exchangemandriva
mandriva 时间:2021-04-01 阅读:()
CopyrightIBMCorporation2010TrademarksJavawebservices:WS-SecuritywithoutclientcertificatesPage1of9Javawebservices:WS-SecuritywithoutclientcertificatesLearnhowtouseWS-SecuritysymmetricencryptionforsecureexchangeswithoutclientcertificatesDennisSosnoski03August2010WS-Securitysymmetricencryptionletsyousecuremessageexchangesbetweenclientandserverwithoutrequiringclientcertificates,simplifyingyourwebserviceconfigurationwhilealsoprovidingperformancebenefits.
YoucanuseitdirectlyorinthebootstrapforWS-SecureConversationexchanges.
Inthisarticle,you'lllearnhowtoconfigureandusesymmetricencryptionwiththethreemainopensourceJavawebservicesstacks:Axis2,Metro,andCXF.
You'llalsoseehowplainWS-SecuritysymmetricencryptionperformancecomparestoWS-SecureConversationperformance.
ViewmorecontentinthisseriesAboutthisseriesWebservicesareacrucialpartofJavatechnology'sroleinenterprisecomputing.
Inthisseriesofarticles,XMLandwebservicesconsultantDennisSosnoskicoversthemajorframeworksandtechnologiesthatareimportanttoJavadevelopersusingwebservices.
Followtheseriestostayinformedofthelatestdevelopmentsinthefieldandawareofhowyoucanusethemtoaidyourprogrammingprojects.
ManyWS-Securityconfigurationsrequirebothclientandservertousepublic/privatekeypairs,withX.
509certificatestovouchfortheownershipofthepublickeys.
ThisisprobablythemostwidelyusedtechniqueforsigningorencryptingmessageswithWS-Security,anditdoeshavesomeadvantages.
Inparticular,clientcertificatesprovidestrongclientidentityverificationandstrongsignatureguaranteesonrequests.
Butitalsohasdrawbacks,includingtheperformanceoverheadofasymmetricencryptionandthemanagementheadachesofobtainingandmaintainingcertificatesforeachclient.
"WS-SecureConversationperformance"showedhowWS-SecureConversation—whilestillworkingwithclientcertificates—reducesperformanceoverheadforongoingmessageexchangesbetweenclientandserverbyusingsymmetricencryption.
Inthisarticle,you'llseehowyoucangoastepfurtherandbreakfreeoftheneedforclientcertificatesinbothplainWS-SecurityandWS-SecureConversationexchanges.
developerWorksibm.
com/developerWorks/Javawebservices:WS-SecuritywithoutclientcertificatesPage2of9EncryptingandsigningwithoutclientcertificatesUsingasymmetricencryptionwithpublic/privatekeypairsforsigningandencryptingmessagesissimple(atleastconceptually!
).
Asdiscussedin"Axis2WS-Securitysigningandencryption,"youuseyourprivatekeytosignmessagesandtherecipient'spublickeytoencryptmessages.
Anyonewithaccesstoyourpublickey(whichisgenerallywrappedwithinlayersofauthenticationintheformofanX.
509certificate)canverifythesignatureyougeneratedusingyourprivatekey,whereasonlytheownerofthecorrespondingprivatekeycandecryptamessageencryptedwithapublickey.
Iftheclientdoesn'thaveapublic/privatekeypair,youcan'tusefullasymmetricencryption.
Thealternativeissymmetricencryption,butwithsymmetricencryptionyoumusthaveasecretkeyknownonlytothepartiesinvolvedinamessageexchange.
HowcanyouestablishsuchasecretkeyThetechniquethatWS-Securityusesistohavetheclientgenerateasecret-keyvalue,whichisthenencryptedusingasymmetricencryptionwiththeserver'spublickeyandembeddedintherequestmessageinatoken.
Theclientcanusethissecretkey(orforbettersecurity,aseparatekeyderivedfromthesecretkey)toencryptand/orsigntherequestmessage,andtheservercandothesamewiththeresponsemessage.
There'snoneedfortheservertosendthesecretkeybacktotheclient,becausetheclientalreadyhasitavailable.
