2.www.k8k8.com
www.k8k8.com 时间:2021-03-20 阅读:()
TITLE:PracticalCryptography:PrivacyforBusinessandE-commerceINSTRUCTOR:FrederickM.
Avolio,independentsecurityconsultantSUMMARYOFTOPICS:UpFront—DefiningTermsBasicsofCryptography—typesandmethods,Applications—PrivateMessaging(E-mail)FilesandDirectoriesStrongUserAuthenticationVirtualPrivateNetworksWebSitesElectronicCommerceNextSteps1PracticalCryptography:AnOverviewFrederickM.
Avolio7/13/98Copyright1998FrederickM.
Avolio2Shameless(butbrief)MarketingAvolioConsulting,http://www.
avolio.
com/–NetworkandcomputersecurityTrainingPolicyandProceduredevelopmentProductReviewandAnalysis–ProductMarketing,technicalassistance–E-mailsystemdesign,configuration,andtraining–Writing:whitepapers,tutorials,productreviews7/13/98Copyright1998FrederickM.
Avolio3SyllabusDefiningTermsBasicsofCryptographyPrivateMessaging(E-mail)FilesandDirectoriesStrongUserAuthenticationVirtualPrivateNetworksWebSitesElectronicCommerce7/13/98Copyright1998FrederickM.
Avolio4DefiningTermsConcernFraudUnauthorizedaccessSnoopingMessageAlterationDisavowalRequirementAuthenticationAuthorizationPrivacyDataIntegrityNon-RepudiationFromUnderstandingDigitalSignaturesbyGailGrant,McGraw-Hill,19977/13/98Copyright1998FrederickM.
Avolio5AuthenticationandIntegrityGuaranteetoReceiverKnowsidentityofsenderMessagenotalteredNotundulydelayedFromInternetSecuritypresentationatWICSbyWhitDiffie7/13/98Copyright1998FrederickM.
Avolio6PrivacyorConfidentialityGuaranteetoSenderAuthorizedreceiversonlyFromInternetSecuritypresentationatWICSbyWhitDiffie7/13/98Copyright1998FrederickM.
Avolio7BusinessNeedsforCryptoPrivacyMostbusinesses(andgovernments)don'tneedlong-termsecurityMailinglists,businessplans,negotiations,productR&DCommerceprivacyneedsaremoderateFinancialinformationmightneedtobesecureforadecadeExceptionsareembarrassments:personal,political,businessFromInternetSecuritypresentationatWICSbyBruceSchneier7/13/98Copyright1998FrederickM.
Avolio8BusinessNeedsforCryptoAuthenticationAuthenticatingsessionsversustransactionsNeedforaudittraildependsonapplicationAudittrailmustbeusableincourtwhilenotcompromisingthefuturesecurityofthesystemFromInternetSecuritypresentationatWICSbyBruceSchneier7/13/98Copyright1998FrederickM.
Avolio9BasicCryptographySecretkeyorsymmetricencryptionPublickeyorassymmetricencryptionOne-wayhashfunctions7/13/98Copyright1998FrederickM.
Avolio10EncryptionSecret-Key(Symmetric)Nowisthetimeforallgoodmen.
.
.
sd84$2*q}59(o32nvt-=gf]|@l^.
.
.
DecryptionEncryptionNowisthetimeforallgoodmen.
.
.
7/13/98Copyright1998FrederickM.
Avolio11EncryptionSecret-Key(Symmetric)BobencryptshismessagestoTedwiththeirsharedsecretkeyTeddecryptsmessagesfromBobwiththesamesecretkey.
7/13/98Copyright1998FrederickM.
Avolio12EncryptionSecret-Key(Symmetric)BobdecryptsTed'smessagesusingtheirsecretkey.
TedsendsmessagesbacktoBobwiththesamesecretkey.
7/13/98Copyright1998FrederickM.
Avolio13EncryptionPublic-Key(Asymmetric)Nowisthetimeforallgoodmen.
.
.
sd84$2*q}59(o32nvt-=gf]|@l^.
.
.
DecryptionEncryptionNowisthetimeforallgoodmen.
.
.
7/13/98Copyright1998FrederickM.
Avolio14EncryptionPublic-Key(Asymmetric)Carol,Ted,Bob,andAliceposttheirpublickeysandkeeptheirprivatekeyssecret7/13/98Copyright1998FrederickM.
Avolio15EncryptionPublic-Key(Asymmetric)TedBobAliceCarol'sPublicKeyCarol'sPublicKeyCarol'sPublicKeyCaroldecryptsthesemessagesusingherprivatekey7/13/98Copyright1998FrederickM.
Avolio16EncryptionPublic-Key(Asymmetric)Ted'spublickeyBob'spublickeyAlice'spublickeyCarolrepliestomessagesusingeachrecipient'spublickeyTedBobAliceTed'sprivatekeyBob'sprivatekeyAlice'sprivatekey7/13/98Copyright1998FrederickM.
Avolio17HashFunctionsConvertsastringofdataofanysizeintoafixed-lengthhashNowaytogobackwardsE.
g.
,afingerprintChancesofanytwostringsofdatahashingtothesamevaluevery,verysmall.
Thisisveryimportant!
7/13/98Copyright1998FrederickM.
Avolio18HashFunctionsMD5Messagetextofarbitrarysize.
.
.
MessageTextHashofMessageofshort,fixedsize7/13/98Copyright1998FrederickM.
Avolio19SecurityProblemsSolvedbyCryptographyPrivacyofstoreddata,messages,andconversationsSecureelectroniccommerceTransactionnon-repudiationUseranddataauthenticationE-mailsecurityMulti-partycontrolSecureauditlogsFromInternetSecuritypresentationatWICSbyBruceSchneier7/13/98Copyright1998FrederickM.
Avolio20ApplicationExamplesE-mailUserAuthenticationPrivacyforFilesandDirectoriesVirtualPrivateNetworksWebSiteSecurity7/13/98Copyright1998FrederickM.
Avolio21PrivateE-mailTheGoalsConfidentialityAuthenticationNon-repudiationSecuringE-mailaswellorbetterthanpostalmail!
7/13/98Copyright1998FrederickM.
Avolio22IntegrityandAuthentication1.
MessageSignatureMD5RSANowisthetimeforallgoodmen.
.
.
Sender'sPrivateKeyMessageTextHashofMessage7/13/98Copyright1998FrederickM.
Avolio23IntegrityandAuthentication2.
DatatoSendNowisthetimeforallgoodmen.
.
.
MessageSignatureMessageText7/13/98Copyright1998FrederickM.
Avolio24DigitallySignedMessageTO:sysadminFrom:avolio@tis.
com-----BEGINPGPSIGNEDMESSAGE-----PleasecompletethedeploymentofthePGPsoftwaretoallemployees.
Fred,CSO-----BEGINPGPSIGNATURE-----Version:4.
