fullybtio.pw
btio.pw 时间:2021-04-09 阅读:()
PwningAdobeReaderAbusingtheReader'sembeddedXFAengineforreliableExploitationSebastianApeltsebastian.
apelt@siberas.
de2016/04/08siberas2016|2/65whoamiMotivation(Short!
)IntroductiontoXFAXFAInternalsXFAObjectsjfCacheManagerExploitingtheReaderDemoConclusionQ&AAgendasiberas2016|3/65SebastianApelt(@bitshifter123)Co-Founderofsiberasin2009IT-SecurityConsulting(Pentests,CodeAudits,etc.
)ResearchLow-leveladdictReverseEngineering,Bughunting,Exploitation>100CVEsinallkindsofProductsPwn2Own2014(IE11onWin8.
1x64)whoamisiberas2016|4/65Motivationsiberas2016|5/65FuzzingatsiberasLet'spwntheReader@Pwn2Own2016!
!
Unfortunately,noloveforReaderthistimeIn2015:XFAfuzzingon128coresFuzzrunyieldedthousandsofcrashesSofar~20Bugsidentifiedasunique(upcoming)Analysistookages…Let'stakealookatatypicalReadercrash!
Motivationsiberas2016|6/650:000>!
heap-p-aecxaddress07b2f3ccfoundin_HEAP@11a0000HEAP_ENTRYSizePrevFlagsUserPtrUserSize-state07b24eb0199c0000[00]07b24eb80ccd8-(busy)(72fc.
72ec):Accessviolation-codec0000005(!
!
!
secondchance!
!
!
)eax=69572c30ebx=00000002ecx=07b2f3ccedx=05658af8esi=0549e538edi=07b2f3cceip=20a29654esp=0031d8c4ebp=00000003iopl=0nvupeiplnznacs=0023ss=002bds=002bes=002bfs=0053gs=002befl=00210206AcroForm!
DllUnregisterServer+0x2f73ce:20a29654movedx,dwordptr[eax]ds:002b:69572c30=MotivationAwesome,wehaveacrash!
Butnousefulfunctionname(DllUnregisterServer)Theobjectholdingthebadreferenceislocatedinthemiddleofahugebuffer=>PageHeapuselessStacktracealsonothelpfulOffset0xa514!
0:000>kcAcroForm!
DllUnregisterServer+0x2f73ceAcroForm!
DllUnregisterServer+0x2f7212AcroForm!
DllUnregisterServer+0x2f7504AcroForm!
DllUnregisterServer+0x35f3aeAcroForm!
DllUnregisterServer+0x358f50siberas2016|7/65AdobeReader=>Nosymbols/RTTIinfos!
NofunctionnamesNoobject/vtableinformationNomeaningfulstacktracesPageHeapuselessRootcauseanalysisisveryhardwithoutcontextComplicatescrashtriagingduringfuzzrunsMotivationsiberas2016|8/65HowdoweANALYZEcrashesinXFAHowdoweEXPLOITthesecrashesObvious:Weneedcontext!
Weneedsymbols!
Noin-depthresearchaboutXFAinternalssofar:Mostuseful:WriteupsaboutXFAexploitfrom2013(DavidandEnriqueofImmunityInc,MatthieuBonettiofPortcullisLabs)Goodtechnicalanalysis,butonlyscratchingthesurfaceMotivationsiberas2016|9/65WritetoolstorecovercontextualinformationLowerthebarforotherresearchers!
Checkhttps://github.
com/siberasinthenextdaysFacilitate:VulnerabilitydiscoveryandrootcauseanalysisCrashtriagingduringfuzzrunsDeliverXFA-specificbackgroundforexploitationMotivationsiberas2016|10/65(Short!
)IntroductiontoXFAsiberas2016|11/65XFA:XMLFormsArchitecture"SpecificationdevelopedbyJetForm,laterAccelio(acquiredbyAdobein2002)–notastandardLatestversion:3.
3(01/2012):Easyreadof1584pages.
BringsdynamicbehaviortothestaticPDFworld:Formsthatcandynamicallychangetheirlayout!
DynamicnatureofXFAispoweredbyJavascript(Spidermonkey24sinceARDC)XFAnotsupportedbymanyPDFReaders,yet(Chrome/Chromium,Firefox,Windows,.
.
.
)(Short!
)IntroductiontoXFAsiberas2016|12/65XFAformdataitselfisanXML-structureembeddedinthePDF,aso-calledXDP-PacketJavascriptembeddedinthisXDPExecuteduponevents(e.
g.
documentisfullyloaded,userclicksonbutton,etc.
)Apracticalexample…(Short!
)IntroductiontoXFAsiberas2016|13/65[…][…]app.
alert(1337);[…](Short!
)IntroductiontoXFAXDPPacketisXMLembeddedinthePDFTheroottagisalwaysxdp"ConfigDOMcontainsconfigurationoptionsforXFAprocessingTemplateDOMisstructuredinsubforms,containingobjectslikefield",text",etc.
Objectscancontaineventobjectsthatfireoncertainactions(e.
g.
click")siberas2016|14/65XFAspecdefinesmultipleDOMsHUGEattacksurface(>200objectsaccessibleviaJS)(Short!
)IntroductiontoXFAtemplateConfigurationOptionsTplDOM:ObjectswhichwillbevisibleinthePDFXML-DatathatcanbeusedtopopulatefieldsinthePDFTemplateandDataaremergedintoFormDOMLayoutDOMmakeslayoutinformationaccessiblexdpconfigdataSetsformlayoutxdcdataDescDevice-specificinformationsourceSetdataDescriptionDOM:DataschemaDOMforDB-/WebService-Connectionssiberas2016|15/65XFAInternalssiberas2016|16/65Tweetby@nilsNice!
SomeSolarisbuildseemstohavesymbols!
Newestversionwhichstillhassymbols:Solarisv9.
4.
1WeneedareliableheuristictoportsymbolsinAcroForm.
api(modulewhichimplementsXFAfunctionality)tonewerARversionsXFAInternals-GeneralApproachsiberas2016|17/65Problems:Codeisratherold(2012)->ManyCodechangesfromv9.
XtoARDC…Functioncount:Solaris~48K,ARDC~95KFunctionsdifferevenifcodestaysthesame(compileroptimizationslikeheavyinlininginv9.
4.
1screwitup)TrieddiffingwithDiaphora–ToomanyfalsepositivesStructures,objectsandvtablesizesdiffer(slightly,butenoughtomakeitveryhardtocreatereliableheuristics)etc.
XFAInternals-GeneralApproachsiberas2016|18/65Approach:TryingtounderstandReaderv9.
4.
1asmuchaspossiblewiththehelpofsymbolsFindbulletproofwaystorecoverthemostimportantsymbols,i.
e.
HeapMgmtfunctionsforthecustomallocatorObjectinformationXFAInternals-GeneralApproachsiberas2016|19/65WhatdoweneedtoknowaboutobjectsHowtoidentifyanobjectinmemoryVtableoffsetsMethodsandpropertiesexposedtoJavaScriptOffsetsoftheentrypointsformethods/property-gettersand-settersFunctionnamesofvtableentriesXFAInternals-Objectssiberas2016|20/65Firstattempt:XFANode::getClassTagFail!
classTagsnotconstantacrossversions!
