rulekaspersky.com
kaspersky.com 时间:2021-03-23 阅读:()
T.
TryfonasandI.
Askoxylakis(Eds.
):HAS2014,LNCS8533,pp.
127–137,2014.
SpringerInternationalPublishingSwitzerland2014ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle*Yee-YinChoongNationalInstituteofStandardsandTechnology,100BureauDrive,Gaithersburg,MD20899,USAyee-yin.
choong@nist.
govAbstract.
Passwordsarethemostcommonlyusedmechanismincontrollingusers'accesstoinformationsystems.
Littleresearchhasbeenestablishedontheentireuserpasswordmanagementlifecyclefromthestartofgeneratingapassword,maintainingthepassword,usingthepasswordtoauthenticate,thentotheendofthelifespanofthepasswordwhenitneedstobechanged.
Wedevelopacognitive-behavioralframeworkdepictingthecognitiveactivitiesthatusersperformwithineachstage,andhowthestagesinteractwiththehumaninformationprocessor,i.
e.
memoryandattentionresources.
Individualfactorsarealsorepresentedintheframeworksuchasattitudes,motivations,andemotionsthatcanaffectusers'behaviorsduringthepasswordmanagementlifecycle.
Thepaperdiscussescognitiveandbehavioralactivitiesthroughoutthelifecycleaswellastheassociatedeconomics.
Weshowtheimportanceofaholisticapproachinunderstandingusers'passwordbehaviorsandtheframeworkprovidesguidanceonfutureresearchdirections.
Keywords:password,passwordmanagementlifecycle,cybersecurity,passwordpolicy,usability,cognitive-behavioralframework,economicsofpasswords.
1IntroductionText-basedpasswordsarethemostcommonlyusedmechanismincontrollingusers'accesstoinformationsystems.
Arguably,passwordsarecurrentlythebestfitformanyauthenticationneedsaspasswordsallowaccessfromanywhereassumingonlyasimplebrowserandrevocationisassimpleaschangingpasswords[1].
Usersoftenpossessmultipleaccount-passwordpairsforwork,schoolandprivateuse.
Forexample,itisreportedthatanaverageuserhas25webaccountsrequiringpasswords[2],andemployeesoforganizationshaveabout4[3]to9passwords[4]atwork.
UsersareoftenviewedbyITsecurityprofessionalsastheweakestlinkofcybersecurity[5,6].
Usersarealsoblamedforemployinginsecurebehaviorssuchasselectingbadandsimple-easy-to-guesspasswords,reusingpasswords,writingdownorsharingtheirpasswords,and,wheneverpossible,notchangingtheirpasswordsona*Therightsofthisworkaretransferredtotheextenttransferableaccordingtotitle17U.
S.
C.
105.
128Y.
-Y.
Choongregularbasis.
Forexample,inarecentmajorsecuritybreachinwhich150millionuseraccountswerecompromised,"123456"wasusedthemostasthepasswordbyover2millionusers,followedbyalittlemorecomplicatedpassword"123456789",andtheword"password"ranked3rdusedby345,000users[7].
Ontheotherhand,forusers,usabilityofpasswordsistheirmainconcern.
Usershavetojugglemultiplepasswordsforwork,schoolorpersonaluseandoftenareforcedtocomplywithpasswordpoliciesthattheyviewasburdensome[4,8].
Frustrationwithloginproblemssuchasforgettingormistypingpasswordsincreasegreatlywiththenumberofpasswordsthatusersmustmanage[1,4].
Usersperceivethatsecuritymeasureshindertheirproductivityandsometimesuseworkaroundstobreakthesecurityprotocol[4,8].
Researchfocusingonhumanfactorsandusabilityofpasswordshasbeenchallengingtheviewthatusersaretheprimarycauseforcybersecurityissuesandpointingoutthatsecuritypoliciesareoftenimposingunreasonablerequirementsandpushingusers'cognitivelimits.
Forexample,atypicalenterprisepasswordpolicycanrequireitsemployeescreatecomplicatedpasswords,notwritedownorstorethem,changepasswordsevery90days,andnotreusethelast10passwords.
Itisalmostimpossibleforemployeestocomplywiththisstringentpolicyespeciallywithmultiplepasswordsastherearefundamentallimitationsonhumanmemory(e.
g.
limitedmemoryspan,memorydecay,recognitionvs.
recall,andmemoryinterferences)assummarizedbySasseetal.
[9].
Manystudieshaveinvestigatedtheconstructofusers'selectionof"good"or"bad"passwords[10-12].
Researchersalsochallengethenecessityandtrueeffectivenessofusingaggressivepasswordpoliciesforsecurityandsacrificingusabilitythatforcesuserstoadoptinsecurepracticesandmayeventuallycompromisesecurity[13-15].
Asshown,studiesareabundantonpasswordusabilityanditsimplicationsoncybersecurity.
However,littleresearchhasbeenestablishedonthecognitiveandbehavioralaspectsoftheentireuserpasswordmanagementlifecycle,i.
e.
fromthestartofgeneratingapasswordtotheendofthelifespanofthepasswordwhenitneedstobechangedduetoeventssuchasforgetting,expiration,orcompromise.
Whileperformingresearchonaparticularstageofthelifecycleprovidesvaluableinsightonusers'experiencesduringthatstage,itdoesnotoffercompleteunderstandingoftheentireprocessandcouldmissopportunitiesforidentifyingpotentialinteractionsandinterdependenciesamongvariousstagesduringthepasswordmanagementlifecycle.
Thispaperfocusesontheholisticviewoftheend-to-endpasswordmanagementlifecycleandproposesaframeworkconnectingthedotsofusers'activitiesduringthelifecycle.
Thisframeworkservesasafoundationinguidingfutureresearchdirections.
2TheCognitive-BehavioralFrameworkWedevelopaframeworktorepresentthecognitiveprocessanduserbehaviorsintheend-to-endpasswordmanagementlifecycleandtoguideourfutureresearch.
Theuserpasswordmanagementlifecycleconsistsofthreestages:Generation,Maintenance,andAuthentication.
Theframeworkdepictsthecognitiveactivitiesthatusersperformwithineachstage,andhowthestagesinteractwiththehumaninformationprocessor,i.
e.
memoryandattentionresources.
Inaddition,individualfactorssuchasattitudes,ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle129motivations,andemotionsarealsoincludedthatcanaffectusers'decision-makingandbehaviorsduringthepasswordmanagementlifecycle.
TheframeworkisillustratedinFigure1andeachstageintheuserpasswordmanagementlifecycleisdescribedindetailinthesectionsbelow.
Fig.
1.
ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle2.
1PasswordGenerationInthefirststageofthepasswordmanagementlifecycle,i.
e.
Generation,usershavetogenerateaplausibletextstringbycombiningvariouscharacterstosatisfytherequirementsforaccessingtheassociatedaccountorsystem.
Therequirements,knownascompositionrules,areacommonorganizationalapproachaimedatforcinguserstoselectstrongerpasswords.
Thecontentsandwordingsofthosecompositionrulesvarygreatlyfromsystemtosystem,buttheygenerallyconsistofruleson:passwordlength(minimumand/ormaximum),use(allowedorprohibited)ofcertaincharacters(uppercaseorlowercasealphabets,numericaldigits,specialcharacters),use(allowedorprohibited)ofcommonnames,dictionarywords,birthdaysorotherpersonalinformation.
Compositionrulescanbepresentedasjustpasswordselectionguidelinesinsomesystems,whereasforothersystems,therulescanbeprogrammaticallyenforcedsuchthatusershavetocreatecompliantpasswordsinordertogainaccesstothesystems.
130Y.
-Y.
ChoongThispasswordgeneratingandcomposingprocessissimilartoawritingprocessthatusuallystartswiththewritersettingupthegoalsofthewriting,understandingtheconstraints(e.
g.
grammar,targetaudience),generatingideas,selectingandarrangingwords,constructingtext,andfinallyrefiningthewrittentext[16].
Thisprocess,inessence,isaproblemsolvingprocessthatincludeshighermentalfunctionsandcreativethinking[17].
Passwordcompositionprogressesinasimilarwaywiththeuserfirstsettingthegoalsofwhataccount/systemthepasswordisfor,understandingtheconstraints,choosingcharacters,thenrefiningthetextstringtomeetthepasswordrequirements.
Theconstraintstothepasswordgenerationproblemcanbecategorizedas:(1)Environmental–suchascompositionrules,platforms(e.
g.
desktopand/orlaptopcomputers,and/ormobiledevices),account/systemtype(e.
g.
web,application,orhardwareaccess);(2)Cognitive–suchasmemoryloadandattentionresources,rulecomprehensionability;(3)Individual–suchasattitudes,motivation,andperceptionofthecriticalityandsensitivityoftheaccountandpotentialsecuritythreats.
Thisstagecanbeiterativeastheusertriestofindthebestcombinationofcharactersthatsatisfiesthepasswordrequirementswhiletakingintoaccountotherenvironmentalconstraints,human-informationprocessconstraints(e.
g.
attentiondeficit,memorycapacity)andindividualfactors(e.
g.
attitudes,motivations,andemotions).
