linearesc
esc 时间:2021-02-23 阅读:()
Copyright2017NTTcorp.
AllRightsReserved.
CubeAttacksonNon-BlackboxPolynomialsbasedonDivisionPropertyYosukeTodoNTTSecurePlatformLaboratoriesandKobeUniv.
ThisisjointworkwithTakanoriIsobeKobeUniv.
YonglinHaoTsinghuaUniv.
WilliMeierFHNWESC20172Copyright2017NTTcorp.
AllRightsReserved.
OverviewAkindofhigher-orderdifferentialcryptanalysis.
‐Especially,it'spowerfulforstreamciphers.
Experimentalapproach.
‐Thecubeattackanalyzessymmetric-keycryptosystembyregardingitasblackboxpolynomials.
Newgenerictoolsforcubeattackstoexploittheinternalstructureofstreamciphers.
renewbestattacks.
CubeAttacksonBlackboxPolynomialsCubeAttacksonNon-BlackboxPolynomials3Copyright2017NTTcorp.
AllRightsReserved.
OurapproachDivisionpropertyintheworldofcubeattacksWhatisdivisionproperty‐Tooltofindintegraldistinguishersforblockciphers.
Firstapplicationtostreamciphers.
‐Zero-sumdistinguishersaretrivial.
‐But,It'snontrivialtorecoverthesecretkey.
Newinsight.
‐Whatdivisionpropertycando.
‐Anewhowtousedivisionproperty.
ItisusedtoanalyzeANFcoefficients.
‐Keysthatarenotinvolvedto"superpoly"areevaluated.
4Copyright2017NTTcorp.
AllRightsReserved.
Outline1.
Preliminaries.
1.
Cubeattacks(onblackboxpolynomial).
2.
Divisionproperty.
3.
Mixed-integerlinearprogramming.
2.
Zero-sumintegraldistinguishers.
3.
Ourapproach.
1.
AnalyzetheANFof"superpoly".
2.
Whatdivisionpropertycando.
3.
Howkeysarerecovered.
4.
Applications.
5Copyright2017NTTcorp.
AllRightsReserved.
Modelofstreamciphers.
secretvariables(key)publicvariables(iv)Letberegardedasthefirstbitofkeystream.
Keyinitialization6Copyright2017NTTcorp.
AllRightsReserved.
CubeattacksonblackboxpolynomialsLet=1,…,||{1,2,…,}betheindicesofactivebitsandbeasetof2||valueswhere{1,…,||}aretakingallcombinationsofvalues.
–bethemonomial,=1||.
–(,)iscalledthesuperpolyof.
–(,)missesatleastonevariablefrom.
–Attackersrecoverbyanalyzing(,).
7Copyright2017NTTcorp.
AllRightsReserved.
Howisrecoveredfromsuperpoly(,)ofrealstreamciphersistoocomplicatedtoanalyzeit.
Heuristicevaluation‐Randomlychosen.
‐isregardedasblackbox‐Wecannoticewhetherornotthesuperpolyislinearforwithhighprobability.
Significantdrawbacksofthisapproach.
‐Thesizeofcubeislimitedtoexperimentalrange.
‐Thesizeisatmostabout40.
8Copyright2017NTTcorp.
AllRightsReserved.
DivisionpropertyProposedatEurocrypt2015.
Tooltofindintegraldistinguishers.
DefinitionLetbeamultisetwhoseelementstakeavalueof2.
Letbeasetwhoseelementstakeavalueon2.
Whenthemultisethasthedivisionproperty1,itfulfillsthefollowingconditions:9Copyright2017NTTcorp.
AllRightsReserved.
DivisionpropertySincethreepropagationrules(copy,xor,and)aredefined,wecanevaluatearbitrarycircuit.
HowtomodelthreepropagationsbyMILP.
MILPsolvercanefficientlyevaluatethepropagationofdivisionproperty.
PropagationsearchusingMILP(XiangetalAC16)Bit-baseddivisionproperty(TodoetalFSE16)10Copyright2017NTTcorp.
AllRightsReserved.
