhavebypassedareworthless.
Byincreasingtheuseofdetectivecontrolsandimplementingmoreaggressivecorrectivecontrols,wecanmitigatetheriskofallowingbroaderaccess.
Thesecontrolsalsoincreaseourabilitytosurviveandrecoverfromasuccessfulattack.
USINGSECURITYBUSINESSINTELLIGENCETODETECTSUSPICIOUSBEHAVIORLikeanylargeorganization,Intelhasexperiencedsecurityissuesinvolvingbothexternalattackersandinsiders,includingattemptstostealintellectualproperty.
Aswe'veinvestigated,wehaveidentifiedmarkersandindicatorsthatarefrequentlyassociatedwiththeseevents.
Werealizedthatifwehadbeenabletospottheseindicatorssooner,wecouldhaverespondedandmitigatedthethreatsmorequickly.
Securitybusinessintelligenceisakeytechnologythatwecanusetodetectsuspiciousbehaviorastheenvironmentbecomesmorecomplexandattackersbecomemoreadeptatconcealingcompromises.
Analyticaltoolsautomatetheprocessofanalyzinglargevolumesofdatatodetectandmonitoranomalousactivity,allowingustodetectproblemsthatwemightotherwisemiss.
Thesecapabilitiesaresimilartothosealreadyimplementedbyfinancialinstitutionstopreventfraudulentcredit-cardtransactions,andbyonlineconsumerservicestopreventtheftofuserdata.
Banksmonitoraccessattemptsandonlinetransactionstodeterminewhethertotrusttheuser'sidentityandwhethertoallowtheuser'sactivity.
Iftheuseristryingtotransferalargesumtoanexternalaccount,thebank'ssystemsmaycomparethetransactionwiththeuser'spreviousbehaviortoseeifitappearstobeabnormal.
Tomitigaterisk,thebankmaydelaylargetransferssoitcanperformadditionalanalysisandinformtheaccountownerbye-mail.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility100Inasimilarway,wecanusesecuritybusinessintelligence—analysisandcorrelationofdatagatheredbymonitoring—toanalyzepatternsofbehavior.
Thiscandetectandthwartpossibleattacks.
Onalargescale,loggingdatageneratedbyserversandsensorsacrossthenetworkcanbecollectedintoadatabaseforanalysis.
AtIntel,weareusinganalytictoolstocorrelatethisaggregateddataandflaganomaliesforfurtherinvestigation.
Forexample,iftrafficwithinaserverclusterbecomesabnormallyhigh,itmightindicatethatabotnetisexploitingoneoftheserverstobroadcasttrafficacrosstheWeb.
Securitybusinessintelligencecanalsobeappliedatthelevelofindividualusersanddevices.
AtIntel,we'reimplementingmonitoringtechnologythattracksusers'loginsandaccessattempts,asIdescribedinChapter5.
Ourstrategyistomakelogininformationavailabletouserssothattheycanhelptospotunauthorizedaccessattempts.
Inthefuture,Ienvisagethatthesystemcouldanalyzeusers'historicalbehaviorpatternstodeterminehowtorespondwhenusersrequestaccesstoresources.
Thesystemcouldcomparetherequestwiththeuser'spreviousactions:whathaveyoudonebefore,andisthisrequestconsistentwiththosebehaviorsorisitananomalyandthereforesuspiciousIftherequestappearsconsistentwithpreviousbehavior,thesystemwouldpasstherequesttothetrustcalculation;ifitappearsanomalous,thesystemmightdenytherequestandalertthesecurityteam.
WithinIntel,wehavealsodeployedadashboardthatprovidesgranularinformationaboutinfectedclientsandservers,boostingourabilitytointervenequicklyandaccurately.
Duetooureffortstodetectandremovemalwarebeforeinfectionsoccur,weachieveda33percentreductioninmalwareimpactsin2011,despiteexperiencinga50percentincreaseinthenumberofvariants(Intel2012a).
Wealsoplantoaddapredictiveenginethatenablesproactiveprotectionandsimulationsthatcanimproveourabilitytorespondtothreats.
Thebalancebetweenpreventative,detective,andcorrectivecontrolswillvary,dependingonthesecurityzone.
Inhigh-trustzones,weimplementextensivemonitoringtodetectpossibleattemptstostealdataorcompromisecriticalsystems.
Redundancywithineachtypeofcontrolcanbeusedtoprovideadditionalprotection.
Thefollowingincludespossibleexamplesofusingdetectiveandpreventativecontrols:AnIntelemployeeattemptstosendaconfidentialdocumenttoanon-Intele-mailaddress.
Monitoringsoftwaredetectstheattempt,preventsthedocumentfrombeingsentoutsidethefirewall,andaskstheIntelemployeeifheorshereallyintendedtodothis.