5iQCVAgUBM+ZICTGr72+Les/dAQHmhwP/WorAeL6LzTJJre6lU77oPkNxYS+izmnM1ozOHxVD6pDlEu7pgsju0g3yRO6tKxN4uJRW5ZeOUtVEgBw+dgFptuOSD9cmDAgSw3SAEFwp9C6cPO0L9MMbc+eps3w8GKLlZkYRZPuANom0ggbmRpqDkjMIU25yEUr5Vj/P54ZuaRY==zu3P-----ENDPGPSIGNATURE--—7/13/98Copyright1998FrederickM.
Avolio25IntegrityandAuthenticationHowcananyonevalidateintegrityandauthenticatesenderMD5RSASender'sPublicKeyCompareRSANowisthetimeforallgoodmen.
.
.
MessageTextMessageSignature7/13/98Copyright1998FrederickM.
Avolio26TO:sysadminFrom:avolio@tis.
com-----BEGINPGPSIGNEDMESSAGE-----PleasecompletethedeploymentofthePGPsoftwaretoallemployees.
Fred,CSO-----BEGINPGPSIGNATURE-----Version:4.
5iQCVAgUBM+ZICTGr72+Les/dAQHmhwP/WorAeL6LzTJJre6lU77oPkNxYS+izmnM1ozOHxVD6pDlEu7pgsju0g3yRO6tKxN4uJRW5ZeOUtVEgBw+dgFptuOSD9cmDAgSw3SAEFwp9C6cPO0L9MMbc+eps3w8GKLlZkYRZPuANom0ggbmRpqDkjMIU25yEUr5Vj/P54ZuaRY==zu3P-----ENDPGPSIGNATURE--—CheckingaSignedMessage7/13/98Copyright1998FrederickM.
Avolio27EncryptionHybridSystemsSymmetrickeyisfastforencryption,butdistributingkeysisdifficultPublickeyisgoodforkeydistribution,butslowatencryptionSolution:usepublickeycryptoasasecuremeansofdistributingthekeysforsymmetricencryption7/13/98Copyright1998FrederickM.
Avolio28AddingPrivacy1.
EncryptedMessageDESRandomkeyNowisthetimeforallgoodmen.
.
.
s5%lk)@slm#]l0|;k^nb[wepqs.
.
.
MessageText7/13/98Copyright1998FrederickM.
Avolio29AddingPrivacy2.
RandomkeyEncryptedkeyRSARecipient'sPublicKey7/13/98Copyright1998FrederickM.
Avolio30AddingPrivacy3.
MD5RSANowisthetimeforallgoodmen.
.
.
Sender'sPrivateKeyMessageSignatureMessageText7/13/98Copyright1998FrederickM.
Avolio31AddingPrivacy4.
EncryptedMessageDatatoSendEncryptedkeys5%lk)@slm#]l0|;k^nb[wepqs.
.
.
MessageSignature7/13/98Copyright1998FrederickM.
Avolio32AddingPrivacyHowcantherecipient(andonlytherecipient)decrypt–DESkeyisencryptedwithrecipientspublickey–Recipientdecryptswithprivatekey(onlyrecipienthasthis)–DESkeyisappliedtoencryptedmessage–Theresultistheclear-textmessage7/13/98Copyright1998FrederickM.
Avolio33SampleEncryptedMessageDate:Tue,08Jul199716:39:25-0400To:user@domainFrom:FrederickMAvolio-----BEGINPGPMESSAGE-----hIwCMavvb4t6z90BA/42UOAdWvnzfhRG2xXyYe203CISLsn2O39vM/y640hNbSl7U29aNGZFfLMRGn7eLZG43SWwBz4cHjphG6iAzeLftRgHkLggxXA9VpGki5PyNID9B0rk4TpRVE3qzgTbdio69aMlK6BdAQ4zWkyxSCi0oR3Vpnh+VVZyOVyaX8etlYRMAvUTsuDYCkr1AQH+OlA4ntqhxoPP/SJpKm5ugMLYiiij8ak8V90a8IYMkYB0CzMrliOJ6ZZxQm1x8orgjL/6Bm5EoSvN4eCCeA/xXKYAAAHXLhG47kVhJkjlPrI/U/sr2aQEm6r+aU1s0ziU1LxF2c5DAW6cD5b4xH+EbvYrnQQJClNMh9y03SjviXvnqFDCO4M70u3iLC50+em4PouqM1DZdoW8O5pb=vhFx-----ENDPGPMESSAGE-----7/13/98Copyright1998FrederickM.
Avolio34Date:Tue,08Jul199716:39:25-0400To:user@domainFrom:FrederickMAvolio-----BEGINPGPMESSAGE-----hIwCMavvb4t6z90BA/42UOAdWvnzfhRG2xXyYe203CISLsn2O39vM/y640hNbSl7U29aNGZFfLMRGn7eLZG43SWwBz4cHjphG6iAzeLftRgHkLggxXA9VpGki5PyNID9B0rk4TpRVE3qzgTbdio69aMlK6BdAQ4zWkyxSCi0oR3Vpnh+VVZyOVyaX8etlYRMAvUTsuDYCkr1AQH+OlA4ntqhxoPP/SJpKm5ugMLYiiij8ak8V90a8IYMkYB0CzMrliOJ6ZZxQm1x8orgjL/6Bm5EoSvN4eCCeA/xXKYAAAHXLhG47kVhJkjlPrI/U/sr2aQEm6r+aU1s0ziU1LxF2c5DAW6cD5b4xH+EbvYrnQQJClNMh9y03SjviXvnqFDCO4M70u3iLC50+em4PouqM1DZdoW8O5pb=vhFx-----ENDPGPMESSAGE-----SampleEncryptedMessage7/13/98Copyright1998FrederickM.
Avolio35SampleEncryptedMessageTO:user@domainFrom:avolio@tis.
comWehavedeployedthePGPmailsoftwareandhavecompletedtraining.
Fred7/13/98Copyright1998FrederickM.
Avolio36SampleEncryptedMessageTO:user@domainFrom:avolio@tis.
comWehavedeployedthePGPmailsoftwareandhavecompletedtraining.
Fred7/13/98Copyright1998FrederickM.
Avolio37FilesandDirectoriesTheGoalsSealdatafilesfromunauthorizedaccessoralteration(reading,writing,etc.
)7/13/98Copyright1998FrederickM.
Avolio38FilesandDirectoriesSimilartoE-mailconcernsandsolutionsEncryptafilewithasymmetrickeyEncryptafilewithYOURpublickeyLikelockingdrawersinadeskoffilecabinetDesertStorm…7/13/98Copyright1998FrederickM.
Avolio39FilesandDirectories7/13/98Copyright1998FrederickM.
