Tejara166dd.com
166dd.com 时间:2021-04-08 阅读:()
Copyright2018AccentureSecurity.
Allrightsreserved.
1GOLDFIN:APersistentCampaignTargetingCISCountrieswithSOCKSBOTJuly26,2018CYBERADVISORYCopyright2018AccentureSecurity.
Allrightsreserved.
2SUMMARYAnumberofsecurityvendorsreportedaseriesofcyber-attacksinvolvingtheuseofamalwarefamilycalledSOCKSBOTandclaimedtobeassociatedwithCANDLEFISH(a.
k.
a.
Patchwork,DroppingElephant).
However,asdisclosedinthisreport,researchbyiDefenseanalystsshowsthatSOCKSBOTwasinfactusedbyathreatgroupinan18-month-longcampaigndubbedGoldfin,spoofingfinancialinstitutionsintheCommonwealthofIndependentStates(CIS)countriessinceasearlyasFebruary2017toasrecentlyasMay2018.
Basedonthetactics,techniquesandprocedures(TTPs)observedinthiscampaign,iDefenseassesseswithmoderateconfidencethatthereportedcampaignisunlikelytobeassociatedwithCANDLEFISH.
Inaddition,iDefenseanalystshaveidentifiedinfrastructureoverlapandtheshareduseofaPowerShellobfuscationtechniquewithFIN7.
AlthoughtheseobservationsarenotenoughtoattributetheGoldfincampaigntoFIN7,iDefenseassessesthesetobeinterestingandnoteworthyobservationsthatfurtherhighlightsthecomplexrelationshipsthatexistbehind-the-sceneinorganizedcybercrime.
HOWTOUSETHISREPORTINTENDEDAUDIENCEiDefenseisprovidinginformationaboutthereportedcampaignstothegeneraliDefensecustomerbase,withthisreportbeingintendedforsecurityoperationscenter(SOC)analystsandengineers.
Managementandexecutiveleadershipmayalsowanttousethisinformation.
HOWTOUSETHISINTELLIGENCEiDefenseisprovidingthisinformationsothatcustomersareawareofthemodusoperandiofahighlyactivethreatgroupthatistargetingfinancialinstitutionsforfinancialgain.
SOCanalystsandengineerscanusethisIA'sdetailedinformationpertainingtotheworkingsofamalwarefamilyandindicatorsofcompromise(IoCs)tocontainormitigatethediscussedthreatthroughmonitoringorblocking.
SOCanalystscanusetheinformationprovidedintheAnalysisandMitigationsectionsofthisIAforhuntingactivitiesforsystemsthatmayhavealreadybeencompromised.
AnalystsandsecurityengineerscanusetheIoCsbyaddingthemtohuntinglistsonendpointdetectionandresponse(EDR)solutionsaswellasnetwork-andhost-basedblackliststodetectanddenymalwareimplantationandcommand-and-control(C2)communication.
IntelligenceanalystsmaywanttousetheinformationprovidedinthisIAtobetterinformtheirownanalyses.
TheprovidedinformationcanalsohelpinformongoingintelligenceCopyright2018AccentureSecurity.
Allrightsreserved.
3analysesandforensicinvestigations,particularlyforcompromisediscovery,damageassessment,andattribution.
Managementandexecutiveleadershipmayusethisinformationtoassesstherisksassociatedwiththethreatdescribedhereintomakeoperationalandpolicydecisionsaccordingly.
HOWTHISINTELLIGENCEHELPSADDRESSEXISTINGORPOTENTIALTHREATSKnowledgeofthegroup'stactics,techniques,andprocedures(TTPs)shouldhelptobetterinformdetectionandresponsetoattacksbythisthreatgroup.
CAMPAIGNANALYSISiDefenseanalystscameacrosstwospear-phishingcampaignsinOctober2017involvingtheuseofamalwarefamilypubliclyknownasSOCKSBOT.
OnecampaignspoofstheHalykBank(Exhibit1)andanotherspoofsthePrivatBank(Exhibit2):Exhibit1:Spear-PhishingEmailSpoofingHalykBankCopyright2018AccentureSecurity.
Allrightsreserved.
4Exhibit2:ContentofaSpear-PhishingE-mailSpoofingPrivatBankSharedonthePublicForumdoneckforum.
comAsExhibits1and2show,bothemailscontainanidenticalmessage,evendowntothelocationoftheembeddedhyperlinks.
TheonlydifferencesaretheembeddedURLsandthesignatureoftheemailinordertoreflectthefinancialinstitutiontheattackerswerespoofing.
Thisinformationsuggestssomesortofphishingkitwaslikelyusedtogeneratethephishingemails.
Anapproximatetranslationofthee-mailspoofingHalykBankisasfollows:Subject:Notificationofopeninganaccount(HalykBankofKazakhstan)Dearcustomer,anaccountwiththePeople'sBankofKazakhstanhasbeenopenedinyourname,youcanfinddetailedinformationintheattachedfile.
Ifyoudidnotreceiveanenvelopewithaloginandpassword,thenyouneedtoregistertoaccessthePersonalArea.
Incaseoflossoflogin/password,youcanregisteranewoneinthesection"Passwordrecovery".
Ifintheprocessofworkyouhaveanyquestionsorproblems,pleasecontacttheCustomerServiceDepartmentatthecontactslistedbelow.
Ourspecialistsarealwaysreadytohelpyou.
Theembeddedmalicioushyperlinksusedintherespectiveattacksareasfollows:hxxp://halyk-bank[.
]com/dog.
ziphxxp://privatbank-ua[.
]com/dog.
zipSubsequenttechnicalanalysisoftheinfectionchaininvolvedlediDefensetouncoveran18-monthlongcampaignofspoofingbanksinCIScountries,withthemostrecentcampaignobservedonMay28,2018spoofingtheIdeaBankCJSC:Copyright2018AccentureSecurity.
Allrightsreserved.
5Exhibit3:Spear-PhishingEmailSpoofingIdeaBankCJSCTheforummemberreportsthattwospear-phishingemailswerereceived:oneclaimingtobeanotificationaboutopeninganaccountandtheotherclaimingtobeanotificationofaloanbeingtakenout.
Thecontentofthelatteremailisapproximatelytranslatedbelow:Dearclient,inyourname,aloanwasissuedtoIdeaBank,formoredetails,seetheattachedfileinwhichthefullnameandphonenumberofyourpersonalloanexpertisindicated,theamountandconditionsforrepayingtheloan.
Anenvelopewithacreditagreementwassenttoyouraddress.
Incaseyoudidnotreceivetheenvelope,youshouldcontactyourpersonalexpert.
Incaseoflossofthecontract,youcanrestoreitatthenearestbranchofthebankorrequestaduplicatethroughyourpersonalexpert.
Foranyquestionsyouareinterestedin,youcancontactyourpersonalexpertortheCustomerServiceDepartmentatthecontactslistedbelow.
Ourspecialistsarealwaysreadytohelpyou.
Yoursfaithfully,IdeaBankCJSCPhoneforcallsfromabroad:+375(17)306-33-14Intheattacksobserved,allinvolvedaphishingemailwithtwoembeddedURLsdirectingtheusertodownloadafilenameddog.
zip.
Basedonthecontentofthee-mailsandthedomainnames,thefollowingbankswerespoofedinthiscampaign:HalykBank(Kazakhstan)PrivatBank(Ukraine)IdeaBank(Belarus)Copyright2018AccentureSecurity.
Allrightsreserved.
6TejaraBank(Iran)Itisalsonoteworthythatinbothphishingkits,therearealwaystwohyperlinkslinkingtothesamemaliciousfile:oneinthebodyofthemessageandoneattheendofthee-mailinalinkcalledДоговор(whichtranslatestoContract).
Thenextsectiondetailstheinfectionchainthatfollowstheinitialdownload.
INFECTIONCHAINANALYSISThegeneralinfectionchainobservedinthiscampaignisasshowninExhibit4:Exhibit4:TheInfectionChainUsedintheSOCKSBOTCampaignSTAGE1-JAVASCRIPTDROPPERBothlinksdeliveredaZIParchivefilenameddog.
zip:hxxp://halyk-bank[.
