providingpermissiondenied
permissiondenied 时间:2021-03-17 阅读:()
CopyrightIBMCorporation2009TrademarksSecureLinuxcontainerscookbookPage1of12SecureLinuxcontainerscookbookStrengthenlightweightcontainerswithSELinuxandSmackSergeE.
HallynFebruary03,2009Lightweightcontainers,otherwiseknownasVirtualPrivateServers(VPS)orJails,areoftenthoughtofasasecuritytoolsdesignedtoconfineuntrustedapplicationsorusers;butaspresentlyconstructed,thesecontainersdonotprovideadequatesecurityguarantees.
BystrengtheningthesecontainersusingSELinuxorSmackpolicy,amuchmoresecurecontainercanbeimplementedinLinux.
ThisarticleshowsyouhowtocreateamoresecureLinux-Security-Modules-protectedcontainer.
BoththeSELinuxandSmackpolicyareconsideredworksinprogress,tobeimproveduponwithhelpfromtheirrespectivecommunities.
Acommonresponsewhensomeonefirsthearsaboutcontainersis"HowdoIcreateasecurecontainer"ThisarticleanswersthatquestionbyshowingyouhowtouseLinuxSecurityModules(LSM)toimprovethesecurityofcontainers.
Inparticular,itshowsyouhowtospecifyasecuritygoalandmeetitwithboththeSmackandSELinuxsecuritymodules.
ForbackgroundreadingonLinuxContainers,see"LXC:Linuxcontainertools"(developerWorks,February2009).
LinuxcontainersarereallyaconceptualartificebuiltatopseveralLinuxtechnologies:Resourcenamespacesallowthemanipulationoflookupsofprocesses,files,SYSVIPCresources,networkinterfaces,andmore,allinsideofcontainers.
Controlgroupsallowresourcelimitstobeplacedoncontainers.
Capabilityboundingsetslimittheprivilegeavailabletocontainers.
Thesetechnologiesmustbecoordinatedinordertoprovidetheillusionofcontainers.
Twoprojectsalreadyprovidethisfunctionality:LibvirtisalargeprojectthatcancreatevirtualmachinesusingtheXenhypervisor,qemuemulator,andkvm,andalsousinglightweightcontainers.
Liblxcisasmallersetoflibrariesanduserspacecommandswritteninparttohelpkerneldevelopersquicklyandeasilytestthecontainersfunctionality.
developerWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage2of12Because"LXC:Linuxcontainertools"waswrittenusingliblxcasitsfoundation,Iwillcontinuewithliblxchere;however,anythingwedoherecanjustaseasilybedoneusinglibvirt'scontainersupport.
Majorplayer1:LSMBeforewestart,ifyouknowlittleabouttheLSM,hereisaquickreview.
AccordingtotheWikipediaentry:LinuxSecurityModules(LSM)isaframeworkthatallowstheLinuxkerneltosupportavarietyofcomputersecuritymodelswhileavoidingfavoritismtowardanysinglesecurityimplementation.
TheframeworkislicensedunderthetermsoftheGNUGeneralPublicLicenseandisstandardpartoftheLinuxkernelsinceLinux2.
6.
.
.
.
LSMwasdesignedtoprovidethespecificneedsofeverythingneededtosuccessfullyimplementamandatoryaccesscontrolmodule,whileimposingthefewestpossiblechangestotheLinuxkernel.
LSMavoidstheapproachofsystemcallinterpositionasusedinSystracebecauseitdoesnotscaletomultiprocessorkernelsandissubjecttoTOCTTOU(race)attacks.
Instead,LSMinserts"hooks"(upcallstothemodule)ateverypointinthekernelwhereauser-levelsystemcallisabouttoresultinaccesstoanimportantinternalkernelobjectsuchasinodesandtaskcontrolblocks.
.
.
.
Theprojectisnarrowlyscopedtosolvetheproblemofaccesscontroltoavoidimposingalargeandcomplexchangepatchonthemainstreamkernel.
Itisnotintendedasageneral"hook"or"upcall"mechanism,nordoesitsupportvirtualization.
.
.
.
LSM'saccesscontrolgoalisverycloselyrelatedtotheproblemofsystemauditing,butissubtlydifferent.
Auditingrequiresthateveryattemptataccessberecorded.
LSMcannotdeliverthat,becauseitwouldrequireagreatmanymorehooks,soastodetectcaseswherethekernel"shortcircuits"failingsystemcallsandreturnsanerrorcodebeforegettingnearsignificantobjects.
Systemsecurityconsistsoftwosomewhatcontradictorygoals.
Thefirstistoachievecompleteandfine-grainedaccesscontrol.
Ateverypointthatinformationcanbeleakedorcorrupted,youmustbeabletoexertcontrol.
Controlsthataretoocoarseisthesameasbeinguncontrolled.
Forinstance,if(attheextreme)allfilesmustbeclassifiedasonetypeandanyonefilemustbeworld-readable,thenallfilesmustbeworld-readable.
Ontheotherhand,configurationmustalsobesimple,otherwiseadministratorswilloftendefaulttogivingtoomuchaccess(andIcan'temphasizethisenough--thisisthesameasbeinguncontrolled).
Forinstance,ifmakingaprogramworkrequiresthousandsofaccessrules,thenchancesareanadminwillgivetheprogramtoomanyaccessrightsratherthantestingwhethereachaccessrulewasreallyneeded.
ThetwoprimarysecuritymodulesinLinuxeachtakeadifferentviewonhowtohandlethisbalance.
SELinuxbeginsbycontrollingeverythingwhileusinganimpressivepolicylanguagetosimplifypolicymanagement.
Smackisprimarilyconcernedwithprovidingasimpleaccesscontrol.
ibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage3of12Majorplayer2:SELinuxSELinuxisbyfarthemostwell-knownMACsystemforLinux(mandatoryaccesscontrol).
Whileitcertainlystillhasitsdetractors,thefactthatthepopularFedoradistributionhasbeendeployedwithSELinuxenforcingforyearsisatremendoustestamenttoitssuccess.
SELinuxisconfiguredusingamodularpolicylanguagewhichallowsaninstalledpolicytobeeasilyupdatedbyusers.
Thelanguagealsoprovidesinterfaces,allowingmorehigh-levelstatementstobeusedtorepresentacollectionoflow-level"allow"statements.
Inthisarticle,wewillbeusinganewinterfacetodefinecontainers.
Whiletheinterfaceitselfwillbequitelargeduetothemanyaccessrightsyoumustgivethecontainer,usingtheinterfacetocreateanewcontainerwillbeverysimple.
Hopefullytheinterfacecanbecomeapartofthecoredistributedpolicy.
Majorplayer3:SmackSmackistheSimplifiedMandatoryAccessControlKernel.
Itbeginsbylabelingallprocesses,files,andnetworktrafficwithsimpletextlabels.