XFAInternals-Objects:IdentificationFromFieldconstructormethod:classTagforField-ObjectinAdobeReader9.
4.
1:0x86classTagattributecanbefound@+0x10classTagforField-ObjectinAcrobatReaderDC:0x8esiberas2016|21/65::TypemethodtotherescueLocated@vtable+8ofeachXFA-ObjectType-IDsarestaticacrossversions!
XFAInternals-Objects:IdentificationTypeis0x7C46forbothv9.
4.
1ANDAcrobatReaderDC!
AdobeReader9.
4.
1AcrobatReaderDCsiberas2016|22/65PossibletoidentifyeveryobjectbyabinarypatterninnewerversionsofAcroForm.
apimoveax,7C46hretnB8467C0000C3XreftotheTypemethodgivesusthevtableoffset(RVA)toeachobject!
XFAInternals-Objects:IdentificationWecansafelyidentify334objects!
Nottoobad!
siberas2016|23/65WhatdoweneedtoknowaboutobjectsHowtoidentifyanobjectinmemoryVtableoffsetsMethodsandpropertiesexposedtoJavaScriptOffsetsoftheentrypointsformethods/property-gettersand-settersFunctionnamesofvtableentriesXFAInternals-Objectssiberas2016|24/65Howaboutmethodsandproperties::getScriptTable()@vtableoffset0x34ReferencesmoScriptTablestructureStructurecontainsinformationaboutmethodandpropertynames,functionpointers,etc.
XFAInternals-ObjectsXFAFieldImpl::moScriptTablesiberas2016|25/65XFAInternals-ObjectsXFAContainerImpl::moScriptTable&field"Property-TableMethod-TableXFAObjectImpl::moScriptTable&tree"Property-TableMethod-TableXFANodeImpl::moScriptTable&container"Property-TableMethod-TableXFATreeImpl::moScriptTable&node"Property-TableMethod-Table0x00000000&object"Property-TableMethod-TablePtr1toproperty-structPtr2toproperty-struct0x00000000Ptr1tomethod-structPtr2tomethod-struct0x00000000&rawValue"func-ptrsetterfunc-ptrgetter&addItem"func-ptraddItemXFAFieldImpl::moScriptTablesiberas2016|26/65WhatdoweneedtoknowaboutobjectsHowtoidentifyanobjectinmemoryVtableoffsetsMethodsandpropertiesexposedtoJavaScriptOffsetsoftheentrypointsformethods/property-gettersand-settersFunctionnamesofvtableentriesXFAInternals-ObjectsTODO…Nottrivial…;-(siberas2016|27/65MostallocationsinAcroForm.
apiaremanagedbyacustomallocatorcalledjfCacheManagerLIFO-styleheapmanagerDatabuffers(blocks")storedinbigheapchunks"IntroducedmostlikelyforperformancereasonsNosecurityfeatures…NoHeapIsolation(seeIE,Flash,etc.
)NoAnti-UAFlikeMemProtect/MemGC…XFAInternals-jfCacheManagersiberas2016|28/65Disclaimer:Nextslideswillonlycovertherelevantdetailsofthememorymanagerintermsofexploitation!
(Morein-depthanalysiswillbecoveredbyapaperwhichwillbereleasedsoon)XFAInternals-jfCacheManagersiberas2016|29/65VerysimplifiedversionofthejfCacheManager:XFAInternals-jfCacheManagerAllocatorstructures:jfCacheManagerjfMemoryCacheListjfMemoryCacheBBBB"AAAAA…"Chunk"(bigcontainer)Block"(smalldatabuffers)sizeXsizeYsiberas2016|30/65XFAInternals-jfCacheManagerStorageofallocationsofsize=0x100[…]0x18jfMemoryCacheList*size0x1jfMemoryCacheList*size0x2[…]jfMemoryCacheList*size0xFF0x418-0x434.
[…]jfCacheManager0x100entriesArrayofjfMemoryCache*jfMemCache*jfMemCache*jfMemCache*jfMemCache*[…][…]ArrayofjfMemoryCache*ArrayofjfMemoryCache*CHUNK(BLOCK-SIZE0x1)jfMemoryCachejfMemoryCachejfMemoryCachejfMemoryCacheCHUNK(BLOCK-SIZE0x1)CHUNK(BLOCK-SIZE0x2)CHUNK(BLOCK-SIZE0xFF)jfMemCacheListjfMemCacheListjfMemoryCacheandthechunkswillberelevantforexploitation!
siberas2016|31/65sizeof(chunk)derivedfromblocksize:Example:allocationsize=0x64=>chunksize=26*(0xc3b3/0x64)*4=0xcb20So,ifIgetacrashandIseemyobjectlocatedinachunkofsize0xcb20,thensizeof(obj)==0x64"Unfortunatelynot…base_size=0xc350//50.
000chunksize=((((size+3)/4)+1)*((base_size+size-1)/size))*4XFAInternals-jfCacheManagersiberas2016|32/65jfMemoryCacheListscanmanageblocksofmultiplesizes=>blocksofsizesXandYcanbothendupinchunkZ!
alloc(X)willbeplacedinsamechunkasalloc(Y)ifanallocationforasizeY>XhasoccuredbeforeandsizeXisinthesamerange"assizeYRangesreachfrom2nto(2n+1-1)(e.
g.
0x20-0x3f,0x40-0x7f)Inshort:DoesthenewblockfitintosomechunkthatwealreadyhaveIfyes,usethatchunkinsteadofallocatinganewone!
XFAInternals-jfCacheManagersiberas2016|33/65XFAInternals-jfCacheManager0x0vtable[…]0x8PtrtoAllocs>=0x100[…]0x18jfMemoryCacheList*size0x1[…]0x138[…]0x1a8jfMemoryCacheList*size0x64[…]jfMemoryCacheList*size0xFF0x418-0x434.