]com/dog.
zip-211fbf34749df5e717e8b11fecb3f648hxxp://privatbank-ua[.
]com/dog.
zip-b3fb88a5aa791aea141bf3b4cf045355BothcontainaJavaScriptfilenameddog.
jswiththeMD5signatures9a273653364dfb143ff196d826d2bac4and21a09cf81f3584a741c7167f622d6c50,respectively.
TheJavaScriptfilecontainsheavilyobfuscatedcodeasExhibit5shows.
Themaliciouscodeisinfacthiddenascommentsandisdynamicallydeobfuscatedoncethescripthasbeenexecuted.
Copyright2018AccentureSecurity.
Allrightsreserved.
7Exhibit5:ObfuscatedCodeindog.
jsOncedeobfuscated(seeExhibit6),itisclearthatthecodeisdesignedtodotwothings:1.
Tolookforarunninganti-virusprocesses,suchasavp.
exe(KasperskyAntivirus).
Notethatsomevariantsofthemalwarealsosearchforekrn.
exe(ESET),cis.
exe(Comodo)andavgnt.
exe(Avira).
2.
TodropandexecuteaPowerShellscriptnamedsetup.
ps1.
ThisscriptisgeneratedbasedonBase64encodeddatastoredinvariablesnameddllDataandcode.
3.
Deletesetup.
ps1Exhibit6:DeobfuscatedCodeindog.
jsCopyright2018AccentureSecurity.
Allrightsreserved.
8STAGE2-POWERSHELLDROPPERWITHEMPIREThePowerShellscriptsetup.
ps1usedineachattackhastherespectiveMD5signatures521c81c62836a233a6e771bc3491300fand00c38b787eac602ffaed0b9372f2c443.
Thescriptisdesignedforthefollowing(seeExhibit7):1.
CreateaPowerShellscriptnamedcheckupdate.
ps1inC:\Users\Public\Downloads\(Thispathishardcodedinthemalware).
ThecontentofthisscriptisstoredinavariablenameddataandisBased64encoded2.
Createacmdletthatwould:a.
movethescriptcheckupdate.
ps1tothehomedirectoryforthecurrentPowerShellinstallb.
establishpersistencebycreatingaWindowsservicenamedCheckforupdates,setto"delay-auto"startandexecutecheckupdate.
ps13.
UseamodifiedversionofthefunctionInvoke-EventVwrBypassfromtheEmpirePost-exploitationframeworktobypassUACandexecutetheabovecmdletExhibit7:DeobfuscatedCodeinsetup.
ps1Copyright2018AccentureSecurity.
Allrightsreserved.
9STAGE3-POWERSHELLREFLECTIVELOADERSimilarly,checkupdate.
ps1usedineachattackhastherespectiveMD5signatures54e7f3a1a1a8857e35a45f4eb2a3317dand29573b1fa60bce8e04dd2a4d554a7447.
Unsurprisingly,thisscriptalsocontainsobfuscatedcode.
Themaliciouspayloadiscompressed,Base64encoded,andembeddedwithinthescript,whichissimilartoatechniqueusedinPowerSploit.
However,theobservedtechniqueappearstobeavariantofPowerSploitastheencodedpayloadisfurthersplitintoanumberofchunksthataredynamicallyloadedintoanarrayvariablenamed$OArrasshowninExhibit8:Exhibit8:ObfuscatedCodeincheckupdate.
ps1ThecodeisinfactaPowerShellreflectiveloaderscriptwithadynamic-linklibrary(DLL)binaryembeddedasBase64-encodeddata(Exhibit9).
Copyright2018AccentureSecurity.
Allrightsreserved.
10Exhibit9:DeobfuscatedCodeincheckupdate.
ps1STAGE4-SOCKSBOTThespecificSOCKSBOTsampleanalyzedinthisreporthasthefollowingproperties:Filename:socksbot.
dllMD5:90f35fd205556a04d13216c33cb0dbe3FileSize:17.
0KB(17408bytes)CompiledTimeStamp:2017-10-2717:46:05Copyright2018AccentureSecurity.
Allrightsreserved.
11Asmentionedinthelastsection,theSOCKSBOTimplantistypicallydeliveredasaBase64-encodedstringreflectivelyloaded(viatheReflectiveLoader@@YGKPAX@Zexportedfunction)inanewlystartedsvchost.
exeprocess.
Assuch,theimplantexistsonlyinmemoryandnevertouchesthedisk.
Theimplantwillfirstverifyifanyofthemutexesinthefollowingformatarepresentinordertonotruntwice:Global\%snpsGlobal\%sstpExhibit10showsanexampleofacreatedmutex.
Exhibit10:MutexCreationa321c0d8979a05bdnpsTheSOCKSBOTimplanthasthefollowingcapabilities:Enumerateprocesses(processlist)TakescreenshotsDownload,upload,write,andexecutefilesCreateandinjectintonewprocessesCommunicatetoC2viasocketsThisimplantwillcommunicatewiththedesignatedC2serverbyfirstcreatingabufferandwill,onfirstexecution,communicatetotheC2serverthatithassuccessfullyinfectedatargetbyusinga.
phpURIthatispseudo-randomlygenerated.
SOCKSBOTusestheObtainUserAgentStringAPItodeterminethedefaultuser-agentofthemachine.
AnexampleofarequesttotheC246.
166.
163[.
]243isshowninExhibit11.
Exhibit11:TraffictotheC2ServerTheC2serverortheoperatoroftheSOCKSBOTimplantcanthenrespondwithaspecificHTTPstatuscodetoperformasetofactions.
Exhibit12showsthisoptionintheimplant.
Copyright2018AccentureSecurity.
Allrightsreserved.
12Exhibit12:C2OptionsThefollowingstatuscodesaresupported:200:createandstartnewsocket202:enumerateprocessesandtakescreenshot203:performasetofactions(download,upload,execute)Exhibit13showsanexampleofpossibleactions:Exhibit13:HTTPStatusCode203ReturnOptionsTheactionsthattheoperatorcanperformareasfollows:WriteandexecutefilesCopyright2018AccentureSecurity.
Allrightsreserved.
13ExecutePowerShellscriptsExecuteaPowerShellscriptandexitSOCKSBOTcanthuswriteotherPowerShellscriptstothe%TEMP%folderandexecutethesehiddenfromtheuser.
Thisisachievedwiththefollowingcommand:%s\System32\WindowsPowerShell\v1.
0\powershell.
exe-ExecutionPolicyBypass-NoLogo-NonInteractive-NoProfile-WindowStyleHidden-File"%s"ThisallowstheattackertouploadotherobfuscatedPowerShellscriptsonthemachineand,assuch,makesSOCKSBOTapowerfulandpersistentbackdoor.
Altogether,theSOCKSBOTsamplesobservedandanalyzedinthisreportareasfollows:90f35fd205556a04d13216c33cb0dbe32a4d16ddad27c6eb60e197b6b07c2df014f71d5cb8f15f0a9943b5d709a85b7392dfd0534b080234f9536371be63e37a039d9e47e4474bee24785f8ec530769555a57741f49d6c887992353bc47846bcOnlythreedifferentC2servershavebeenobserved:5.
8.
88[.
]6446.
166.
163[.
]2435.
135.
73[.
]113INFECTIONCHAINVARIATIONSWhilethedescribedinfectionchainaboveisthemostcommoninfectionchainobserved,iDefenseanalystshavealsoobservedanumberofdifferentvariationsinrelatedcampaigns:1.
SOCKSBOTDropper2.
dog.
jsObfuscation3.
RandomPowerShellScriptNames4.
ReflectiveloadingPowerShellScriptObfuscationVARIATION1:SOCKSBOTDROPPERAsidefromthePowerShellreflectiveloader,iDefenseanalystshavealsoidentifiedadropperexecutablebinarywiththefollowingpropertiesthatwasusedtoreflectivelyloadSOCKSBOTintoachosenprocess(usuallysvchost.
exe):Filename:MD5:14f71d5cb8f15f0a9943b5d709a85b73FileSize:23.
