输入网站漏洞检测归类和解决方案(Site vulnerability detection, classification and solution)
网站漏洞检测归类和解决方案Site vulnerability detection,classification and solution
DOC documents may experience poor browsing on the WAP side. Itis recommended that you first select TXT, or download the sourcefile to the local view.
A,
Typical website vulnerability classification
According to the risk level, the website vulnerability can bedivided into three kinds of high risk, medium risk and low risk.Among them, high-risk vulnerabilities must be blocked. Some ofthe loopholes in the medium and low risk vulnerabilities mustbe blocked. There are also some medium and low riskvulnerabilities, which may be selectively blocked because thecost of plugging may be higher than the losses caused by nonblocking. Tools can be used to search the platform forvulnerability scanning, the specific address is:http://www. iiscan.com typical website vulnerabilityclassification and corresponding sealing requirements as shownin the table below:
Risk level
1, the highriskof SQL injection2, cross site vulnerabilitiesMedium and low risk 1, default test case file 2, managementbackground landing portal
Medium and low risk 1, email address exists
Vulnerability name
3, XPATH injection leak 3, application error caused by 2,invalid link hole information leakage 4, backup files causedby source code leakage 3, Web application default directorySealing requirement
Must plug
Selective plugging
One
Two,
Typical website vulnerability impact and Solutions
1, SQL injection vulnerability impact: this vulnerabilitybelongs to the common vulnerabilities in Web applicationsecurity, belonging to OWASP TOP 10 (2007) in the injectionclass vulnerabilities. SQL injection vulnerabilities arepresent in many WEB applications. SQL injection is an attackerwhouses code flaws to attack, and canbe used in any applicationparameter that can affect database queries. For example, theparameters of the URL itself, post data, or cookie values. Anormal SQL injection attack depends largely on the attacker' saccess to information from the error message. However, even ifno error messages are displayed, the application may still be
affected by the SQL injection. In general, SQL injection is anattack on Web applications rather than on the web server or theoperating system itself. As its name suggests, SQL injectionis the act of adding unexpected SQL commands to a query tomanipulate the database in a way that database administratorsor developers do not anticipate. If successful, you can obtain,modify, inject, or delete data from the database server thatis used by the vulnerability web application. In some cases,the SQL can be injected into the fully controlled system.Solution: protection recommendations include the deployment oflayered security measures (including in accept user input whenusing parameterized queries) , to ensure that applications useonly the expected data, strengthening the database server toprevent access data inappropriate. The following measures arerecommended to prevent SQL injection vulnerabilities:Two
Use the following suggestions for development. Written from theweb applicationof SQL injectionattack effect. Aparameterizedquery: SQL injection from the attacker control data to modifythe query query logic, so the best way to prevent SQL injectionattacks is to query the logic and data separation, which canprevent the execution of the injection from the user inputcommands. Defects in this way are likely to have an impact onperformance (but with little impact) , and each query on the sitemust be constructed in this way to be fully valid. Justbypassing a query inadvertently is enough to cause theapplication to be affected bySQL injection. The following codeshows an example of a SQL statement that can do SQL injection.
SSql = "SELECT, LocationName, Locations, FROM"; sSql = sSql +,"WHERE, LocationID =" + Request[, "LocationID" [] =oCmd.CommandText = sSq l;
The following example uses parameterized queries that are notaffected by SQL injection attacks.