Avolio40FilesandDirectoriesNeedtobebuiltintofilesystemNeedtobebuiltintoapplicationsOpen—automaticallydecryptifencryptedClose—automaticallyencryptifwasencrypted(anddeletecleartext)Closewithencrypt7/13/98Copyright1998FrederickM.
Avolio41StrongUserAuthenticationThegoals"Toestablishthevalidityofaclaimedidentityortoprovideprotectionagainstfraudulenttransactionsbyestablishingthevalidityof.
.
.
[the]individual.
.
.
"—NCSC"RedBook"Toidentifyinawaythatisnotvulnerabletoareplayattack7/13/98Copyright1998FrederickM.
Avolio42ReplayAttackUsername:fredPassword:lisa%7/13/98Copyright1998FrederickM.
Avolio43Stronguserauthentication–SmartcardsortokensSoftware(server)andsmartcardbasedPIN-protectedsmartcardprivatekeySystemissueschallengebasedonuserUserusespasswordtounlocksmartcard,whichreadschallenge,calculatescryptographicresponseResponseisusedasresponsetochallengeAuthenticationTechniques7/13/98Copyright1998FrederickM.
Avolio44AuthenticationTechniquesChallenge:"876261"ServersendsUser"unlocks"authenticationtokenbykeyinginPersonalIdentificationNumberUserenterschallengeintoauthenticationtokenTokenreturnsanencryptedresponsetothechallenge"722512""1105""876261"UserrespondstoserverwithuniqueresponseServercomparesresponse"722512"(Serverandtokenshareasecretencryptionkeythatuserneverhasaccessto)(Secretkey:"0x8A5F42")7/13/98Copyright1998FrederickM.
Avolio45VirtualPrivateNetworksThegoalsPrivacyofcommunicationbetweensecureenclavesoveranuntrustednetworkPrivacyandaccessforremoteemployeesPrivacyandcontrolledaccessforremoteclients7/13/98Copyright1998FrederickM.
Avolio46Encryption—"VirtualPrivateNetworks"and"VirtualNetworkPerimeters"LANALANALANBLANBPrivacy7/13/98Copyright1998FrederickM.
Avolio47VirtualPrivateNetworksFirewall-to-firewallconnectionsovertheInternet.
Usingencrypted"tunnels"overtheInternettoconnectLANsandWANscanreducecosts23-50%(USComputerMarch1996).
SecureWideAreaNetworking(S/WAN).
IPv6,end-to-endencryption,IPSECFirewall-to-firewallconnectionsovertheInternet.
Usingencrypted"tunnels"overtheInternettoconnectLANsandWANscanreducecosts23-50%(USComputerMarch1996).
SecureWideAreaNetworking(S/WAN).
IPv6,end-to-endencryption,IPSEC7/13/98Copyright1998FrederickM.
Avolio48ExtendingthePerimeterPublicNetworkVirtualNetworkPerimeter7/13/98Copyright1998FrederickM.
Avolio49GlobalVPNsKeyIssues–TheInternetisaworldwidenetwork–Companiescrossinternationalboundries–Partnershipscrossinternationalboundries–Privacyinbusinesstransactionsiscriticaltosuccess–NetworkcommunicationsprivacymeansemployingencryptionKeyIssues–TheInternetisaworldwidenetwork–Companiescrossinternationalboundries–Partnershipscrossinternationalboundries–Privacyinbusinesstransactionsiscriticaltosuccess–Networkcommunicationsprivacymeansemployingencryption7/13/98Copyright1998FrederickM.
Avolio50GlobalVPNsEncryptionRequirementsStrong(56bitorbetterkeylength)ExportablePlatformindependentEncryptionRequirementsStrong(56bitorbetterkeylength)ExportablePlatformindependent7/13/98Copyright1998FrederickM.
Avolio51WebSiteSecurityThegoalsDeploymentofwebsitesforinternalandexternaluseProtectionfrommodificationAssurancedatahasnotbeenmodifiedControlofaccess7/13/98Copyright1998FrederickM.
Avolio52WebSiteSecurityWebsiteattacksCIADOJNASAUSAFSingaporeGovernmentNationofIslamMGMStudios7/13/98Copyright1998FrederickM.
Avolio53WebSiteSecurityMessagehashofallfilesonwebsitekept–Periodiccheckingofstoredhashagainsthashofpages—integritycheckingDigitallysignpages,documents,software–Assuranceforusersthatdatahasnotbeenmodified7/13/98Copyright1998FrederickM.
Avolio54WebSiteSecurityControlledaccess–Stronguserauthentication–Usernameandpasswordoverprotectedchannel7/13/98Copyright1998FrederickM.
Avolio55WebSiteSecurityftp://info.
cert.
org/pub/cert_advisories/CA-97.
20.
javascript:-----BEGINPGPSIGNEDMESSAGE-----CERT*AdvisoryCA-97.
20Originalissuedate:July8,1997Lastrevised:July28,1997,AppendixA-addedinformationforHewlett-PackardandIBM.
SectionIII.
A-slightwordingchange.
Acompleterevisionhistoryisattheendofthisfile.
Topic:JavaScriptVulnerability…-----BEGINPGPSIGNATURE-----Version:2.
6.
2iQCVAwUBM9yyN3VP+x0t4w7BAQFLAgP/Z1moGK6SI2Q3OBbV/fpCOcW2J9TdXE3/UHuZ7vHCjKDWxelHr5551JQ9i19s6sVBNDOX1W031IrlS36nIblp3vX4rVuAaufwVOxqxYg44i3gxsC8NgC/HW5j7KHsOiGzoRmU5a+vWyLmmged+Y2wBDrxGeqbHacE4S6FPph4/w8==5MP2-----ENDPGPSIGNATURE-----7/13/98Copyright1998FrederickM.
Avolio56E-CommerceTransactionsecurity–Privacyofasale–IntegrityofasaleElectronicpayment–Privacy–Integrity–ProvenanceofanagreementtotransferfundsFromWebSecuritySourcebookbyRubin,atal,JohnWiley&Sons,19977/13/98Copyright1998FrederickM.
Avolio57TransactionSecurityVirtualPrivateNetworkapproach–Encryptionandauthenticationdoneaspartofthenetworkcommunication–Networksoftwaremustbemodified–UsersneednotmodifybehaviororapplicationsoftwareFromWebSecuritySourcebookbyRubin,atal,JohnWiley&Sons,19977/13/98Copyright1998FrederickM.
Avolio58TransactionSecurityApplication-levelencryption–OSandplatformindependent–Nodataisexposedbetweenclientandserversoftware–MostwebbrowsersareusingthistypeofsecuritySSL,SHTTPFromWebSecuritySourcebookbyRubin,atal,JohnWiley&Sons,19977/13/98Copyright1998FrederickM.
Avolio59TransactionSecurityApplication-levelencryption–Browserandservershakehandsanddecideonencryptionschemeandkey–Dataistransmittedencryptedwiththekey–Theyshakehandsattheend.