6KB(24200bytes)CompiledTimeStamp:2017-02-0113:40:14Copyright2018AccentureSecurity.
Allrightsreserved.
14Signer:MagnumTravelClub(Serial:1F8A3E60EEC1E3AA63B39BDD26E110FB)Notethatthebinarywassignedwithacode-signingcertificatepurportedlyfromanorganizationcalledMagnumTravelClub.
ThisdropperwillcreateacopyofitselfinC:\Programdata\Logsasahiddensystemfileandwillthendeletetheoriginalfile.
Anothercopywillbecreatedin%appdata%\Microsoft\Windows\StartMenu\Programs\Startupwiththesamepropertiestoensurepersistence.
Finally,thedropperwillstartanewsvchost.
exeprocessinasuspendedstateandconsequentlyreflectivelyload(andinject)theSOCKSBOTimplantintotheprocess.
AnadditionalWindowsservicemaybecreatedforpersistenceaswell,whichisdonebyfirstenumeratingexistinglegitimateservicesandcreatinganewservicespoofingoneoftheserviceswithanalmostidenticalname.
Inthiscase,anewservicenamedXindowsErrorReportingServicewascreated(seeExhibit14).
Exhibit14:ServiceCreationWhilethisdropperdoesindeedloadtheSOCKSBOTimplant,allotheriterationsorcampaignshaveusedscripts,inparticularJavaScriptandPowerShell,toreflectivelyloadtheSOCKSBOTpayload.
VARIATION2:DOG.
JSOBFUSCATIONWhilemostdog.
jssamplesobservedwereobfuscatedasreportedintheinfectionchainsection,therearealsoversionsthatwerenotobfuscatedatallorwereobfuscatedusingadifferentobfuscationtechniquesuchasdifferentcharacterencoding(Exhibit15):Copyright2018AccentureSecurity.
Allrightsreserved.
15Exhibit15:ADifferentObfuscationTechniqueUsedindog.
jsOnceexecuted,thissample(MD5:b01cf8f375bc0aff2cfe3dc1b4c1823c)willdeobfuscateandgenerateanewfilecalled~~1.
tmpin%appdata%\Futures.
Thescriptisdeletedafterexecution.
VARIATION3:RANDOMPOWERSHELLSCRIPTNAMESCertainvariantsofdog.
jsalsohaveanewfunctiontorandomlygeneratefilenamesforthesecond-andthird-stagePowerShellscripts:functionmakerndps1(){vartext="";varpossible="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789";for(vari=0;i<5;i++)text+=possible.
charAt(Math.
floor(Math.
random()*possible.
length));returntext+'.
ps1';}4.
REFLECTIVELOADINGPOWERSHELLSCRIPTOBFUSCATIONAsidefromchangestothedog.
jsobfuscation,iDefenseanalystshavealsofoundadifferentobfuscationtechniqueusedtoobscurethecodeinthereflectiveloadingscript(seeExhibit16):Copyright2018AccentureSecurity.
Allrightsreserved.
16Exhibit16:DifferentObfuscationTechniqueUsedintheReflectiveLoadingPowerShellScriptThesampleconcernedhastheMD5signaturec38b06f871d2268972fa01725b59d7ed.
Notealsothattheexecutioncommandusedforpersistenceisagainencoded(seeExhibit17):Exhibit17:ObfuscatedExecutionCommandinCheckforupdateServiceUsedforPersistenceATTRIBUTIONBasedonthepreferencetospooffinancialinstitutionsinCIScountries,thenetworkinfrastructureusedandtheobservedtargeting,iDefenseassesseswithmoderateconfidencethatthereportedcampaignisunlikelytobeassociatedwithCANDLEFISH.
Furthermore,iDefenseanalystshaveidentifiedanumberofinterestingandnoteworthyoverlapswithFIN7:IdenticalWHOISinformationusedindomainsassociatedwiththeGoldfincampaignandFIN7,aswellasnetworkhostingoverlapShareduseofaPowerShellobfuscationtechniqueCopyright2018AccentureSecurity.
Allrightsreserved.
17OVERLAP1:IDENTICALWHOISINFORMATIONANDNETWORKHOSTINGOVERLAPResearchshowsthatthedomainsprivat-bankau[.
]com,halyk-bank[.
]com,andtejara-bank[.
]comallhavetheorganizationnameGoldfinLLC,anear-identicalregistrantaddress(seebelow),anda@rambler.
rue-mailaddressusedastheregistrante-mailaddress.
RegistrantOrganization:GoldfinLLCRegistrantStreet:ulArbat5RegistrantCity:MoscowRegistrantState/Province:MoscowRegistrantPostalCode:115343RegistrantCountry:RUThispatternoverlapswithtwootherdomains-despanabrandfood[.
]comandsilverdiners[.
]com(seeExhibit18)-thatiDefensecurrentassesseswithlowconfidencearelikelyassociatedwithFIN7duetothefollowing:1.
SpoofingrestaurantchainsDespaaBrandFoods(legitimatedomaindespanabrandfoods.
com)andSilverDiner(legitimatedomainsilverdiners.
com),aknowntechniqueassociatedwithFIN7.
Thewebsitedespanabrandfood[.
]comremainsindexedbyGoogle(seeExhibit19)2.
PreviouslyresolvedtotheIPaddress192.
99.
14[.
]211,whichwasreportedbyTrustwaveandtr1dxasassociatedwithFIN7towardslate2016andearly2017.
Inaddition,likemanydomainsassociatedwithFIN7aswellastheCarbanakgroup,manyofthedomainsusedintheGoldfincampaignwerealsoparkedat31.
41.
41[.
]41whichisassociatedwithCISHosting.
However,iDefenseanalystsareawarebothhostsarelikelytobeshared/parkinghostshencetheassociationwithFIN7basedonthisoverlapisoflowconfidence.
Exhibit18:WHOISInformationSimilaritiesbetweenDomainsUsedintheGoldfinCampaignandThoseAssociatedwithFIN7Copyright2018AccentureSecurity.
Allrightsreserved.
18Exhibit19:Spoofingdomaindespanabrandfood[.
]comremainsindexedbyGoogleatthetimeofwriting,showingtheattacker'sintentiontoplagiarisethelegitimatewebsitedespanabrandfoods[.
]comExhibit20illustratestheoverlappinginfrastructurebetweentheGoldfincampaignandinfrastructureassociatedwithFIN7:Exhibit20:MaltegoGraphShowingtheOverlappingInfrastructurebetweenGoldfinCampaignandFIN7Copyright2018AccentureSecurity.
Allrightsreserved.
19OVERLAP2:SHAREDUSEOFAPOWERSHELLOBFUSCATIONTECHNIQUEAsmentionedintheinfectionchainanalysis,thecodeembeddedwithinthethird-stagePowerShellscriptcheckupdate.
ps1isobfuscatedusingatechniquesimilartothatofPowerSploit.
However,thetechniqueusedappearstobeanichevariantastheembeddedpayloadisfurthersplitintochunksanddynamicallyaddedtoanarrayvariablenamed$OArr.
Interestingly,iDefenseanalystshavepreviouslyobservedthisobfuscationusedinaPowerShellcomponent(MD5:87327b4045b9d004697aec7e7a4b9ba8)thatwasdroppedbyaHALFBAKEDsample(MD5:31fcf8a4ec7a4c693eda9336321cf401)backinAugust2017.
HALFBAKEDisamalwarefamilyassociatedwithFIN7.
Exhibit21:SimilarPowerShellObfuscationTechniqueUsedbetweentheGoldfinCampaignandFIN7WhiletheaboveoverlappingfeaturesarenotstrongenoughtobeusedtoconcludethattheGoldfincampaignisassociatedwithFIN7,iDefenseanalystsbelievetheyaresignificantandnoteworthyandmaywelladdtonewevidencethatmaycometolightinthefutureasresearchcontinues.