Newlycreatedfilesarecreatedwiththelabelofthecreatingprocess.
Afewdefaulttypesalwaysexistwithclearlydefinedaccessrules.
Aprocesscanalwaysreadandwriteobjectsofthesamelabel.
PrivilegetobypasstheSmackaccessrulesarecontrolledusingPOSIXcapabilities,soataskcarryingCAP_MAC_OVERRIDEcanoverridetherules;ataskcarryingCAP_MAC_ADMINcanchangetherulesandlabels.
"POSIXfilecapabilities:Parcelingthepowerofroot"(Relatedtopics)demonstratestheseprivileges.
OursecuritygoalInsteadofsimplyblindlyapplyingpolicyandhopingtoendupwithsomethinguseful,let'sbeginbydefiningaclearsecuritygoal.
ThesimplicityofSmackactuallylimitsthegoalswecanachieve,butwe'llpursuethefollowinggoal:1.
CreatecontainerswithsegregatedfilesystemsprovidingWebandsshservices.
2.
Containerswillbeprotectedfromeachother.
Acontainerdesignatedvs1cannotreadfilesownedbyanothercontainervs2orkillitstasks.
3.
Thehostcanprotectitskeyfilesfromcontainers.
4.
TheoutsideworldcanreachtheWebserversandsshserversonthecontainers.
ThegeneralsetupInthisarticlewe'lldotwoexperiments--firstwe'llsetupcontainersprotectedbySELinux,thencontainersprotectedbySmack.
Theexperimentswillsharemuchofthepreliminarysetup.
Youcanusearealmachinetodotheseexperiments,butyoumayfinditeasierormorecomfortingtouseavirtualmachine.
Touseqemuorkvm,youcancreateaharddiskusingqemu-imgcreatevm.
img10G.
BootthevirtualmachinefromCDROMusingacommandlikekvm-hdavm.
img-cdromcdrom.
iso-bootd-m512M.
AgoodchoiceforaCDROMimageistogotofedoraproject.
org/get-fedoraanddownloadaninstallationDVDforFedora10fori386.
SubstitutethefilenameyoudownloadfordeveloperWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage4of12cdrom.
isointhepreviouscommand.
Youcanmostlyusetheinstallationdefaults,butmakesuretounselectofficeandproductivityandselectsoftwaredevelopment.
You'llalsowanttoinstallthebridge-utils,debootstrap,andncurses-develrpms,probablyusingtheyumpackagemanager.
Nowyouneedtocompileacustomkernel.
Downloadthekernel-sourcesrpm,patchitwithenable-netns.
patch(seetheDownloadsection)toprovidenetworknamespaces(whichwillbeupstreamasof2.
6.
29butnotinFedora10),changetheconfiguration,thencompletethecompilationandinstallation,byfollowingthefollowinginstructionsasroot:yumdownloader--sourcekernelrpm-ikernel*cdrpmbuildrpmbuild-bcSPECS/kernel-*cdBUILD/kernel-2.
6.
27/linux-2.
6*patch-p1Networkingoptionsmenus).
FortheSmackexperiment,alsogointotheSecurityoptionsmenu,deselectSELinux,andselectthenextoption,Smack.
Youmayalsoneedtoswitchthedefaultbootentryin/boot/grub/grub.
confbackto0insteadof1.
Nowwewanttotryoutliblxc.
"LXC:Linuxcontainertools"describesthebasicusageofliblxcindetail,sowe'llglossoverithere.
Simplyusethecontainer_setup.
shscript(seetheDownloadsection)tosetupthebridgeonwhichcontainernetworkdeviceswilltalk.
Itwillalsoclearyourfirewall,whichbydefaultisn'tsetuptohandlethebridge,aswellassetuptheSmackpolicy(whichwe'llcreatelaterinthefile/etc/smackaccesses)ifyouaredoingtheSmackexperiment.
You'llneedtoruncontainer_setup.
shaftereachrebootorifyouknowhow,makeitrunatbootautomatically.
Nowyourmachineisready!
Let'stryoutliblxc.
Youcandownloadthelatestsourceusingcvsfromlxc.
sf.
netandcompileitusingthefollowing:cvs-d:pserver:anonymous@lxc.
cvs.
sourceforge.
net:/cvsroot/lxclogincvs-z3-d:pserver:anonymous@lxc.
cvs.
sourceforge.
net:/cvsroot/lxcco-Plxccdlxc.
/bootstrap&&.
/configure&&make&&makeinstallNowifyoulookattheREADME,you'llseetherearequiteafewoptionsforgettingstarted.
Containerscanbeextremelylightweightbecausetheycansharemanyresourceswithyoursystem--includingthefilesystem.
Butourgoalistoprovidesomesimpleisolationsowewillusethescriptlxc-debiantocreateafulldebianchrootimageforeachcontainer.
Beginbycreatingacontainernamedvsplain:ibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage5of12mkdir/vsplaincd/vsplainlxc-debiancreatecontainername:vsplainhostname:vsplainIP10.
0.
2.
20gateway:10.
0.
2.
2Theconfigurationforthiscontainerisstoredunderthedirectory/usr/local/var/lxc/vsplain.
Ifyoulookatthefilecalledcgroup,you'llseesomelinesbeginningwithdevices.
.
Thesearedirectivestothedeviceswhitelistcgroupwhichwillmediatedevicecreation,read,andwritebythecontainer.
Startthiscontainerusingthecommandlxc-start-nvsplain.
You'llbepresentedwithaloginprompt.
Logintothecontainerusingusernamerootwithnopassword.
Finally,whenyourcontainerisupandrunning,youwillwanttoapt-getinstallopenssh-serverapt-getinstallapacheNowyoucansshfromthekvmhosttothecontainerandlookatitsWebpageusing10.
0.
2.
20forvsplain'sipaddressand10.
0.
2.
15forthehost's.
Youcanshutthecontainerdownatanytimefromarootterminalonthekvmhostusingthecommandlxc-stop-nvsplain.
Atthispoint,youmaywanttosaveyourselfsometimebycloningtwonewvirtualmachinesfromthistemplate.
Shutdownyourvmanddo:cpvm.
imgselinux.
imgcpvm.
imgsmack.
imgSELinux-protectedcontainersTheSELinuxpolicyforcontainerswe'llusewillconsistofapolicymodule;themodulehasbeenpostedtorefpolicy--SELinuxReferencePolicydevelopmentmaillist.
Downloadthepolicyintoadirectory/root/vs,intofilescalledvs.
if,vs.
fc,andvs.
terespectively.
Compileandinstallthenewmoduleasfollows:cp-r/usr/share/selinux/devel/usr/share/selinux/vscp/root/vs.