Thisstagecanalsobeapurelydecisionmakingstagewithoutinvolvingpasswordcompositionoronlyinvolvingcompositionpartially.
Thishappenswhentheuserdecidestoreuseormakeminorchangestoanexistingpasswordasthebestapproachinthesolutionspacewhilemeetingthepasswordrequirementsandtheuser'sindividualneeds.
2.
2PasswordMaintenanceOncetheusergeneratesasatisfactorypasswordforaspecificaccount/system,thepasswordmovesintoitssecondstageofthelifecycle,Maintenance.
Theusermakesdecisionsonhowhe/shewillkeeptrackofthenewlygeneratedpassword,bymemorizingorstoringusingsomemechanism;andhe/shealsoneedstodecidehowbesttoorganize–mentallyorphysically–thenewlygeneratedpasswordalongwithotherexistingandactivepasswordstominimizememoryinterferencesatalaterstage.
Iftheuserdecidestomemorizethepassword,he/sheneedstoemploysomestrategies(e.
g.
mnemonicdevice,roterehearsing,ortypingmultipletimestoestablishmusclememory)tomakesurethepasswordhasbeenencodedproperlyintothelong-termmemory.
Iftheuserdecidestostorethepassword,he/sheneedstodecidethestoragemechanism,forexample,writingdown(initsentirety,partially,ordisguised),recordingelectronically(file,devices,etc.
),orutilizingsomepasswordmanagementsoftware.
Sometimes,theremaybeanorganizationalpolicyonhowpasswordsshouldbemaintainedbylimitingmaintenanceoptionstousers.
Forexample,"Passwordsshouldneverbewrittendownorstoredon-linewithoutencryption.
"isthemostcommonpolicysetbymanyorganizations.
ItshouldbenotedthattherecanbeinteractionsandinterdependenciesbetweentheGenerationandMaintenancestagesastheusermayholdanaprioripreferenceonwhethertomemorizeortostorethepasswordwhichcanimpacttheuser'spasswordACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle131composingprocesswiththethoughtthathe/shehastomemorizethetextforlateruse.
Also,thememorabilityofatextstringcanimpacttheuser'sdecisiononhowtomaintainthepassword.
2.
3AuthenticationThelaststageinthelifecycleisAuthenticationinwhichthepasswordisusedtogainaccesstotheassociatedaccount/system.
Theauthenticationstageisrepetitiveasthepasswordwillbeusedmultipletimesforitsentirelifespanuntilachangeeventoccurssuchasforgotten,expiration,passwordcompromised,oruser'sdesiretosynchronizemultiplepasswordsfordifferentaccounts.
Ineachauthenticationinstance,theuserneedstoretrievethecorrectpasswordeitherbyrecallingfrommemoryorbylookingupfromstoredmediathatmatchestheassociatedaccount/systemforaccess,atthesametimestruggleswithforgettingduetomemorydecayorinterferencesfromotherpasswords,andneedstoenterthepasswordcorrectlywhichrequiresattentions,motorskills,musclememory,andhand-eyecoordination.
Therearemanyfactorsthatcanaffectauser'sauthenticationexperiencewithapasswordsuchasauthenticationfrequency,howthepasswordismaintained,memorabilityandtype-abilityoftheaccount/passwordpair,orinterferencesfromotherpasswords.
Theauthenticationexperience(positiveornegative)cantheninfluencehowtheusercreatesnewpasswordswhenhe/shemovesoutfromtheauthenticationstageandstartsthenextpasswordmanagementlifecycle.
3HolisticResearchApproachonUserPasswordBehaviorsGuidedbytheFrameworkTheframeworkservesasaconstantreminderinresearchapproachestoalwaysconsiderusers'passwordbehaviorsinaholisticmannerthat,atanypointoftime,theusersaregoingthroughastageinthepasswordmanagementlifecycleandtheirbehaviorsareareflectionoftheinteractionsamongstagesinthelifecycle,thecapabilitiesandlimitationsofthehumaninformationprocessor,andtheindividualfactors.
Inthefollowingsections,wediscusstheimportanceofemployingaholisticapproachandsomemisconceptionsintheliteratureonuserpasswordbehaviorsresearch.
Wealsoreviewrelevantresearchandpointoutareasforfurtherresearch.
3.
1PasswordGeneration–MorethanaSelectionTaskThemostcommonmisconceptionofpasswordgenerationintheliteratureisthenotionofusers'selectingpasswords.
Itisoftendescribedthatusersselectbadandinsecurepasswords[11,18,19].
However,generatingpasswordsismorethanaselectiontaskinthattheword"selection"implieschoosingfromasetofreadilyavailablepasswordoptions.
Usersonlyselectpasswordswhentheydecidetoreuseexistingpasswords.
Inpasswordgeneratingtasks,usersemployhigh-levelcognitive,132Y.
-Y.
Choongproblem-solvingtaskswhentheyarefacedwiththetaskofcomposingtextstringstosatisfypasswordrequirementsofcombiningandarrangingvariouscharacterswithlengthlimitswhiletryingtomakesenseofthetextstringsandmeetingtheirownpersonalneeds.
3.
2PasswordComposition–ProblemSolvingAsnotedearlier,passwordcompositionisinessenceproblemsolvinginthatitinvolvesgoalsdefining,ideassearching/planning,andrefining/finalizing.
Therehavebeenfewstudiesinvestigatingpasswordgenerationunderrestrictivecompositionrules[11,20,21].
However,thosestudiesfocusedonlyontheoutcomesofthepasswordgeneration,i.
e.
thecharacteristicsofthepasswordsgenerated,andtheimpactsoftherestrictions,butdidnotinvestigatetheentiregenerationprocess.
Passwordresearchhasseldomrecognizedthatcompositionisnotatrivialtask.
Thereisaneedforresearchonhowuserssolvethe"passwordgeneration"problemfromthebeginningwhenusersfirstencounterandperceivetheproblemdomain;comprehendtheconstraints(Environmental,Cognitive,andIndividual);explorethesolutionspace;verifysolutionfeasibility;refine/narrowsolutionspace;andmakedecisionsonthebest-fitsolution.
Byresearchingpasswordgenerationasaproblemsolvingeffortwiththeframework,itenablesustoinvestigatetopicssuchasthedifferencesamongthe"problemsolvers"(e.
g.
expertsvs.
novices);theimpactsofpasswordconstraintsonthesolutionspace;themostimportantfactor(s)leadingtothebest-fitsolution;andtheinfluencesofthemaintenancedecisiononpasswordgeneration.
3.
3TheEconomics–PasswordManagementLifecycleThecostofpasswordsappearslowataglancefromtheserviceproviders'perspectiveasdeployingafunctionalpasswordsystemisrelativelysimplecomparedtootherauthenticationalternativessuchasbiometricsorsmartcards.
Fromtheusers'perspective,itdoesn'tseemtocostmuch,either,sincepasswordsallowinstantaneousaccountsetupandarereadilyunderstood[1].
However,therearesignificantcostsassociatedwiththepasswordauthenticationmechanismforboththeserviceprovidersandtheendusers.
Itisshownqualitatively[15]thatanunusablepasswordpolicycandegradeemployees'productivity,andultimatelyaffecttheorganization'soverallproductivity.
Itisreportedthatmorethan30%ofITsupportcentercallswererelatedtopasswordresets[22].
Onaverage,eachcalllastsabout5minutesandthecostofsupportperincidentis$251onaverage[23].
Inadditiontothesupportcentercost,therearealsocostsassociatedwithauser'stimeandproductivitylosswhenmakingcallstothesupportcenter.
Ofthethreestagesintheuserpasswordmanagementlifecycle,GenerationandAuthenticationarethemosteffort-andtime-consumingstagesfortheusers.
Itisimperativeforresearcherstostartinvestigatingtheassociatedcostsforthesetwostagesfromtheusers'perspective.
1AllcostestimatesinthispaperarebasedontheUnitedStatesdollar,i.
e.
USDorUS$.
ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle133TheCostofPasswordGenerationBesidescompositionrules,organizationsoftenincludeotherrequirementssuchaspasswordexpiration,passwordreuselimitations,andpassworduniquenessintheirorganizationalpolicies.
Itwillbedifficulttoquantifythedirectimpactsofthepasswordpoliciesonusers'cognitiveactivitiesandbehaviorsandtranslatetheimpactsintoassociatedcosts.
Onewaytoestimatethecostsistolookatthenumberofpasswordsgeneratedandthetimeittakestogeneratethosepasswords.
InthestudyperformedbyChoongetal.
[4],itisreportedthatanemployeehasonaverage9work-relatedpasswords.
Anorganizationalpasswordpolicycommonlylookslike:PasswordmustbeoChangedatleastevery60daysoAtleast12characterslongoConsistentwiththecomplexityrequirements(mixed-casecharacters,numbers,andspecialcharacters)PasswordmustnotoBewrittendownorstoredon-lineonnon-organizationsystemsoReuseanypasswordofthelast24priorpasswordsoUsethesamepasswordonmultiplesystems,applicationsorwebsitesIfanewemployeeacquireshis/her9passwordsinthefirstmonthsonthejob,byfollowingthepolicy,itmeansthatthenewemployeewillhavetogenerate54uniquepasswordswithinthefirstyearofemployment,whichmeansthatauniqueandcomplexpasswordisgeneratedonaverageeveryweekthroughouttheyear.