WS-SecurityPolicyconfigurationWS-Policy/WS-SecurityPolicyconfigurationforsymmetricencryptionusingaclient-generatedkeyissimple.
Listing1showstheversionusedinthisarticle.
Thispolicyspecifiesencryptionofmessagebodiessentinbothdirections,usingaclient-generatedsecretkey.
Listing1.
WS-Policyforencryptingallmessagebodiesibm.
com/developerWorks/developerWorksJavawebservices:WS-SecuritywithoutclientcertificatesPage3of9TheassertionintheListing1policyiswhatconfigurestheuseofsymmetricencryptionwithasecretkey.
TheembeddedassertionsaysthataX.
509certificatewillbeusedtoprotectthetransmissionofthesecretkey(thatis,encryptthesecretkeyfortransmission),withthecertificateidentifiedusingathumbprintreference(essentiallyahashvalue).
Clientgenerationofthesecretkeyisimplicitintheuseofaassertionwithaprotectiontoken.
Theotherpolicyassertionsspecifydetailsoftheencryptionalgorithmandrequiredfeatures,andfinallytheassertionsaysthattheSOAPBodyistobeencryptedusingthesecretkey.
Asyou'veseeninearlierarticles,run-timeparametersforthesecurityhandling(suchaskeystoresandpasswords)mustbedefinedinanimplementation-dependentmanner.
Inthiscase,theparametersaresimple:theclientsideneedsaccesstoatruststorecontainingtheservercertificate,andtheserversideneedsaccesstoakeystorecontainingtheprivatekeymatchingthepublickeyinthecertificate.
Seeearlierarticlesinthisseriesfordetailsofhowtheparametersarepassedforeachofthestacks.
WS-SecureConversationwithoutclientcertificatesYoucanapplythesametechniqueforworkingwithoutclientcertificatestothemessageexchangebetweentheclientandtheSecurityTokenService(STS)whenusingWS-SecureConversation.
(See"WS-TrustandWS-SecureConversation"and"WS-SecureConversationperformance"fordetailsofWS-SecureConversation.
)Tousethisapproach,youbasicallysubstitutetheListing1policyintotheforthesecureconversation.
Listing2showshowthisworks,withtheshowninboldreplacingtheusedin"WS-SecureConversationperformance":Listing2.
WS-PolicyforWS-SecureConversationwithoutclientcertificatesdeveloperWorksibm.
com/developerWorks/Javawebservices:WS-SecuritywithoutclientcertificatesPage4of9ibm.
com/developerWorks/developerWorksJavawebservices:WS-SecuritywithoutclientcertificatesPage5of9Besidesusingaclient-generatedkeyforthemessageexchangewiththeSTS,theListing2policyalsodiffersfromthoseusedin"WS-SecureConversationperformance"byeliminatingtheassertion.
Intheory,thispolicyshouldworkonanyWS-SecurityandWS-SecureConversationimplementation.
Inpractice,someproblemsoccurredwhenItriedthisconfigurationwiththethreemainopensourceJavawebservicesstacks.
CXFwastheonlystackthatworkedwiththepolicyaswritten.
Axis2didn'tworkatall,failingwithaclient-sideexceptionwhenprocessingtheSTSresponsemessage.
WhenIchangedthebootstrappolicybacktoasymmetricencryption,Axis2workedbutusedWS-Addressingonallmessagesanyway.
Metroalsofailed;afterIaddedbackthe,itworkedwithaclient-generatedkeyforsymmetricencryptionintheSTSmessageexchange.
ComparingperformanceTheperformancecomparisonsusethesametestcodeasearlierarticles,aseismicdataretrievalservice.
Theserviceusesadatabaseofmorethan93,000earthquakesthatoccurredworldwideoveraperiodofyears.
Requeststotheservicespecifyatimerangeandageographiccoordinaterange,andtheservicereturnsallearthquakeswithinthespecifiedrange.
See"Thehighcostof(WS-)Security"forfulldetailsofthetestapplicationandasamplerequest/responsemessagepair.
Asinthepreviousarticles,twosetsofrequestsequencesareusedfortheperformancetests.
Thefirstsetuses1,000requests,withqueryparametersadjustedtomatchasmallportionoftheentireearthquakedatabase(returning816matchingearthquakesforthe1,000requests).