/usr/share/selinux/vs/cd/usr/share/selinux/vsmake&&semodule-ivs.
ppThencreatecontainers/vs1and/vs2usinglxc-debianandrelabeltheirfilesystemsusingdeveloperWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage6of12mkdir/vs1;cd/vs1lxc-debiancreatecontainername:vs1hostname:vs1address:10.
0.
2.
21gateway:10.
0.
2.
2arch:2(i386)mkdir/vs2;cd/vs2lxc-debiancreatecontainername:vs2hostname:vs2address:10.
0.
2.
22gateway:10.
0.
2.
2arch:2(i386)fixfilesrelabel/vs1fixfilesrelabel/vs2Whenyoustartyourcontainers(forinstancebyusinglxc-start-nvs1),you'lllikelygetafewauditmessagesaboutSELinuxaccessdenials.
Don'tworry--thecontainerstartsupfinewithnetworkservicesenabledandthecontainersarenowisolated.
Ifyouhelpcontainervs1cheatusingmount--bind//vs1/rootfs.
vs1/mntbeforestartingthecontainer,you'llfindthateventhoughyouaretherootuser,ls/mnt/rootwillberefused.
Toseehowthisworks,let'slookatthevs.
ifinterfacefile.
Thisdefinesaninterfacecalledcontainerwhichtakesoneargument,thebasenameforthecontainertodefine.
Thevs.
tefilecallsthisfunctiontwicewiththecontainernamesvs1,vs2.
Intheinterface,$1isexpandedtotheargument,so$1_tbecomesvs1_twhenwecallcontainer(vs1).
(Fromhereonlet'sassumewearedefiningvs1).
Themostimportantlinesarethoseinvolvingvs1_exec_t.
Thecontainerrunsintypevs1_t.
Itentersthistypewhenunconfined_texecutesthecontainer's/sbin/initwhichisoftypevs1_exec_t.
Mostoftherestofthepolicymerelyistheretograntthecontainersufficientprivilegetoaccessbitsofthesystem:networkports,devices,consoles,etc.
Theinterfaceisaslongasitisduetothefine-grainednatureoftheexistingSELinuxreferencepolicy.
Aswe'reabouttosee,theSmack-protectedcontainerwillhaveamuchsimplerpolicy;inreturn,itwillpromisemuchlessflexibleprotectionfrommisbehavingsystemservices.
Thereisonemorethingyouneedtodo.
Youmayhavenotedthatwhilethecontainerisnotabletooverwriteits$1_exec_t,thatis/sbin/init.
Butwhatitcandoissomethinglikemv/sbin/sbin.
bakmkdir/sbintouch/sbin/initTheresulting/sbin/initwillbeoftypevs1_file_t.
WhydoyouthinkthecontaineradminwouldwanttodothisBecauseitwouldlaunchthecontainer,includingthesshdaemon,intheunconfined_tdomain,givinghimaprivilegedshellandallowinghimtoescapetheSELinuxconstraintsweweretryingtoenforce.
Topreventthis,youactuallywanttostartthecontainerthroughacustomscriptandrelabelsbin/inittovs1_exec_tbeforestartingthecontainer.
Infact,youcancopyapristinecopyofinitbackintoibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage7of12thecontainerandrelabelthatifthecontaineradministratordidn'tmind.
Butwe'lljustrelabeltheexistinginit:cat>>/vs1/vs1.
sh>/vs1/vs1.
sh/proc/self/attr/currentlxc-start-nvs1/bin/dropmacadmin/sbin/initEOFchmodu+x/vs1/vs1.
shOnemorethingwillletvs1writetothetmpfsfilesystemitisgoingtomount:sed-i's/defaults/defaults,smackfsroot=vs1,smackfsdef=vs1/'\/vs1/rootfs.
vs1/etc/fstabThiswillcausethetmpfsfilesystemmountedat/dev/shmtocarrythevs1labelsothatvs1canwritetoit.
Otherwise,vs1initscriptswon'tbeabletocreatethe/dev/shm/networkdirectoryituseswhilesettingupthenetwork.
Similarly,ifyouwanttousearam-based/tmp,you'llwantthosesameoptions.
Nowagainlet'shelpvs1cheat.
Createvs2thesamewayyoucreatedvs1,substitutingvs2forvs1ateachstep.
Thenbind-mounttherootfilesystemundervs1's/mnt:mount--bind/vs1/vs1mount--make-runbindable/vs1mount--rbind//vs1/rootfs.
vs1/mntibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage9of12Startthecontainerusingvs1.
sh.
NotethatyoucanstillseetheWebpageonvs1andvs2fromthekvmhost.
Notealsothatvs1cannotaccessvs2overthenetwork.
Italsocan'tlookthroughvs2'sfiles:vs1:~#ls/mnt/(directorylisting)vs1:~#ls/mnt/vs2/rootfs.
vs2ls:/mnt/vs2/rootfs.
vs2:Permissiondeniedvs1:~#mkdir/cgroupvs1:~#mount-tcgroupcgroup/cgroupvs1:~#ls/cgroupls:/mnt/vs3:Permissiondeniedvs1:~#mknod/dev/sda1b81mknod:`/dev/sda1':Operationnotpermittedvs1:~#mount/mnt/dev/sda1/tmpmount:permissiondeniedItcanlookthroughthehostfilesystem.
Anythingwewanttoprotectagainst,wecanlabelwiththehostlabel.
That'swhatwedidwiththecgroupfilesystemwhichiswhyls/cgroupfailed.
Finally,thedeviceswhitelistcgroupispreventingusfromcreatingadiskdevice,aswellasmountingitifitexists(asitdoesthrough/mnt).
Ofcourse,thewaywe'vesetthisup,thecontaineradmincanremove/mnt/dev/sda1,aswellmessupthehostinanynumberofways,sootherthanasdemonstrationthisbindmountisobviouslynotdesirable!
NotethatwhileontheSELinuxsystem,thedefault(andeasy)routewastoallowthecontainerstotalktoeachotheroverthenetwork,theinverseistrueinSmack.
Allowingcontainerstotalktoeachotheriscurrentlyveryhardtodo.
AnabilitytosetlabelsonIPaddressesiscomingsoonthoughandshouldallowustosetuppolicytoallowcontainerstocommunicate.
RelatedtohowwesetupSmacknetworking,wehaveanotherproblem.
Thecommandkill-9-1killseverytaskonthesystem.
Whendonebyataskinacontainer,thisshouldonlykilltasksinthesamecontainer.
Thatbehaviorisnowfixedintheupstreamkernel,butnotintheFedora10kernelweareusing.
Soeverytaskwillbesenta-9signal.
IntheSELinux-protectedcontainers,SELinuxstopsthesignalsfrompassingthecontainerboundary,sokill-9-1isactuallysafe.
ButinSmacktasksbydefaultarelabeled_justasthenetworkis,sosinceweallowedthecontainertowrite_toallowwritingtothenetwork,andsincekillingataskisconsideredawriteaccessbySmack,youarealsoallowingthecontaineradmintokillanytasksonthewholesystem.