Theconstantpasswordgenerationtaskputsahugeamountofburdenonemployeeswhoonlyseemanagingpasswordsasasecondarytaskenablingaccesstotheirprimarytask[24].
Thisestimatedoesnottakeintoaccountotherpasswordgenerationeventsoutsideoftheregularchangingcycleduetounplannedincidentssuchasforgottenpasswordsorpasswordcompromises.
Itisalsoreportedthatthelongesttimeittakestogeneratepasswordsforworkis,onaverage,98.
5minutesforfrequentpasswordsand86.
6minutesforoccasionallypasswords[4].
Theworstscenario:ifeverypasswordtakesthelongesttimetogenerate,anemployeecanspend18.
6hours(or2businessdays)ata60-daycycleeachyeargeneratingpasswordsfortheirwork.
Iftheaverageannualwageof$81,704(or$39.
15/hour)offederalcivilianworkersisused[25],wecanestimateanannualcostof$728.
19peremployeebeingpulledawayfromworktogeneratepasswords.
TheCostofAuthenticationUsersinteractwithauthenticationsystemsonadailybasisforwork,school,orforpersonaluse.
AsshowninFigure1,eachauthenticationinstanceinvolvesretrievingthecorrectpassword(frommemoryorfromstoredmedia)andtypingthepasswordtogainaccess.
Thisauthenticationinstancecanbeiterativeinitselfifanystepfailsinthesequence,e.
g.
incorrectpasswordretrieved–forgettingorinterferences,typingerrors,orsystemfailure.
134Y.
-Y.
ChoongResearchinvestigatingreal-lifeuserauthenticationexperienceincludesdiarystudies,e.
g.
[15,24,26,27],andlongitudinalstudies,e.
g.
[2,28].
Thenumberofauthenticationinstancesvariesgreatlyinthosestudies,rangingfromtyping8.
11passwordsperday[2],75passwordeventsinatwo-weekspan[27],to23authenticationeventsinadaywith46.
9%(~11times)beingpasswordlogins[24].
Usersexpressedfrustrationandtimewastedfromvariousloginproblemssuchasmistypingpasswords,forgettingpasswords,mismatchingaccountandpassword,andgettinglockedout[4].
Whenenteringpasswordsfrommemory,itisreportedthatthemostcommonerrorisincorrectcapitalization(shifting),followedbymissingcharacter(s)[29].
Whileitisdifficulttoestimatethefullcostsofusers'authenticationexperiencewithpasswords,wecanstartwithasimplifiedwaytocalculatethecostsassociatedwithpasswordentry.
InthediarystudydoneattheNationalInstituteofStandardsandTechnology(NIST)[24],employeesenteredpasswordsabout11timesinadayandtheNIST'spasswordpolicyrequirespasswordsbeing12charactersorlonger.
Asreportedin[21],ittakesroughly14secondstotypeapasswordof8characterslong.
Estimatingconservatively(astheNISTrequiredpasswordsarelongerthan8characters),atypicalfull-timeemployeecanspend10.
27hoursayearontypingpasswordsforauthentication2.
Theestimateshouldbedoubled,i.
e.
20.
54hours,asacompleteauthenticationoftenincludestypingtheusernamebesidesthepassword.
Usingthesamewageinformation(i.
e.
$39.
15/hour)in[25],theannualcostperemployeeonenteringusernameandpasswordpairsforauthenticationisroughly$804.
14.
Foranorganizationwith100employees,aroughestimateof$153,000annuallycanbespentonemployees'basicpasswordmanagementactivities(Maintenancenotincluded),i.
e.
Generation($728.
19)andAuthentication($802.
58),asidefromproductivity.
Forlargeorganizationswith1,000employeesormore,thiscostofbasicpasswordmanagementcanbemorethan$1,500,000eachyear.
HiddenCostsBeyondthetwocostsforbasicpasswordmanagementdemonstratedearlier,thereareotherhiddencostsassociatedwiththepasswordmanagementlifecycle.
Forexample,itisnotuncommonfororganizationstoenforcetimeoutsandscreenlockingtomitigateopportunisticmisuseofanunattendedcomputer[15,24].
Itcreatesconstanttaskinterruptionsandrequiresuserstorecoverfrominterruptionsthatwillalsotranslatetoproductivityloss.
Moreandmoreusers'computingexperienceshappenonmobiledevicessuchaslaptopcomputers,tablets,andsmartphones.
Thecognitiveandbehavioralframeworkwillprovideusafoundationtoexploretheimpactsonpasswordenteringexperiencewithdifferentkeyboardsandlayouts.
Itwillalsoallowustoinvestigatethepotentialinterferencesonusers'musclememoryofawell-practicedpasswordandtheincreaseonrecallerrorsortypingerrorsduetotransitioningfromoneplatformtoanotherorhavingtoswitchbackandforthbetweenplatforms.
Researchisneededtounderstandtheassociatedcostsofusers'mobileauthenticationexperience.
2Totalof240workdaysassuming5daysaweek,52weeks,andminustwovacationweeksand10federalholidays.
ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle1353.
4PositiveAttitudes=BetterSecurityBehaviorsandLessFrustrationIngeneral,usersareconcernedwithsecurity,buttheyoftenareforcedtodeveloplesssecurecopingstrategies(e.
g.
reusepasswords,orwritedownpasswords)whentheyareunabletocomplywithpasswordpoliciesthataretoorestrictiveandinflexibletomatchusers'capabilities[15].
However,inalarge-scalesurveystudy[4],theresearchersfoundthatusers'attitudestowardorganizationalpasswordrequirementsarerelatedtotheirpasswordbehaviorsandexperiencesacrossallthreestagesinthepasswordmanagementlifecycle.
Usersholdingpositiveattitudestowardpasswordrequirementsvaluemoreincreatingcompliantandstrongpasswords,writedownpasswordslessoften,feellessfrustrationwithauthenticationproblems,betterunderstandandrespectthesignificanceofsecurity,ascomparedtouserswithnegativeattitudes.
Thefindingsonattitudesleadustomoreresearchquestionsonsearchingforplausiblemeanstoencouragepositiveuserattitudesandtoprovideusersupportaddressingthenegativethoughts.
4ConclusionArecybersecurityandusabilitytwoparallellinesthatnevermeetOr,aretheycrossroadswheretheintersectionisyettobereachedWebelievethat,thoughitmaynotbeeasilyseen,theintersectiondoesexistamongthetheoretical,technical,andusabilityaspectsofcybersecurity.
Itrequirescollaborationfromresearchersandpractitionerswithmulti-disciplinarybackgroundsinfindingtherightbalancetoreachthatintersectionthatwillprovideacceptablesecurityandusability.
Moreresearchisneededonusers'cognitiveandbehavioralactivitiesregardinginterrelationshipsamongthethreestagesinthepasswordmanagementlifecycle.
Whatcanbedonemoreonthetechnologysidetoensuresecurityandprotectinformationassets,andalleviatetheburdenonuserssotheywillthinkmorepositivelyaboutsecuritymeasuresFutureresearchshoulduseaholisticapproachwiththegoalofprovidingdatatoenablethepolicymakerstomakeinformeddecisionsonsecuritypoliciesthatarebothsecureandusable,andtoprovideguidanceinusersupportandeducationtopromotepositiveattitudes.
References1.
Herley,C.
,vanOorschot,P.
:AResearchAgendaAcknowledgingthePersistenceofPasswords.
IEEESecurity&Privacy10(1),28–36(2012)2.
Florêncio,D.
,Herley,C.
:ALarge-ScaleStudyofWebPasswordHabits.
In:Proceedingsofthe16thInternationalConferenceonWorldWideWeb,pp.
657–666.
ACM(2007)3.
Hoonakker,P.
,Bornoe,N.
,Carayon,P.
:PasswordAuthenticationfromaHumanFactorsPerspective:ResultsofaSurveyamongEnd-Users.
In:ProceedingsoftheHumanFactorsandErgonomicsSocietyAnnualMeeting,vol.
53(6),pp.
459–463.
SAGEPublications(2009)136Y.
-Y.
Choong4.
Choong,Y.
-Y.
T.
M.
,Liu,H.
-K.
:ALarge-ScaleSurveyofEmployees'PasswordBehaviors.
Manuscriptsubmittedforpublication(2014)5.
Goverance,I.
T.
:BoardroomCyberWatch2013–Report(2013),http://www.
itgovernance.
co.
uk/what-is-cybersecurity/boardroom-cyber-watch.
aspx6.
Haskins,W.
:NetworkSecurity:GullibleUsersAretheWeakestLink.
TechNewsWorld(November29,2007),http://www.
technewsworld.
com/story/60520.
html(retrieved)7.
Malenkovich,S.
:10WorstPasswordIdeas(AsSeenIntheAdobeHack).
KasperskyLabDaily(November21,2013),http://blog.
kaspersky.
com/10-worst-password-ideas-as-seen-in-the-adobe-hack/(retrieved)8.