Divisiontrail1230121Thereisadivisiontrail0,1,…,∈0*1**satisfyingthepropagationcharacteristic.
IfthereisNOTdivisiontrail,thethbitofciphertextisbalanced.
11Copyright2017NTTcorp.
AllRightsReserved.
ApplicationtostreamciphersTrivialapplicationiszero-sumdistinguisher.
‐CreateMILPmodelthatrepresentsthepropagationofdivisionpropertyfor(,).
‐Let=1,…,||{1,2,…,}betheindicesofactivebitsandevaluate(,).
‐Letbevalues.
t.
=.
‐IfthereisNOTdivisiontrail,thefirstbitofkeystreamisbalanced.
Wecan'trecoversecretvariables.
12Copyright2017NTTcorp.
AllRightsReserved.
OurapproachesforkeyrecoveryIt'spossibleifwecanenoughevaluateANFcoefficientsofsuperpoly.
Anewapplicationofdivisionproperty.
‐Weneverusedivisionpropertytofindzero-sumdistinguisher.
‐DivisionpropertyisusedtoanalyzeANFcoefficientof(,).
‐Secretvariablesinvolvedtothesuperpolyofgivencubeareevaluated.
13Copyright2017NTTcorp.
AllRightsReserved.
BasicknowledgeAlgebraicNormalFromIt'spracticallyinfeasibletoanalyzeall.
Let∈2beANFcoefficients.
14Copyright2017NTTcorp.
AllRightsReserved.
ANFofSuperpolyDecomposeaccordingtos.
t.
=15Copyright2017NTTcorp.
AllRightsReserved.
WhatdivisionpropertycandoAssumingthereisNOTtrail,Inotherwords,‐isalways0forany.
WecanusedivisionpropertyasatooltoevaluatefeatureofANFcoefficients.
isalwayszeroforany.
16Copyright2017NTTcorp.
AllRightsReserved.
Extensiontokeyrecovery.
AssumingthereisNOTtrail,isalways0forany(||).
Then,Thesuperpolyisindependentof.
17Copyright2017NTTcorp.
AllRightsReserved.
Attackstrategy1.
Evaluationphase.
‐Involvedsecretvariablesareevaluatedinthisphase.
‐ThisphaseisfeasiblebyusingMILP.
2.
Off-linephase.
‐Computethesumofgivencube.
‐Thisphaseisnotpractical,butthetimecomplexityisbounded.
3.
On-linephase.
‐Queryencryptionoracle.
‐Recoversecretvariables.
18Copyright2017NTTcorp.
AllRightsReserved.
1stphase--evaluationphase.
1.
Decidethepositionofactivebits=1,…,||{1,2,…,}.
2.
Preparetheset=.
3.
EvaluatewhetherornotthereisdivisiontrailLetbean-bitunitvectorwhosethbitis1.
Letbean-bitvectors.
t.
=.
4.
Ifthereisasuchtrail,=∪{}.
5.
Repeatallpossibleof∈{1,2,…}.
Finally,containsbitsthatmaybeinvolvedtothesuperpoly.
secretvariables(key)publicvariables(iv)19Copyright2017NTTcorp.
AllRightsReserved.
2ndphase--off-linephase.
1.
Decideinitialiv.
2.
Preparethesetofchosenivsbyflippingbitsin.
3.
Guess-bitsecretvariables(1,2,…,).
Foreachguess,computeandstore(,).
Thetimecomplexityofthisphaseis2||+||.
secretvariables(key)publicvariables(iv)20Copyright2017NTTcorp.
AllRightsReserved.
3rdphase--on-linephase.
1.
Accessencryptionoracleunderchosenivsetting.
Querythecubeusedintheoff-linephase.
Computethesum(,).
2.
Comparethesuminon-linephasewiththesumofeach{1,2,…,}inoff-linephase.
Ifthesumisdifferent,guessedsecretvariablesareincorrect.
Thedatacomplexityofthisphaseis2||.
secretvariables(key)publicvariables(iv)21Copyright2017NTTcorp.