Anothershortcoming(whichisalsopresentintheSELinuxcontainers)hastodowithUnix98pseudo-terminals.
Opentwographicalterminals.
Inthefirst,startupvs1andlookunder/dev/pts.
Youwillseeatleasttwoentries,0and1,onebelongingtoeachterminal.
Fromthevs1containeryouareabletowriteintotheentrycorrespondingtotheotherterminal.
WiththeFedorakerneltherearetwosolutions.
Youcanusethedevicewhitelistcgrouptodenythecontainertheabilitytoopenthedevices.
However,thiswillhavetobedonebyhandeachtimethedeveloperWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage10of12containerisstartedinordertograntitaccesstoitsterminal;oryoucanachievethesameeffectbyapplyingSELinuxandSmacklabels.
Thenewer2.
6.
29kernelsupportsdevptsnamespaces.
Acontainerwillremount/dev/pts,afterwhichitwillbeunabletoaccessthedevptsentriesbelongingtothehostorothercontainers.
ConclusionThisarticleshowcasedthebasictoolsforcreatingLSM-protectedcontainers,butmuchworkremainstobedone:ForSmack,youmustchoosefilestolabelashost.
ForSELinux,youshouldfine-tuneandthenpushacontainerinterfaceintotheupstreamreferencepolicy.
Whilesuchworkisongoing,anduntilmoreexperienceisgainedwithLSM-protectedcontainers,youshouldnotputallyourtrustinthesemechanismstoprotectagainstanuntrustedrootuser.
Althoughtherearenoestablishedbestpracticesforcreatingcontainersyet(thatIknowof),thereareafewideasworthstartingwith.
First,rememberyouareconsolidatingtwosomewhatcontradictorygoals:Youwanttominimizeduplicationamongcontainers(andthehost)whileneedingtoensureisolation.
Onewaytoachievethesegoalscouldbetocreateasinglefullminimalrootfsinwhichnocontainerrunsandlabelingitatypewhichallcontainerscanread.
Thenuseacustomversionofthelxc-sshdscripttocreateeachactualcontainerbasedontheprototype,creatingread-onlymountsformostofthecontainer'sfilesystemwhileprovidingaprivatewritableplaceforthecontainertostorefiles,saylike/scratch.
Sinceeachcontainerhasaprivatemountsnamespace,itcanbind-mountanyfilesordirectorieswhichitneedstobeprivateand/orwriteablefromitsprivateshareddirectory.
Forinstance,ifitwantsaprivate/lib,itcanmount--bind/scratch/rootfs/lib/lib.
Likewise,theadmincanensurethateverycontainerdoesmount--bind/scratch/shadow/etc/shadowatstartup.
OneclearlimitationoftheapproachIdemonstratedherewithbothSELinuxandSmackisthatthecontaineradministratorcannotexploitLSMtocontrolinformationflowwithinhisowncontainer.
Rather,forsimplicity,alltasksinthecontaineraretreatedthesamebyMACpolicy.
Inanotherarticle,IhopetoexplorehowtoallowcontaineradministratorstospecifytheirownLSMpolicieswithoutallowingthemtoescapetheirowncontraints.
ThismaterialisbaseduponworksupportedbytheDefenseAdvancedResearchProjectsAgencyunderitsAgreementNo.
HR0011-07-9-0002.
AcknowledgmentsCaseySchaufler,theauthorofSmack,helpedingettingtheSmack-protectedcontainerofftheground,andDanWalshwaskindenoughtoprovidefeedbackontheSELinuxpolicy.
ibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage11of12DownloadableresourcesDescriptionNameSizeCodeforthisarticlecode.
zip3KBdeveloperWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage12of12Relatedtopics"LXC:Linuxcontainertools"(developerWorks,February2009)isastep-by-stepguidetocreatingLinuxcontainers.
Therefpolicy--SELinuxReferencePolicydevelopmentmaillistiswhereyou'llfindthepolicymoduleweusedinthisarticle.
"SELinuxfromscratch"(developerWorks,May2006)isadetailedintroductiontoSELinux.
PlanetSELinuxisanaggregationofblogpostsfrommembersoftheSELinuxdevelopmentcommunity.
"Smackforsimplifiedaccesscontrol"(LWN.
net,August2007)isanearlywriteupontheSmacksubmission.
LinuxResourceContainersprojectonSourceForge.
netisarepositoryofcodeforapplicationcontainerimplementationintheLinuxkernel,astagingareaforcodethatmaybesenttothelinux-kernelmailinglist.
OthercontainertechnologiesincludeSolarisZones(Solaris)BSDjails(FreeBSD)Linux-Vserver(Linux)OpenVZ(Linux)InthedeveloperWorksLinuxzone,findmoreresourcesforLinuxdevelopers(includingdeveloperswhoarenewtoLinux),andscanourmostpopulararticlesandtutorials.
SeeallLinuxtipsandLinuxtutorialsondeveloperWorks.
SELinuxcontainerspolicyCopyrightIBMCorporation2009(www.
ibm.
com/legal/copytrade.
shtml)Trademarks(www.
ibm.
com/developerworks/ibm/trademarks/)
HallynFebruary03,2009Lightweightcontainers,otherwiseknownasVirtualPrivateServers(VPS)orJails,areoftenthoughtofasasecuritytoolsdesignedtoconfineuntrustedapplicationsorusers;butaspresentlyconstructed,thesecontainersdonotprovideadequatesecurityguarantees.
BystrengtheningthesecontainersusingSELinuxorSmackpolicy,amuchmoresecurecontainercanbeimplementedinLinux.
ThisarticleshowsyouhowtocreateamoresecureLinux-Security-Modules-protectedcontainer.
BoththeSELinuxandSmackpolicyareconsideredworksinprogress,tobeimproveduponwithhelpfromtheirrespectivecommunities.
Acommonresponsewhensomeonefirsthearsaboutcontainersis"HowdoIcreateasecurecontainer"ThisarticleanswersthatquestionbyshowingyouhowtouseLinuxSecurityModules(LSM)toimprovethesecurityofcontainers.
Inparticular,itshowsyouhowtospecifyasecuritygoalandmeetitwithboththeSmackandSELinuxsecuritymodules.
ForbackgroundreadingonLinuxContainers,see"LXC:Linuxcontainertools"(developerWorks,February2009).
LinuxcontainersarereallyaconceptualartificebuiltatopseveralLinuxtechnologies:Resourcenamespacesallowthemanipulationoflookupsofprocesses,files,SYSVIPCresources,networkinterfaces,andmore,allinsideofcontainers.
Controlgroupsallowresourcelimitstobeplacedoncontainers.
Capabilityboundingsetslimittheprivilegeavailabletocontainers.
Thesetechnologiesmustbecoordinatedinordertoprovidetheillusionofcontainers.