MeriTalk.
:CyberSecurityExperience:SecurityProsfromMars,UsersfromMercury(2013),http://www.
meritalk.
com/cybersecurityexperience(retrieved)9.
Sasse,M.
A.
,Brostoff,B.
,Weirich,D.
:Transformingthe'weakestlink'—ahuman/computerinteractionapproachtousableandeffectivesecurity.
BTTechnologyJournal19(3),122–131(2001)10.
Brown,A.
S.
,Bracken,E.
,Zoccoli,S.
,Douglas,K.
:Generatingandrememberingpasswords.
AppliedCognitivePsychology18(6),641–651(2004)11.
Campbell,J.
,Ma,W.
,Kleeman,D.
:Impactofrestrictivecompositionpolicyonuserpasswordchoices.
Behaviour&InformationTechnology30(3),379–388(2011)12.
Yan,J.
,Blackwell,A.
,Anderson,R.
,Grant,A.
:PasswordMemorabilityandSecurity:EmpiricalResults.
IEEESecurity&Privacy2(5),25–31(2004)13.
Florêncio,D.
,Herley,C.
,Coskun,B.
:DoStrongWebPasswordsAccomplishAnythingIn:Proceedingsofthe2ndUSENIXWorkshoponHotTopicsinSecurity,pp.
1–6(2007)14.
Herley,C.
:SoLong,AndNoThanksfortheExternalities:TheRationalRejectionofSecurityAdvicebyUsers.
In:NSPW2009Proceedingsofthe2009WorkshoponNewSecurityParadigmsWorkshop,pp.
133–144(2009)15.
Inglesant,P.
,Sasse,M.
A.
:TheTrueCostofUnusablePasswordPolicies:PasswordUseintheWild.
In:ProceedingsoftheSIGCHIConferenceonHumanFactorsinComputingSystems,pp.
383–392(2010)16.
Flower,L.
H.
,Hayes,J.
R.
:ACognitiveProcessTheoryofWriting.
CollegeCompositionandCommunication32(4),365–387(1981)17.
Flower,L.
H.
,Hayes,J.
R.
:Problem-solvingstrategiesandthewritingprocess.
CollegeEnglish39(4),449–461(1977)18.
ImervaApplicationDefenseCenter(ADC).
:ConsumerPasswordWorstPractices.
ImpervaWhitePaper(2009),http://www.
imperva.
com/docs/wp_consumer_password_worst_practices.
pdf(retrieved)19.
Zhang,Y.
,Monrose,F.
,Reiter,M.
K.
:TheSecurityofModernPasswordExpiration:AnAlgorithmicFrameworkandEmpiricalAnalysis.
In:Proceedingsofthe17thACMConferenceonComputerandCommunicationsSecurity,pp.
176–186(2010)20.
Proctor,R.
W.
,Lien,M.
-C.
,Vu,K.
-P.
L.
,Schultz,E.
E.
,Salvendy,G.
:Improvingcomputersecurityforauthenticationofusers:Influenceofproactivepasswordrestrictions.
BehaviorResearchMethods,Instruments,&Computers34(2),163–169(2002)21.
Vu,K.
-P.
L.
,Bhargav,A.
,Proctor,R.
W.
:ImposingPasswordRestrictionsforMultipleAccounts:ImpactonGenerationandRecallofPasswords.
In:ProceedingsoftheHumanFactorsandErgonomicsSocietyAnnualMeeting,vol.
47(11),pp.
1331–1335.
SAGEPublications(2003)ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle13722.
Pratt,M.
K.
:5AnnonyingHelpDeskCalls-AndHowtoBanishThem.
PCWorld(April3,2012),http://www.
pcworld.
com/article/253073/5_annoying_help_desk_calls_and_how_to_banish_them.
html(retrieved)23.
Abel,S.
:IndustryAverageHelpDeskSupportCosts.
TheContentWrangler(April28,2011),http://thecontentwrangler.
com/2011/04/28/industry-average-help-desk-support-costs/(retrieved)24.
Steves,M.
,Chisnell,D.
,Sasse,M.
A.
,Krol,K.
,Theofanos,M.
,Wald,H.
:Report:AuthenticationDiaryStudy.
NISTIR7983.
NationalInstituteofStandardsandTechnology,Gaithersburg,MD(2014)25.
U.
S.
BureauofEconomicAnalysis:NationalIncomeandProductAccounts,Tables6.
6D,WagesandSalariesPerFull-TimeEquivalentEmployeebyIndustry(August7,2013),http://www.
bea.
gov/national/nipaweb(retrieved)26.
Grawemeyer,B.
,Johnson,H.
:Usingandmanagingmultiplepasswords:Aweektoaview.
InteractingwithComputers23(3),256–267(2011)27.
Hayashi,E.
,Hong,J.
I.
:ADiaryStudyofPasswordUsageinDailyLife.
In:ProceedingsoftheSIGCHIConferenceonHumanFactorsinComputingSystems,pp.
2627–2630.
ACM(2011)28.
Keith,M.
,Shao,B.
,Steinbart,P.
:ABehavioralAnalysisofPassphraseDesignandEffectiveness.
JournaloftheAssociationforInformationSystems10(2),63–89(2009)29.
Stanton,B.
,Greene,K.
K.
:CharacterStrings,MemoryandPasswords:WhataRecallStudyCanTellUs.
In:Proceedingsofthe16thInternationalConferenceonHuman-ComputerInteraction(inpress,2014)
TryfonasandI.
Askoxylakis(Eds.
):HAS2014,LNCS8533,pp.
127–137,2014.
SpringerInternationalPublishingSwitzerland2014ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle*Yee-YinChoongNationalInstituteofStandardsandTechnology,100BureauDrive,Gaithersburg,MD20899,USAyee-yin.
choong@nist.
govAbstract.
Passwordsarethemostcommonlyusedmechanismincontrollingusers'accesstoinformationsystems.
Littleresearchhasbeenestablishedontheentireuserpasswordmanagementlifecyclefromthestartofgeneratingapassword,maintainingthepassword,usingthepasswordtoauthenticate,thentotheendofthelifespanofthepasswordwhenitneedstobechanged.
Wedevelopacognitive-behavioralframeworkdepictingthecognitiveactivitiesthatusersperformwithineachstage,andhowthestagesinteractwiththehumaninformationprocessor,i.
e.
memoryandattentionresources.
Individualfactorsarealsorepresentedintheframeworksuchasattitudes,motivations,andemotionsthatcanaffectusers'behaviorsduringthepasswordmanagementlifecycle.
Thepaperdiscussescognitiveandbehavioralactivitiesthroughoutthelifecycleaswellastheassociatedeconomics.
Weshowtheimportanceofaholisticapproachinunderstandingusers'passwordbehaviorsandtheframeworkprovidesguidanceonfutureresearchdirections.
Keywords:password,passwordmanagementlifecycle,cybersecurity,passwordpolicy,usability,cognitive-behavioralframework,economicsofpasswords.
1IntroductionText-basedpasswordsarethemostcommonlyusedmechanismincontrollingusers'accesstoinformationsystems.
Arguably,passwordsarecurrentlythebestfitformanyauthenticationneedsaspasswordsallowaccessfromanywhereassumingonlyasimplebrowserandrevocationisassimpleaschangingpasswords[1].
Usersoftenpossessmultipleaccount-passwordpairsforwork,schoolandprivateuse.
Forexample,itisreportedthatanaverageuserhas25webaccountsrequiringpasswords[2],andemployeesoforganizationshaveabout4[3]to9passwords[4]atwork.
UsersareoftenviewedbyITsecurityprofessionalsastheweakestlinkofcybersecurity[5,6].
Usersarealsoblamedforemployinginsecurebehaviorssuchasselectingbadandsimple-easy-to-guesspasswords,reusingpasswords,writingdownorsharingtheirpasswords,and,wheneverpossible,notchangingtheirpasswordsona*Therightsofthisworkaretransferredtotheextenttransferableaccordingtotitle17U.
S.
C.
105.
128Y.
-Y.
Choongregularbasis.
Forexample,inarecentmajorsecuritybreachinwhich150millionuseraccountswerecompromised,"123456"wasusedthemostasthepasswordbyover2millionusers,followedbyalittlemorecomplicatedpassword"123456789",andtheword"password"ranked3rdusedby345,000users[7].
Ontheotherhand,forusers,usabilityofpasswordsistheirmainconcern.
Usershavetojugglemultiplepasswordsforwork,schoolorpersonaluseandoftenareforcedtocomplywithpasswordpoliciesthattheyviewasburdensome[4,8].
Frustrationwithloginproblemssuchasforgettingormistypingpasswordsincreasegreatlywiththenumberofpasswordsthatusersmustmanage[1,4].
Usersperceivethatsecuritymeasureshindertheirproductivityandsometimesuseworkaroundstobreakthesecurityprotocol[4,8].
Researchfocusingonhumanfactorsandusabilityofpasswordshasbeenchallengingtheviewthatusersaretheprimarycauseforcybersecurityissuesandpointingoutthatsecuritypoliciesareoftenimposingunreasonablerequirementsandpushingusers'cognitivelimits.