SSql = "SELECT * FROM Locations"";ssql = ssql + “LocationID = @ LocationID” ocmd. commandtext= ssql ocmd。参数。添加 “@LocationID” 要求“LocationID[” ]
应用程序没有包含用户输入向服务器发送SQL语句而是使用@LocationID-参数替代该输入这样用户输入就无法成为SQL执行的命令。
三
这种方式可以有效的拒绝攻击者所注入的任何输入尽管仍会生成错误但仅为数据类型转换错误而不是黑客可以利用的错误。以下代码示例显示从HTTP查询字符串中获得产品ID并使用到SQL查询中。请注意传送给SqlCommand的包含有选择的字符串仅仅是个静态字符串不是从输入中截取的。此外还请注意使用Sql Parame ter对象传送输入参数的方式该对象的名称@ PID匹配SQL查询中所使用的名称。
C #示例
一串connstring
=webconf igurationmanager。 connectionStrings [ “myconn” ] 。connectionstr ING使用SqlConnection conn=新的SqlConnectionconnstring {康涅狄格州open() SqlCommand CMD =新SqlCommand “select count *从产品prodid= “PID” CONNSqlParameter prm =新的SqlParameter “PID”
SqlDbType.VarChar 50 PRM。值=请求。 QueryString [ “PID” ] CMD参数。添加PRM int reccount=int命令。executescalar() }
四vb.net示例
昏暗的connstring
作为
字符串
=webconf igurationmanager。 ConnectionStrings “ConnectionString myconn” 。
使用新的SqlConnection conn connstring康涅狄格州open()暗淡CMD为SqlCommand=新SqlCommand “sel ect count *从产品prodid = “PID” CONN昏暗的PRM为SqlParameter =新的SqlParameter “PID”
SqlDbType.VarChar 50 PRM。值=请求。 QueryString “PID” 命令参数。添加PRM昏暗的reccount整数=CMD executescalar()端使用。
验证输入可通过正确验证用户输入的类型和格式防范大多数SQL注入攻击最佳方式是通过白名单定义方法为对于相关的字段只接受特定的帐号号码或帐号类型或对于其他仅接受英文字母表的整数或字母。很多开发人员都试图使用黑名单字符或转义的方式验证输入。总体上讲这种方式通过在恶意数据前添加转义字符来拒绝已知的恶意数据如单引号这样之后的项就可以用作文字值。
五
这种方式没有白名单有效 因为不可能事先知道所有形式的恶意数据。
对于安全操作============
使用以下建议帮助防范对Web应用的SQL注入攻击。
限制应用程序权限 限制用户凭据仅使用应用运行所必需权限的。任何成功的SQL注入攻击都会运行在用户凭据的环境中尽管限制权限无法完全防范SQL注入攻击但可以大大增加其难度。
强系统管理员口令策略通常攻击者需要管理员帐号的功能才能使用特定的SQL命令如果系统管理员口令较弱的话就比较容易暴力猜
测
Increase the likelihood of successful SQL injection attacks.Another option is not to use the system administrator passwordat all, but to create a specific account for a specific purpose.Consistent error message program: make sure you provide aslittle information as possible when a database error occurs.Do not leak the entire error message and process error messageson both the web and the application server. When a web serverencounters a processing error, a generic web page responseshouldbeused, or the user redirectedto the standard location.Never release debug information or other details that might beuseful to attackers.
For instructions on how to close verbose errormessages in IIS,see:
Six
Http://www.microsoft.com/windows2000/en/server/i is/def ault.asp? Url= /windows2000/en/server/i is/htm/core/iierrcst.htm?Use the syntax below to suppress error messages on the Apacheserver:
Syntax: , ErrorDocument, <3-digi t-code>, Examp le: ,
ErrorDocument, 500, /webserver_errors/server_error500. txtApplication servers like WebSphere usually default byinstalling error messages or debugging settings. For
information about how to suppress these error messages, referto the application server document.
Stored procedures: if not used, delete the SQL storedprocedures such as master. .Xp_cmdshell, xp_startmail,xp_sendmail, sp_makewebtask, and so on.
The SQL injection vulnerability fundamentally depends on thecode for the web application. Although not a fix, you can detectSQL injection attacks by adding rules that incorporate regularexpressions to IDS as an emergency measure. Although it isimpossible to fix all possible SQL injection vulnerabilities,it is easy to implement and requires attackers to improve theirmethods in order to achieve successful attacks. Regularexpressions can be used as follows.
Delete the SQL regular expression metacharacters: / (\%27) |(' ) | (\-\-) | (\%23) | (#) /ix
Seven
Following the regular expression canbe added to the Snort alertTCP$EXTERNAL_NET ru l es: any-> $HTTP_SERVERS$HTTP_PORTS (msg:"SQL Injection-
Paranoid; flow:to_server, established; uricontent: .Pl ; pcre:/ (\%27) | (' ) | (\-\ -) | (%23) | (#) ;classtype:Web-application-attack; sid:9099; /i rev:5) ;The regular expression of traditional SQL injection attacks:/\w* ((\%27) | (' ) ( |o| ) (\%6F) (\%4F) ( |r| ) (\%72) (\%52)) /ix
The regular expression to delete the UNION keyword SQLinjection attack: / ((\%27) | (' )) union/ix (\%27) | (' )Similar regular expressions can be written for other SQLqueries such as select, insert, update, delete, drop, and soon.
Regular expressions for SQL injection attacks are detected onthe MS SQL server: /exec (\s|\+) + (s|x) p\w+/ix
For quality assurance ============
E i gh t
Addressing SQL injection defects ultimately requires codebased fixes, providing information necessary to fix thesevulnerabilities for development and for the steps described inthe security operations section. The following steps outlinehow to manually test SQL injection for an application.How do you manually test SQL injection into an application?:
1. open web applications that want to test SQL injectionvulnerabilities in your browser.