Twoprojectsalreadyprovidethisfunctionality:LibvirtisalargeprojectthatcancreatevirtualmachinesusingtheXenhypervisor,qemuemulator,andkvm,andalsousinglightweightcontainers.
Liblxcisasmallersetoflibrariesanduserspacecommandswritteninparttohelpkerneldevelopersquicklyandeasilytestthecontainersfunctionality.
developerWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage2of12Because"LXC:Linuxcontainertools"waswrittenusingliblxcasitsfoundation,Iwillcontinuewithliblxchere;however,anythingwedoherecanjustaseasilybedoneusinglibvirt'scontainersupport.
Majorplayer1:LSMBeforewestart,ifyouknowlittleabouttheLSM,hereisaquickreview.
AccordingtotheWikipediaentry:LinuxSecurityModules(LSM)isaframeworkthatallowstheLinuxkerneltosupportavarietyofcomputersecuritymodelswhileavoidingfavoritismtowardanysinglesecurityimplementation.
TheframeworkislicensedunderthetermsoftheGNUGeneralPublicLicenseandisstandardpartoftheLinuxkernelsinceLinux2.
6.
.
.
.
LSMwasdesignedtoprovidethespecificneedsofeverythingneededtosuccessfullyimplementamandatoryaccesscontrolmodule,whileimposingthefewestpossiblechangestotheLinuxkernel.
LSMavoidstheapproachofsystemcallinterpositionasusedinSystracebecauseitdoesnotscaletomultiprocessorkernelsandissubjecttoTOCTTOU(race)attacks.
Instead,LSMinserts"hooks"(upcallstothemodule)ateverypointinthekernelwhereauser-levelsystemcallisabouttoresultinaccesstoanimportantinternalkernelobjectsuchasinodesandtaskcontrolblocks.
.
.
.
Theprojectisnarrowlyscopedtosolvetheproblemofaccesscontroltoavoidimposingalargeandcomplexchangepatchonthemainstreamkernel.
Itisnotintendedasageneral"hook"or"upcall"mechanism,nordoesitsupportvirtualization.
.
.
.
LSM'saccesscontrolgoalisverycloselyrelatedtotheproblemofsystemauditing,butissubtlydifferent.
Auditingrequiresthateveryattemptataccessberecorded.
LSMcannotdeliverthat,becauseitwouldrequireagreatmanymorehooks,soastodetectcaseswherethekernel"shortcircuits"failingsystemcallsandreturnsanerrorcodebeforegettingnearsignificantobjects.
Systemsecurityconsistsoftwosomewhatcontradictorygoals.
Thefirstistoachievecompleteandfine-grainedaccesscontrol.
Ateverypointthatinformationcanbeleakedorcorrupted,youmustbeabletoexertcontrol.
Controlsthataretoocoarseisthesameasbeinguncontrolled.
Forinstance,if(attheextreme)allfilesmustbeclassifiedasonetypeandanyonefilemustbeworld-readable,thenallfilesmustbeworld-readable.
Ontheotherhand,configurationmustalsobesimple,otherwiseadministratorswilloftendefaulttogivingtoomuchaccess(andIcan'temphasizethisenough--thisisthesameasbeinguncontrolled).
Forinstance,ifmakingaprogramworkrequiresthousandsofaccessrules,thenchancesareanadminwillgivetheprogramtoomanyaccessrightsratherthantestingwhethereachaccessrulewasreallyneeded.
ThetwoprimarysecuritymodulesinLinuxeachtakeadifferentviewonhowtohandlethisbalance.
SELinuxbeginsbycontrollingeverythingwhileusinganimpressivepolicylanguagetosimplifypolicymanagement.
Smackisprimarilyconcernedwithprovidingasimpleaccesscontrol.
ibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage3of12Majorplayer2:SELinuxSELinuxisbyfarthemostwell-knownMACsystemforLinux(mandatoryaccesscontrol).
Whileitcertainlystillhasitsdetractors,thefactthatthepopularFedoradistributionhasbeendeployedwithSELinuxenforcingforyearsisatremendoustestamenttoitssuccess.
SELinuxisconfiguredusingamodularpolicylanguagewhichallowsaninstalledpolicytobeeasilyupdatedbyusers.
Thelanguagealsoprovidesinterfaces,allowingmorehigh-levelstatementstobeusedtorepresentacollectionoflow-level"allow"statements.
Inthisarticle,wewillbeusinganewinterfacetodefinecontainers.
Whiletheinterfaceitselfwillbequitelargeduetothemanyaccessrightsyoumustgivethecontainer,usingtheinterfacetocreateanewcontainerwillbeverysimple.
Hopefullytheinterfacecanbecomeapartofthecoredistributedpolicy.
Majorplayer3:SmackSmackistheSimplifiedMandatoryAccessControlKernel.
Itbeginsbylabelingallprocesses,files,andnetworktrafficwithsimpletextlabels.
Newlycreatedfilesarecreatedwiththelabelofthecreatingprocess.
Afewdefaulttypesalwaysexistwithclearlydefinedaccessrules.
Aprocesscanalwaysreadandwriteobjectsofthesamelabel.
PrivilegetobypasstheSmackaccessrulesarecontrolledusingPOSIXcapabilities,soataskcarryingCAP_MAC_OVERRIDEcanoverridetherules;ataskcarryingCAP_MAC_ADMINcanchangetherulesandlabels.
"POSIXfilecapabilities:Parcelingthepowerofroot"(Relatedtopics)demonstratestheseprivileges.
OursecuritygoalInsteadofsimplyblindlyapplyingpolicyandhopingtoendupwithsomethinguseful,let'sbeginbydefiningaclearsecuritygoal.
ThesimplicityofSmackactuallylimitsthegoalswecanachieve,butwe'llpursuethefollowinggoal:1.
CreatecontainerswithsegregatedfilesystemsprovidingWebandsshservices.
2.
Containerswillbeprotectedfromeachother.
Acontainerdesignatedvs1cannotreadfilesownedbyanothercontainervs2orkillitstasks.
3.
Thehostcanprotectitskeyfilesfromcontainers.
4.
TheoutsideworldcanreachtheWebserversandsshserversonthecontainers.
ThegeneralsetupInthisarticlewe'lldotwoexperiments--firstwe'llsetupcontainersprotectedbySELinux,thencontainersprotectedbySmack.
Theexperimentswillsharemuchofthepreliminarysetup.
Youcanusearealmachinetodotheseexperiments,butyoumayfinditeasierormorecomfortingtouseavirtualmachine.
Touseqemuorkvm,youcancreateaharddiskusingqemu-imgcreatevm.
img10G.
BootthevirtualmachinefromCDROMusingacommandlikekvm-hdavm.
img-cdromcdrom.
iso-bootd-m512M.