FromWebSecuritySourcebookbyRubin,atal,JohnWiley&Sons,1997ThisisthemeaningofthefilledinkeyontheNetscapebrowsers.
7/13/98Copyright1998FrederickM.
Avolio60TransactionSecurityMoste-commercetodayusesapplication-leveltransactionsecurityMosttransactionsecuritytodayprotectsprivacyofthedatasentfromtheclient–Orderblanksorquestionnaires–CreditCardnumbersMoste-commerceontheInternettodayisliketelephonecatalogorderingwithoutthecatalogortelephone7/13/98Copyright1998FrederickM.
Avolio617/13/98Copyright1998FrederickM.
Avolio627/13/98Copyright1998FrederickM.
Avolio63ElectronicPaymentSecurepaymentprotocolsexistMostinvolveatrustedthirdentityactingasagatewaytofinancialnetworksordirectlytoabank7/13/98Copyright1998FrederickM.
Avolio64WheredowegofromhereOr,whatmoreisneeded7/13/98Copyright1998FrederickM.
Avolio65InfrastructureNeededPublicKeyInfrastructureKeycreationKeydistributionKeycertificationKeylookupKeyrevocationLocallyandGlobally7/13/98Copyright1998FrederickM.
Avolio66CertificatesAmessageName,e-mail,publickey-----BEGINPGPPUBLICKEYBLOCK-----Version:4.
5mQCNAjPmUEIAAAEEAMj14c0xswae9XfbMVQeDFq8OVf29+N1745Hey5vkYw7UZUn7K1ehDYK44W+f1Y/Ns4g3lFJNxuFRbPZXUPAc8dlPiBR1xq+wqcoOIm+gpQEd5Dl1EgsUyE+3Si0WQ6zELRvKCWKww6/8egKDaMqQTgMqZFQEqjRFEvspjTJR9s3AAURtAt1c2VyQGRvbWFpbg===Cexv-----ENDPGPPUBLICKEYBLOCK-----7/13/98Copyright1998FrederickM.
Avolio67CertificateSignedbysomeonetrustworthyFredAvolioPublicKey:dhe34j3ffhhej3457/13/98Copyright1998FrederickM.
Avolio68SummaryandReview7/13/98Copyright1998FrederickM.
Avolio69EncryptionUsesEncryptionistheencodingofinformationandcanbeusedatmanydifferentpoints:–Fileencryptionforstorage(e.
g.
.
,forlaptops)–PrivateE-mail–DigitalsignaturesforDoctorOrders–Integritycheckingforchangestopatientrecords–EncrypteddataintransitRoutertorouterencryptionFirewalltofirewallencryptionattheIPlevel7/13/98Copyright1998FrederickM.
Avolio70EncryptionApplicationsAccessControl–UsecryptographicfunctionstodistributeaccesscontrollistsandprivilegesAuthentication–DigitalSignaturesprovidepositiveproofofidentity–Digitalcertificatesusedtobindpublickeytophysicalidentity7/13/98Copyright1998FrederickM.
Avolio71EncryptionApplicationsNon-repudiation–CryptographicfunctionsusetoprovideunforgeableproofofreceiptorauthorshipAvailability–Combinationofapplicationsusedtoreducethechancesofdenialofserviceormalicioussystemoutages7/13/98Copyright1998FrederickM.
Avolio72BasicToolsofCryptographySymmetricencryption–ProvidessecrecyamongpartieswhoshareacommonkeyMessageauthenticationcodes–ProvidesintegritycheckingandauthenticationPublic-keyencryption–Allowssomeonetoreceivesecretmessagefrompeoplehe'snevermet–AllowsmethodofexchangingsecretkeysDigitalsignatureschemes–Establishesintegrity,authenticity,andnon-repudiationSecurehashfunctions–UsedtoreduceamessagetoafixedsizeforsignatureFromInternetSecuritypresentationatWICSbyBruceSchneier73PracticalCryptography:AnOverviewFrederickM.
Avolio
Avolio,independentsecurityconsultantSUMMARYOFTOPICS:UpFront—DefiningTermsBasicsofCryptography—typesandmethods,Applications—PrivateMessaging(E-mail)FilesandDirectoriesStrongUserAuthenticationVirtualPrivateNetworksWebSitesElectronicCommerceNextSteps1PracticalCryptography:AnOverviewFrederickM.
Avolio7/13/98Copyright1998FrederickM.
Avolio2Shameless(butbrief)MarketingAvolioConsulting,http://www.
avolio.
com/–NetworkandcomputersecurityTrainingPolicyandProceduredevelopmentProductReviewandAnalysis–ProductMarketing,technicalassistance–E-mailsystemdesign,configuration,andtraining–Writing:whitepapers,tutorials,productreviews7/13/98Copyright1998FrederickM.
Avolio3SyllabusDefiningTermsBasicsofCryptographyPrivateMessaging(E-mail)FilesandDirectoriesStrongUserAuthenticationVirtualPrivateNetworksWebSitesElectronicCommerce7/13/98Copyright1998FrederickM.
Avolio4DefiningTermsConcernFraudUnauthorizedaccessSnoopingMessageAlterationDisavowalRequirementAuthenticationAuthorizationPrivacyDataIntegrityNon-RepudiationFromUnderstandingDigitalSignaturesbyGailGrant,McGraw-Hill,19977/13/98Copyright1998FrederickM.
Avolio5AuthenticationandIntegrityGuaranteetoReceiverKnowsidentityofsenderMessagenotalteredNotundulydelayedFromInternetSecuritypresentationatWICSbyWhitDiffie7/13/98Copyright1998FrederickM.
Avolio6PrivacyorConfidentialityGuaranteetoSenderAuthorizedreceiversonlyFromInternetSecuritypresentationatWICSbyWhitDiffie7/13/98Copyright1998FrederickM.
Avolio7BusinessNeedsforCryptoPrivacyMostbusinesses(andgovernments)don'tneedlong-termsecurityMailinglists,businessplans,negotiations,productR&DCommerceprivacyneedsaremoderateFinancialinformationmightneedtobesecureforadecadeExceptionsareembarrassments:personal,political,businessFromInternetSecuritypresentationatWICSbyBruceSchneier7/13/98Copyright1998FrederickM.
Avolio8BusinessNeedsforCryptoAuthenticationAuthenticatingsessionsversustransactionsNeedforaudittraildependsonapplicationAudittrailmustbeusableincourtwhilenotcompromisingthefuturesecurityofthesystemFromInternetSecuritypresentationatWICSbyBruceSchneier7/13/98Copyright1998FrederickM.
Avolio9BasicCryptographySecretkeyorsymmetricencryptionPublickeyorassymmetricencryptionOne-wayhashfunctions7/13/98Copyright1998FrederickM.