Theyalsohighlightthecomplexhiddenrelationshipsthatexistbehind-the-scenesinorganizedcybercrime.
MITIGATIONToeffectivelydefendagainstthethreatsdescribedinthisreport,iDefenserecommendsblockingthefollowingaccessURIsandIPaddress:blopsadmvdrl[.
]combipovnerlvd[.
]comkiprovolswe[.
]comkiprovol[.
]comvoievnenibrinw[.
]combnrnboerxce[.
]comtejara-bank[.
]comprivat-bankau[.
]comCopyright2018AccentureSecurity.
Allrightsreserved.
20halyk-bank[.
]comwedogreatpurchases[.
]comprivatbank-ua[.
]commoneyma-r[.
]comfisrteditionps[.
]comessentialetimes[.
]comdewifal[.
]commicro-earth[.
]com5.
8.
88[.
]6446.
166.
163[.
]2435.
135.
73[.
]113Itwillalsobeusefulforincidentresponseandthreat-huntingpurposestoverifytheexistenceofanyofthefollowingartefacts:ArandomlynamedfileinC:\Programdata\Logsor%appdata%\Microsoft\Windows\StartMenu\Programs\StartupRandomlynamedPowerShellorJavaScriptfilesin%temp%Afilenameddog.
zipanddog.
jsAfilenamed~~1.
tmpin%appdata%\FuturesAservicenamewithsignificantspellingerrorsAservicenamedCheckforupdatesAPowerShellscriptnamedcheckupdate.
ps1indefaultPowerShellinstallationdirectoryAsvchost.
exeprocessthatdoesnothavewininit.
exeasparentprocessItwillalsobeusefultoverifytheexistenceofanyofthefollowinghashesonthehost:de394e9d294d2c325298eb54826ba11609d43765c2259a8df868a5fa6206ae2b9a273653364dfb143ff196d826d2bac46da6025fc7956f644b0b161781071cec211fbf34749df5e717e8b11fecb3f648dae11ed0013d58000f10919b8cba8023949b7e0f9d309e8a7ab32fa4664a7906bdaa27c6284ff95c01178db7a96121a450598c4dc7c299d0cbd92c128a56944e21a09cf81f3584a741c7167f622d6c50b3fb88a5aa791aea141bf3b4cf04535554e7f3a1a1a8857e35a45f4eb2a3317d29573b1fa60bce8e04dd2a4d554a74477b528c9d8150e4a4ab27b90a4e3337637f1aa2b2d539aa7d3dbb067417457309b10c3d00a7ceff0b7050f450968c8f6929573b1fa60bce8e04dd2a4d554a7447c38b06f871d2268972fa01725b59d7edCopyright2018AccentureSecurity.
Allrightsreserved.
21CONTACTUSJoshuaRayjoshua.
a.
ray@accenture.
comHowardMarshallhoward.
marshall@accenture.
comRobertCoderrerobert.
c.
coderre@accenture.
comJaysonJeanjayson.
jean@accenture.
comEmilyCodyemily.
a.
cody@accenture.
comABOUTACCENTUREAccentureisaleadingglobalprofessionalservicescompany,providingabroadrangeofservicesandsolutionsinstrategy,consulting,digital,technologyandoperations.
Combiningunmatchedexperienceandspecializedskillsacrossmorethan40industriesandallbusinessfunctions—underpinnedbytheworld'slargestdeliverynetwork—Accentureworksattheintersectionofbusinessandtechnologytohelpclientsimprovetheirperformanceandcreatesustainablevaluefortheirstakeholders.
Withapproximately425,000peopleservingclientsinmorethan120countries,Accenturedrivesinnovationtoimprovethewaytheworldworksandlives.
Visitusatwww.
accenture.
comABOUTACCENTURESECURITYAccentureSecurityhelpsorganizationsbuildresiliencefromtheinsideout,sotheycanconfidentlyfocusoninnovationandgrowth.
Leveragingitsglobalnetworkofcybersecuritylabs,deepindustryunderstandingacrossclientvaluechainsandservicesthatspanthesecuritylifecycle,Accentureprotectsorganization'svaluableassets,end-to-end.
Withservicesthatincludestrategyandriskmanagement,cyberdefense,digitalidentity,applicationsecurityandmanagedsecurity,Accentureenablesbusinessesaroundtheworldtodefendagainstknownsophisticatedthreats,andtheunknown.
Followus@AccentureSecureonTwitterorvisittheAccentureSecurityblog.
LEGALNOTICE&DISCLAIMER:2018Accenture.
Allrightsreserved.
Accenture,theAccenturelogo,iDefenseandothertrademarks,servicemarks,anddesignsareregisteredorunregisteredtrademarksofAccentureanditssubsidiariesintheUnitedStatesandinforeigncountries.
Alltrademarksarepropertiesoftheirrespectiveowners.
Allmaterialsareintendedfortheoriginalrecipientonly.
ThereproductionanddistributionofthismaterialisforbiddenwithoutexpresswrittenpermissionfromiDefense.
Theopinions,statements,andassessmentsinthisreportaresolelythoseoftheindividualauthor(s)anddonotconstitutelegaladvice,nordotheynecessarilyreflecttheviewsofAccenture,itssubsidiaries,oraffiliates.
Giventheinherentnatureofthreatintelligence,thecontentcontainedinthisalertisbasedoninformationgatheredandunderstoodatthetimeofitscreation.
Itissubjecttochange.
ACCENTUREPROVIDESTHEINFORMATIONONAN"AS-IS"BASISWITHOUTREPRESENTATIONORWARRANTYANDACCEPTSNOLIABILITYFORANYACTIONORFAILURETOACTTAKENINRESPONSETOTHEINFORMATIONCONTAINEDORREFERENCEDINTHISALERT.
Allrightsreserved.
1GOLDFIN:APersistentCampaignTargetingCISCountrieswithSOCKSBOTJuly26,2018CYBERADVISORYCopyright2018AccentureSecurity.
Allrightsreserved.
2SUMMARYAnumberofsecurityvendorsreportedaseriesofcyber-attacksinvolvingtheuseofamalwarefamilycalledSOCKSBOTandclaimedtobeassociatedwithCANDLEFISH(a.
k.
a.
Patchwork,DroppingElephant).
However,asdisclosedinthisreport,researchbyiDefenseanalystsshowsthatSOCKSBOTwasinfactusedbyathreatgroupinan18-month-longcampaigndubbedGoldfin,spoofingfinancialinstitutionsintheCommonwealthofIndependentStates(CIS)countriessinceasearlyasFebruary2017toasrecentlyasMay2018.
Basedonthetactics,techniquesandprocedures(TTPs)observedinthiscampaign,iDefenseassesseswithmoderateconfidencethatthereportedcampaignisunlikelytobeassociatedwithCANDLEFISH.
Inaddition,iDefenseanalystshaveidentifiedinfrastructureoverlapandtheshareduseofaPowerShellobfuscationtechniquewithFIN7.
AlthoughtheseobservationsarenotenoughtoattributetheGoldfincampaigntoFIN7,iDefenseassessesthesetobeinterestingandnoteworthyobservationsthatfurtherhighlightsthecomplexrelationshipsthatexistbehind-the-sceneinorganizedcybercrime.
HOWTOUSETHISREPORTINTENDEDAUDIENCEiDefenseisprovidinginformationaboutthereportedcampaignstothegeneraliDefensecustomerbase,withthisreportbeingintendedforsecurityoperationscenter(SOC)analystsandengineers.
Managementandexecutiveleadershipmayalsowanttousethisinformation.
HOWTOUSETHISINTELLIGENCEiDefenseisprovidingthisinformationsothatcustomersareawareofthemodusoperandiofahighlyactivethreatgroupthatistargetingfinancialinstitutionsforfinancialgain.
SOCanalystsandengineerscanusethisIA'sdetailedinformationpertainingtotheworkingsofamalwarefamilyandindicatorsofcompromise(IoCs)tocontainormitigatethediscussedthreatthroughmonitoringorblocking.