AgoodchoiceforaCDROMimageistogotofedoraproject.
org/get-fedoraanddownloadaninstallationDVDforFedora10fori386.
SubstitutethefilenameyoudownloadfordeveloperWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage4of12cdrom.
isointhepreviouscommand.
Youcanmostlyusetheinstallationdefaults,butmakesuretounselectofficeandproductivityandselectsoftwaredevelopment.
You'llalsowanttoinstallthebridge-utils,debootstrap,andncurses-develrpms,probablyusingtheyumpackagemanager.
Nowyouneedtocompileacustomkernel.
Downloadthekernel-sourcesrpm,patchitwithenable-netns.
patch(seetheDownloadsection)toprovidenetworknamespaces(whichwillbeupstreamasof2.
6.
29butnotinFedora10),changetheconfiguration,thencompletethecompilationandinstallation,byfollowingthefollowinginstructionsasroot:yumdownloader--sourcekernelrpm-ikernel*cdrpmbuildrpmbuild-bcSPECS/kernel-*cdBUILD/kernel-2.
6.
27/linux-2.
6*patch-p1Networkingoptionsmenus).
FortheSmackexperiment,alsogointotheSecurityoptionsmenu,deselectSELinux,andselectthenextoption,Smack.
Youmayalsoneedtoswitchthedefaultbootentryin/boot/grub/grub.
confbackto0insteadof1.
Nowwewanttotryoutliblxc.
"LXC:Linuxcontainertools"describesthebasicusageofliblxcindetail,sowe'llglossoverithere.
Simplyusethecontainer_setup.
shscript(seetheDownloadsection)tosetupthebridgeonwhichcontainernetworkdeviceswilltalk.
Itwillalsoclearyourfirewall,whichbydefaultisn'tsetuptohandlethebridge,aswellassetuptheSmackpolicy(whichwe'llcreatelaterinthefile/etc/smackaccesses)ifyouaredoingtheSmackexperiment.
You'llneedtoruncontainer_setup.
shaftereachrebootorifyouknowhow,makeitrunatbootautomatically.
Nowyourmachineisready!
Let'stryoutliblxc.
Youcandownloadthelatestsourceusingcvsfromlxc.
sf.
netandcompileitusingthefollowing:cvs-d:pserver:anonymous@lxc.
cvs.
sourceforge.
net:/cvsroot/lxclogincvs-z3-d:pserver:anonymous@lxc.
cvs.
sourceforge.
net:/cvsroot/lxcco-Plxccdlxc.
/bootstrap&&.
/configure&&make&&makeinstallNowifyoulookattheREADME,you'llseetherearequiteafewoptionsforgettingstarted.
Containerscanbeextremelylightweightbecausetheycansharemanyresourceswithyoursystem--includingthefilesystem.
Butourgoalistoprovidesomesimpleisolationsowewillusethescriptlxc-debiantocreateafulldebianchrootimageforeachcontainer.
Beginbycreatingacontainernamedvsplain:ibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage5of12mkdir/vsplaincd/vsplainlxc-debiancreatecontainername:vsplainhostname:vsplainIP10.
0.
2.
20gateway:10.
0.
2.
2Theconfigurationforthiscontainerisstoredunderthedirectory/usr/local/var/lxc/vsplain.
Ifyoulookatthefilecalledcgroup,you'llseesomelinesbeginningwithdevices.
.
Thesearedirectivestothedeviceswhitelistcgroupwhichwillmediatedevicecreation,read,andwritebythecontainer.
Startthiscontainerusingthecommandlxc-start-nvsplain.
You'llbepresentedwithaloginprompt.
Logintothecontainerusingusernamerootwithnopassword.
Finally,whenyourcontainerisupandrunning,youwillwanttoapt-getinstallopenssh-serverapt-getinstallapacheNowyoucansshfromthekvmhosttothecontainerandlookatitsWebpageusing10.
0.
2.
20forvsplain'sipaddressand10.
0.
2.
15forthehost's.
Youcanshutthecontainerdownatanytimefromarootterminalonthekvmhostusingthecommandlxc-stop-nvsplain.
Atthispoint,youmaywanttosaveyourselfsometimebycloningtwonewvirtualmachinesfromthistemplate.
Shutdownyourvmanddo:cpvm.
imgselinux.
imgcpvm.
imgsmack.
imgSELinux-protectedcontainersTheSELinuxpolicyforcontainerswe'llusewillconsistofapolicymodule;themodulehasbeenpostedtorefpolicy--SELinuxReferencePolicydevelopmentmaillist.
Downloadthepolicyintoadirectory/root/vs,intofilescalledvs.
if,vs.
fc,andvs.
terespectively.
Compileandinstallthenewmoduleasfollows:cp-r/usr/share/selinux/devel/usr/share/selinux/vscp/root/vs.
/usr/share/selinux/vs/cd/usr/share/selinux/vsmake&&semodule-ivs.
ppThencreatecontainers/vs1and/vs2usinglxc-debianandrelabeltheirfilesystemsusingdeveloperWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage6of12mkdir/vs1;cd/vs1lxc-debiancreatecontainername:vs1hostname:vs1address:10.
0.
2.
21gateway:10.
0.
2.
2arch:2(i386)mkdir/vs2;cd/vs2lxc-debiancreatecontainername:vs2hostname:vs2address:10.
0.
2.
22gateway:10.
0.
2.
2arch:2(i386)fixfilesrelabel/vs1fixfilesrelabel/vs2Whenyoustartyourcontainers(forinstancebyusinglxc-start-nvs1),you'lllikelygetafewauditmessagesaboutSELinuxaccessdenials.
Don'tworry--thecontainerstartsupfinewithnetworkservicesenabledandthecontainersarenowisolated.
Ifyouhelpcontainervs1cheatusingmount--bind//vs1/rootfs.
vs1/mntbeforestartingthecontainer,you'llfindthateventhoughyouaretherootuser,ls/mnt/rootwillberefused.
Toseehowthisworks,let'slookatthevs.
ifinterfacefile.
Thisdefinesaninterfacecalledcontainerwhichtakesoneargument,thebasenameforthecontainertodefine.
Thevs.
tefilecallsthisfunctiontwicewiththecontainernamesvs1,vs2.
Intheinterface,$1isexpandedtotheargument,so$1_tbecomesvs1_twhenwecallcontainer(vs1).
(Fromhereonlet'sassumewearedefiningvs1).
Themostimportantlinesarethoseinvolvingvs1_exec_t.
Thecontainerrunsintypevs1_t.
Itentersthistypewhenunconfined_texecutesthecontainer's/sbin/initwhichisoftypevs1_exec_t.
Mostoftherestofthepolicymerelyistheretograntthecontainersufficientprivilegetoaccessbitsofthesystem:networkports,devices,consoles,etc.
Theinterfaceisaslongasitisduetothefine-grainednatureoftheexistingSELinuxreferencepolicy.