Forexample,atypicalenterprisepasswordpolicycanrequireitsemployeescreatecomplicatedpasswords,notwritedownorstorethem,changepasswordsevery90days,andnotreusethelast10passwords.
Itisalmostimpossibleforemployeestocomplywiththisstringentpolicyespeciallywithmultiplepasswordsastherearefundamentallimitationsonhumanmemory(e.
g.
limitedmemoryspan,memorydecay,recognitionvs.
recall,andmemoryinterferences)assummarizedbySasseetal.
[9].
Manystudieshaveinvestigatedtheconstructofusers'selectionof"good"or"bad"passwords[10-12].
Researchersalsochallengethenecessityandtrueeffectivenessofusingaggressivepasswordpoliciesforsecurityandsacrificingusabilitythatforcesuserstoadoptinsecurepracticesandmayeventuallycompromisesecurity[13-15].
Asshown,studiesareabundantonpasswordusabilityanditsimplicationsoncybersecurity.
However,littleresearchhasbeenestablishedonthecognitiveandbehavioralaspectsoftheentireuserpasswordmanagementlifecycle,i.
e.
fromthestartofgeneratingapasswordtotheendofthelifespanofthepasswordwhenitneedstobechangedduetoeventssuchasforgetting,expiration,orcompromise.
Whileperformingresearchonaparticularstageofthelifecycleprovidesvaluableinsightonusers'experiencesduringthatstage,itdoesnotoffercompleteunderstandingoftheentireprocessandcouldmissopportunitiesforidentifyingpotentialinteractionsandinterdependenciesamongvariousstagesduringthepasswordmanagementlifecycle.
Thispaperfocusesontheholisticviewoftheend-to-endpasswordmanagementlifecycleandproposesaframeworkconnectingthedotsofusers'activitiesduringthelifecycle.
Thisframeworkservesasafoundationinguidingfutureresearchdirections.
2TheCognitive-BehavioralFrameworkWedevelopaframeworktorepresentthecognitiveprocessanduserbehaviorsintheend-to-endpasswordmanagementlifecycleandtoguideourfutureresearch.
Theuserpasswordmanagementlifecycleconsistsofthreestages:Generation,Maintenance,andAuthentication.
Theframeworkdepictsthecognitiveactivitiesthatusersperformwithineachstage,andhowthestagesinteractwiththehumaninformationprocessor,i.
e.
memoryandattentionresources.
Inaddition,individualfactorssuchasattitudes,ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle129motivations,andemotionsarealsoincludedthatcanaffectusers'decision-makingandbehaviorsduringthepasswordmanagementlifecycle.
TheframeworkisillustratedinFigure1andeachstageintheuserpasswordmanagementlifecycleisdescribedindetailinthesectionsbelow.
Fig.
1.
ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle2.
1PasswordGenerationInthefirststageofthepasswordmanagementlifecycle,i.
e.
Generation,usershavetogenerateaplausibletextstringbycombiningvariouscharacterstosatisfytherequirementsforaccessingtheassociatedaccountorsystem.
Therequirements,knownascompositionrules,areacommonorganizationalapproachaimedatforcinguserstoselectstrongerpasswords.
Thecontentsandwordingsofthosecompositionrulesvarygreatlyfromsystemtosystem,buttheygenerallyconsistofruleson:passwordlength(minimumand/ormaximum),use(allowedorprohibited)ofcertaincharacters(uppercaseorlowercasealphabets,numericaldigits,specialcharacters),use(allowedorprohibited)ofcommonnames,dictionarywords,birthdaysorotherpersonalinformation.
Compositionrulescanbepresentedasjustpasswordselectionguidelinesinsomesystems,whereasforothersystems,therulescanbeprogrammaticallyenforcedsuchthatusershavetocreatecompliantpasswordsinordertogainaccesstothesystems.
130Y.
-Y.
ChoongThispasswordgeneratingandcomposingprocessissimilartoawritingprocessthatusuallystartswiththewritersettingupthegoalsofthewriting,understandingtheconstraints(e.
g.
grammar,targetaudience),generatingideas,selectingandarrangingwords,constructingtext,andfinallyrefiningthewrittentext[16].
Thisprocess,inessence,isaproblemsolvingprocessthatincludeshighermentalfunctionsandcreativethinking[17].
Passwordcompositionprogressesinasimilarwaywiththeuserfirstsettingthegoalsofwhataccount/systemthepasswordisfor,understandingtheconstraints,choosingcharacters,thenrefiningthetextstringtomeetthepasswordrequirements.
Theconstraintstothepasswordgenerationproblemcanbecategorizedas:(1)Environmental–suchascompositionrules,platforms(e.
g.
desktopand/orlaptopcomputers,and/ormobiledevices),account/systemtype(e.
g.
web,application,orhardwareaccess);(2)Cognitive–suchasmemoryloadandattentionresources,rulecomprehensionability;(3)Individual–suchasattitudes,motivation,andperceptionofthecriticalityandsensitivityoftheaccountandpotentialsecuritythreats.
Thisstagecanbeiterativeastheusertriestofindthebestcombinationofcharactersthatsatisfiesthepasswordrequirementswhiletakingintoaccountotherenvironmentalconstraints,human-informationprocessconstraints(e.
g.
attentiondeficit,memorycapacity)andindividualfactors(e.
g.
attitudes,motivations,andemotions).
Thisstagecanalsobeapurelydecisionmakingstagewithoutinvolvingpasswordcompositionoronlyinvolvingcompositionpartially.
Thishappenswhentheuserdecidestoreuseormakeminorchangestoanexistingpasswordasthebestapproachinthesolutionspacewhilemeetingthepasswordrequirementsandtheuser'sindividualneeds.
2.
2PasswordMaintenanceOncetheusergeneratesasatisfactorypasswordforaspecificaccount/system,thepasswordmovesintoitssecondstageofthelifecycle,Maintenance.
Theusermakesdecisionsonhowhe/shewillkeeptrackofthenewlygeneratedpassword,bymemorizingorstoringusingsomemechanism;andhe/shealsoneedstodecidehowbesttoorganize–mentallyorphysically–thenewlygeneratedpasswordalongwithotherexistingandactivepasswordstominimizememoryinterferencesatalaterstage.
Iftheuserdecidestomemorizethepassword,he/sheneedstoemploysomestrategies(e.
g.
mnemonicdevice,roterehearsing,ortypingmultipletimestoestablishmusclememory)tomakesurethepasswordhasbeenencodedproperlyintothelong-termmemory.
Iftheuserdecidestostorethepassword,he/sheneedstodecidethestoragemechanism,forexample,writingdown(initsentirety,partially,ordisguised),recordingelectronically(file,devices,etc.
),orutilizingsomepasswordmanagementsoftware.
Sometimes,theremaybeanorganizationalpolicyonhowpasswordsshouldbemaintainedbylimitingmaintenanceoptionstousers.
Forexample,"Passwordsshouldneverbewrittendownorstoredon-linewithoutencryption.
"isthemostcommonpolicysetbymanyorganizations.
ItshouldbenotedthattherecanbeinteractionsandinterdependenciesbetweentheGenerationandMaintenancestagesastheusermayholdanaprioripreferenceonwhethertomemorizeortostorethepasswordwhichcanimpacttheuser'spasswordACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle131composingprocesswiththethoughtthathe/shehastomemorizethetextforlateruse.
Also,thememorabilityofatextstringcanimpacttheuser'sdecisiononhowtomaintainthepassword.
2.
3AuthenticationThelaststageinthelifecycleisAuthenticationinwhichthepasswordisusedtogainaccesstotheassociatedaccount/system.
Theauthenticationstageisrepetitiveasthepasswordwillbeusedmultipletimesforitsentirelifespanuntilachangeeventoccurssuchasforgotten,expiration,passwordcompromised,oruser'sdesiretosynchronizemultiplepasswordsfordifferentaccounts.
Ineachauthenticationinstance,theuserneedstoretrievethecorrectpasswordeitherbyrecallingfrommemoryorbylookingupfromstoredmediathatmatchestheassociatedaccount/systemforaccess,atthesametimestruggleswithforgettingduetomemorydecayorinterferencesfromotherpasswords,andneedstoenterthepasswordcorrectlywhichrequiresattentions,motorskills,musclememory,andhand-eyecoordination.
Therearemanyfactorsthatcanaffectauser'sauthenticationexperiencewithapasswordsuchasauthenticationfrequency,howthepasswordismaintained,memorabilityandtype-abilityoftheaccount/passwordpair,orinterferencesfromotherpasswords.
Theauthenticationexperience(positiveornegative)cantheninfluencehowtheusercreatesnewpasswordswhenhe/shemovesoutfromtheauthenticationstageandstartsthenextpasswordmanagementlifecycle.
3HolisticResearchApproachonUserPasswordBehaviorsGuidedbytheFrameworkTheframeworkservesasaconstantreminderinresearchapproachestoalwaysconsiderusers'passwordbehaviorsinaholisticmannerthat,atanypointoftime,theusersaregoingthroughastageinthepasswordmanagementlifecycleandtheirbehaviorsareareflectionoftheinteractionsamongstagesinthelifecycle,thecapabilitiesandlimitationsofthehumaninformationprocessor,andtheindividualfactors.