[…]jfCacheManagerArrayofjfMemoryCache*jfMemoryCachejfMemCacheListObjectX(size0x64)ObjectY(size0x48)StringoflengthZ(size0x64)Objectofsize0x48fitsintochunkwithblocksize0x64jfMemoryCacheList*size0x48siberas2016|34/65Let'stakealookatthestructureswithinthechunksandwhathappensduringalloc/freeoperations…XFAInternals-jfCacheManagersiberas2016|35/650x0blocksize=0x100x4max_entries[…]0xcchunk**[…]0x1Calloc_count=00x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00flink0x10flink0x20flink0x30flink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrpointstotheblockwhichwillbereturnedwiththenextallocationflinksformasinglelinkedlistseparatingthedatablocksblockofsize0x10Initialstate–Allblocksarefreesiberas2016|36/650x0blocksize=0x100x4max_entries[…]0xcchunk**[…]0x1Calloc_count=10x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00jfMC*AAAABBBBCCCC0x10DDDDflink0x20flink0x30flink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrisoverwrittenwithflinkflinkisoverwrittenwithpointerbacktojfMemoryCacheallocs_counterisincrementedto1Afterfirstallocationsiberas2016|37/650x0blocksize=0x100x4max_entries[…]0xcchunk**[…]0x1Calloc_count=20x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00jfMC*AAAABBBBCCCC0x10DDDDjfMC*EEEEFFFF0x20GGGGHHHHflink0x30flink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrisoverwrittenwithflinkflinkisoverwrittenwithpointerbacktojfMemoryCacheallocs_counterisincrementedto2Aftersecondallocationsiberas2016|38/650x0blocksize=0x100x4max_entries[…]0xcchunk**[…]0x1Calloc_count=30x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00jfMC*AAAABBBBCCCC0x10DDDDjfMC*EEEEFFFF0x20GGGGHHHHjfMC*IIII0x30JJJJKKKKLLLLflink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrisoverwrittenwithflinkflinkisoverwrittenwithpointerbacktojfMemoryCacheallocs_counterisincrementedto3Afterthirdallocationsiberas2016|39/650x0blocksize0x4max_entries[…]0xcchunk**[…]0x1Calloc_count=20x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00jfMC*AAAABBBBCCCC0x10DDDDflink0x20jfMC*IIII0x30JJJJKKKKLLLLflink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrisoverwrittenwithpointertofreeblock-4jfMC*isoverwrittenwithnext_alloc_ptr(becomesflinkagain)allocs_counterisdecrementedto2Freesecondblocksiberas2016|40/65Stilldon'tlikethejfCacheManagerStillmissingPageHeapGetoffsetjfCacheManager_active"withXFAnalyze_funcs.
pyChangebytefrom1to0inbinaryReplaceoriginalAcroForm.
apiYoujustswitchedoffthejfCacheManager:PXFAInternals-jfCacheManagersiberas2016|41/65ExploitingtheReadersiberas2016|42/65ExploitingtheReaderUnderstandtheBugUnderstandtheHeapKnowyourCorruptionTargetsGoalsBypassASLRbycorruptingspecificbyte(s)tocauseamemoryleakFindflexible"overwritetargetNoneedforawrite-what-where(e.
g.
0-DWORDwriteorapartialoverwritetoacontrolledaddressshouldsuffice!
)Findtechniquewhichisfast,reliableandmostimportantlyindependantfromOSandARversionsiberas2016|43/65Let'stargetthemetadatacontainedwithinthechunks!
Twopossibilities:Bothmethodscanbeabusedcreateamemoryleak!
ButhittingtheflinkistheeasiestwaytogoExploitingtheReader0x00jfMC*6161616161616161616161610x1061616161flink0x20jfMC*636363630x30636363636363636363636363flink0x400x50flinkflink…………ChunkHitthejfMemoryCache*BlockisallocatedTriggerswhenblockisfreedHitaflinkBlockisfreeTriggerswhenblockisallocatedsiberas2016|44/65ExploitingtheReader-Hittheflink!
0x00flink0x10flink0x20flink…………0x0blocksize0x4max_entries[…]0xcchunk**[…]0x1C00x20next_alloc_ptr0x24jfCacheMgr*jfMemoryCacheInitialsituationThisisouroverwritetarget!
siberas2016|45/65ExploitingtheReader-Hittheflink!
0x00badflink"0x10flink0x20flink…………0x0blocksize0x4max_entries[…]0xcchunk**[…]0x1C00x20next_alloc_ptr0x24jfCacheMgr*jfMemoryCacheAfterflinkoverwriteRequirement:flinkmustpointtocontrolleddataafteroverwriteStillveryflexible:Doablewithnearlyanykindofmemcorruption!
Let'sseewhathappenswhenweallocatethebad"block0x00Attacker-ControlledData0x100x20…………siberas2016|46/650x00jfMC*AAAABBBBCCCC0x10DDDDflink0x20flink…………next_alloc_ptrisoverwrittenwiththebad"flinkflinkisoverwrittenwithpointerbacktojfMemoryCacheNowwhathappenswhenweallocateanobjectofsize0x10…ExploitingtheReader-Hittheflink!
0x0blocksize0x4max_entries[…]0xcchunk**[…]0x1C10x20next_alloc_ptr0x24jfCacheMgr*jfMemoryCache0x00flink"0x100x20…………Afterallocationofblockwithbad"flinksiberas2016|47/650x00jfMC*AAAABBBBCCCC0x10DDDDflink0x20flink…………Nextallocationwillreturnthedatabufferaftertheflink"Theobjectwillbeplacedinthemiddleofourcontrolleddata=>Wegetavtableincontrolleddata!
!
ExploitingtheReader-Hittheflink!
0x0blocksize0x4max_entries[…]0xcchunk**[…]0x1C10x20next_alloc_ptr0x24jfCacheMgr*jfMemoryCache0x00jfMC*VTABLErefcount0x100x20…………Allocateanobjectsiberas2016|48/65ExploitingtheReader-Hittheflink!
AssoonasthevtableisinacontrolledareayoucanjustreaditoutThecontrolleddataareacanbesprayedwithstringsorevenfloatarraysaslandingzone"SettheoverwrittenfloatorreplacethestringwithdatawhichwillpointtoyourROPpivotgadgetForfloats:YoucancomputetheirbinaryrepresenationafterspecIEEE754:4.
18356164518379836860971488084E-216willbe0x13371337deadc0deontheheapGAMEOVER!
siberas2016|49/65ExploitingtheReaderLet'shavealookatapracticalexample…Setting:A0-DWORDwriteprimitivetoanarbitraryaddressExploitationofa0-DWORDwritehasbeenpresented@SyScan360Checkoutmyslidesifyou'reinterested;)siberas2016|50/65Let'smakeitharderthan0-DWORDoverwriteForInfiltrate:Let'sexploitZDI-CAN-3507OriginallyplannedforPwn2Own2016…Obvious:Ican'trevealanyinformationaboutthebugButIcandescribetheexploitmethodologyAtleastthebasicstepsWARNING:Thebugisugly.
.
.
But:Thatmakesitagreatexampletoshowcasetheflexibilityofthedescribedflinkoverwritetechnique!
ExploitingtheReadersiberas2016|51/65ExploitingtheReader-ZDI-CAN-3507Setting:Writeprimitiveofanobject-pointer(non-XFA)toanarbitraryaddress!
!
Wecanonlywritetoanaddresswherewehavea0-DWORDcmp[ecx],0//ecxisundercontrol!
jnz*ecx=alloc_some_nonXFA_object()siberas2016|52/65ExploitingtheReader-ZDI-CAN-3507Plan:BypassASLRbyonlytriggeringthevulntwiceFirstshottoderiveinformationabouttheheaplayoutSecondshottoattacktheflinkFirstpartiseasy:Hitfloatingpointarrays!
Wecan'tshootintoheapsprayofstrings:No0-DWORD…Pushvalue1.