Avolio10EncryptionSecret-Key(Symmetric)Nowisthetimeforallgoodmen.
.
.
sd84$2*q}59(o32nvt-=gf]|@l^.
.
.
DecryptionEncryptionNowisthetimeforallgoodmen.
.
.
7/13/98Copyright1998FrederickM.
Avolio11EncryptionSecret-Key(Symmetric)BobencryptshismessagestoTedwiththeirsharedsecretkeyTeddecryptsmessagesfromBobwiththesamesecretkey.
7/13/98Copyright1998FrederickM.
Avolio12EncryptionSecret-Key(Symmetric)BobdecryptsTed'smessagesusingtheirsecretkey.
TedsendsmessagesbacktoBobwiththesamesecretkey.
7/13/98Copyright1998FrederickM.
Avolio13EncryptionPublic-Key(Asymmetric)Nowisthetimeforallgoodmen.
.
.
sd84$2*q}59(o32nvt-=gf]|@l^.
.
.
DecryptionEncryptionNowisthetimeforallgoodmen.
.
.
7/13/98Copyright1998FrederickM.
Avolio14EncryptionPublic-Key(Asymmetric)Carol,Ted,Bob,andAliceposttheirpublickeysandkeeptheirprivatekeyssecret7/13/98Copyright1998FrederickM.
Avolio15EncryptionPublic-Key(Asymmetric)TedBobAliceCarol'sPublicKeyCarol'sPublicKeyCarol'sPublicKeyCaroldecryptsthesemessagesusingherprivatekey7/13/98Copyright1998FrederickM.
Avolio16EncryptionPublic-Key(Asymmetric)Ted'spublickeyBob'spublickeyAlice'spublickeyCarolrepliestomessagesusingeachrecipient'spublickeyTedBobAliceTed'sprivatekeyBob'sprivatekeyAlice'sprivatekey7/13/98Copyright1998FrederickM.
Avolio17HashFunctionsConvertsastringofdataofanysizeintoafixed-lengthhashNowaytogobackwardsE.
g.
,afingerprintChancesofanytwostringsofdatahashingtothesamevaluevery,verysmall.
Thisisveryimportant!
7/13/98Copyright1998FrederickM.
Avolio18HashFunctionsMD5Messagetextofarbitrarysize.
.
.
MessageTextHashofMessageofshort,fixedsize7/13/98Copyright1998FrederickM.
Avolio19SecurityProblemsSolvedbyCryptographyPrivacyofstoreddata,messages,andconversationsSecureelectroniccommerceTransactionnon-repudiationUseranddataauthenticationE-mailsecurityMulti-partycontrolSecureauditlogsFromInternetSecuritypresentationatWICSbyBruceSchneier7/13/98Copyright1998FrederickM.
Avolio20ApplicationExamplesE-mailUserAuthenticationPrivacyforFilesandDirectoriesVirtualPrivateNetworksWebSiteSecurity7/13/98Copyright1998FrederickM.
Avolio21PrivateE-mailTheGoalsConfidentialityAuthenticationNon-repudiationSecuringE-mailaswellorbetterthanpostalmail!
7/13/98Copyright1998FrederickM.
Avolio22IntegrityandAuthentication1.
MessageSignatureMD5RSANowisthetimeforallgoodmen.
.
.
Sender'sPrivateKeyMessageTextHashofMessage7/13/98Copyright1998FrederickM.
Avolio23IntegrityandAuthentication2.
DatatoSendNowisthetimeforallgoodmen.
.
.
MessageSignatureMessageText7/13/98Copyright1998FrederickM.
Avolio24DigitallySignedMessageTO:sysadminFrom:avolio@tis.
com-----BEGINPGPSIGNEDMESSAGE-----PleasecompletethedeploymentofthePGPsoftwaretoallemployees.
Fred,CSO-----BEGINPGPSIGNATURE-----Version:4.
5iQCVAgUBM+ZICTGr72+Les/dAQHmhwP/WorAeL6LzTJJre6lU77oPkNxYS+izmnM1ozOHxVD6pDlEu7pgsju0g3yRO6tKxN4uJRW5ZeOUtVEgBw+dgFptuOSD9cmDAgSw3SAEFwp9C6cPO0L9MMbc+eps3w8GKLlZkYRZPuANom0ggbmRpqDkjMIU25yEUr5Vj/P54ZuaRY==zu3P-----ENDPGPSIGNATURE--—7/13/98Copyright1998FrederickM.
Avolio25IntegrityandAuthenticationHowcananyonevalidateintegrityandauthenticatesenderMD5RSASender'sPublicKeyCompareRSANowisthetimeforallgoodmen.
.
.
MessageTextMessageSignature7/13/98Copyright1998FrederickM.
Avolio26TO:sysadminFrom:avolio@tis.
com-----BEGINPGPSIGNEDMESSAGE-----PleasecompletethedeploymentofthePGPsoftwaretoallemployees.
Fred,CSO-----BEGINPGPSIGNATURE-----Version:4.
5iQCVAgUBM+ZICTGr72+Les/dAQHmhwP/WorAeL6LzTJJre6lU77oPkNxYS+izmnM1ozOHxVD6pDlEu7pgsju0g3yRO6tKxN4uJRW5ZeOUtVEgBw+dgFptuOSD9cmDAgSw3SAEFwp9C6cPO0L9MMbc+eps3w8GKLlZkYRZPuANom0ggbmRpqDkjMIU25yEUr5Vj/P54ZuaRY==zu3P-----ENDPGPSIGNATURE--—CheckingaSignedMessage7/13/98Copyright1998FrederickM.
Avolio27EncryptionHybridSystemsSymmetrickeyisfastforencryption,butdistributingkeysisdifficultPublickeyisgoodforkeydistribution,butslowatencryptionSolution:usepublickeycryptoasasecuremeansofdistributingthekeysforsymmetricencryption7/13/98Copyright1998FrederickM.
Avolio28AddingPrivacy1.
EncryptedMessageDESRandomkeyNowisthetimeforallgoodmen.
.
.
s5%lk)@slm#]l0|;k^nb[wepqs.
.
.
MessageText7/13/98Copyright1998FrederickM.
Avolio29AddingPrivacy2.
RandomkeyEncryptedkeyRSARecipient'sPublicKey7/13/98Copyright1998FrederickM.
Avolio30AddingPrivacy3.
MD5RSANowisthetimeforallgoodmen.
.
.
Sender'sPrivateKeyMessageSignatureMessageText7/13/98Copyright1998FrederickM.
Avolio31AddingPrivacy4.
EncryptedMessageDatatoSendEncryptedkeys5%lk)@slm#]l0|;k^nb[wepqs.
.
.
MessageSignature7/13/98Copyright1998FrederickM.