SOCanalystscanusetheinformationprovidedintheAnalysisandMitigationsectionsofthisIAforhuntingactivitiesforsystemsthatmayhavealreadybeencompromised.
AnalystsandsecurityengineerscanusetheIoCsbyaddingthemtohuntinglistsonendpointdetectionandresponse(EDR)solutionsaswellasnetwork-andhost-basedblackliststodetectanddenymalwareimplantationandcommand-and-control(C2)communication.
IntelligenceanalystsmaywanttousetheinformationprovidedinthisIAtobetterinformtheirownanalyses.
TheprovidedinformationcanalsohelpinformongoingintelligenceCopyright2018AccentureSecurity.
Allrightsreserved.
3analysesandforensicinvestigations,particularlyforcompromisediscovery,damageassessment,andattribution.
Managementandexecutiveleadershipmayusethisinformationtoassesstherisksassociatedwiththethreatdescribedhereintomakeoperationalandpolicydecisionsaccordingly.
HOWTHISINTELLIGENCEHELPSADDRESSEXISTINGORPOTENTIALTHREATSKnowledgeofthegroup'stactics,techniques,andprocedures(TTPs)shouldhelptobetterinformdetectionandresponsetoattacksbythisthreatgroup.
CAMPAIGNANALYSISiDefenseanalystscameacrosstwospear-phishingcampaignsinOctober2017involvingtheuseofamalwarefamilypubliclyknownasSOCKSBOT.
OnecampaignspoofstheHalykBank(Exhibit1)andanotherspoofsthePrivatBank(Exhibit2):Exhibit1:Spear-PhishingEmailSpoofingHalykBankCopyright2018AccentureSecurity.
Allrightsreserved.
4Exhibit2:ContentofaSpear-PhishingE-mailSpoofingPrivatBankSharedonthePublicForumdoneckforum.
comAsExhibits1and2show,bothemailscontainanidenticalmessage,evendowntothelocationoftheembeddedhyperlinks.
TheonlydifferencesaretheembeddedURLsandthesignatureoftheemailinordertoreflectthefinancialinstitutiontheattackerswerespoofing.
Thisinformationsuggestssomesortofphishingkitwaslikelyusedtogeneratethephishingemails.
Anapproximatetranslationofthee-mailspoofingHalykBankisasfollows:Subject:Notificationofopeninganaccount(HalykBankofKazakhstan)Dearcustomer,anaccountwiththePeople'sBankofKazakhstanhasbeenopenedinyourname,youcanfinddetailedinformationintheattachedfile.
Ifyoudidnotreceiveanenvelopewithaloginandpassword,thenyouneedtoregistertoaccessthePersonalArea.
Incaseoflossoflogin/password,youcanregisteranewoneinthesection"Passwordrecovery".
Ifintheprocessofworkyouhaveanyquestionsorproblems,pleasecontacttheCustomerServiceDepartmentatthecontactslistedbelow.
Ourspecialistsarealwaysreadytohelpyou.
Theembeddedmalicioushyperlinksusedintherespectiveattacksareasfollows:hxxp://halyk-bank[.
]com/dog.
ziphxxp://privatbank-ua[.
]com/dog.
zipSubsequenttechnicalanalysisoftheinfectionchaininvolvedlediDefensetouncoveran18-monthlongcampaignofspoofingbanksinCIScountries,withthemostrecentcampaignobservedonMay28,2018spoofingtheIdeaBankCJSC:Copyright2018AccentureSecurity.
Allrightsreserved.
5Exhibit3:Spear-PhishingEmailSpoofingIdeaBankCJSCTheforummemberreportsthattwospear-phishingemailswerereceived:oneclaimingtobeanotificationaboutopeninganaccountandtheotherclaimingtobeanotificationofaloanbeingtakenout.
Thecontentofthelatteremailisapproximatelytranslatedbelow:Dearclient,inyourname,aloanwasissuedtoIdeaBank,formoredetails,seetheattachedfileinwhichthefullnameandphonenumberofyourpersonalloanexpertisindicated,theamountandconditionsforrepayingtheloan.
Anenvelopewithacreditagreementwassenttoyouraddress.
Incaseyoudidnotreceivetheenvelope,youshouldcontactyourpersonalexpert.
Incaseoflossofthecontract,youcanrestoreitatthenearestbranchofthebankorrequestaduplicatethroughyourpersonalexpert.
Foranyquestionsyouareinterestedin,youcancontactyourpersonalexpertortheCustomerServiceDepartmentatthecontactslistedbelow.
Ourspecialistsarealwaysreadytohelpyou.
Yoursfaithfully,IdeaBankCJSCPhoneforcallsfromabroad:+375(17)306-33-14Intheattacksobserved,allinvolvedaphishingemailwithtwoembeddedURLsdirectingtheusertodownloadafilenameddog.
zip.
Basedonthecontentofthee-mailsandthedomainnames,thefollowingbankswerespoofedinthiscampaign:HalykBank(Kazakhstan)PrivatBank(Ukraine)IdeaBank(Belarus)Copyright2018AccentureSecurity.
Allrightsreserved.
6TejaraBank(Iran)Itisalsonoteworthythatinbothphishingkits,therearealwaystwohyperlinkslinkingtothesamemaliciousfile:oneinthebodyofthemessageandoneattheendofthee-mailinalinkcalledДоговор(whichtranslatestoContract).
Thenextsectiondetailstheinfectionchainthatfollowstheinitialdownload.
INFECTIONCHAINANALYSISThegeneralinfectionchainobservedinthiscampaignisasshowninExhibit4:Exhibit4:TheInfectionChainUsedintheSOCKSBOTCampaignSTAGE1-JAVASCRIPTDROPPERBothlinksdeliveredaZIParchivefilenameddog.
zip:hxxp://halyk-bank[.
]com/dog.
zip-211fbf34749df5e717e8b11fecb3f648hxxp://privatbank-ua[.
]com/dog.
zip-b3fb88a5aa791aea141bf3b4cf045355BothcontainaJavaScriptfilenameddog.
jswiththeMD5signatures9a273653364dfb143ff196d826d2bac4and21a09cf81f3584a741c7167f622d6c50,respectively.
TheJavaScriptfilecontainsheavilyobfuscatedcodeasExhibit5shows.
Themaliciouscodeisinfacthiddenascommentsandisdynamicallydeobfuscatedoncethescripthasbeenexecuted.
Copyright2018AccentureSecurity.
Allrightsreserved.
7Exhibit5:ObfuscatedCodeindog.
jsOncedeobfuscated(seeExhibit6),itisclearthatthecodeisdesignedtodotwothings:1.
Tolookforarunninganti-virusprocesses,suchasavp.
exe(KasperskyAntivirus).
Notethatsomevariantsofthemalwarealsosearchforekrn.
exe(ESET),cis.
exe(Comodo)andavgnt.
exe(Avira).
2.
TodropandexecuteaPowerShellscriptnamedsetup.
ps1.
ThisscriptisgeneratedbasedonBase64encodeddatastoredinvariablesnameddllDataandcode.
3.
Deletesetup.
ps1Exhibit6:DeobfuscatedCodeindog.
jsCopyright2018AccentureSecurity.
Allrightsreserved.
8STAGE2-POWERSHELLDROPPERWITHEMPIREThePowerShellscriptsetup.
ps1usedineachattackhastherespectiveMD5signatures521c81c62836a233a6e771bc3491300fand00c38b787eac602ffaed0b9372f2c443.
Thescriptisdesignedforthefollowing(seeExhibit7):1.
CreateaPowerShellscriptnamedcheckupdate.
ps1inC:\Users\Public\Downloads\(Thispathishardcodedinthemalware).
ThecontentofthisscriptisstoredinavariablenameddataandisBased64encoded2.
Createacmdletthatwould:a.
movethescriptcheckupdate.
ps1tothehomedirectoryforthecurrentPowerShellinstallb.
establishpersistencebycreatingaWindowsservicenamedCheckforupdates,setto"delay-auto"startandexecutecheckupdate.
ps13.