Aswe'reabouttosee,theSmack-protectedcontainerwillhaveamuchsimplerpolicy;inreturn,itwillpromisemuchlessflexibleprotectionfrommisbehavingsystemservices.
Thereisonemorethingyouneedtodo.
Youmayhavenotedthatwhilethecontainerisnotabletooverwriteits$1_exec_t,thatis/sbin/init.
Butwhatitcandoissomethinglikemv/sbin/sbin.
bakmkdir/sbintouch/sbin/initTheresulting/sbin/initwillbeoftypevs1_file_t.
WhydoyouthinkthecontaineradminwouldwanttodothisBecauseitwouldlaunchthecontainer,includingthesshdaemon,intheunconfined_tdomain,givinghimaprivilegedshellandallowinghimtoescapetheSELinuxconstraintsweweretryingtoenforce.
Topreventthis,youactuallywanttostartthecontainerthroughacustomscriptandrelabelsbin/inittovs1_exec_tbeforestartingthecontainer.
Infact,youcancopyapristinecopyofinitbackintoibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage7of12thecontainerandrelabelthatifthecontaineradministratordidn'tmind.
Butwe'lljustrelabeltheexistinginit:cat>>/vs1/vs1.
sh>/vs1/vs1.
sh/proc/self/attr/currentlxc-start-nvs1/bin/dropmacadmin/sbin/initEOFchmodu+x/vs1/vs1.
shOnemorethingwillletvs1writetothetmpfsfilesystemitisgoingtomount:sed-i's/defaults/defaults,smackfsroot=vs1,smackfsdef=vs1/'\/vs1/rootfs.
vs1/etc/fstabThiswillcausethetmpfsfilesystemmountedat/dev/shmtocarrythevs1labelsothatvs1canwritetoit.
Otherwise,vs1initscriptswon'tbeabletocreatethe/dev/shm/networkdirectoryituseswhilesettingupthenetwork.
Similarly,ifyouwanttousearam-based/tmp,you'llwantthosesameoptions.
Nowagainlet'shelpvs1cheat.
Createvs2thesamewayyoucreatedvs1,substitutingvs2forvs1ateachstep.
Thenbind-mounttherootfilesystemundervs1's/mnt:mount--bind/vs1/vs1mount--make-runbindable/vs1mount--rbind//vs1/rootfs.
vs1/mntibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage9of12Startthecontainerusingvs1.
sh.
NotethatyoucanstillseetheWebpageonvs1andvs2fromthekvmhost.
Notealsothatvs1cannotaccessvs2overthenetwork.
Italsocan'tlookthroughvs2'sfiles:vs1:~#ls/mnt/(directorylisting)vs1:~#ls/mnt/vs2/rootfs.
vs2ls:/mnt/vs2/rootfs.
vs2:Permissiondeniedvs1:~#mkdir/cgroupvs1:~#mount-tcgroupcgroup/cgroupvs1:~#ls/cgroupls:/mnt/vs3:Permissiondeniedvs1:~#mknod/dev/sda1b81mknod:`/dev/sda1':Operationnotpermittedvs1:~#mount/mnt/dev/sda1/tmpmount:permissiondeniedItcanlookthroughthehostfilesystem.
Anythingwewanttoprotectagainst,wecanlabelwiththehostlabel.
That'swhatwedidwiththecgroupfilesystemwhichiswhyls/cgroupfailed.
Finally,thedeviceswhitelistcgroupispreventingusfromcreatingadiskdevice,aswellasmountingitifitexists(asitdoesthrough/mnt).
Ofcourse,thewaywe'vesetthisup,thecontaineradmincanremove/mnt/dev/sda1,aswellmessupthehostinanynumberofways,sootherthanasdemonstrationthisbindmountisobviouslynotdesirable!
NotethatwhileontheSELinuxsystem,thedefault(andeasy)routewastoallowthecontainerstotalktoeachotheroverthenetwork,theinverseistrueinSmack.
Allowingcontainerstotalktoeachotheriscurrentlyveryhardtodo.
AnabilitytosetlabelsonIPaddressesiscomingsoonthoughandshouldallowustosetuppolicytoallowcontainerstocommunicate.
RelatedtohowwesetupSmacknetworking,wehaveanotherproblem.
Thecommandkill-9-1killseverytaskonthesystem.
Whendonebyataskinacontainer,thisshouldonlykilltasksinthesamecontainer.
Thatbehaviorisnowfixedintheupstreamkernel,butnotintheFedora10kernelweareusing.
Soeverytaskwillbesenta-9signal.
IntheSELinux-protectedcontainers,SELinuxstopsthesignalsfrompassingthecontainerboundary,sokill-9-1isactuallysafe.
ButinSmacktasksbydefaultarelabeled_justasthenetworkis,sosinceweallowedthecontainertowrite_toallowwritingtothenetwork,andsincekillingataskisconsideredawriteaccessbySmack,youarealsoallowingthecontaineradmintokillanytasksonthewholesystem.
Anothershortcoming(whichisalsopresentintheSELinuxcontainers)hastodowithUnix98pseudo-terminals.
Opentwographicalterminals.
Inthefirst,startupvs1andlookunder/dev/pts.
Youwillseeatleasttwoentries,0and1,onebelongingtoeachterminal.
Fromthevs1containeryouareabletowriteintotheentrycorrespondingtotheotherterminal.
WiththeFedorakerneltherearetwosolutions.
Youcanusethedevicewhitelistcgrouptodenythecontainertheabilitytoopenthedevices.
However,thiswillhavetobedonebyhandeachtimethedeveloperWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage10of12containerisstartedinordertograntitaccesstoitsterminal;oryoucanachievethesameeffectbyapplyingSELinuxandSmacklabels.
Thenewer2.
6.
29kernelsupportsdevptsnamespaces.
Acontainerwillremount/dev/pts,afterwhichitwillbeunabletoaccessthedevptsentriesbelongingtothehostorothercontainers.
ConclusionThisarticleshowcasedthebasictoolsforcreatingLSM-protectedcontainers,butmuchworkremainstobedone:ForSmack,youmustchoosefilestolabelashost.
ForSELinux,youshouldfine-tuneandthenpushacontainerinterfaceintotheupstreamreferencepolicy.
Whilesuchworkisongoing,anduntilmoreexperienceisgainedwithLSM-protectedcontainers,youshouldnotputallyourtrustinthesemechanismstoprotectagainstanuntrustedrootuser.
Althoughtherearenoestablishedbestpracticesforcreatingcontainersyet(thatIknowof),thereareafewideasworthstartingwith.
First,rememberyouareconsolidatingtwosomewhatcontradictorygoals:Youwanttominimizeduplicationamongcontainers(andthehost)whileneedingtoensureisolation.
Onewaytoachievethesegoalscouldbetocreateasinglefullminimalrootfsinwhichnocontainerrunsandlabelingitatypewhichallcontainerscanread.