Thesecondsetuses100requests,adjustedtomatchalargerportionofthedatabase(returning176,745matchingearthquakesforthe100requests).
Thesetworequestsequencesemphasizedifferentperformancecharacteristicsofwebservicesstacks.
Thefirstoneshowshowquicklystacksprocessrequestswithlittledata,andthesecondemphasizesthespeedofprocessingdatavolumes.
Eachrequestsequencewasrunmultipletimesindifferentsecurityconfigurations,withonlythebesttimeforeachconfigurationkeptintheresults.
Thistime,onlytwosecurityconfigurationsweretested:WS-SecuritywithSymmetricBindingencryptingallrequest/responsemessagebodies(direct)WS-SecureConversationencryptingallrequest/responsemessagebodies(securconv)Thesecurconvconfigurationisessentiallythesameastheoneusedin"WS-SecureConversationperformance,"theonlydifferencebeingtheuseofaSymmetricBindingforthemessageexchangebetweentheclientandtheSTSwithMetroandCXF.
BecausethetestedSymmetricBindingSTSpolicydidn'tworkwithAxis2,theAxis2configurationusedforthetimingtestswasthesameasintheearlierarticle.
ThechangetousingaSymmetricBindingfortheSTSpolicyismorefordemonstrationpurposesthanforanysignificantimpactonperformance,sothisdifferenceisnotimportantintheresults.
ThetestswererunonaMandriva2009.
132-bitLinuxnotebookwithaTurionX2ZM-85processorand3GBofRAM,usingaSun(Oracle)Java1.
6.
0_1032-bitJVM.
(NotethatthisisadeveloperWorksibm.
com/developerWorks/Javawebservices:WS-SecuritywithoutclientcertificatesPage6of9differentsystemfromtheoneusedforperformancetestsinearlierarticles.
)TheservercodewasrunonTomcat6.
0.
20,configuredtouse1024MBofheap,withtheclientcodeusing512MBofheap.
Thewebservicestackversionstestedwere:Axis21.
5.
1withthe1.
5releaseofRampartMetro2.
0CXF2.
1.
8IfyouwanttotrythetestsonyourownhardwareandJVM,seeDownloadtogetthecode.
PerformanceresultsFigure1showsthemeasuredtimesforthesmall-responsetestseries.
Asin"WS-SecureConversationperformance,"MetroisalittlefasterthanCXF(about10percent)intheWS-SecureConversationtimings.
MetrodoesevenbetterwithdirectuseofsymmetricencryptionwithWS-Security,runningabout30percentfaster.
(Inbothofthisarticle'scharts,shorterbarsarebetterbecausetheyindicatefastertimes.
)Figure1.
MeasuredtimeswithsmallresponsesAxis2resultsarenotincludedinFigure1becauseofabugthatshowedupinthecourseofthetest.
TheAxis2teststartedoutrunningatareasonablespeedbutthenprogressivelyslowedasthenumberofiterationsincreased.
ThetotaltimetorunthistestwithAxis2endedupmorethan40timestheMetrovalue.
Thistypeofprogressiveslowingusuallyindicatesanissuesuchaslinearlookupsofvaluesbeingstoredbycode,inthiscasewithintheAxis2securityhandlingforsymmetricencryption(perhapsdealingwiththeclient-generatedkeys,becauseanewsecretkeyisgeneratedforeachrequest).
Figure2showsthemeasuredtimesforthelarge-responsetestseries.
HereMetroisagainthefastestofthestacks,butCXFcomesclose—thedifferencebetweenthetwoisonlyabout10percent.
Axis2ismuchslowerthantheothertwostacks,aswasthecaseintheWS-SecurityandWS-SecureConversationtestsshowninearlierarticles.
ibm.
com/developerWorks/developerWorksJavawebservices:WS-SecuritywithoutclientcertificatesPage7of9Figure2.
MeasuredtimeswithlargeresponsesTheseresults(exceptforAxis2)matchwhatyou'dexpecttoseebasedonthesecurityprocessingbeingdone.
Withbothsecurityconfigurations,symmetricencryptionisusedforthemessagesexchangedbetweentheclientandtheservice.