Inthefollowingsections,wediscusstheimportanceofemployingaholisticapproachandsomemisconceptionsintheliteratureonuserpasswordbehaviorsresearch.
Wealsoreviewrelevantresearchandpointoutareasforfurtherresearch.
3.
1PasswordGeneration–MorethanaSelectionTaskThemostcommonmisconceptionofpasswordgenerationintheliteratureisthenotionofusers'selectingpasswords.
Itisoftendescribedthatusersselectbadandinsecurepasswords[11,18,19].
However,generatingpasswordsismorethanaselectiontaskinthattheword"selection"implieschoosingfromasetofreadilyavailablepasswordoptions.
Usersonlyselectpasswordswhentheydecidetoreuseexistingpasswords.
Inpasswordgeneratingtasks,usersemployhigh-levelcognitive,132Y.
-Y.
Choongproblem-solvingtaskswhentheyarefacedwiththetaskofcomposingtextstringstosatisfypasswordrequirementsofcombiningandarrangingvariouscharacterswithlengthlimitswhiletryingtomakesenseofthetextstringsandmeetingtheirownpersonalneeds.
3.
2PasswordComposition–ProblemSolvingAsnotedearlier,passwordcompositionisinessenceproblemsolvinginthatitinvolvesgoalsdefining,ideassearching/planning,andrefining/finalizing.
Therehavebeenfewstudiesinvestigatingpasswordgenerationunderrestrictivecompositionrules[11,20,21].
However,thosestudiesfocusedonlyontheoutcomesofthepasswordgeneration,i.
e.
thecharacteristicsofthepasswordsgenerated,andtheimpactsoftherestrictions,butdidnotinvestigatetheentiregenerationprocess.
Passwordresearchhasseldomrecognizedthatcompositionisnotatrivialtask.
Thereisaneedforresearchonhowuserssolvethe"passwordgeneration"problemfromthebeginningwhenusersfirstencounterandperceivetheproblemdomain;comprehendtheconstraints(Environmental,Cognitive,andIndividual);explorethesolutionspace;verifysolutionfeasibility;refine/narrowsolutionspace;andmakedecisionsonthebest-fitsolution.
Byresearchingpasswordgenerationasaproblemsolvingeffortwiththeframework,itenablesustoinvestigatetopicssuchasthedifferencesamongthe"problemsolvers"(e.
g.
expertsvs.
novices);theimpactsofpasswordconstraintsonthesolutionspace;themostimportantfactor(s)leadingtothebest-fitsolution;andtheinfluencesofthemaintenancedecisiononpasswordgeneration.
3.
3TheEconomics–PasswordManagementLifecycleThecostofpasswordsappearslowataglancefromtheserviceproviders'perspectiveasdeployingafunctionalpasswordsystemisrelativelysimplecomparedtootherauthenticationalternativessuchasbiometricsorsmartcards.
Fromtheusers'perspective,itdoesn'tseemtocostmuch,either,sincepasswordsallowinstantaneousaccountsetupandarereadilyunderstood[1].
However,therearesignificantcostsassociatedwiththepasswordauthenticationmechanismforboththeserviceprovidersandtheendusers.
Itisshownqualitatively[15]thatanunusablepasswordpolicycandegradeemployees'productivity,andultimatelyaffecttheorganization'soverallproductivity.
Itisreportedthatmorethan30%ofITsupportcentercallswererelatedtopasswordresets[22].
Onaverage,eachcalllastsabout5minutesandthecostofsupportperincidentis$251onaverage[23].
Inadditiontothesupportcentercost,therearealsocostsassociatedwithauser'stimeandproductivitylosswhenmakingcallstothesupportcenter.
Ofthethreestagesintheuserpasswordmanagementlifecycle,GenerationandAuthenticationarethemosteffort-andtime-consumingstagesfortheusers.
Itisimperativeforresearcherstostartinvestigatingtheassociatedcostsforthesetwostagesfromtheusers'perspective.
1AllcostestimatesinthispaperarebasedontheUnitedStatesdollar,i.
e.
USDorUS$.
ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle133TheCostofPasswordGenerationBesidescompositionrules,organizationsoftenincludeotherrequirementssuchaspasswordexpiration,passwordreuselimitations,andpassworduniquenessintheirorganizationalpolicies.
Itwillbedifficulttoquantifythedirectimpactsofthepasswordpoliciesonusers'cognitiveactivitiesandbehaviorsandtranslatetheimpactsintoassociatedcosts.
Onewaytoestimatethecostsistolookatthenumberofpasswordsgeneratedandthetimeittakestogeneratethosepasswords.
InthestudyperformedbyChoongetal.
[4],itisreportedthatanemployeehasonaverage9work-relatedpasswords.
Anorganizationalpasswordpolicycommonlylookslike:PasswordmustbeoChangedatleastevery60daysoAtleast12characterslongoConsistentwiththecomplexityrequirements(mixed-casecharacters,numbers,andspecialcharacters)PasswordmustnotoBewrittendownorstoredon-lineonnon-organizationsystemsoReuseanypasswordofthelast24priorpasswordsoUsethesamepasswordonmultiplesystems,applicationsorwebsitesIfanewemployeeacquireshis/her9passwordsinthefirstmonthsonthejob,byfollowingthepolicy,itmeansthatthenewemployeewillhavetogenerate54uniquepasswordswithinthefirstyearofemployment,whichmeansthatauniqueandcomplexpasswordisgeneratedonaverageeveryweekthroughouttheyear.
Theconstantpasswordgenerationtaskputsahugeamountofburdenonemployeeswhoonlyseemanagingpasswordsasasecondarytaskenablingaccesstotheirprimarytask[24].
Thisestimatedoesnottakeintoaccountotherpasswordgenerationeventsoutsideoftheregularchangingcycleduetounplannedincidentssuchasforgottenpasswordsorpasswordcompromises.
Itisalsoreportedthatthelongesttimeittakestogeneratepasswordsforworkis,onaverage,98.
5minutesforfrequentpasswordsand86.
6minutesforoccasionallypasswords[4].
Theworstscenario:ifeverypasswordtakesthelongesttimetogenerate,anemployeecanspend18.
6hours(or2businessdays)ata60-daycycleeachyeargeneratingpasswordsfortheirwork.
Iftheaverageannualwageof$81,704(or$39.
15/hour)offederalcivilianworkersisused[25],wecanestimateanannualcostof$728.
19peremployeebeingpulledawayfromworktogeneratepasswords.
TheCostofAuthenticationUsersinteractwithauthenticationsystemsonadailybasisforwork,school,orforpersonaluse.
AsshowninFigure1,eachauthenticationinstanceinvolvesretrievingthecorrectpassword(frommemoryorfromstoredmedia)andtypingthepasswordtogainaccess.
Thisauthenticationinstancecanbeiterativeinitselfifanystepfailsinthesequence,e.
g.
incorrectpasswordretrieved–forgettingorinterferences,typingerrors,orsystemfailure.
134Y.
-Y.
ChoongResearchinvestigatingreal-lifeuserauthenticationexperienceincludesdiarystudies,e.
g.
[15,24,26,27],andlongitudinalstudies,e.
g.
[2,28].
Thenumberofauthenticationinstancesvariesgreatlyinthosestudies,rangingfromtyping8.
11passwordsperday[2],75passwordeventsinatwo-weekspan[27],to23authenticationeventsinadaywith46.
9%(~11times)beingpasswordlogins[24].
Usersexpressedfrustrationandtimewastedfromvariousloginproblemssuchasmistypingpasswords,forgettingpasswords,mismatchingaccountandpassword,andgettinglockedout[4].
Whenenteringpasswordsfrommemory,itisreportedthatthemostcommonerrorisincorrectcapitalization(shifting),followedbymissingcharacter(s)[29].
Whileitisdifficulttoestimatethefullcostsofusers'authenticationexperiencewithpasswords,wecanstartwithasimplifiedwaytocalculatethecostsassociatedwithpasswordentry.
InthediarystudydoneattheNationalInstituteofStandardsandTechnology(NIST)[24],employeesenteredpasswordsabout11timesinadayandtheNIST'spasswordpolicyrequirespasswordsbeing12charactersorlonger.
Asreportedin[21],ittakesroughly14secondstotypeapasswordof8characterslong.
Estimatingconservatively(astheNISTrequiredpasswordsarelongerthan8characters),atypicalfull-timeemployeecanspend10.
27hoursayearontypingpasswordsforauthentication2.
Theestimateshouldbedoubled,i.
e.
20.
54hours,asacompleteauthenticationoftenincludestypingtheusernamebesidesthepassword.
Usingthesamewageinformation(i.
e.
$39.
15/hour)in[25],theannualcostperemployeeonenteringusernameandpasswordpairsforauthenticationisroughly$804.
14.
Foranorganizationwith100employees,aroughestimateof$153,000annuallycanbespentonemployees'basicpasswordmanagementactivities(Maintenancenotincluded),i.
e.
Generation($728.