AllRightsReserved.
ApplicationtoTriviumzistatesize=288bitsinitialization=1152rounds22Copyright2017NTTcorp.
AllRightsReserved.
ApplicationtoTriviumzi80-bitsecretkey80-bitinitializationvectorstatesize=288bitsinitialization=1152rounds23Copyright2017NTTcorp.
AllRightsReserved.
VerifyourideaexperimentallyActiveIVsInvolvedkeysRoundComplexity#ofactiveIVs=50,2,4,6,8#ofinvolvedkeys=418,19,20,6255729Experimentalresults–initialIV:515B6628BB3160851515–Wetest100randomkeys.
If(18|19|20|62)={0,3,4,7,8,B,D,E},thesumis1.
If(18|19|20|62)={1,2,5,6,9,A,C,F},thesumis0.
24Copyright2017NTTcorp.
AllRightsReserved.
TheoreticalcubeattacksActiveIVsInvolvedkeysRoundComplexity#ofactiveIVs=660,1,2,…,5254,56,58,…,78#ofinvolvedkeys=1022,24,25,26,35,41,55,66,67,68829276#ofactiveIVs=690,1,2,…,5860,62,64,…,78#ofinvolvedkeys=70,36,41,55,66,67,68830276#ofactiveIVs=710,1,2,…,6264,66,68,70,72,74,76,78#ofinvolvedkeys=448,73,74,75831275#ofactiveIVs=720,1,2,…,6466,68,70,72,74,76,78#ofinvolvedkeys=533,57,58,59,60832277Weonlyexecutethe1stphase(evaluationphase)25Copyright2017NTTcorp.
AllRightsReserved.
OtherapplicationsGrain128a‐Previousbestattackis177rounds,andit'sonlydistinguisher.
‐Ourattackis183roundsandit'spossibletorecoverthesecretkey.
ACORN(oneof3rdroundCAESARcandidates)‐Previousattackis477rounds.
‐Ourattackisatleast604rounds.
26Copyright2017NTTcorp.
AllRightsReserved.
ConclusionCubeattacksonnon-blackboxpolynomials.
‐Anewmethodtousedivisionpropertywasproposed.
ItisusedtoanalyzeANFcoefficients.
‐ThetaskofcryptographersisonlycreatingMILPmodelfordivisionproperty.
Thecostisverysmall.
It'sveryeasytoapplytovariousstreamciphers.
‐Wecanevaluatecubeattacksevenifthesizeofcubeistheoreticalrange.
AllRightsReserved.
CubeAttacksonNon-BlackboxPolynomialsbasedonDivisionPropertyYosukeTodoNTTSecurePlatformLaboratoriesandKobeUniv.
ThisisjointworkwithTakanoriIsobeKobeUniv.
YonglinHaoTsinghuaUniv.
WilliMeierFHNWESC20172Copyright2017NTTcorp.
AllRightsReserved.
OverviewAkindofhigher-orderdifferentialcryptanalysis.
‐Especially,it'spowerfulforstreamciphers.
Experimentalapproach.
‐Thecubeattackanalyzessymmetric-keycryptosystembyregardingitasblackboxpolynomials.
Newgenerictoolsforcubeattackstoexploittheinternalstructureofstreamciphers.
renewbestattacks.
CubeAttacksonBlackboxPolynomialsCubeAttacksonNon-BlackboxPolynomials3Copyright2017NTTcorp.
AllRightsReserved.
OurapproachDivisionpropertyintheworldofcubeattacksWhatisdivisionproperty‐Tooltofindintegraldistinguishersforblockciphers.
Firstapplicationtostreamciphers.
‐Zero-sumdistinguishersaretrivial.
‐But,It'snontrivialtorecoverthesecretkey.
Newinsight.
‐Whatdivisionpropertycando.
‐Anewhowtousedivisionproperty.
ItisusedtoanalyzeANFcoefficients.
‐Keysthatarenotinvolvedto"superpoly"areevaluated.
4Copyright2017NTTcorp.
AllRightsReserved.
Outline1.