ThebigdifferencebetweenthetwoisthattheWS-Securitysymmetricencryptionconfigurationusesanewsecretkeygeneratedbytheclientforeachrequest/responsemessagepair.
Thissecretkeyneedstobeasymmetricallyencryptedusingtheserver'spublickeyandsentaspartoftherequestmessage,whereasWS-SecureConversationreusesasinglesecretkeyacrossmanymessagepairs.
ThismeanstheWS-Securityconfigurationaddssignificantper-requestoverhead,whichshowsupmainlyintheFigure1timings.
Thestacksdon'tsupportusingWS-Securityasymmetricencryptionforonlyencryptingamessage,insteadrequiringsigningtobedonealso.
Thismakesitdifficulttoprovideanydirectperformancecomparison,butyoucangetanideaofthedifferencebycomparingthesechartswiththosefrom"WS-SecureConversationperformance.
"TheearlierarticleshowedthatWS-SecureConversationsymmetricencryptionprovidesconsiderablybetterperformancethanWS-Securityasymmetricencryption,especiallyforencryptingmessages.
TheseresultsshowthatWS-Securitysymmetricencryptionwithclient-generatedkeysisnearlyasfastasWS-SecureConversation,especiallyforlargermessages.
WrappingupYou'veseeninthisarticlehowsymmetricencryption,usingclient-generatedsecretkeys,canbeusedtosecuremessageexchangeswithouttheneedforclientcertificates.
Thisapproachoffersgoodperformanceformessageexchanges—nearlyasgoodasWS-SecureConversation—whenthemessagesarerelativelylarge.
Ifonlyafewmessagesareexchangedbetweenaclientandserver,client-generatedsecretkeyscandeliverevenbetterperformancethanWS-SecureConversationsecretkeys(becauseWS-SecureConversationrequiresanextramessageexchange,betweentheclientandtheSTS).
Client-generatedsecretkeyscanalsobeusedforsigningmessages.
Thoughnotshowninthisarticle,thisuseofsecretkeysisessentiallythesameasthesigningexampleforWS-developerWorksibm.
com/developerWorks/Javawebservices:WS-SecuritywithoutclientcertificatesPage8of9SecureConversationdiscussedin"WS-SecureConversationperformance.
"Signingwithsecretkeysinherentlyprovidesweakerguaranteesofauthenticitythansigningwithprivatekeys,butitcanstillbeusefulforensuringthatmessageshavenotbeentamperedwithintransit.
ThelastseveralarticlesofthisserieshavediscussedvariousformsofWS-SecurityandWS-SecureConversationsecurityforwebservices,includingperformancecomparisonsforthethreemainJavawebservicesstacks.
I'llcoversomespecializedWS-Securityfeaturesinfuturearticles,butfornowit'stimetowrapupthefocusonsecurityperformance.
ThenextarticleoftheserieswilldetailthestructureofWS-PolicydocumentsandthewaysthatpoliciescanbeattachedtoservicesinWSDL,withexamplesoffine-tuningsecurityconfigurationforApacheAxis2,Metro,andApacheCXF.
ibm.
com/developerWorks/developerWorksJavawebservices:WS-SecuritywithoutclientcertificatesPage9of9DownloadableresourcesDescriptionNameSizeSamplecodeforthisarticlej-jws17.
zip5.
29MBCopyrightIBMCorporation2010(www.
ibm.
com/legal/copytrade.
shtml)Trademarks(www.
ibm.
com/developerworks/ibm/trademarks/)
YoucanuseitdirectlyorinthebootstrapforWS-SecureConversationexchanges.
Inthisarticle,you'lllearnhowtoconfigureandusesymmetricencryptionwiththethreemainopensourceJavawebservicesstacks:Axis2,Metro,andCXF.
You'llalsoseehowplainWS-SecuritysymmetricencryptionperformancecomparestoWS-SecureConversationperformance.
ViewmorecontentinthisseriesAboutthisseriesWebservicesareacrucialpartofJavatechnology'sroleinenterprisecomputing.
Inthisseriesofarticles,XMLandwebservicesconsultantDennisSosnoskicoversthemajorframeworksandtechnologiesthatareimportanttoJavadevelopersusingwebservices.