UseamodifiedversionofthefunctionInvoke-EventVwrBypassfromtheEmpirePost-exploitationframeworktobypassUACandexecutetheabovecmdletExhibit7:DeobfuscatedCodeinsetup.
ps1Copyright2018AccentureSecurity.
Allrightsreserved.
9STAGE3-POWERSHELLREFLECTIVELOADERSimilarly,checkupdate.
ps1usedineachattackhastherespectiveMD5signatures54e7f3a1a1a8857e35a45f4eb2a3317dand29573b1fa60bce8e04dd2a4d554a7447.
Unsurprisingly,thisscriptalsocontainsobfuscatedcode.
Themaliciouspayloadiscompressed,Base64encoded,andembeddedwithinthescript,whichissimilartoatechniqueusedinPowerSploit.
However,theobservedtechniqueappearstobeavariantofPowerSploitastheencodedpayloadisfurthersplitintoanumberofchunksthataredynamicallyloadedintoanarrayvariablenamed$OArrasshowninExhibit8:Exhibit8:ObfuscatedCodeincheckupdate.
ps1ThecodeisinfactaPowerShellreflectiveloaderscriptwithadynamic-linklibrary(DLL)binaryembeddedasBase64-encodeddata(Exhibit9).
Copyright2018AccentureSecurity.
Allrightsreserved.
10Exhibit9:DeobfuscatedCodeincheckupdate.
ps1STAGE4-SOCKSBOTThespecificSOCKSBOTsampleanalyzedinthisreporthasthefollowingproperties:Filename:socksbot.
dllMD5:90f35fd205556a04d13216c33cb0dbe3FileSize:17.
0KB(17408bytes)CompiledTimeStamp:2017-10-2717:46:05Copyright2018AccentureSecurity.
Allrightsreserved.
11Asmentionedinthelastsection,theSOCKSBOTimplantistypicallydeliveredasaBase64-encodedstringreflectivelyloaded(viatheReflectiveLoader@@YGKPAX@Zexportedfunction)inanewlystartedsvchost.
exeprocess.
Assuch,theimplantexistsonlyinmemoryandnevertouchesthedisk.
Theimplantwillfirstverifyifanyofthemutexesinthefollowingformatarepresentinordertonotruntwice:Global\%snpsGlobal\%sstpExhibit10showsanexampleofacreatedmutex.
Exhibit10:MutexCreationa321c0d8979a05bdnpsTheSOCKSBOTimplanthasthefollowingcapabilities:Enumerateprocesses(processlist)TakescreenshotsDownload,upload,write,andexecutefilesCreateandinjectintonewprocessesCommunicatetoC2viasocketsThisimplantwillcommunicatewiththedesignatedC2serverbyfirstcreatingabufferandwill,onfirstexecution,communicatetotheC2serverthatithassuccessfullyinfectedatargetbyusinga.
phpURIthatispseudo-randomlygenerated.
SOCKSBOTusestheObtainUserAgentStringAPItodeterminethedefaultuser-agentofthemachine.
AnexampleofarequesttotheC246.
166.
163[.
]243isshowninExhibit11.
Exhibit11:TraffictotheC2ServerTheC2serverortheoperatoroftheSOCKSBOTimplantcanthenrespondwithaspecificHTTPstatuscodetoperformasetofactions.
Exhibit12showsthisoptionintheimplant.
Copyright2018AccentureSecurity.
Allrightsreserved.
12Exhibit12:C2OptionsThefollowingstatuscodesaresupported:200:createandstartnewsocket202:enumerateprocessesandtakescreenshot203:performasetofactions(download,upload,execute)Exhibit13showsanexampleofpossibleactions:Exhibit13:HTTPStatusCode203ReturnOptionsTheactionsthattheoperatorcanperformareasfollows:WriteandexecutefilesCopyright2018AccentureSecurity.
Allrightsreserved.
13ExecutePowerShellscriptsExecuteaPowerShellscriptandexitSOCKSBOTcanthuswriteotherPowerShellscriptstothe%TEMP%folderandexecutethesehiddenfromtheuser.
Thisisachievedwiththefollowingcommand:%s\System32\WindowsPowerShell\v1.
0\powershell.
exe-ExecutionPolicyBypass-NoLogo-NonInteractive-NoProfile-WindowStyleHidden-File"%s"ThisallowstheattackertouploadotherobfuscatedPowerShellscriptsonthemachineand,assuch,makesSOCKSBOTapowerfulandpersistentbackdoor.
Altogether,theSOCKSBOTsamplesobservedandanalyzedinthisreportareasfollows:90f35fd205556a04d13216c33cb0dbe32a4d16ddad27c6eb60e197b6b07c2df014f71d5cb8f15f0a9943b5d709a85b7392dfd0534b080234f9536371be63e37a039d9e47e4474bee24785f8ec530769555a57741f49d6c887992353bc47846bcOnlythreedifferentC2servershavebeenobserved:5.
8.
88[.
]6446.
166.
163[.
]2435.
135.
73[.
]113INFECTIONCHAINVARIATIONSWhilethedescribedinfectionchainaboveisthemostcommoninfectionchainobserved,iDefenseanalystshavealsoobservedanumberofdifferentvariationsinrelatedcampaigns:1.
SOCKSBOTDropper2.
dog.
jsObfuscation3.
RandomPowerShellScriptNames4.
ReflectiveloadingPowerShellScriptObfuscationVARIATION1:SOCKSBOTDROPPERAsidefromthePowerShellreflectiveloader,iDefenseanalystshavealsoidentifiedadropperexecutablebinarywiththefollowingpropertiesthatwasusedtoreflectivelyloadSOCKSBOTintoachosenprocess(usuallysvchost.
exe):Filename:MD5:14f71d5cb8f15f0a9943b5d709a85b73FileSize:23.
6KB(24200bytes)CompiledTimeStamp:2017-02-0113:40:14Copyright2018AccentureSecurity.
Allrightsreserved.
14Signer:MagnumTravelClub(Serial:1F8A3E60EEC1E3AA63B39BDD26E110FB)Notethatthebinarywassignedwithacode-signingcertificatepurportedlyfromanorganizationcalledMagnumTravelClub.
ThisdropperwillcreateacopyofitselfinC:\Programdata\Logsasahiddensystemfileandwillthendeletetheoriginalfile.
Anothercopywillbecreatedin%appdata%\Microsoft\Windows\StartMenu\Programs\Startupwiththesamepropertiestoensurepersistence.
Finally,thedropperwillstartanewsvchost.
exeprocessinasuspendedstateandconsequentlyreflectivelyload(andinject)theSOCKSBOTimplantintotheprocess.
AnadditionalWindowsservicemaybecreatedforpersistenceaswell,whichisdonebyfirstenumeratingexistinglegitimateservicesandcreatinganewservicespoofingoneoftheserviceswithanalmostidenticalname.
Inthiscase,anewservicenamedXindowsErrorReportingServicewascreated(seeExhibit14).
Exhibit14:ServiceCreationWhilethisdropperdoesindeedloadtheSOCKSBOTimplant,allotheriterationsorcampaignshaveusedscripts,inparticularJavaScriptandPowerShell,toreflectivelyloadtheSOCKSBOTpayload.
VARIATION2:DOG.
JSOBFUSCATIONWhilemostdog.
jssamplesobservedwereobfuscatedasreportedintheinfectionchainsection,therearealsoversionsthatwerenotobfuscatedatallorwereobfuscatedusingadifferentobfuscationtechniquesuchasdifferentcharacterencoding(Exhibit15):Copyright2018AccentureSecurity.
Allrightsreserved.
15Exhibit15:ADifferentObfuscationTechniqueUsedindog.
jsOnceexecuted,thissample(MD5:b01cf8f375bc0aff2cfe3dc1b4c1823c)willdeobfuscateandgenerateanewfilecalled~~1.
tmpin%appdata%\Futures.