2. hover the mouse cursor over the link to the Web site and payattention to the status bar at the bottom. You can see the URLto which the link points. Find the URL with parameters, suchas
- 输入网站漏洞检测归类和解决方案(Site vulnerability detection, classification and solution)相关文档
- 模块网站漏洞检测软件WEBSCAN的策划和完成.doc
- 输入网站漏洞检测归类和解决方案(Website vulnerability detection, classification and solution)
- 漏洞网站漏洞检测软件的设计与应用
- 病毒学校规章制度之中学网站病毒检测和网络安全漏洞监测制度
- 漏洞网站漏洞检测软件的设计与应用(本科范文)
- 网站漏洞检测谁有网站漏洞检测工具?一般黑客使用的,急需!可以发到我邮箱qiutiandaole010@163.com
小欢互联19元/月起, 即日起至10月底 美国CERA 促销活动 美国/香港八折
小欢互联成立于2019年10月,主打海外高性价比云服务器、CDN和虚拟主机服务。近期上线了自营美国CERA机房高速VPS,进行促销活动,为客户奉上美国/香港八折优惠码:Xxc1mtLB优惠码适用于美国CERA一区/二区以及香港一区/二区优惠时间:即日起至10月底优惠码可无限次使用,且续费同价!官网:https://idc.xh-ws.com购买地址:美国CERA一区:https://idc.xh-...
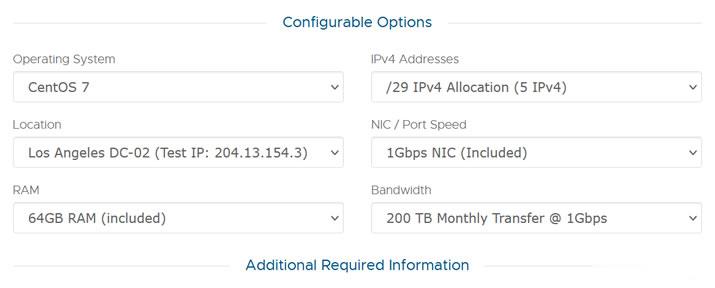
月费$389,RackNerd美国大硬盘独立服务器
这次RackNerd商家提供的美国大硬盘独立服务器,数据中心位于洛杉矶multacom,可选Windows、Linux镜像系统,默认内存是64GB,也可升级至128GB内存,而且硬盘采用的是256G SSD系统盘+10个16TSAS数据盘,端口提供的是1Gbps带宽,每月提供200TB,且包含5个IPv4,如果有需要更多IP,也可以升级增加。CPU核心内存硬盘流量带宽价格选择2XE5-2640V2...
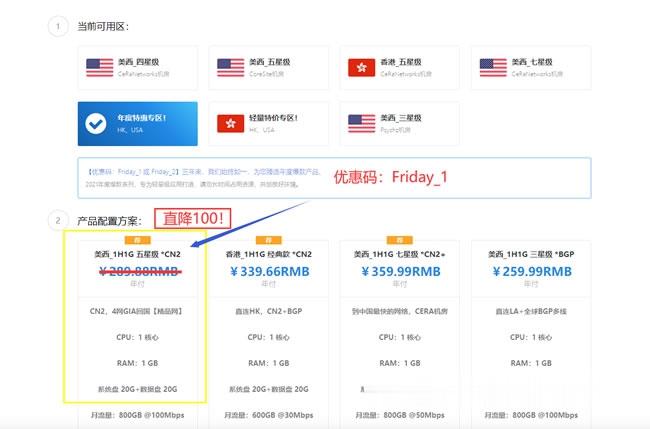
极光KVM美国美国洛杉矶元/极光kvmCN7月促销,美国CN2 GIA大带宽vps,洛杉矶联通CUVIP,14元/月起
极光KVM怎么样?极光KVM本月主打产品:美西CN2双向,1H1G100M,189/年!在美西CN2资源“一兆难求”的大环境下,CN2+大带宽 是很多用户的福音,也是商家实力的象征。目前,极光KVM在7月份的促销,7月促销,美国CN2 GIA大带宽vps,洛杉矶联通cuvip,14元/月起;香港CN2+BGP仅19元/月起,这次补货,机会,不要错过了。点击进入:极光KVM官方网站地址极光KVM七月...
-
restrictionsserver支持ipad支持ipad支持ipad支持ipadipadwifiipad的wifi打不开怎么办?css下拉菜单html+css下拉菜单怎么制作127.0.0.1为什么输入127.0.0.1无法打开页面google中国地图谷歌中国地图用的是什么投影,什么坐标系360chrome360的chrome浏览器进程有点多哦???