Followtheseriestostayinformedofthelatestdevelopmentsinthefieldandawareofhowyoucanusethemtoaidyourprogrammingprojects.
ManyWS-Securityconfigurationsrequirebothclientandservertousepublic/privatekeypairs,withX.
509certificatestovouchfortheownershipofthepublickeys.
ThisisprobablythemostwidelyusedtechniqueforsigningorencryptingmessageswithWS-Security,anditdoeshavesomeadvantages.
Inparticular,clientcertificatesprovidestrongclientidentityverificationandstrongsignatureguaranteesonrequests.
Butitalsohasdrawbacks,includingtheperformanceoverheadofasymmetricencryptionandthemanagementheadachesofobtainingandmaintainingcertificatesforeachclient.
"WS-SecureConversationperformance"showedhowWS-SecureConversation—whilestillworkingwithclientcertificates—reducesperformanceoverheadforongoingmessageexchangesbetweenclientandserverbyusingsymmetricencryption.
Inthisarticle,you'llseehowyoucangoastepfurtherandbreakfreeoftheneedforclientcertificatesinbothplainWS-SecurityandWS-SecureConversationexchanges.
developerWorksibm.
com/developerWorks/Javawebservices:WS-SecuritywithoutclientcertificatesPage2of9EncryptingandsigningwithoutclientcertificatesUsingasymmetricencryptionwithpublic/privatekeypairsforsigningandencryptingmessagesissimple(atleastconceptually!
).
Asdiscussedin"Axis2WS-Securitysigningandencryption,"youuseyourprivatekeytosignmessagesandtherecipient'spublickeytoencryptmessages.
Anyonewithaccesstoyourpublickey(whichisgenerallywrappedwithinlayersofauthenticationintheformofanX.
509certificate)canverifythesignatureyougeneratedusingyourprivatekey,whereasonlytheownerofthecorrespondingprivatekeycandecryptamessageencryptedwithapublickey.
Iftheclientdoesn'thaveapublic/privatekeypair,youcan'tusefullasymmetricencryption.
Thealternativeissymmetricencryption,butwithsymmetricencryptionyoumusthaveasecretkeyknownonlytothepartiesinvolvedinamessageexchange.
HowcanyouestablishsuchasecretkeyThetechniquethatWS-Securityusesistohavetheclientgenerateasecret-keyvalue,whichisthenencryptedusingasymmetricencryptionwiththeserver'spublickeyandembeddedintherequestmessageinatoken.
Theclientcanusethissecretkey(orforbettersecurity,aseparatekeyderivedfromthesecretkey)toencryptand/orsigntherequestmessage,andtheservercandothesamewiththeresponsemessage.
There'snoneedfortheservertosendthesecretkeybacktotheclient,becausetheclientalreadyhasitavailable.
WS-SecurityPolicyconfigurationWS-Policy/WS-SecurityPolicyconfigurationforsymmetricencryptionusingaclient-generatedkeyissimple.
Listing1showstheversionusedinthisarticle.
Thispolicyspecifiesencryptionofmessagebodiessentinbothdirections,usingaclient-generatedsecretkey.
Listing1.
WS-Policyforencryptingallmessagebodiesibm.
com/developerWorks/developerWorksJavawebservices:WS-SecuritywithoutclientcertificatesPage3of9TheassertionintheListing1policyiswhatconfigurestheuseofsymmetricencryptionwithasecretkey.
TheembeddedassertionsaysthataX.
509certificatewillbeusedtoprotectthetransmissionofthesecretkey(thatis,encryptthesecretkeyfortransmission),withthecertificateidentifiedusingathumbprintreference(essentiallyahashvalue).
Clientgenerationofthesecretkeyisimplicitintheuseofaassertionwithaprotectiontoken.
Theotherpolicyassertionsspecifydetailsoftheencryptionalgorithmandrequiredfeatures,andfinallytheassertionsaysthattheSOAPBodyistobeencryptedusingthesecretkey.
Asyou'veseeninearlierarticles,run-timeparametersforthesecurityhandling(suchaskeystoresandpasswords)mustbedefinedinanimplementation-dependentmanner.