19)andAuthentication($802.
58),asidefromproductivity.
Forlargeorganizationswith1,000employeesormore,thiscostofbasicpasswordmanagementcanbemorethan$1,500,000eachyear.
HiddenCostsBeyondthetwocostsforbasicpasswordmanagementdemonstratedearlier,thereareotherhiddencostsassociatedwiththepasswordmanagementlifecycle.
Forexample,itisnotuncommonfororganizationstoenforcetimeoutsandscreenlockingtomitigateopportunisticmisuseofanunattendedcomputer[15,24].
Itcreatesconstanttaskinterruptionsandrequiresuserstorecoverfrominterruptionsthatwillalsotranslatetoproductivityloss.
Moreandmoreusers'computingexperienceshappenonmobiledevicessuchaslaptopcomputers,tablets,andsmartphones.
Thecognitiveandbehavioralframeworkwillprovideusafoundationtoexploretheimpactsonpasswordenteringexperiencewithdifferentkeyboardsandlayouts.
Itwillalsoallowustoinvestigatethepotentialinterferencesonusers'musclememoryofawell-practicedpasswordandtheincreaseonrecallerrorsortypingerrorsduetotransitioningfromoneplatformtoanotherorhavingtoswitchbackandforthbetweenplatforms.
Researchisneededtounderstandtheassociatedcostsofusers'mobileauthenticationexperience.
2Totalof240workdaysassuming5daysaweek,52weeks,andminustwovacationweeksand10federalholidays.
ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle1353.
4PositiveAttitudes=BetterSecurityBehaviorsandLessFrustrationIngeneral,usersareconcernedwithsecurity,buttheyoftenareforcedtodeveloplesssecurecopingstrategies(e.
g.
reusepasswords,orwritedownpasswords)whentheyareunabletocomplywithpasswordpoliciesthataretoorestrictiveandinflexibletomatchusers'capabilities[15].
However,inalarge-scalesurveystudy[4],theresearchersfoundthatusers'attitudestowardorganizationalpasswordrequirementsarerelatedtotheirpasswordbehaviorsandexperiencesacrossallthreestagesinthepasswordmanagementlifecycle.
Usersholdingpositiveattitudestowardpasswordrequirementsvaluemoreincreatingcompliantandstrongpasswords,writedownpasswordslessoften,feellessfrustrationwithauthenticationproblems,betterunderstandandrespectthesignificanceofsecurity,ascomparedtouserswithnegativeattitudes.
Thefindingsonattitudesleadustomoreresearchquestionsonsearchingforplausiblemeanstoencouragepositiveuserattitudesandtoprovideusersupportaddressingthenegativethoughts.
4ConclusionArecybersecurityandusabilitytwoparallellinesthatnevermeetOr,aretheycrossroadswheretheintersectionisyettobereachedWebelievethat,thoughitmaynotbeeasilyseen,theintersectiondoesexistamongthetheoretical,technical,andusabilityaspectsofcybersecurity.
Itrequirescollaborationfromresearchersandpractitionerswithmulti-disciplinarybackgroundsinfindingtherightbalancetoreachthatintersectionthatwillprovideacceptablesecurityandusability.
Moreresearchisneededonusers'cognitiveandbehavioralactivitiesregardinginterrelationshipsamongthethreestagesinthepasswordmanagementlifecycle.
Whatcanbedonemoreonthetechnologysidetoensuresecurityandprotectinformationassets,andalleviatetheburdenonuserssotheywillthinkmorepositivelyaboutsecuritymeasuresFutureresearchshoulduseaholisticapproachwiththegoalofprovidingdatatoenablethepolicymakerstomakeinformeddecisionsonsecuritypoliciesthatarebothsecureandusable,andtoprovideguidanceinusersupportandeducationtopromotepositiveattitudes.
References1.
Herley,C.
,vanOorschot,P.
:AResearchAgendaAcknowledgingthePersistenceofPasswords.
IEEESecurity&Privacy10(1),28–36(2012)2.
Florêncio,D.
,Herley,C.
:ALarge-ScaleStudyofWebPasswordHabits.
In:Proceedingsofthe16thInternationalConferenceonWorldWideWeb,pp.
657–666.
ACM(2007)3.
Hoonakker,P.
,Bornoe,N.
,Carayon,P.
:PasswordAuthenticationfromaHumanFactorsPerspective:ResultsofaSurveyamongEnd-Users.
In:ProceedingsoftheHumanFactorsandErgonomicsSocietyAnnualMeeting,vol.
53(6),pp.
459–463.
SAGEPublications(2009)136Y.
-Y.
Choong4.
Choong,Y.
-Y.
T.
M.
,Liu,H.
-K.
:ALarge-ScaleSurveyofEmployees'PasswordBehaviors.
Manuscriptsubmittedforpublication(2014)5.
Goverance,I.
T.
:BoardroomCyberWatch2013–Report(2013),http://www.
itgovernance.
co.
uk/what-is-cybersecurity/boardroom-cyber-watch.
aspx6.
Haskins,W.
:NetworkSecurity:GullibleUsersAretheWeakestLink.
TechNewsWorld(November29,2007),http://www.
technewsworld.
com/story/60520.
html(retrieved)7.
Malenkovich,S.
:10WorstPasswordIdeas(AsSeenIntheAdobeHack).
KasperskyLabDaily(November21,2013),http://blog.
kaspersky.
com/10-worst-password-ideas-as-seen-in-the-adobe-hack/(retrieved)8.
MeriTalk.
:CyberSecurityExperience:SecurityProsfromMars,UsersfromMercury(2013),http://www.
meritalk.
com/cybersecurityexperience(retrieved)9.
Sasse,M.
A.
,Brostoff,B.
,Weirich,D.
:Transformingthe'weakestlink'—ahuman/computerinteractionapproachtousableandeffectivesecurity.
BTTechnologyJournal19(3),122–131(2001)10.
Brown,A.
S.
,Bracken,E.
,Zoccoli,S.
,Douglas,K.
:Generatingandrememberingpasswords.
AppliedCognitivePsychology18(6),641–651(2004)11.
Campbell,J.
,Ma,W.
,Kleeman,D.
:Impactofrestrictivecompositionpolicyonuserpasswordchoices.
Behaviour&InformationTechnology30(3),379–388(2011)12.
Yan,J.
,Blackwell,A.
,Anderson,R.
,Grant,A.
:PasswordMemorabilityandSecurity:EmpiricalResults.
IEEESecurity&Privacy2(5),25–31(2004)13.
Florêncio,D.
,Herley,C.
,Coskun,B.
:DoStrongWebPasswordsAccomplishAnythingIn:Proceedingsofthe2ndUSENIXWorkshoponHotTopicsinSecurity,pp.
1–6(2007)14.
Herley,C.
:SoLong,AndNoThanksfortheExternalities:TheRationalRejectionofSecurityAdvicebyUsers.
In:NSPW2009Proceedingsofthe2009WorkshoponNewSecurityParadigmsWorkshop,pp.
133–144(2009)15.
Inglesant,P.
,Sasse,M.
A.
:TheTrueCostofUnusablePasswordPolicies:PasswordUseintheWild.
In:ProceedingsoftheSIGCHIConferenceonHumanFactorsinComputingSystems,pp.
383–392(2010)16.
Flower,L.
H.
,Hayes,J.
R.
:ACognitiveProcessTheoryofWriting.
CollegeCompositionandCommunication32(4),365–387(1981)17.
Flower,L.
H.
,Hayes,J.
R.
:Problem-solvingstrategiesandthewritingprocess.
CollegeEnglish39(4),449–461(1977)18.
ImervaApplicationDefenseCenter(ADC).
:ConsumerPasswordWorstPractices.
ImpervaWhitePaper(2009),http://www.
imperva.
com/docs/wp_consumer_password_worst_practices.
pdf(retrieved)19.
Zhang,Y.
,Monrose,F.
,Reiter,M.
K.
:TheSecurityofModernPasswordExpiration:AnAlgorithmicFrameworkandEmpiricalAnalysis.
In:Proceedingsofthe17thACMConferenceonComputerandCommunicationsSecurity,pp.
176–186(2010)20.
Proctor,R.
W.
,Lien,M.
-C.
,Vu,K.
-P.
L.
,Schultz,E.
E.
,Salvendy,G.
:Improvingcomputersecurityforauthenticationofusers:Influenceofproactivepasswordrestrictions.
BehaviorResearchMethods,Instruments,&Computers34(2),163–169(2002)21.
Vu,K.
-P.
L.
,Bhargav,A.
,Proctor,R.
W.
:ImposingPasswordRestrictionsforMultipleAccounts:ImpactonGenerationandRecallofPasswords.
In:ProceedingsoftheHumanFactorsandErgonomicsSocietyAnnualMeeting,vol.
47(11),pp.
1331–1335.
SAGEPublications(2003)ACognitive-BehavioralFrameworkofUserPasswordManagementLifecycle13722.
Pratt,M.
K.
:5AnnonyingHelpDeskCalls-AndHowtoBanishThem.
PCWorld(April3,2012),http://www.
pcworld.
com/article/253073/5_annoying_help_desk_calls_and_how_to_banish_them.
html(retrieved)23.