59275155158737554072477261984e-315intoarrays=>Resultsinbinarypattern(afterspecIEEE754)1337133700000000133713370000000013371337000000001337133700000000…siberas2016|53/65ArrayX-1ArrayX+1Firstshotwillgoto0x10101014,thiswillbemappedbythearrayheapsprayExploitingtheReader-ZDI-CAN-3507ArrayX-2Firstshot@0x10101014hitsa0-DWORD1337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000…1337133700000000siberas2016|54/65ArrayX-1ArrayX+1ExploitingtheReader-ZDI-CAN-3507ArrayX-2SuccessfuloverwritegivesusbaseaddressofArrayX13371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337AABBCCDD133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000……andnowwealsoknowbaseaddressesofArraysX-1,X-2,X+1,X+2,…!
13371337AABBCCDDsiberas2016|55/65ExploitingtheReader-ZDI-CAN-3507NowweneedtooverwriteaflinkAflinkisanaddress,obviously!
=0,butwecanonlywritetoanaddresswherewehavea0-DW.
.
.
Solution:Partialoverwriteaflinkwhichendson00's!
Let'smanipulatetheflinksothatitisshiftedintoaneighboringfloatarray!
Whenanobjectallocationwiththebadflink"occurs,theobject(andhencethevtable)isplacedintothefloatarraySohowdoIknowwheremyflinksareinmemoryAndhowdoIknowinwhereIcanfindthechunkthatcontainstheflinkendingon00's(ourtargetflink)siberas2016|56/65ExploitingtheReader-ZDI-CAN-3507ArrayBufferZArrayBufferZ-1ArrayBufferZ+1FREEIT[…]jfMC*BlockdatajfMC*BlockdataFreebufferAllocateenoughjfCacheobjectstocauseallocationofnewchunk=>Arrayreplaced!
flinkFreebufferflinksiberas2016|57/65ExploitingtheReader-ZDI-CAN-3507[…]jfMC*BlockdatajfMC*BlockdataFreebufferFreebufferflinkArraybufferZ-1Weknowthearraybaseaddress=>WeknowtheflinkaddressesifwereplaceArrayZ!
Nowwecanfindasuitableflinkendingon00's=>Thiswillbetheoverwritetarget!
flinkjfMC*BlockdatajfMC*BlockdataFreebufferFreebufferflinkflink[…]=>WeknowtheflinkaddressesifwereplaceArrayZ+n!
siberas2016|58/65ExploitingtheReader-ZDI-CAN-3507Knowingtheflinkaddressesweneedtosearchaflinkofform0xXXYY0000Whynot00Youwon'tshifttheflinkintothenextarray!
Whynot000000Veryunlikelytofindsuchaflink!
Lower16bitsoftheflinkwillbeoverwrittenwithupper16bitsoftheobjectpointerLet'sassumewriteofobjectpointer==0x09204060000000000000YYXXflinkPartialoverwrite000060402009YYXXsiberas2016|59/65Partialoverwrite:0xXXYY0000=>0xXXYY0920Flinkwillbeshifted0x920bytesinthiscaseFlinkshouldbelocatedneartotheendofthechunksothataftertheoverwriteitpointstothenextArrayZ+1!
ExploitingtheReader-ZDI-CAN-3507ArrayZ+1[…]jfMC*BlockdatajfMC*BlockdataFreebufferflinkFreebufferflinkArrayZ-1siberas2016|60/65WhentheblockwiththeoverwrittenflinkisallocatedthedataisplacedinArrayZ+1Ifanobjectisallocatedthevtablewillbeplacedtherereadytoberead=>ASLRbypassed!
=)ExploitingtheReader-ZDI-CAN-3507ArrayX+1[…]jfMC*BlockdatajfMC*BlockdataFreebufferflinkFreebufferflinkArrayX-1jfMC*VTABLEobjdataobjdataobjdataobjdata……siberas2016|61/65ExploitingtheReader-ZDI-CAN-3507AndRCESupereasy!
LocatethevtablepointerbyfindingtheoverwrittenfloatvalueinArrayZ+1OverwritethisfloatvaluesothatwehitourstackpivotwiththenextvtablecallReferencetheobjectwiththeoverwrittenvtablepointertocauseavtablecallandjumpintoyourROPGAMEOVER.
siberas2016|62/65Demosiberas2016|63/65Conclusionsiberas2016|64/65Veryeasy,buthighlyeffectivetechniquetoleakdataNoglobalRWprimitive,butenoughtopwnARVersion-independantOS-independantVeryfast:Fromstarttopwnin~1secpossibleZDI-CAN-3507slowbecausevulnneedstimetotriggerFlexibletechniquewhichcanbeusedwithalmosteverykindofoverwrite(aswehavejustseen)CustomallocatorprovesonceagaintobeaperfecttargetinmemorycorruptionscenariosConclusionsiberas2016|65/65Q&AThankyouforyourattention!
apelt@siberas.
de2016/04/08siberas2016|2/65whoamiMotivation(Short!
)IntroductiontoXFAXFAInternalsXFAObjectsjfCacheManagerExploitingtheReaderDemoConclusionQ&AAgendasiberas2016|3/65SebastianApelt(@bitshifter123)Co-Founderofsiberasin2009IT-SecurityConsulting(Pentests,CodeAudits,etc.
)ResearchLow-leveladdictReverseEngineering,Bughunting,Exploitation>100CVEsinallkindsofProductsPwn2Own2014(IE11onWin8.
1x64)whoamisiberas2016|4/65Motivationsiberas2016|5/65FuzzingatsiberasLet'spwntheReader@Pwn2Own2016!
!
Unfortunately,noloveforReaderthistimeIn2015:XFAfuzzingon128coresFuzzrunyieldedthousandsofcrashesSofar~20Bugsidentifiedasunique(upcoming)Analysistookages…Let'stakealookatatypicalReadercrash!
Motivationsiberas2016|6/650:000>!
heap-p-aecxaddress07b2f3ccfoundin_HEAP@11a0000HEAP_ENTRYSizePrevFlagsUserPtrUserSize-state07b24eb0199c0000[00]07b24eb80ccd8-(busy)(72fc.
72ec):Accessviolation-codec0000005(!
!
!
secondchance!
!
!
)eax=69572c30ebx=00000002ecx=07b2f3ccedx=05658af8esi=0549e538edi=07b2f3cceip=20a29654esp=0031d8c4ebp=00000003iopl=0nvupeiplnznacs=0023ss=002bds=002bes=002bfs=0053gs=002befl=00210206AcroForm!
DllUnregisterServer+0x2f73ce:20a29654movedx,dwordptr[eax]ds:002b:69572c30=MotivationAwesome,wehaveacrash!
Butnousefulfunctionname(DllUnregisterServer)Theobjectholdingthebadreferenceislocatedinthemiddleofahugebuffer=>PageHeapuselessStacktracealsonothelpfulOffset0xa514!
0:000>kcAcroForm!
DllUnregisterServer+0x2f73ceAcroForm!
DllUnregisterServer+0x2f7212AcroForm!
DllUnregisterServer+0x2f7504AcroForm!