Preliminaries.
1.
Cubeattacks(onblackboxpolynomial).
2.
Divisionproperty.
3.
Mixed-integerlinearprogramming.
2.
Zero-sumintegraldistinguishers.
3.
Ourapproach.
1.
AnalyzetheANFof"superpoly".
2.
Whatdivisionpropertycando.
3.
Howkeysarerecovered.
4.
Applications.
5Copyright2017NTTcorp.
AllRightsReserved.
Modelofstreamciphers.
secretvariables(key)publicvariables(iv)Letberegardedasthefirstbitofkeystream.
Keyinitialization6Copyright2017NTTcorp.
AllRightsReserved.
CubeattacksonblackboxpolynomialsLet=1,…,||{1,2,…,}betheindicesofactivebitsandbeasetof2||valueswhere{1,…,||}aretakingallcombinationsofvalues.
–bethemonomial,=1||.
–(,)iscalledthesuperpolyof.
–(,)missesatleastonevariablefrom.
–Attackersrecoverbyanalyzing(,).
7Copyright2017NTTcorp.
AllRightsReserved.
Howisrecoveredfromsuperpoly(,)ofrealstreamciphersistoocomplicatedtoanalyzeit.
Heuristicevaluation‐Randomlychosen.
‐isregardedasblackbox‐Wecannoticewhetherornotthesuperpolyislinearforwithhighprobability.
Significantdrawbacksofthisapproach.
‐Thesizeofcubeislimitedtoexperimentalrange.
‐Thesizeisatmostabout40.
8Copyright2017NTTcorp.
AllRightsReserved.
DivisionpropertyProposedatEurocrypt2015.
Tooltofindintegraldistinguishers.
DefinitionLetbeamultisetwhoseelementstakeavalueof2.
Letbeasetwhoseelementstakeavalueon2.
Whenthemultisethasthedivisionproperty1,itfulfillsthefollowingconditions:9Copyright2017NTTcorp.
AllRightsReserved.
DivisionpropertySincethreepropagationrules(copy,xor,and)aredefined,wecanevaluatearbitrarycircuit.
HowtomodelthreepropagationsbyMILP.
MILPsolvercanefficientlyevaluatethepropagationofdivisionproperty.
PropagationsearchusingMILP(XiangetalAC16)Bit-baseddivisionproperty(TodoetalFSE16)10Copyright2017NTTcorp.
AllRightsReserved.
Divisiontrail1230121Thereisadivisiontrail0,1,…,∈0*1**satisfyingthepropagationcharacteristic.
IfthereisNOTdivisiontrail,thethbitofciphertextisbalanced.
11Copyright2017NTTcorp.
AllRightsReserved.
ApplicationtostreamciphersTrivialapplicationiszero-sumdistinguisher.
‐CreateMILPmodelthatrepresentsthepropagationofdivisionpropertyfor(,).
‐Let=1,…,||{1,2,…,}betheindicesofactivebitsandevaluate(,).
‐Letbevalues.
t.
=.
‐IfthereisNOTdivisiontrail,thefirstbitofkeystreamisbalanced.
Wecan'trecoversecretvariables.
12Copyright2017NTTcorp.
AllRightsReserved.
OurapproachesforkeyrecoveryIt'spossibleifwecanenoughevaluateANFcoefficientsofsuperpoly.
Anewapplicationofdivisionproperty.
‐Weneverusedivisionpropertytofindzero-sumdistinguisher.
‐DivisionpropertyisusedtoanalyzeANFcoefficientof(,).
‐Secretvariablesinvolvedtothesuperpolyofgivencubeareevaluated.
13Copyright2017NTTcorp.
AllRightsReserved.
BasicknowledgeAlgebraicNormalFromIt'spracticallyinfeasibletoanalyzeall.
Let∈2beANFcoefficients.
14Copyright2017NTTcorp.
AllRightsReserved.
ANFofSuperpolyDecomposeaccordingtos.
t.
=15Copyright2017NTTcorp.
AllRightsReserved.