Iftheemployeeconfirmsthatthiswasintended,thedocumentmaybetransmitted—orifthedocumentishighlysensitive,aredactedversionmaybesent.
Chapter7ANewSecurityArchitecturetoImproveBusinessAgility101Inappropriateuseofadocumentprotectedwithenterpriserightsmanagementtechnologyresultsinrevocationofaccesstothedocument.
Thesystemallowsaccesstospecificdocumentsbuttrackstheactivity.
Ausercandownloadafewdocumentswithoutcausingconcerns.
However,iftheuserattemptstodownloadhundredsofdocuments,thesystemslowsdownthespeedofdelivery(forinstance,onlyallowingtentobecheckedoutatatime)andalertstheuser'smanager.
Ifthemanagerapproves,theuserisgivenfasteraccess.
Thedetectionofaninfectedsystemplacesthesystemonaremediationnetwork,isolatingthesystemandrestrictingaccesstoenterpriseinformationandapplications.
Thesystemmayretainsomeabilitytoaccesscorporateassets,butallactivityiscloselyloggedtoenableincidentresponseifnecessary.
Whenasystemisfoundtobecompromised,weexamineallitsrecentactivitiesandinteractionswithothersystems.
Additionalmonitoringofthosesystemsisautomaticallyenabled.
UsersandData:TheNewPerimetersTheconceptofbalancedcontrolsalsoextendstotheprotectionofusersanddata.
Traditionalnetworksecurityboundariesaredissolvingwiththeproliferationofnewdevicesandusers'expectationsthattheyshouldbeabletoaccessinformationfromanywhereatanytime.
Usersareunderdirectassaultfromabarrageofattacksdesignedtotrickthemintotakingactionsthatcancompromisetheinformationontheirdevicesoronenterprisesystems.
Thesetrendsmeanthatweneedtothinkmorebroadlyabouthowweprotectinformation,aswellastheusersofthisinformation.
Whilewecontinuetoimplemententerprisenetworkcontrols,suchasperimeterdefensesandthedetectivecontrolsdescribedearlier,weneedtosupplementthesecontrolswithafocusontheusersandontheprimaryassetswearetryingtoprotectsuchasintellectualproperty.
Thenewarchitecturethereforeexpandsourdefensestotwoadditionalperimeters:thedataitselfandtheuserswhohaveaccesstothedata.
DataPerimeterImportantdatashouldbeprotectedatalltimes—whenitiscreated,stored,andtransmitted.
Thisbecomesincreasinglychallengingaswemovedatatomoreandmoredevicesandletmorepeopleaccessit.
Howdoweprotectinformationwhenit'slocatedoutsidethephysicalperimeteronapersonaldeviceAtIntelIT,we'reimplementingtechnologiesthatcloselyintegrateprotectionwithhigh-valuedatasothatthedataremainsprotectedasitmovestodifferentdevicesandlocations.
Technologies,suchasenterpriserightsmanagementanddataleakprevention,canbeusedtowatermarkandtaginformationsothatwecantrackandmanageitsuse.
Withenterpriserightsmanagement,thecreatorofadocumentcandefineexactlywhoChapter7ANewSecurityArchitecturetoImproveBusinessAgility102hasaccessrightsthroughoutthelifeofthedocumentandcanrevokeaccessatanypoint.
Datalosspreventionisusedtotagdocuments,tracktheirmovements,andpreventtransferoutsidetheorganizationifnecessary.
UserPerimeterAsIdescribedinChapter5,peoplearepartofthesecurityperimeter,andweneedtotreatthemassuch.
Userscanbecomesecurityrisksforavarietyofreasons.
Theyaretargetedmorefrequentlyinsocialengineeringattacks,andtheyaremorevulnerabletotheseattacksbecausetheirpersonalinformationisoftenreadilyavailableonsocialnetworkingsites.
Theymayalsoclickmaliciouslinksine-mail,downloadmalware,orstoredataonportabledevicesthatthenarelost.
AtIntel,we'vefoundthatacombinationoftraining,incentives,andotheractivitiescanhelpinstillinformationsecurityandprivacyprotectionintothecorporatecultureandsuccessfullyencouragesemployeestoownresponsibilityforprotectingenterpriseandpersonalinformation.
We'veseenoureffortspayoff,withemployeescallingthehelpdeskorsendinge-mailalertswhentheynoticesomethingthatdoesn'tseemright.
Asdiscussedinthesidebar("UsingSecurityBusinessIntelligencetoDetectSuspiciousBehavior"),ourstrategyalsoincludesmakingaccountaccesslogsavailabletouserssothattheycanhelpspotunauthorizedaccessattempts.
ConclusionThischapterdescribesanewarchitecturedesignedtosupporttheProtecttoEnablemission.
Itsgoalistoallowfasteradoptionofnewservicesandcapabilitieswhileimprovingsurvivability.