Avolio32AddingPrivacyHowcantherecipient(andonlytherecipient)decrypt–DESkeyisencryptedwithrecipientspublickey–Recipientdecryptswithprivatekey(onlyrecipienthasthis)–DESkeyisappliedtoencryptedmessage–Theresultistheclear-textmessage7/13/98Copyright1998FrederickM.
Avolio33SampleEncryptedMessageDate:Tue,08Jul199716:39:25-0400To:user@domainFrom:FrederickMAvolio-----BEGINPGPMESSAGE-----hIwCMavvb4t6z90BA/42UOAdWvnzfhRG2xXyYe203CISLsn2O39vM/y640hNbSl7U29aNGZFfLMRGn7eLZG43SWwBz4cHjphG6iAzeLftRgHkLggxXA9VpGki5PyNID9B0rk4TpRVE3qzgTbdio69aMlK6BdAQ4zWkyxSCi0oR3Vpnh+VVZyOVyaX8etlYRMAvUTsuDYCkr1AQH+OlA4ntqhxoPP/SJpKm5ugMLYiiij8ak8V90a8IYMkYB0CzMrliOJ6ZZxQm1x8orgjL/6Bm5EoSvN4eCCeA/xXKYAAAHXLhG47kVhJkjlPrI/U/sr2aQEm6r+aU1s0ziU1LxF2c5DAW6cD5b4xH+EbvYrnQQJClNMh9y03SjviXvnqFDCO4M70u3iLC50+em4PouqM1DZdoW8O5pb=vhFx-----ENDPGPMESSAGE-----7/13/98Copyright1998FrederickM.
Avolio34Date:Tue,08Jul199716:39:25-0400To:user@domainFrom:FrederickMAvolio-----BEGINPGPMESSAGE-----hIwCMavvb4t6z90BA/42UOAdWvnzfhRG2xXyYe203CISLsn2O39vM/y640hNbSl7U29aNGZFfLMRGn7eLZG43SWwBz4cHjphG6iAzeLftRgHkLggxXA9VpGki5PyNID9B0rk4TpRVE3qzgTbdio69aMlK6BdAQ4zWkyxSCi0oR3Vpnh+VVZyOVyaX8etlYRMAvUTsuDYCkr1AQH+OlA4ntqhxoPP/SJpKm5ugMLYiiij8ak8V90a8IYMkYB0CzMrliOJ6ZZxQm1x8orgjL/6Bm5EoSvN4eCCeA/xXKYAAAHXLhG47kVhJkjlPrI/U/sr2aQEm6r+aU1s0ziU1LxF2c5DAW6cD5b4xH+EbvYrnQQJClNMh9y03SjviXvnqFDCO4M70u3iLC50+em4PouqM1DZdoW8O5pb=vhFx-----ENDPGPMESSAGE-----SampleEncryptedMessage7/13/98Copyright1998FrederickM.
Avolio35SampleEncryptedMessageTO:user@domainFrom:avolio@tis.
comWehavedeployedthePGPmailsoftwareandhavecompletedtraining.
Fred7/13/98Copyright1998FrederickM.
Avolio36SampleEncryptedMessageTO:user@domainFrom:avolio@tis.
comWehavedeployedthePGPmailsoftwareandhavecompletedtraining.
Fred7/13/98Copyright1998FrederickM.
Avolio37FilesandDirectoriesTheGoalsSealdatafilesfromunauthorizedaccessoralteration(reading,writing,etc.
)7/13/98Copyright1998FrederickM.
Avolio38FilesandDirectoriesSimilartoE-mailconcernsandsolutionsEncryptafilewithasymmetrickeyEncryptafilewithYOURpublickeyLikelockingdrawersinadeskoffilecabinetDesertStorm…7/13/98Copyright1998FrederickM.
Avolio39FilesandDirectories7/13/98Copyright1998FrederickM.
Avolio40FilesandDirectoriesNeedtobebuiltintofilesystemNeedtobebuiltintoapplicationsOpen—automaticallydecryptifencryptedClose—automaticallyencryptifwasencrypted(anddeletecleartext)Closewithencrypt7/13/98Copyright1998FrederickM.
Avolio41StrongUserAuthenticationThegoals"Toestablishthevalidityofaclaimedidentityortoprovideprotectionagainstfraudulenttransactionsbyestablishingthevalidityof.
.
.
[the]individual.
.
.
"—NCSC"RedBook"Toidentifyinawaythatisnotvulnerabletoareplayattack7/13/98Copyright1998FrederickM.
Avolio42ReplayAttackUsername:fredPassword:lisa%7/13/98Copyright1998FrederickM.
Avolio43Stronguserauthentication–SmartcardsortokensSoftware(server)andsmartcardbasedPIN-protectedsmartcardprivatekeySystemissueschallengebasedonuserUserusespasswordtounlocksmartcard,whichreadschallenge,calculatescryptographicresponseResponseisusedasresponsetochallengeAuthenticationTechniques7/13/98Copyright1998FrederickM.
Avolio44AuthenticationTechniquesChallenge:"876261"ServersendsUser"unlocks"authenticationtokenbykeyinginPersonalIdentificationNumberUserenterschallengeintoauthenticationtokenTokenreturnsanencryptedresponsetothechallenge"722512""1105""876261"UserrespondstoserverwithuniqueresponseServercomparesresponse"722512"(Serverandtokenshareasecretencryptionkeythatuserneverhasaccessto)(Secretkey:"0x8A5F42")7/13/98Copyright1998FrederickM.
Avolio45VirtualPrivateNetworksThegoalsPrivacyofcommunicationbetweensecureenclavesoveranuntrustednetworkPrivacyandaccessforremoteemployeesPrivacyandcontrolledaccessforremoteclients7/13/98Copyright1998FrederickM.
Avolio46Encryption—"VirtualPrivateNetworks"and"VirtualNetworkPerimeters"LANALANALANBLANBPrivacy7/13/98Copyright1998FrederickM.
Avolio47VirtualPrivateNetworksFirewall-to-firewallconnectionsovertheInternet.
Usingencrypted"tunnels"overtheInternettoconnectLANsandWANscanreducecosts23-50%(USComputerMarch1996).
SecureWideAreaNetworking(S/WAN).
IPv6,end-to-endencryption,IPSECFirewall-to-firewallconnectionsovertheInternet.
Usingencrypted"tunnels"overtheInternettoconnectLANsandWANscanreducecosts23-50%(USComputerMarch1996).
SecureWideAreaNetworking(S/WAN).
IPv6,end-to-endencryption,IPSEC7/13/98Copyright1998FrederickM.
Avolio48ExtendingthePerimeterPublicNetworkVirtualNetworkPerimeter7/13/98Copyright1998FrederickM.