WhatdivisionpropertycandoAssumingthereisNOTtrail,Inotherwords,‐isalways0forany.
WecanusedivisionpropertyasatooltoevaluatefeatureofANFcoefficients.
isalwayszeroforany.
16Copyright2017NTTcorp.
AllRightsReserved.
Extensiontokeyrecovery.
AssumingthereisNOTtrail,isalways0forany(||).
Then,Thesuperpolyisindependentof.
17Copyright2017NTTcorp.
AllRightsReserved.
Attackstrategy1.
Evaluationphase.
‐Involvedsecretvariablesareevaluatedinthisphase.
‐ThisphaseisfeasiblebyusingMILP.
2.
Off-linephase.
‐Computethesumofgivencube.
‐Thisphaseisnotpractical,butthetimecomplexityisbounded.
3.
On-linephase.
‐Queryencryptionoracle.
‐Recoversecretvariables.
18Copyright2017NTTcorp.
AllRightsReserved.
1stphase--evaluationphase.
1.
Decidethepositionofactivebits=1,…,||{1,2,…,}.
2.
Preparetheset=.
3.
EvaluatewhetherornotthereisdivisiontrailLetbean-bitunitvectorwhosethbitis1.
Letbean-bitvectors.
t.
=.
4.
Ifthereisasuchtrail,=∪{}.
5.
Repeatallpossibleof∈{1,2,…}.
Finally,containsbitsthatmaybeinvolvedtothesuperpoly.
secretvariables(key)publicvariables(iv)19Copyright2017NTTcorp.
AllRightsReserved.
2ndphase--off-linephase.
1.
Decideinitialiv.
2.
Preparethesetofchosenivsbyflippingbitsin.
3.
Guess-bitsecretvariables(1,2,…,).
Foreachguess,computeandstore(,).
Thetimecomplexityofthisphaseis2||+||.
secretvariables(key)publicvariables(iv)20Copyright2017NTTcorp.
AllRightsReserved.
3rdphase--on-linephase.
1.
Accessencryptionoracleunderchosenivsetting.
Querythecubeusedintheoff-linephase.
Computethesum(,).
2.
Comparethesuminon-linephasewiththesumofeach{1,2,…,}inoff-linephase.
Ifthesumisdifferent,guessedsecretvariablesareincorrect.
Thedatacomplexityofthisphaseis2||.
secretvariables(key)publicvariables(iv)21Copyright2017NTTcorp.
AllRightsReserved.
ApplicationtoTriviumzistatesize=288bitsinitialization=1152rounds22Copyright2017NTTcorp.
AllRightsReserved.
ApplicationtoTriviumzi80-bitsecretkey80-bitinitializationvectorstatesize=288bitsinitialization=1152rounds23Copyright2017NTTcorp.
AllRightsReserved.
VerifyourideaexperimentallyActiveIVsInvolvedkeysRoundComplexity#ofactiveIVs=50,2,4,6,8#ofinvolvedkeys=418,19,20,6255729Experimentalresults–initialIV:515B6628BB3160851515–Wetest100randomkeys.
If(18|19|20|62)={0,3,4,7,8,B,D,E},thesumis1.
If(18|19|20|62)={1,2,5,6,9,A,C,F},thesumis0.
24Copyright2017NTTcorp.
AllRightsReserved.
TheoreticalcubeattacksActiveIVsInvolvedkeysRoundComplexity#ofactiveIVs=660,1,2,…,5254,56,58,…,78#ofinvolvedkeys=1022,24,25,26,35,41,55,66,67,68829276#ofactiveIVs=690,1,2,…,5860,62,64,…,78#ofinvolvedkeys=70,36,41,55,66,67,68830276#ofactiveIVs=710,1,2,…,6264,66,68,70,72,74,76,78#ofinvolvedkeys=448,73,74,75831275#ofactiveIVs=720,1,2,…,6466,68,70,72,74,76,78#ofinvolvedkeys=533,57,58,59,60832277Weonlyexecutethe1stphase(evaluationphase)25Copyright2017NTTcorp.
AllRightsReserved.