AtIntel,webelievethatthisarchitecturecanbeusedtomeetabroadrangeofevolvingrequirements,includingnewusagemodelsandthreats.
Becauseofthis,weareworkingtoingrainthismodelintoallaspectsofIntelIT,fromdevelopmenttooperations.
We'vealreadyusedaspectsofthearchitecturetoprovidesolutionstochallengingusecases,whileactuallyreducingrisk.
Forexample,we'vebeenabletomoveimportantinternalandInternet-facingapplicationstoaprivatecloudbyutilizinghigh-trustzones.
We'vesuccessfullyusedvariousapproachestoprotecttheuseranddataperimeters.
Wealsousedbalancedcontrolsandtrustzonestoenablenetworkaccessfromemployee-owneddevices.
Insomecases,projectshaveseentheirsecurityoverheaddecreasebyadoptingthismodel.
Ibelievethatthearchitecturecouldprovidesimilarvaluetootherorganizationsfacingsimilarchallenges.
Bypublishinginformationaboutthearchitecture,wehopetoencourageotherstotakeadvantageofthisarchitecturewhereveritmeetstheirneeds.
Wealsohopethatmakingthisinformationavailablewillstimulatemorediscussionandideas,andthatotherswillbuildontheseconceptstocreatefurtherinnovationsthatbenefitallofus.
- typespartnersonline相关文档
- varietypartnersonline
- shallowpartnersonline
- playerspartnersonline
- responsepartnersonline
- previouspartnersonline
- characteristicspartnersonline
spinservers:圣何塞10Gbps带宽服务器月付$109起,可升级1Gbps无限流量
spinservers是Majestic Hosting Solutions LLC旗下站点,主营国外服务器租用和Hybrid Dedicated等,数据中心在美国达拉斯和圣何塞机房。目前,商家针对圣何塞部分独立服务器进行促销优惠,使用优惠码后Dual Intel Xeon E5-2650L V3(24核48线程)+64GB内存服务器每月仅109美元起,提供10Gbps端口带宽,可以升级至1Gbp...

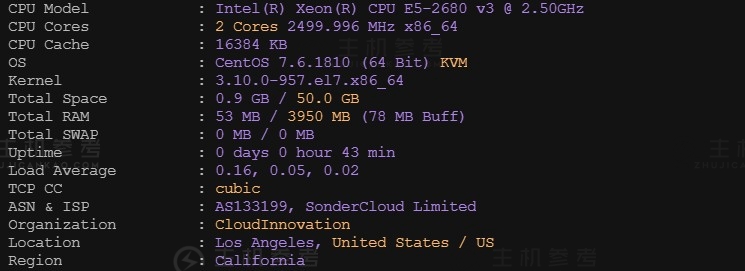
恒创科技SonderCloud,美国VPS综合性能测评报告,美国洛杉矶机房,CN2+BGP优质线路,2核4G内存10Mbps带宽,适用于稳定建站业务需求
最近主机参考拿到了一台恒创科技的美国VPS云服务器测试机器,那具体恒创科技美国云服务器性能到底怎么样呢?主机参考进行了一番VPS测评,大家可以参考一下,总体来说还是非常不错的,是值得购买的。非常适用于稳定建站业务需求。恒创科技服务器怎么样?恒创科技服务器好不好?henghost怎么样?henghost值不值得购买?SonderCloud服务器好不好?恒创科技henghost值不值得购买?恒创科技是...
iON Cloud:新加坡cn2 gia vps/1核/2G内存/25G SSD/250G流量/10M带宽,$35/月
iON Cloud怎么样?iON Cloud升级了新加坡CN2 VPS的带宽和流量最低配的原先带宽5M现在升级为10M,流量也从原先的150G升级为250G。注意,流量也仅计算出站方向。iON Cloud是Krypt旗下的云服务器品牌,成立于2019年,是美国老牌机房(1998~)krypt旗下的VPS云服务器品牌,主打国外VPS云服务器业务,均采用KVM架构,整体性能配置较高,云服务器产品质量靠...
partnersonline为你推荐
-
京沪高铁上市首秀京沪高铁怎么老是出问题?高铁的核心技术是中国自己的吗?特朗普取消访问丹麦特朗普专机抵达日本安保警力情形如何?微信回应封杀钉钉微信发过来的钉钉链接打不开?中老铁路中国有哪些正在修的铁路原代码求数字代码大全?罗伦佐娜米开朗琪罗简介月神谭求古典武侠类的变身小说~!haole018.comhttp://www.haoledy.com/view/32092.html 轩辕剑天之痕11、12集在线观看ip在线查询通过对方的IP地址怎么样找到他的详细地址?m.2828dy.com电影虫www.dyctv.com这个电影站能下载电影吗?