Thescriptisdeletedafterexecution.
VARIATION3:RANDOMPOWERSHELLSCRIPTNAMESCertainvariantsofdog.
jsalsohaveanewfunctiontorandomlygeneratefilenamesforthesecond-andthird-stagePowerShellscripts:functionmakerndps1(){vartext="";varpossible="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789";for(vari=0;i<5;i++)text+=possible.
charAt(Math.
floor(Math.
random()*possible.
length));returntext+'.
ps1';}4.
REFLECTIVELOADINGPOWERSHELLSCRIPTOBFUSCATIONAsidefromchangestothedog.
jsobfuscation,iDefenseanalystshavealsofoundadifferentobfuscationtechniqueusedtoobscurethecodeinthereflectiveloadingscript(seeExhibit16):Copyright2018AccentureSecurity.
Allrightsreserved.
16Exhibit16:DifferentObfuscationTechniqueUsedintheReflectiveLoadingPowerShellScriptThesampleconcernedhastheMD5signaturec38b06f871d2268972fa01725b59d7ed.
Notealsothattheexecutioncommandusedforpersistenceisagainencoded(seeExhibit17):Exhibit17:ObfuscatedExecutionCommandinCheckforupdateServiceUsedforPersistenceATTRIBUTIONBasedonthepreferencetospooffinancialinstitutionsinCIScountries,thenetworkinfrastructureusedandtheobservedtargeting,iDefenseassesseswithmoderateconfidencethatthereportedcampaignisunlikelytobeassociatedwithCANDLEFISH.
Furthermore,iDefenseanalystshaveidentifiedanumberofinterestingandnoteworthyoverlapswithFIN7:IdenticalWHOISinformationusedindomainsassociatedwiththeGoldfincampaignandFIN7,aswellasnetworkhostingoverlapShareduseofaPowerShellobfuscationtechniqueCopyright2018AccentureSecurity.
Allrightsreserved.
17OVERLAP1:IDENTICALWHOISINFORMATIONANDNETWORKHOSTINGOVERLAPResearchshowsthatthedomainsprivat-bankau[.
]com,halyk-bank[.
]com,andtejara-bank[.
]comallhavetheorganizationnameGoldfinLLC,anear-identicalregistrantaddress(seebelow),anda@rambler.
rue-mailaddressusedastheregistrante-mailaddress.
RegistrantOrganization:GoldfinLLCRegistrantStreet:ulArbat5RegistrantCity:MoscowRegistrantState/Province:MoscowRegistrantPostalCode:115343RegistrantCountry:RUThispatternoverlapswithtwootherdomains-despanabrandfood[.
]comandsilverdiners[.
]com(seeExhibit18)-thatiDefensecurrentassesseswithlowconfidencearelikelyassociatedwithFIN7duetothefollowing:1.
SpoofingrestaurantchainsDespaaBrandFoods(legitimatedomaindespanabrandfoods.
com)andSilverDiner(legitimatedomainsilverdiners.
com),aknowntechniqueassociatedwithFIN7.
Thewebsitedespanabrandfood[.
]comremainsindexedbyGoogle(seeExhibit19)2.
PreviouslyresolvedtotheIPaddress192.
99.
14[.
]211,whichwasreportedbyTrustwaveandtr1dxasassociatedwithFIN7towardslate2016andearly2017.
Inaddition,likemanydomainsassociatedwithFIN7aswellastheCarbanakgroup,manyofthedomainsusedintheGoldfincampaignwerealsoparkedat31.
41.
41[.
]41whichisassociatedwithCISHosting.
However,iDefenseanalystsareawarebothhostsarelikelytobeshared/parkinghostshencetheassociationwithFIN7basedonthisoverlapisoflowconfidence.
Exhibit18:WHOISInformationSimilaritiesbetweenDomainsUsedintheGoldfinCampaignandThoseAssociatedwithFIN7Copyright2018AccentureSecurity.
Allrightsreserved.
18Exhibit19:Spoofingdomaindespanabrandfood[.
]comremainsindexedbyGoogleatthetimeofwriting,showingtheattacker'sintentiontoplagiarisethelegitimatewebsitedespanabrandfoods[.
]comExhibit20illustratestheoverlappinginfrastructurebetweentheGoldfincampaignandinfrastructureassociatedwithFIN7:Exhibit20:MaltegoGraphShowingtheOverlappingInfrastructurebetweenGoldfinCampaignandFIN7Copyright2018AccentureSecurity.
Allrightsreserved.
19OVERLAP2:SHAREDUSEOFAPOWERSHELLOBFUSCATIONTECHNIQUEAsmentionedintheinfectionchainanalysis,thecodeembeddedwithinthethird-stagePowerShellscriptcheckupdate.
ps1isobfuscatedusingatechniquesimilartothatofPowerSploit.
However,thetechniqueusedappearstobeanichevariantastheembeddedpayloadisfurthersplitintochunksanddynamicallyaddedtoanarrayvariablenamed$OArr.
Interestingly,iDefenseanalystshavepreviouslyobservedthisobfuscationusedinaPowerShellcomponent(MD5:87327b4045b9d004697aec7e7a4b9ba8)thatwasdroppedbyaHALFBAKEDsample(MD5:31fcf8a4ec7a4c693eda9336321cf401)backinAugust2017.
HALFBAKEDisamalwarefamilyassociatedwithFIN7.
Exhibit21:SimilarPowerShellObfuscationTechniqueUsedbetweentheGoldfinCampaignandFIN7WhiletheaboveoverlappingfeaturesarenotstrongenoughtobeusedtoconcludethattheGoldfincampaignisassociatedwithFIN7,iDefenseanalystsbelievetheyaresignificantandnoteworthyandmaywelladdtonewevidencethatmaycometolightinthefutureasresearchcontinues.
Theyalsohighlightthecomplexhiddenrelationshipsthatexistbehind-the-scenesinorganizedcybercrime.
MITIGATIONToeffectivelydefendagainstthethreatsdescribedinthisreport,iDefenserecommendsblockingthefollowingaccessURIsandIPaddress:blopsadmvdrl[.
]combipovnerlvd[.
]comkiprovolswe[.
]comkiprovol[.
]comvoievnenibrinw[.
]combnrnboerxce[.
]comtejara-bank[.
]comprivat-bankau[.
]comCopyright2018AccentureSecurity.
Allrightsreserved.
20halyk-bank[.
]comwedogreatpurchases[.
]comprivatbank-ua[.
]commoneyma-r[.
]comfisrteditionps[.
]comessentialetimes[.
]comdewifal[.
]commicro-earth[.
]com5.
8.
88[.
]6446.
166.
163[.
]2435.
135.
73[.
]113Itwillalsobeusefulforincidentresponseandthreat-huntingpurposestoverifytheexistenceofanyofthefollowingartefacts:ArandomlynamedfileinC:\Programdata\Logsor%appdata%\Microsoft\Windows\StartMenu\Programs\StartupRandomlynamedPowerShellorJavaScriptfilesin%temp%Afilenameddog.
zipanddog.
jsAfilenamed~~1.
tmpin%appdata%\FuturesAservicenamewithsignificantspellingerrorsAservicenamedCheckforupdatesAPowerShellscriptnamedcheckupdate.
ps1indefaultPowerShellinstallationdirectoryAsvchost.
exeprocessthatdoesnothavewininit.
exeasparentprocessItwillalsobeusefultoverifytheexistenceofanyofthefollowinghashesonthehost:de394e9d294d2c325298eb54826ba11609d43765c2259a8df868a5fa6206ae2b9a273653364dfb143ff196d826d2bac46da6025fc7956f644b0b161781071cec211fbf34749df5e717e8b11fecb3f648dae11ed0013d58000f10919b8cba8023949b7e0f9d309e8a7ab32fa4664a7906bdaa27c6284ff95c01178db7a96121a450598c4dc7c299d0cbd92c128a56944e21a09cf81f3584a741c7167f622d6c50b3fb88a5aa791aea141bf3b4cf04535554e7f3a1a1a8857e35a45f4eb2a3317d29573b1fa60bce8e04dd2a4d554a74477b528c9d8150e4a4ab27b90a4e3337637f1aa2b2d539aa7d3dbb067417457309b10c3d00a7ceff0b7050f450968c8f6929573b1fa60bce8e04dd2a4d554a7447c38b06f871d2268972fa01725b59d7edCopyright2018AccentureSecurity.