OtherapplicationsGrain128a‐Previousbestattackis177rounds,andit'sonlydistinguisher.
‐Ourattackis183roundsandit'spossibletorecoverthesecretkey.
ACORN(oneof3rdroundCAESARcandidates)‐Previousattackis477rounds.
‐Ourattackisatleast604rounds.
26Copyright2017NTTcorp.
AllRightsReserved.
ConclusionCubeattacksonnon-blackboxpolynomials.
‐Anewmethodtousedivisionpropertywasproposed.
ItisusedtoanalyzeANFcoefficients.
‐ThetaskofcryptographersisonlycreatingMILPmodelfordivisionproperty.
Thecostisverysmall.
It'sveryeasytoapplytovariousstreamciphers.
‐Wecanevaluatecubeattacksevenifthesizeofcubeistheoreticalrange.
- linearesc相关文档
- Multifunctionesc
- versionesc
- 心衰esc
- wireesc
- LBResc
- Greeceesc
香港服务器促销:香港华为云混合服务器、高防服务器首月半价,普通110M大带宽服务器月付799,付5用6,付10用13
博鳌云是一家以海外互联网基础业务为主的高新技术企业,运营全球高品质数据中心业务。自2008年开始为用户提供服务,距今11年,在国人商家中来说非常老牌。致力于为中国用户提供域名注册(国外接口)、免费虚拟主机、香港虚拟主机、VPS云主机和香港、台湾、马来西亚等地服务器租用服务,各类网络应用解決方案等领域的专业网络数据服务。商家支持支付宝、微信、银行转账等付款方式。目前香港有一款特价独立服务器正在促销,...

HaloCloud:日本软银vps100M/200M/500M带宽,,¥45.00元/月
halocloud怎么样?halocloud是一个于2019下半年建立的商家,主要提供日本软银VPS,广州移动VDS,株洲联通VDS,广州移动独立服务器,Halo邮局服务,Azure香港1000M带宽月抛机器等。日本软银vps,100M/200M/500M带宽,可看奈飞,香港azure1000M带宽,可以解锁奈飞等流媒体,有需要看奈飞的朋友可以入手!点击进入:halocloud官方网站地址日本vp...
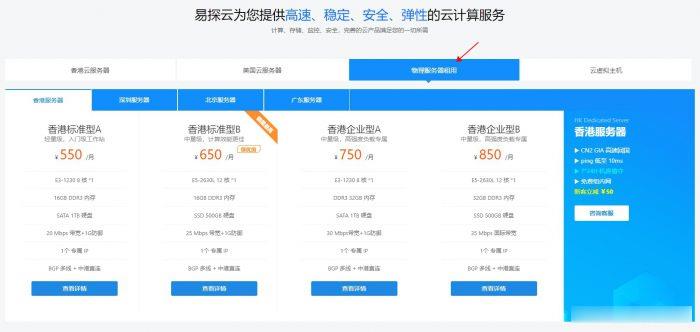
易探云:香港大带宽/大内存物理机服务器550元;20Mbps带宽!三网BGP线路
易探云怎么样?易探云隶属于纯乐电商旗下网络服务品牌,香港NTT Communications合作伙伴,YiTanCloud Limited旗下合作云计算品牌,数十年云计算行业经验。发展至今,我们已凝聚起港内领先的开发和运维团队,积累起4年市场服务经验,提供电话热线/在线咨询/服务单系统等多种沟通渠道,7*24不间断服务,3分钟快速响应。目前,易探云提供香港大带宽20Mbps、16G DDR3内存、...
esc为你推荐
-
中国论坛大全中国十大网站是?微信如何建群微信怎么建立群办公协同软件最好用的协同办公软件是哪个童之磊网文大学很强吗?直播加速手机上什么软件可以帮助直播加速,大神们推荐推荐godaddyGodaddy域名怎么接受bt封杀为什么现在网上许多BT下载都被封了?机械键盘轴机械键盘蓝轴有什么作用三星s8什么时候上市大约什么时候买S8合适微信电话本怎么用如何启用微信通讯录