DllUnregisterServer+0x35f3aeAcroForm!
DllUnregisterServer+0x358f50siberas2016|7/65AdobeReader=>Nosymbols/RTTIinfos!
NofunctionnamesNoobject/vtableinformationNomeaningfulstacktracesPageHeapuselessRootcauseanalysisisveryhardwithoutcontextComplicatescrashtriagingduringfuzzrunsMotivationsiberas2016|8/65HowdoweANALYZEcrashesinXFAHowdoweEXPLOITthesecrashesObvious:Weneedcontext!
Weneedsymbols!
Noin-depthresearchaboutXFAinternalssofar:Mostuseful:WriteupsaboutXFAexploitfrom2013(DavidandEnriqueofImmunityInc,MatthieuBonettiofPortcullisLabs)Goodtechnicalanalysis,butonlyscratchingthesurfaceMotivationsiberas2016|9/65WritetoolstorecovercontextualinformationLowerthebarforotherresearchers!
Checkhttps://github.
com/siberasinthenextdaysFacilitate:VulnerabilitydiscoveryandrootcauseanalysisCrashtriagingduringfuzzrunsDeliverXFA-specificbackgroundforexploitationMotivationsiberas2016|10/65(Short!
)IntroductiontoXFAsiberas2016|11/65XFA:XMLFormsArchitecture"SpecificationdevelopedbyJetForm,laterAccelio(acquiredbyAdobein2002)–notastandardLatestversion:3.
3(01/2012):Easyreadof1584pages.
BringsdynamicbehaviortothestaticPDFworld:Formsthatcandynamicallychangetheirlayout!
DynamicnatureofXFAispoweredbyJavascript(Spidermonkey24sinceARDC)XFAnotsupportedbymanyPDFReaders,yet(Chrome/Chromium,Firefox,Windows,.
.
.
)(Short!
)IntroductiontoXFAsiberas2016|12/65XFAformdataitselfisanXML-structureembeddedinthePDF,aso-calledXDP-PacketJavascriptembeddedinthisXDPExecuteduponevents(e.
g.
documentisfullyloaded,userclicksonbutton,etc.
)Apracticalexample…(Short!
)IntroductiontoXFAsiberas2016|13/65[…][…]app.
alert(1337);[…](Short!
)IntroductiontoXFAXDPPacketisXMLembeddedinthePDFTheroottagisalwaysxdp"ConfigDOMcontainsconfigurationoptionsforXFAprocessingTemplateDOMisstructuredinsubforms,containingobjectslikefield",text",etc.
Objectscancontaineventobjectsthatfireoncertainactions(e.
g.
click")siberas2016|14/65XFAspecdefinesmultipleDOMsHUGEattacksurface(>200objectsaccessibleviaJS)(Short!
)IntroductiontoXFAtemplateConfigurationOptionsTplDOM:ObjectswhichwillbevisibleinthePDFXML-DatathatcanbeusedtopopulatefieldsinthePDFTemplateandDataaremergedintoFormDOMLayoutDOMmakeslayoutinformationaccessiblexdpconfigdataSetsformlayoutxdcdataDescDevice-specificinformationsourceSetdataDescriptionDOM:DataschemaDOMforDB-/WebService-Connectionssiberas2016|15/65XFAInternalssiberas2016|16/65Tweetby@nilsNice!
SomeSolarisbuildseemstohavesymbols!
Newestversionwhichstillhassymbols:Solarisv9.
4.
1WeneedareliableheuristictoportsymbolsinAcroForm.
api(modulewhichimplementsXFAfunctionality)tonewerARversionsXFAInternals-GeneralApproachsiberas2016|17/65Problems:Codeisratherold(2012)->ManyCodechangesfromv9.
XtoARDC…Functioncount:Solaris~48K,ARDC~95KFunctionsdifferevenifcodestaysthesame(compileroptimizationslikeheavyinlininginv9.
4.
1screwitup)TrieddiffingwithDiaphora–ToomanyfalsepositivesStructures,objectsandvtablesizesdiffer(slightly,butenoughtomakeitveryhardtocreatereliableheuristics)etc.
XFAInternals-GeneralApproachsiberas2016|18/65Approach:TryingtounderstandReaderv9.
4.
1asmuchaspossiblewiththehelpofsymbolsFindbulletproofwaystorecoverthemostimportantsymbols,i.
e.
HeapMgmtfunctionsforthecustomallocatorObjectinformationXFAInternals-GeneralApproachsiberas2016|19/65WhatdoweneedtoknowaboutobjectsHowtoidentifyanobjectinmemoryVtableoffsetsMethodsandpropertiesexposedtoJavaScriptOffsetsoftheentrypointsformethods/property-gettersand-settersFunctionnamesofvtableentriesXFAInternals-Objectssiberas2016|20/65Firstattempt:XFANode::getClassTagFail!
classTagsnotconstantacrossversions!
XFAInternals-Objects:IdentificationFromFieldconstructormethod:classTagforField-ObjectinAdobeReader9.
4.
1:0x86classTagattributecanbefound@+0x10classTagforField-ObjectinAcrobatReaderDC:0x8esiberas2016|21/65::TypemethodtotherescueLocated@vtable+8ofeachXFA-ObjectType-IDsarestaticacrossversions!
XFAInternals-Objects:IdentificationTypeis0x7C46forbothv9.
4.
1ANDAcrobatReaderDC!
AdobeReader9.
4.
1AcrobatReaderDCsiberas2016|22/65PossibletoidentifyeveryobjectbyabinarypatterninnewerversionsofAcroForm.
apimoveax,7C46hretnB8467C0000C3XreftotheTypemethodgivesusthevtableoffset(RVA)toeachobject!
XFAInternals-Objects:IdentificationWecansafelyidentify334objects!
Nottoobad!
siberas2016|23/65WhatdoweneedtoknowaboutobjectsHowtoidentifyanobjectinmemoryVtableoffsetsMethodsandpropertiesexposedtoJavaScriptOffsetsoftheentrypointsformethods/property-gettersand-settersFunctionnamesofvtableentriesXFAInternals-Objectssiberas2016|24/65Howaboutmethodsandproperties::getScriptTable()@vtableoffset0x34ReferencesmoScriptTablestructureStructurecontainsinformationaboutmethodandpropertynames,functionpointers,etc.
XFAInternals-ObjectsXFAFieldImpl::moScriptTablesiberas2016|25/65XFAInternals-ObjectsXFAContainerImpl::moScriptTable&field"Property-TableMethod-TableXFAObjectImpl::moScriptTable&tree"Property-TableMethod-TableXFANodeImpl::moScriptTable&container"Property-TableMethod-TableXFATreeImpl::moScriptTable&node"Property-TableMethod-Table0x00000000&object"Property-TableMethod-TablePtr1toproperty-structPtr2toproperty-struct0x00000000Ptr1tomethod-structPtr2tomethod-struct0x00000000&rawValue"func-ptrsetterfunc-ptrgetter&addItem"func-ptraddItemXFAFieldImpl::moScriptTablesiberas2016|26/65WhatdoweneedtoknowaboutobjectsHowtoidentifyanobjectinmemoryVtableoffsetsMethodsandpropertiesexposedtoJavaScriptOffsetsoftheentrypointsformethods/property-gettersand-settersFunctionnamesofvtableentriesXFAInternals-ObjectsTODO…Nottrivial…;-(siberas2016|27/65MostallocationsinAcroForm.
apiaremanagedbyacustomallocatorcalledjfCacheManagerLIFO-styleheapmanagerDatabuffers(blocks")storedinbigheapchunks"IntroducedmostlikelyforperformancereasonsNosecurityfeatures…NoHeapIsolation(seeIE,Flash,etc.