Thenuseacustomversionofthelxc-sshdscripttocreateeachactualcontainerbasedontheprototype,creatingread-onlymountsformostofthecontainer'sfilesystemwhileprovidingaprivatewritableplaceforthecontainertostorefiles,saylike/scratch.
Sinceeachcontainerhasaprivatemountsnamespace,itcanbind-mountanyfilesordirectorieswhichitneedstobeprivateand/orwriteablefromitsprivateshareddirectory.
Forinstance,ifitwantsaprivate/lib,itcanmount--bind/scratch/rootfs/lib/lib.
Likewise,theadmincanensurethateverycontainerdoesmount--bind/scratch/shadow/etc/shadowatstartup.
OneclearlimitationoftheapproachIdemonstratedherewithbothSELinuxandSmackisthatthecontaineradministratorcannotexploitLSMtocontrolinformationflowwithinhisowncontainer.
Rather,forsimplicity,alltasksinthecontaineraretreatedthesamebyMACpolicy.
Inanotherarticle,IhopetoexplorehowtoallowcontaineradministratorstospecifytheirownLSMpolicieswithoutallowingthemtoescapetheirowncontraints.
ThismaterialisbaseduponworksupportedbytheDefenseAdvancedResearchProjectsAgencyunderitsAgreementNo.
HR0011-07-9-0002.
AcknowledgmentsCaseySchaufler,theauthorofSmack,helpedingettingtheSmack-protectedcontainerofftheground,andDanWalshwaskindenoughtoprovidefeedbackontheSELinuxpolicy.
ibm.
com/developerWorks/developerWorksSecureLinuxcontainerscookbookPage11of12DownloadableresourcesDescriptionNameSizeCodeforthisarticlecode.
zip3KBdeveloperWorksibm.
com/developerWorks/SecureLinuxcontainerscookbookPage12of12Relatedtopics"LXC:Linuxcontainertools"(developerWorks,February2009)isastep-by-stepguidetocreatingLinuxcontainers.
Therefpolicy--SELinuxReferencePolicydevelopmentmaillistiswhereyou'llfindthepolicymoduleweusedinthisarticle.
"SELinuxfromscratch"(developerWorks,May2006)isadetailedintroductiontoSELinux.
PlanetSELinuxisanaggregationofblogpostsfrommembersoftheSELinuxdevelopmentcommunity.
"Smackforsimplifiedaccesscontrol"(LWN.
net,August2007)isanearlywriteupontheSmacksubmission.
LinuxResourceContainersprojectonSourceForge.
netisarepositoryofcodeforapplicationcontainerimplementationintheLinuxkernel,astagingareaforcodethatmaybesenttothelinux-kernelmailinglist.
OthercontainertechnologiesincludeSolarisZones(Solaris)BSDjails(FreeBSD)Linux-Vserver(Linux)OpenVZ(Linux)InthedeveloperWorksLinuxzone,findmoreresourcesforLinuxdevelopers(includingdeveloperswhoarenewtoLinux),andscanourmostpopulararticlesandtutorials.
SeeallLinuxtipsandLinuxtutorialsondeveloperWorks.
SELinuxcontainerspolicyCopyrightIBMCorporation2009(www.
ibm.
com/legal/copytrade.
shtml)Trademarks(www.
ibm.
com/developerworks/ibm/trademarks/)
- providingpermissiondenied相关文档
- 协商permissiondenied
- 4.permissiondenied
- termpermissiondenied
- Settingpermissiondenied
- 用户permissiondenied
- 5.permissiondenied
CYUN专注海外精品服务器资源 国庆钜惠 最低5折起 限量促销
国庆钜惠 最低5折起 限量促销CYUN专注海外精品服务器资源,主营香港CN2 GIA、美国CERA、美国高防服务器资源,实体公司,ISP/IDC资质齐全,客服配备齐全。本次针对国庆推出非常给力的促销活动,旗下所有平台同享,新老客户同享,限时限量,售完截止。活动截止时间:2021年10月9日官网地址:www.cyun.net参与机型:香港CN2 GIA云服务器、香港双程CN2云服...

HostYun:联通AS9929线路,最低月付18元起,最高500Mbps带宽,洛杉矶机房
最近AS9929线路比较火,联通A网,对标电信CN2,HostYun也推出了走联通AS9929线路的VPS主机,基于KVM架构,开设在洛杉矶机房,采用SSD硬盘,分为入门和高带宽型,最高提供500Mbps带宽,可使用9折优惠码,最低每月仅18元起。这是一家成立于2008年的VPS主机品牌,原主机分享组织(hostshare.cn),商家以提供低端廉价VPS产品而广为人知,是小成本投入学习练手首选。...

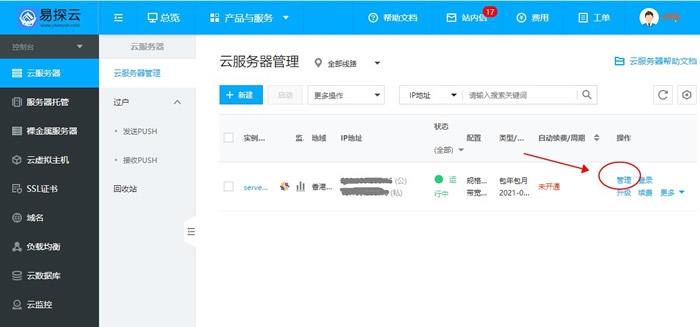
易探云服务器怎么过户/转让?云服务器PUSH实操步骤
易探云服务器怎么过户/转让?易探云支持云服务器PUSH功能,该功能可将云服务器过户给指定用户。可带价PUSH,收到PUSH请求的用户在接收云服务器的同时,系统会扣除接收方的款项,同时扣除相关手续费,然后将款项打到发送方的账户下。易探云“PUSH服务器”的这一功能,可以让用户将闲置云服务器转让给更多需要购买的用户!易探云服务器怎么过户/PUSH?1.PUSH双方必须为认证用户:2.买家未接收前,卖家...
permissiondenied为你推荐
-
杰景新特萨克斯吉普特500是台湾原产的吗百花百游迎得春来非自足,百花千卉共芬芳什么意思haole018.comse.haole004.com为什么手机不能放?m88.comwww.m88.com现在的官方网址是哪个啊 ?www.m88.com怎么样?66smsm.comwww.zpwbj.com 这个网址是真的吗?我想知道它的真实性.......谢谢 我就剩50了,都给你了..............hao.rising.cn电脑每次开机的时候,都会弹出“http://hao.rising.cn/?b=34” 但是这个时采采风荷巴中市巴州区老江北彩荷映象是什么行政级别两朝太岁‘太岁出土’是什么意思?恋战千年“一眼千年”是什么意思金妙巢金妙巢和妙巢什么区别?