Allrightsreserved.
21CONTACTUSJoshuaRayjoshua.
a.
ray@accenture.
comHowardMarshallhoward.
marshall@accenture.
comRobertCoderrerobert.
c.
coderre@accenture.
comJaysonJeanjayson.
jean@accenture.
comEmilyCodyemily.
a.
cody@accenture.
comABOUTACCENTUREAccentureisaleadingglobalprofessionalservicescompany,providingabroadrangeofservicesandsolutionsinstrategy,consulting,digital,technologyandoperations.
Combiningunmatchedexperienceandspecializedskillsacrossmorethan40industriesandallbusinessfunctions—underpinnedbytheworld'slargestdeliverynetwork—Accentureworksattheintersectionofbusinessandtechnologytohelpclientsimprovetheirperformanceandcreatesustainablevaluefortheirstakeholders.
Withapproximately425,000peopleservingclientsinmorethan120countries,Accenturedrivesinnovationtoimprovethewaytheworldworksandlives.
Visitusatwww.
accenture.
comABOUTACCENTURESECURITYAccentureSecurityhelpsorganizationsbuildresiliencefromtheinsideout,sotheycanconfidentlyfocusoninnovationandgrowth.
Leveragingitsglobalnetworkofcybersecuritylabs,deepindustryunderstandingacrossclientvaluechainsandservicesthatspanthesecuritylifecycle,Accentureprotectsorganization'svaluableassets,end-to-end.
Withservicesthatincludestrategyandriskmanagement,cyberdefense,digitalidentity,applicationsecurityandmanagedsecurity,Accentureenablesbusinessesaroundtheworldtodefendagainstknownsophisticatedthreats,andtheunknown.
Followus@AccentureSecureonTwitterorvisittheAccentureSecurityblog.
LEGALNOTICE&DISCLAIMER:2018Accenture.
Allrightsreserved.
Accenture,theAccenturelogo,iDefenseandothertrademarks,servicemarks,anddesignsareregisteredorunregisteredtrademarksofAccentureanditssubsidiariesintheUnitedStatesandinforeigncountries.
Alltrademarksarepropertiesoftheirrespectiveowners.
Allmaterialsareintendedfortheoriginalrecipientonly.
ThereproductionanddistributionofthismaterialisforbiddenwithoutexpresswrittenpermissionfromiDefense.
Theopinions,statements,andassessmentsinthisreportaresolelythoseoftheindividualauthor(s)anddonotconstitutelegaladvice,nordotheynecessarilyreflecttheviewsofAccenture,itssubsidiaries,oraffiliates.
Giventheinherentnatureofthreatintelligence,thecontentcontainedinthisalertisbasedoninformationgatheredandunderstoodatthetimeofitscreation.
Itissubjecttochange.
ACCENTUREPROVIDESTHEINFORMATIONONAN"AS-IS"BASISWITHOUTREPRESENTATIONORWARRANTYANDACCEPTSNOLIABILITYFORANYACTIONORFAILURETOACTTAKENINRESPONSETOTHEINFORMATIONCONTAINEDORREFERENCEDINTHISALERT.
- Tejara166dd.com相关文档
- BioMed166dd.com
- fs166dd.com
- 填土166dd.com
- KENYA166dd.com
- 集合166dd.com
- Association166dd.com
2021年国内/国外便宜VPS主机/云服务器商家推荐整理
2021年各大云服务商竞争尤为激烈,因为云服务商家的竞争我们可以选择更加便宜的VPS或云服务器,这样成本更低,选择空间更大。但是,如果我们是建站用途或者是稳定项目的,不要太过于追求便宜VPS或便宜云服务器,更需要追求稳定和服务。不同的商家有不同的特点,而且任何商家和线路不可能一直稳定,我们需要做的就是定期观察和数据定期备份。下面,请跟云服务器网(yuntue.com)小编来看一下2021年国内/国...

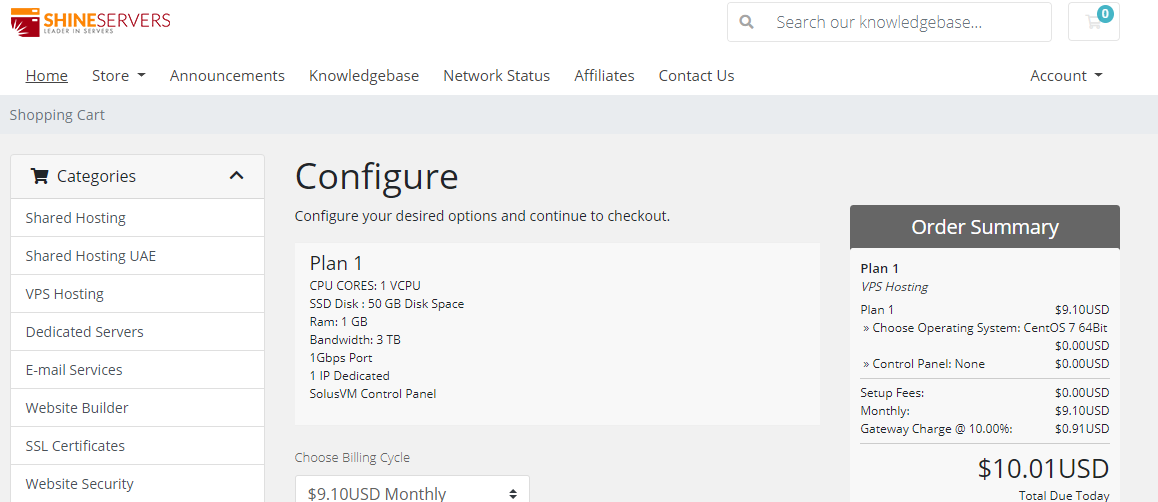
ShineServers(5美元/月)荷兰VPS、阿联酋VPS首月五折/1核1G/50GB硬盘/3TB流量/1Gbps带宽
优惠码50SSDOFF 首月5折50WHTSSD 年付5折15OFF 85折优惠,可循环使用荷兰VPSCPU内存SSD带宽IPv4价格购买1核1G50G1Gbps/3TB1个$ 9.10/月链接2核2G80G1Gbps/5TB1个$ 12.70/月链接2核3G100G1Gbps/7TB1个$ 16.30/月链接3核4G150G1Gbps/10TB1个$ 18.10/月链接阿联酋VPSCPU内存SS...
WebHorizon($10.56/年)256MB/5G SSD/200GB/日本VPS
WebHorizon是一家去年成立的国外VPS主机商,印度注册,提供虚拟主机和VPS产品,其中VPS包括OpenVZ和KVM架构,有独立IP也有共享IP,数据中心包括美国、波兰、日本、新加坡等(共享IP主机可选机房更多)。目前商家对日本VPS提供一个8折优惠码,优惠后最低款OpenVZ套餐年付10.56美元起。OpenVZCPU:1core内存:256MB硬盘:5G NVMe流量:200GB/1G...
166dd.com为你推荐
-
网易网盘关闭入口怎么打开网易网盘??有机zz怎么看不了呢有机zz怎么进不去了嘉兴商标注册我在濮院想注册一个羊毛衫商标?该怎么做?同ip网站查询怎样查询一个ip绑了多少域名xyq.163.cbg.com梦幻西游藏宝阁丑福晋八阿哥胤禩有几个福晋 都叫啥名儿呀百度关键词工具常见百度关键词挖掘方法分别是什么请列举?www.niuav.com给我个看电影的网站www.javmoo.comjavimdb怎么看se95se.comwww.sea8.com这个网站是用什么做的 需要多少钱