)NoAnti-UAFlikeMemProtect/MemGC…XFAInternals-jfCacheManagersiberas2016|28/65Disclaimer:Nextslideswillonlycovertherelevantdetailsofthememorymanagerintermsofexploitation!
(Morein-depthanalysiswillbecoveredbyapaperwhichwillbereleasedsoon)XFAInternals-jfCacheManagersiberas2016|29/65VerysimplifiedversionofthejfCacheManager:XFAInternals-jfCacheManagerAllocatorstructures:jfCacheManagerjfMemoryCacheListjfMemoryCacheBBBB"AAAAA…"Chunk"(bigcontainer)Block"(smalldatabuffers)sizeXsizeYsiberas2016|30/65XFAInternals-jfCacheManagerStorageofallocationsofsize=0x100[…]0x18jfMemoryCacheList*size0x1jfMemoryCacheList*size0x2[…]jfMemoryCacheList*size0xFF0x418-0x434.
[…]jfCacheManager0x100entriesArrayofjfMemoryCache*jfMemCache*jfMemCache*jfMemCache*jfMemCache*[…][…]ArrayofjfMemoryCache*ArrayofjfMemoryCache*CHUNK(BLOCK-SIZE0x1)jfMemoryCachejfMemoryCachejfMemoryCachejfMemoryCacheCHUNK(BLOCK-SIZE0x1)CHUNK(BLOCK-SIZE0x2)CHUNK(BLOCK-SIZE0xFF)jfMemCacheListjfMemCacheListjfMemoryCacheandthechunkswillberelevantforexploitation!
siberas2016|31/65sizeof(chunk)derivedfromblocksize:Example:allocationsize=0x64=>chunksize=26*(0xc3b3/0x64)*4=0xcb20So,ifIgetacrashandIseemyobjectlocatedinachunkofsize0xcb20,thensizeof(obj)==0x64"Unfortunatelynot…base_size=0xc350//50.
000chunksize=((((size+3)/4)+1)*((base_size+size-1)/size))*4XFAInternals-jfCacheManagersiberas2016|32/65jfMemoryCacheListscanmanageblocksofmultiplesizes=>blocksofsizesXandYcanbothendupinchunkZ!
alloc(X)willbeplacedinsamechunkasalloc(Y)ifanallocationforasizeY>XhasoccuredbeforeandsizeXisinthesamerange"assizeYRangesreachfrom2nto(2n+1-1)(e.
g.
0x20-0x3f,0x40-0x7f)Inshort:DoesthenewblockfitintosomechunkthatwealreadyhaveIfyes,usethatchunkinsteadofallocatinganewone!
XFAInternals-jfCacheManagersiberas2016|33/65XFAInternals-jfCacheManager0x0vtable[…]0x8PtrtoAllocs>=0x100[…]0x18jfMemoryCacheList*size0x1[…]0x138[…]0x1a8jfMemoryCacheList*size0x64[…]jfMemoryCacheList*size0xFF0x418-0x434.
[…]jfCacheManagerArrayofjfMemoryCache*jfMemoryCachejfMemCacheListObjectX(size0x64)ObjectY(size0x48)StringoflengthZ(size0x64)Objectofsize0x48fitsintochunkwithblocksize0x64jfMemoryCacheList*size0x48siberas2016|34/65Let'stakealookatthestructureswithinthechunksandwhathappensduringalloc/freeoperations…XFAInternals-jfCacheManagersiberas2016|35/650x0blocksize=0x100x4max_entries[…]0xcchunk**[…]0x1Calloc_count=00x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00flink0x10flink0x20flink0x30flink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrpointstotheblockwhichwillbereturnedwiththenextallocationflinksformasinglelinkedlistseparatingthedatablocksblockofsize0x10Initialstate–Allblocksarefreesiberas2016|36/650x0blocksize=0x100x4max_entries[…]0xcchunk**[…]0x1Calloc_count=10x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00jfMC*AAAABBBBCCCC0x10DDDDflink0x20flink0x30flink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrisoverwrittenwithflinkflinkisoverwrittenwithpointerbacktojfMemoryCacheallocs_counterisincrementedto1Afterfirstallocationsiberas2016|37/650x0blocksize=0x100x4max_entries[…]0xcchunk**[…]0x1Calloc_count=20x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00jfMC*AAAABBBBCCCC0x10DDDDjfMC*EEEEFFFF0x20GGGGHHHHflink0x30flink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrisoverwrittenwithflinkflinkisoverwrittenwithpointerbacktojfMemoryCacheallocs_counterisincrementedto2Aftersecondallocationsiberas2016|38/650x0blocksize=0x100x4max_entries[…]0xcchunk**[…]0x1Calloc_count=30x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00jfMC*AAAABBBBCCCC0x10DDDDjfMC*EEEEFFFF0x20GGGGHHHHjfMC*IIII0x30JJJJKKKKLLLLflink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrisoverwrittenwithflinkflinkisoverwrittenwithpointerbacktojfMemoryCacheallocs_counterisincrementedto3Afterthirdallocationsiberas2016|39/650x0blocksize0x4max_entries[…]0xcchunk**[…]0x1Calloc_count=20x20next_alloc_ptr0x24jfCacheMgr*XFAInternals-jfCacheManagerjfMemoryCache0x00jfMC*AAAABBBBCCCC0x10DDDDflink0x20jfMC*IIII0x30JJJJKKKKLLLLflink0x400x50flinkflink……….
.
Chunk(blocksize0x10,chunksize0xf424)next_alloc_ptrisoverwrittenwithpointertofreeblock-4jfMC*isoverwrittenwithnext_alloc_ptr(becomesflinkagain)allocs_counterisdecrementedto2Freesecondblocksiberas2016|40/65Stilldon'tlikethejfCacheManagerStillmissingPageHeapGetoffsetjfCacheManager_active"withXFAnalyze_funcs.
pyChangebytefrom1to0inbinaryReplaceoriginalAcroForm.
apiYoujustswitchedoffthejfCacheManager:PXFAInternals-jfCacheManagersiberas2016|41/65ExploitingtheReadersiberas2016|42/65ExploitingtheReaderUnderstandtheBugUnderstandtheHeapKnowyourCorruptionTargetsGoalsBypassASLRbycorruptingspecificbyte(s)tocauseamemoryleakFindflexible"overwritetargetNoneedforawrite-what-where(e.
g.