Abel,S.
:IndustryAverageHelpDeskSupportCosts.
TheContentWrangler(April28,2011),http://thecontentwrangler.
com/2011/04/28/industry-average-help-desk-support-costs/(retrieved)24.
Steves,M.
,Chisnell,D.
,Sasse,M.
A.
,Krol,K.
,Theofanos,M.
,Wald,H.
:Report:AuthenticationDiaryStudy.
NISTIR7983.
NationalInstituteofStandardsandTechnology,Gaithersburg,MD(2014)25.
U.
S.
BureauofEconomicAnalysis:NationalIncomeandProductAccounts,Tables6.
6D,WagesandSalariesPerFull-TimeEquivalentEmployeebyIndustry(August7,2013),http://www.
bea.
gov/national/nipaweb(retrieved)26.
Grawemeyer,B.
,Johnson,H.
:Usingandmanagingmultiplepasswords:Aweektoaview.
InteractingwithComputers23(3),256–267(2011)27.
Hayashi,E.
,Hong,J.
I.
:ADiaryStudyofPasswordUsageinDailyLife.
In:ProceedingsoftheSIGCHIConferenceonHumanFactorsinComputingSystems,pp.
2627–2630.
ACM(2011)28.
Keith,M.
,Shao,B.
,Steinbart,P.
:ABehavioralAnalysisofPassphraseDesignandEffectiveness.
JournaloftheAssociationforInformationSystems10(2),63–89(2009)29.
Stanton,B.
,Greene,K.
K.
:CharacterStrings,MemoryandPasswords:WhataRecallStudyCanTellUs.
In:Proceedingsofthe16thInternationalConferenceonHuman-ComputerInteraction(inpress,2014)
- rulekaspersky.com相关文档
- T1105kaspersky.com
- unsecurekaspersky.com
- executingkaspersky.com
- Botnetzeskaspersky.com
- serviceskaspersky.com
- lysiskaspersky.com
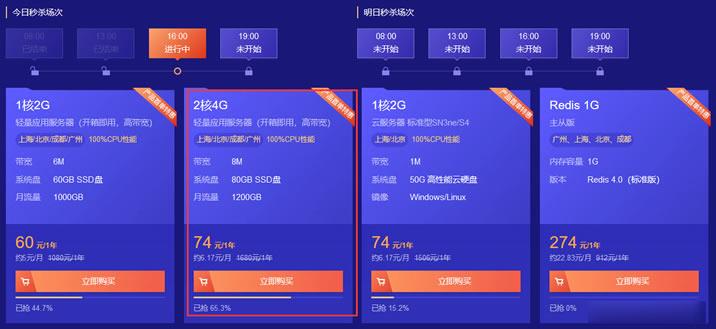
腾讯云轻量服务器两款低价年付套餐 2核4GB内存8M带宽 年74元
昨天,有在"阿里云秋季促销活动 轻量云服务器2G5M配置新购年60元"文章中记录到阿里云轻量服务器2GB内存、5M带宽一年60元的活动,当然这个也是国内机房的。我们很多人都清楚备案是需要接入的,如果我们在其他服务商的域名备案的,那是不能解析的。除非我们不是用来建站,而是用来云端的,是可以用的。这不看到其对手腾讯云也有推出两款轻量服务器活动。其中一款是4GB内存、8M带宽,这个比阿里云还要狠。这个真...
创梦网络-四川大带宽、镇江电信服务器云服务器低至56元
达州创梦网络怎么样,达州创梦网络公司位于四川省达州市,属于四川本地企业,资质齐全,IDC/ISP均有,从创梦网络这边租的服务器均可以备案,属于一手资源,高防机柜、大带宽、高防IP业务,一手整C IP段,四川电信,一手四川托管服务商,成都优化线路,机柜租用、服务器云服务器租用,适合建站做游戏,不须要在套CDN,全国访问快,直连省骨干,大网封UDP,无视UDP攻击,机房集群高达1.2TB,单机可提供1...
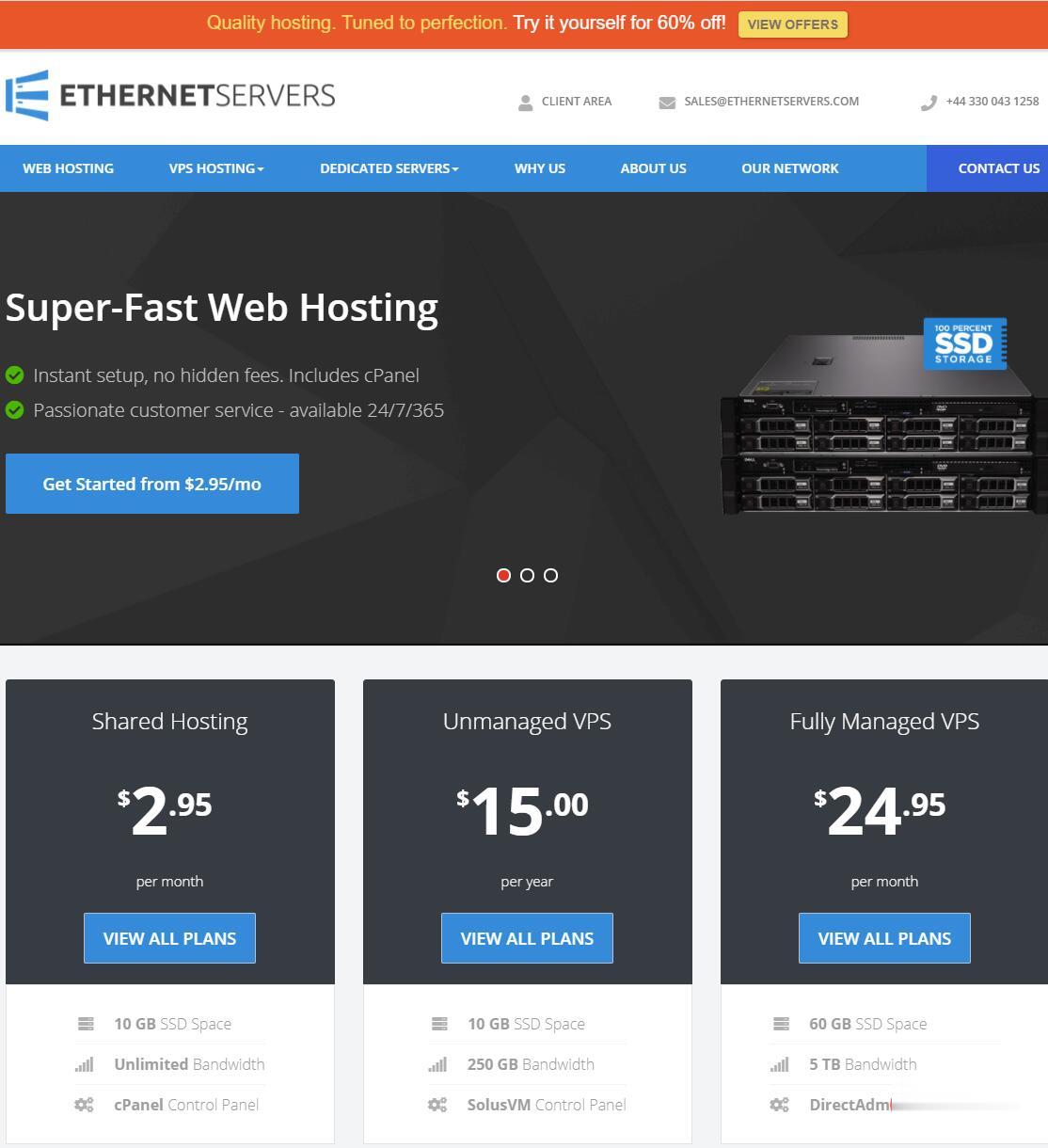
EtherNetservers年付仅10美元,美国洛杉矶VPS/1核512M内存10GB硬盘1Gpbs端口月流量500GB/2个IP
EtherNetservers是一家成立于2013年的英国主机商,提供基于OpenVZ和KVM架构的VPS,数据中心包括美国洛杉矶、新泽西和杰克逊维尔,商家支持使用PayPal、支付宝等付款方式,提供 60 天退款保证,这在IDC行业来说很少见,也可见商家对自家产品很有信心。有需要便宜VPS、多IP VPS的朋友可以关注一下。优惠码SUMMER-VPS-15 (终身 15% 的折扣)SUMMER-...
kaspersky.com为你推荐
-
地陷裂口地陷前期会有什么征兆吗?psbc.com邮政银行卡6215995915000241921是哪个地区的www.yahoo.com.hk香港有什么网页抓站工具一起来捉妖神行抓妖辅助工具都有哪些?广告法中华人民共和国广告法中,有哪些广告不得发布?19ise.com欲火难耐看什么电影 19部性感至极的佳片梦遗姐我和亲姐姐发生关系了175qq.comhttp://www.qq10008.com/这个网页是真的吗?百度关键字百度推广中关键词匹配方式分为哪几种?邯郸纠风网河北邯郸有几个县个名单非法集资