Avolio49GlobalVPNsKeyIssues–TheInternetisaworldwidenetwork–Companiescrossinternationalboundries–Partnershipscrossinternationalboundries–Privacyinbusinesstransactionsiscriticaltosuccess–NetworkcommunicationsprivacymeansemployingencryptionKeyIssues–TheInternetisaworldwidenetwork–Companiescrossinternationalboundries–Partnershipscrossinternationalboundries–Privacyinbusinesstransactionsiscriticaltosuccess–Networkcommunicationsprivacymeansemployingencryption7/13/98Copyright1998FrederickM.
Avolio50GlobalVPNsEncryptionRequirementsStrong(56bitorbetterkeylength)ExportablePlatformindependentEncryptionRequirementsStrong(56bitorbetterkeylength)ExportablePlatformindependent7/13/98Copyright1998FrederickM.
Avolio51WebSiteSecurityThegoalsDeploymentofwebsitesforinternalandexternaluseProtectionfrommodificationAssurancedatahasnotbeenmodifiedControlofaccess7/13/98Copyright1998FrederickM.
Avolio52WebSiteSecurityWebsiteattacksCIADOJNASAUSAFSingaporeGovernmentNationofIslamMGMStudios7/13/98Copyright1998FrederickM.
Avolio53WebSiteSecurityMessagehashofallfilesonwebsitekept–Periodiccheckingofstoredhashagainsthashofpages—integritycheckingDigitallysignpages,documents,software–Assuranceforusersthatdatahasnotbeenmodified7/13/98Copyright1998FrederickM.
Avolio54WebSiteSecurityControlledaccess–Stronguserauthentication–Usernameandpasswordoverprotectedchannel7/13/98Copyright1998FrederickM.
Avolio55WebSiteSecurityftp://info.
cert.
org/pub/cert_advisories/CA-97.
20.
javascript:-----BEGINPGPSIGNEDMESSAGE-----CERT*AdvisoryCA-97.
20Originalissuedate:July8,1997Lastrevised:July28,1997,AppendixA-addedinformationforHewlett-PackardandIBM.
SectionIII.
A-slightwordingchange.
Acompleterevisionhistoryisattheendofthisfile.
Topic:JavaScriptVulnerability…-----BEGINPGPSIGNATURE-----Version:2.
6.
2iQCVAwUBM9yyN3VP+x0t4w7BAQFLAgP/Z1moGK6SI2Q3OBbV/fpCOcW2J9TdXE3/UHuZ7vHCjKDWxelHr5551JQ9i19s6sVBNDOX1W031IrlS36nIblp3vX4rVuAaufwVOxqxYg44i3gxsC8NgC/HW5j7KHsOiGzoRmU5a+vWyLmmged+Y2wBDrxGeqbHacE4S6FPph4/w8==5MP2-----ENDPGPSIGNATURE-----7/13/98Copyright1998FrederickM.
Avolio56E-CommerceTransactionsecurity–Privacyofasale–IntegrityofasaleElectronicpayment–Privacy–Integrity–ProvenanceofanagreementtotransferfundsFromWebSecuritySourcebookbyRubin,atal,JohnWiley&Sons,19977/13/98Copyright1998FrederickM.
Avolio57TransactionSecurityVirtualPrivateNetworkapproach–Encryptionandauthenticationdoneaspartofthenetworkcommunication–Networksoftwaremustbemodified–UsersneednotmodifybehaviororapplicationsoftwareFromWebSecuritySourcebookbyRubin,atal,JohnWiley&Sons,19977/13/98Copyright1998FrederickM.
Avolio58TransactionSecurityApplication-levelencryption–OSandplatformindependent–Nodataisexposedbetweenclientandserversoftware–MostwebbrowsersareusingthistypeofsecuritySSL,SHTTPFromWebSecuritySourcebookbyRubin,atal,JohnWiley&Sons,19977/13/98Copyright1998FrederickM.
Avolio59TransactionSecurityApplication-levelencryption–Browserandservershakehandsanddecideonencryptionschemeandkey–Dataistransmittedencryptedwiththekey–Theyshakehandsattheend.
FromWebSecuritySourcebookbyRubin,atal,JohnWiley&Sons,1997ThisisthemeaningofthefilledinkeyontheNetscapebrowsers.
7/13/98Copyright1998FrederickM.
Avolio60TransactionSecurityMoste-commercetodayusesapplication-leveltransactionsecurityMosttransactionsecuritytodayprotectsprivacyofthedatasentfromtheclient–Orderblanksorquestionnaires–CreditCardnumbersMoste-commerceontheInternettodayisliketelephonecatalogorderingwithoutthecatalogortelephone7/13/98Copyright1998FrederickM.
Avolio617/13/98Copyright1998FrederickM.
Avolio627/13/98Copyright1998FrederickM.
Avolio63ElectronicPaymentSecurepaymentprotocolsexistMostinvolveatrustedthirdentityactingasagatewaytofinancialnetworksordirectlytoabank7/13/98Copyright1998FrederickM.
Avolio64WheredowegofromhereOr,whatmoreisneeded7/13/98Copyright1998FrederickM.
Avolio65InfrastructureNeededPublicKeyInfrastructureKeycreationKeydistributionKeycertificationKeylookupKeyrevocationLocallyandGlobally7/13/98Copyright1998FrederickM.
Avolio66CertificatesAmessageName,e-mail,publickey-----BEGINPGPPUBLICKEYBLOCK-----Version:4.
5mQCNAjPmUEIAAAEEAMj14c0xswae9XfbMVQeDFq8OVf29+N1745Hey5vkYw7UZUn7K1ehDYK44W+f1Y/Ns4g3lFJNxuFRbPZXUPAc8dlPiBR1xq+wqcoOIm+gpQEd5Dl1EgsUyE+3Si0WQ6zELRvKCWKww6/8egKDaMqQTgMqZFQEqjRFEvspjTJR9s3AAURtAt1c2VyQGRvbWFpbg===Cexv-----ENDPGPPUBLICKEYBLOCK-----7/13/98Copyright1998FrederickM.
Avolio67CertificateSignedbysomeonetrustworthyFredAvolioPublicKey:dhe34j3ffhhej3457/13/98Copyright1998FrederickM.
Avolio68SummaryandReview7/13/98Copyright1998FrederickM.
Avolio69EncryptionUsesEncryptionistheencodingofinformationandcanbeusedatmanydifferentpoints:–Fileencryptionforstorage(e.
g.
.
,forlaptops)–PrivateE-mail–DigitalsignaturesforDoctorOrders–Integritycheckingforchangestopatientrecords–EncrypteddataintransitRoutertorouterencryptionFirewalltofirewallencryptionattheIPlevel7/13/98Copyright1998FrederickM.
Avolio70EncryptionApplicationsAccessControl–UsecryptographicfunctionstodistributeaccesscontrollistsandprivilegesAuthentication–DigitalSignaturesprovidepositiveproofofidentity–Digitalcertificatesusedtobindpublickeytophysicalidentity7/13/98Copyright1998FrederickM.