0-DWORDwriteorapartialoverwritetoacontrolledaddressshouldsuffice!
)Findtechniquewhichisfast,reliableandmostimportantlyindependantfromOSandARversionsiberas2016|43/65Let'stargetthemetadatacontainedwithinthechunks!
Twopossibilities:Bothmethodscanbeabusedcreateamemoryleak!
ButhittingtheflinkistheeasiestwaytogoExploitingtheReader0x00jfMC*6161616161616161616161610x1061616161flink0x20jfMC*636363630x30636363636363636363636363flink0x400x50flinkflink…………ChunkHitthejfMemoryCache*BlockisallocatedTriggerswhenblockisfreedHitaflinkBlockisfreeTriggerswhenblockisallocatedsiberas2016|44/65ExploitingtheReader-Hittheflink!
0x00flink0x10flink0x20flink…………0x0blocksize0x4max_entries[…]0xcchunk**[…]0x1C00x20next_alloc_ptr0x24jfCacheMgr*jfMemoryCacheInitialsituationThisisouroverwritetarget!
siberas2016|45/65ExploitingtheReader-Hittheflink!
0x00badflink"0x10flink0x20flink…………0x0blocksize0x4max_entries[…]0xcchunk**[…]0x1C00x20next_alloc_ptr0x24jfCacheMgr*jfMemoryCacheAfterflinkoverwriteRequirement:flinkmustpointtocontrolleddataafteroverwriteStillveryflexible:Doablewithnearlyanykindofmemcorruption!
Let'sseewhathappenswhenweallocatethebad"block0x00Attacker-ControlledData0x100x20…………siberas2016|46/650x00jfMC*AAAABBBBCCCC0x10DDDDflink0x20flink…………next_alloc_ptrisoverwrittenwiththebad"flinkflinkisoverwrittenwithpointerbacktojfMemoryCacheNowwhathappenswhenweallocateanobjectofsize0x10…ExploitingtheReader-Hittheflink!
0x0blocksize0x4max_entries[…]0xcchunk**[…]0x1C10x20next_alloc_ptr0x24jfCacheMgr*jfMemoryCache0x00flink"0x100x20…………Afterallocationofblockwithbad"flinksiberas2016|47/650x00jfMC*AAAABBBBCCCC0x10DDDDflink0x20flink…………Nextallocationwillreturnthedatabufferaftertheflink"Theobjectwillbeplacedinthemiddleofourcontrolleddata=>Wegetavtableincontrolleddata!
!
ExploitingtheReader-Hittheflink!
0x0blocksize0x4max_entries[…]0xcchunk**[…]0x1C10x20next_alloc_ptr0x24jfCacheMgr*jfMemoryCache0x00jfMC*VTABLErefcount0x100x20…………Allocateanobjectsiberas2016|48/65ExploitingtheReader-Hittheflink!
AssoonasthevtableisinacontrolledareayoucanjustreaditoutThecontrolleddataareacanbesprayedwithstringsorevenfloatarraysaslandingzone"SettheoverwrittenfloatorreplacethestringwithdatawhichwillpointtoyourROPpivotgadgetForfloats:YoucancomputetheirbinaryrepresenationafterspecIEEE754:4.
18356164518379836860971488084E-216willbe0x13371337deadc0deontheheapGAMEOVER!
siberas2016|49/65ExploitingtheReaderLet'shavealookatapracticalexample…Setting:A0-DWORDwriteprimitivetoanarbitraryaddressExploitationofa0-DWORDwritehasbeenpresented@SyScan360Checkoutmyslidesifyou'reinterested;)siberas2016|50/65Let'smakeitharderthan0-DWORDoverwriteForInfiltrate:Let'sexploitZDI-CAN-3507OriginallyplannedforPwn2Own2016…Obvious:Ican'trevealanyinformationaboutthebugButIcandescribetheexploitmethodologyAtleastthebasicstepsWARNING:Thebugisugly.
.
.
But:Thatmakesitagreatexampletoshowcasetheflexibilityofthedescribedflinkoverwritetechnique!
ExploitingtheReadersiberas2016|51/65ExploitingtheReader-ZDI-CAN-3507Setting:Writeprimitiveofanobject-pointer(non-XFA)toanarbitraryaddress!
!
Wecanonlywritetoanaddresswherewehavea0-DWORDcmp[ecx],0//ecxisundercontrol!
jnz*ecx=alloc_some_nonXFA_object()siberas2016|52/65ExploitingtheReader-ZDI-CAN-3507Plan:BypassASLRbyonlytriggeringthevulntwiceFirstshottoderiveinformationabouttheheaplayoutSecondshottoattacktheflinkFirstpartiseasy:Hitfloatingpointarrays!
Wecan'tshootintoheapsprayofstrings:No0-DWORD…Pushvalue1.
59275155158737554072477261984e-315intoarrays=>Resultsinbinarypattern(afterspecIEEE754)1337133700000000133713370000000013371337000000001337133700000000…siberas2016|53/65ArrayX-1ArrayX+1Firstshotwillgoto0x10101014,thiswillbemappedbythearrayheapsprayExploitingtheReader-ZDI-CAN-3507ArrayX-2Firstshot@0x10101014hitsa0-DWORD1337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000…1337133700000000siberas2016|54/65ArrayX-1ArrayX+1ExploitingtheReader-ZDI-CAN-3507ArrayX-2SuccessfuloverwritegivesusbaseaddressofArrayX13371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337AABBCCDD133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000133713370000000013371337000000001337133700000000……andnowwealsoknowbaseaddressesofArraysX-1,X-2,X+1,X+2,…!
13371337AABBCCDDsiberas2016|55/65ExploitingtheReader-ZDI-CAN-3507NowweneedtooverwriteaflinkAflinkisanaddress,obviously!
=0,butwecanonlywritetoanaddresswherewehavea0-DW.
.
.
Solution:Partialoverwriteaflinkwhichendson00's!
Let'smanipulatetheflinksothatitisshiftedintoaneighboringfloatarray!
Whenanobjectallocationwiththebadflink"occurs,theobject(andhencethevtable)isplacedintothefloatarraySohowdoIknowwheremyflinksareinmemoryAndhowdoIknowinwhereIcanfindthechunkthatcontainstheflinkendingon00's(ourtargetflink)siberas2016|56/65ExploitingtheReader-ZDI-CAN-3507ArrayBufferZArrayBufferZ-1ArrayBufferZ+1FREEIT[…]jfMC*BlockdatajfMC*BlockdataFreebufferAllocateenoughjfCacheobjectstocauseallocationofnewchunk=>Arrayreplaced!
flinkFreebufferflinksiberas2016|57/65ExploitingtheReader-ZDI-CAN-3507[…]jfMC*BlockdatajfMC*BlockdataFreebufferFreebufferflinkArraybufferZ-1Weknowthearraybaseaddress=>WeknowtheflinkaddressesifwereplaceArrayZ!
Nowwecanfindasuitableflinkendingon00's=>Thiswillbetheoverwritetarget!
flinkjfMC*BlockdatajfMC*BlockdataFreebufferFreebufferflinkflink[…]=>WeknowtheflinkaddressesifwereplaceArrayZ+n!
siberas2016|58/65ExploitingtheReader-ZDI-CAN-3507Knowingtheflinkaddressesweneedtosearchaflinkofform0xXXYY0000Whynot00Youwon'tshifttheflinkintothenextarray!
Whynot000000Veryunlikelytofindsuchaflink!
Lower16bitsoftheflinkwillbeoverwrittenwithupper16bitsoftheobjectpointerLet'sassumewriteofobjectpointer==0x09204060000000000000YYXXflinkPartialoverwrite000060402009YYXXsiberas2016|59/65Partialoverwrite:0xXXYY0000=>0xXXYY0920Flinkwillbeshifted0x920bytesinthiscaseFlinkshouldbelocatedneartotheendofthechunksothataftertheoverwriteitpointstothenextArrayZ+1!
ExploitingtheReader-ZDI-CAN-3507ArrayZ+1[…]jfMC*BlockdatajfMC*BlockdataFreebufferflinkFreebufferflinkArrayZ-1siberas2016|60/65WhentheblockwiththeoverwrittenflinkisallocatedthedataisplacedinArrayZ+1Ifanobjectisallocatedthevtablewillbeplacedtherereadytoberead=>ASLRbypassed!
=)ExploitingtheReader-ZDI-CAN-3507ArrayX+1[…]jfMC*BlockdatajfMC*BlockdataFreebufferflinkFreebufferflinkArrayX-1jfMC*VTABLEobjdataobjdataobjdataobjdata……siberas2016|61/65ExploitingtheReader-ZDI-CAN-3507AndRCESupereasy!
LocatethevtablepointerbyfindingtheoverwrittenfloatvalueinArrayZ+1OverwritethisfloatvaluesothatwehitourstackpivotwiththenextvtablecallReferencetheobjectwiththeoverwrittenvtablepointertocauseavtablecallandjumpintoyourROPGAMEOVER.
siberas2016|62/65Demosiberas2016|63/65Conclusionsiberas2016|64/65Veryeasy,buthighlyeffectivetechniquetoleakdataNoglobalRWprimitive,butenoughtopwnARVersion-independantOS-independantVeryfast:Fromstarttopwnin~1secpossibleZDI-CAN-3507slowbecausevulnneedstimetotriggerFlexibletechniquewhichcanbeusedwithalmosteverykindofoverwrite(aswehavejustseen)CustomallocatorprovesonceagaintobeaperfecttargetinmemorycorruptionscenariosConclusionsiberas2016|65/65Q&AThankyouforyourattention!
- fullybtio.pw相关文档
- http://www.nec.com/global/solutions/retail-pos/
- 53.00btio.pw
- U219btio.pw
- femalebtio.pw
- operatingbtio.pw
- decentralizedbtio.pw
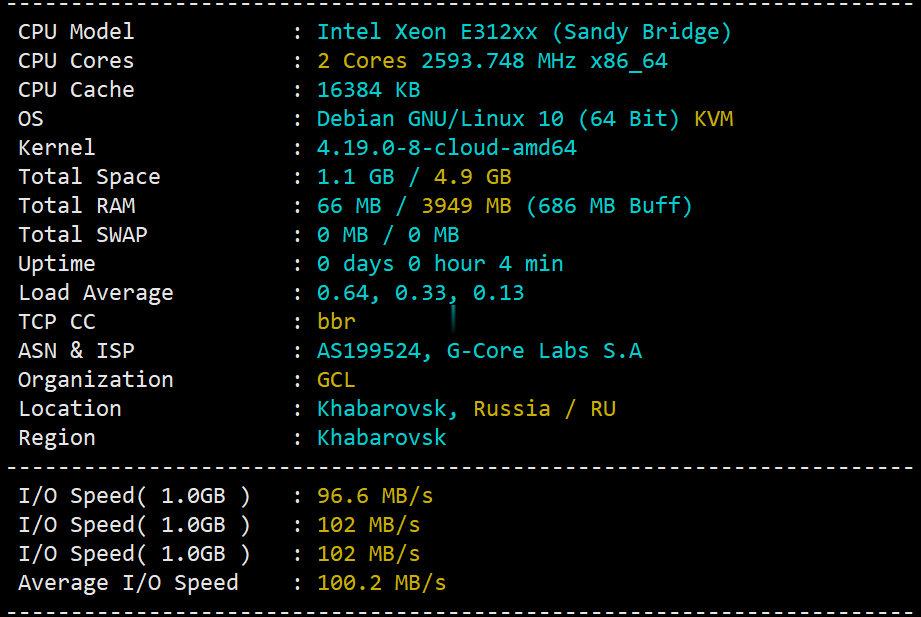
gcorelabs远东khabarovsk伯力Cloud云服务器测评,告诉你gcorelabs云服务器怎么样
说明一下:gcorelabs的俄罗斯远东机房“伯力”既有“Virtual servers”也有“CLOUD SERVICES”,前者是VPS,后者是云服务器,不是一回事;由于平日大家习惯把VPS和云服务器当做一回事儿,所以这里要特别说明一下。本次测评的是gcorelabs的cloud,也就是云服务器。 官方网站:https://gcorelabs.com 支持:数字加密货币、信用卡、PayPal...
Megalayer(48元)新增 美国CN2优化线路特价服务器和VPS方案
Megalayer 商家算是新晋的服务商,商家才开始的时候主要是以香港、美国独立服务器。后来有新增菲律宾机房,包括有VPS云服务器、独立服务器、站群服务器等产品。线路上有CN2优化带宽、全向带宽和国际带宽,这里有看到商家的特价方案有增加至9个,之前是四个的。在这篇文章中,我来整理看看。第一、香港服务器系列这里香港服务器会根据带宽的不同区别。我这里将香港机房的都整理到一个系列里。核心内存硬盘IP带宽...

HostYun 新增可选洛杉矶/日本机房 全场9折月付19.8元起
关于HostYun主机商在之前也有几次分享,这个前身是我们可能熟悉的小众的HostShare商家,主要就是提供廉价主机,那时候官方还声称选择这个品牌的机器不要用于正式生产项目,如今这个品牌重新转变成Hostyun。目前提供的VPS主机包括KVM和XEN架构,数据中心可选日本、韩国、香港和美国的多个地区机房,电信双程CN2 GIA线路,香港和日本机房,均为国内直连线路,访问质量不错。今天和大家分享下...

btio.pw为你推荐
-
netlife熊猫烧香是怎么制作的广东GDP破10万亿广东省城市经济排名陈嘉垣马德钟狼吻案事件是怎么回事www.765.com哪里有免费的电影网站m.kan84.net经常使用http://www.feikan.cc看电影的进来帮我下啊www.6vhao.com有哪些电影网站partnersonline电脑内一切浏览器无法打开partnersonline国外外贸平台有哪些?ww.66bobo.com谁知道11qqq com被换成哪个网站baqizi.cc和空姐一起的日子电视剧在线观看 和空姐一起的日子全集在线观看