Avolio71EncryptionApplicationsNon-repudiation–CryptographicfunctionsusetoprovideunforgeableproofofreceiptorauthorshipAvailability–Combinationofapplicationsusedtoreducethechancesofdenialofserviceormalicioussystemoutages7/13/98Copyright1998FrederickM.
Avolio72BasicToolsofCryptographySymmetricencryption–ProvidessecrecyamongpartieswhoshareacommonkeyMessageauthenticationcodes–ProvidesintegritycheckingandauthenticationPublic-keyencryption–Allowssomeonetoreceivesecretmessagefrompeoplehe'snevermet–AllowsmethodofexchangingsecretkeysDigitalsignatureschemes–Establishesintegrity,authenticity,andnon-repudiationSecurehashfunctions–UsedtoreduceamessagetoafixedsizeforsignatureFromInternetSecuritypresentationatWICSbyBruceSchneier73PracticalCryptography:AnOverviewFrederickM.
Avolio
- 2.www.k8k8.com相关文档
- Moderatewww.k8k8.com
- recipientswww.k8k8.com
- Packagewww.k8k8.com
- Completewww.k8k8.com
- PHYwww.k8k8.com
- Engineer-to-Engineer
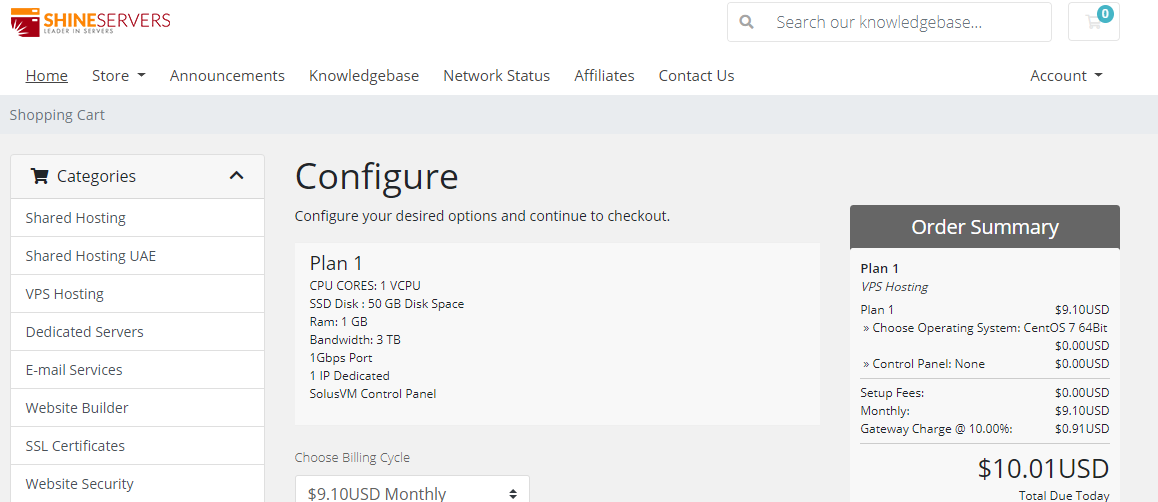
ShineServers(5美元/月)荷兰VPS、阿联酋VPS首月五折/1核1G/50GB硬盘/3TB流量/1Gbps带宽
优惠码50SSDOFF 首月5折50WHTSSD 年付5折15OFF 85折优惠,可循环使用荷兰VPSCPU内存SSD带宽IPv4价格购买1核1G50G1Gbps/3TB1个$ 9.10/月链接2核2G80G1Gbps/5TB1个$ 12.70/月链接2核3G100G1Gbps/7TB1个$ 16.30/月链接3核4G150G1Gbps/10TB1个$ 18.10/月链接阿联酋VPSCPU内存SS...
蓝速数据(58/年)秒杀服务器独立1核2G 1M
蓝速数据金秋上云季2G58/年怎么样?蓝速数据物理机拼团0元购劲爆?蓝速数据服务器秒杀爆产品好不好?蓝速数据是广州五联科技信息有限公司旗下品牌云计算平台、采用国内首选Zkeys公有云建设多种开通方式、具有IDC、ISP从业资格证IDC运营商新老用户值得信赖的商家。我司主要从事内地的枣庄、宿迁、深圳、绍兴、成都(市、县)。待开放地区:北京、广州、十堰、西安、镇江(市、县)。等地区数据中心业务,均KV...
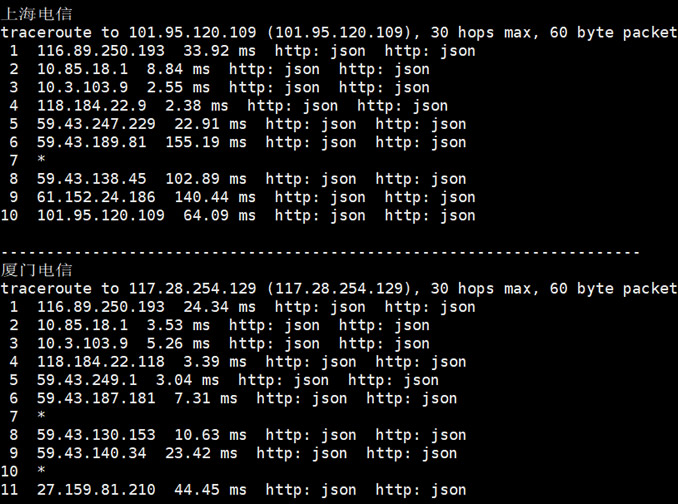
香港2GB内存DIYVM2核(¥50月)香港沙田CN2云服务器
DiyVM 香港沙田机房,也是采用的CN2优化线路,目前也有入手且在使用中,我个人感觉如果中文业务需要用到的话虽然日本机房也是CN2,但是线路的稳定性不如香港机房,所以我们在这篇文章中亲测看看香港机房,然后对比之前看到的日本机房。香港机房的配置信息。CPU内存 硬盘带宽IP价格购买地址2核2G50G2M1¥50/月选择方案4核4G60G3M1¥100/月选择方案4核8G70G3M4¥200/月选择...
www.k8k8.com为你推荐
-
存储备份小型机 存储备份网罗设计谁知道怎么做网络设计啊?就是设计名片啊?设计什么的?我想自己亲自做,急!!!sonicchatwe chat和微信区别嘉兴商标注册怎么查商标注册日期www.hao360.cn每次打开电脑桌面都出现以下图标,打开后链接指向www.hao.360.cn。怎么彻底删除?51sese.com谁有免费看电影的网站?ip在线查询通过对方的IP地址怎么样找到他的详细地址?www.gegeshe.com有什么好听的流行歌曲lcoc.toptop weenie 是什么?www.ijinshan.com在电脑看港台电视台那个网站最好而又不用钱速度又快