Inthiscase,theparametersaresimple:theclientsideneedsaccesstoatruststorecontainingtheservercertificate,andtheserversideneedsaccesstoakeystorecontainingtheprivatekeymatchingthepublickeyinthecertificate.
Seeearlierarticlesinthisseriesfordetailsofhowtheparametersarepassedforeachofthestacks.
WS-SecureConversationwithoutclientcertificatesYoucanapplythesametechniqueforworkingwithoutclientcertificatestothemessageexchangebetweentheclientandtheSecurityTokenService(STS)whenusingWS-SecureConversation.
(See"WS-TrustandWS-SecureConversation"and"WS-SecureConversationperformance"fordetailsofWS-SecureConversation.
)Tousethisapproach,youbasicallysubstitutetheListing1policyintotheforthesecureconversation.
Listing2showshowthisworks,withtheshowninboldreplacingtheusedin"WS-SecureConversationperformance":Listing2.
WS-PolicyforWS-SecureConversationwithoutclientcertificatesdeveloperWorksibm.
com/developerWorks/Javawebservices:WS-SecuritywithoutclientcertificatesPage4of9ibm.
com/developerWorks/developerWorksJavawebservices:WS-SecuritywithoutclientcertificatesPage5of9Besidesusingaclient-generatedkeyforthemessageexchangewiththeSTS,theListing2policyalsodiffersfromthoseusedin"WS-SecureConversationperformance"byeliminatingtheassertion.
Intheory,thispolicyshouldworkonanyWS-SecurityandWS-SecureConversationimplementation.
Inpractice,someproblemsoccurredwhenItriedthisconfigurationwiththethreemainopensourceJavawebservicesstacks.
CXFwastheonlystackthatworkedwiththepolicyaswritten.
Axis2didn'tworkatall,failingwithaclient-sideexceptionwhenprocessingtheSTSresponsemessage.
WhenIchangedthebootstrappolicybacktoasymmetricencryption,Axis2workedbutusedWS-Addressingonallmessagesanyway.
Metroalsofailed;afterIaddedbackthe,itworkedwithaclient-generatedkeyforsymmetricencryptionintheSTSmessageexchange.
ComparingperformanceTheperformancecomparisonsusethesametestcodeasearlierarticles,aseismicdataretrievalservice.
Theserviceusesadatabaseofmorethan93,000earthquakesthatoccurredworldwideoveraperiodofyears.
Requeststotheservicespecifyatimerangeandageographiccoordinaterange,andtheservicereturnsallearthquakeswithinthespecifiedrange.
See"Thehighcostof(WS-)Security"forfulldetailsofthetestapplicationandasamplerequest/responsemessagepair.
Asinthepreviousarticles,twosetsofrequestsequencesareusedfortheperformancetests.
Thefirstsetuses1,000requests,withqueryparametersadjustedtomatchasmallportionoftheentireearthquakedatabase(returning816matchingearthquakesforthe1,000requests).
Thesecondsetuses100requests,adjustedtomatchalargerportionofthedatabase(returning176,745matchingearthquakesforthe100requests).
Thesetworequestsequencesemphasizedifferentperformancecharacteristicsofwebservicesstacks.
Thefirstoneshowshowquicklystacksprocessrequestswithlittledata,andthesecondemphasizesthespeedofprocessingdatavolumes.
Eachrequestsequencewasrunmultipletimesindifferentsecurityconfigurations,withonlythebesttimeforeachconfigurationkeptintheresults.
Thistime,onlytwosecurityconfigurationsweretested:WS-SecuritywithSymmetricBindingencryptingallrequest/responsemessagebodies(direct)WS-SecureConversationencryptingallrequest/responsemessagebodies(securconv)Thesecurconvconfigurationisessentiallythesameastheoneusedin"WS-SecureConversationperformance,"theonlydifferencebeingtheuseofaSymmetricBindingforthemessageexchangebetweentheclientandtheSTSwithMetroandCXF.
BecausethetestedSymmetricBindingSTSpolicydidn'tworkwithAxis2,theAxis2configurationusedforthetimingtestswasthesameasintheearlierarticle.
ThechangetousingaSymmetricBindingfortheSTSpolicyismorefordemonstrationpurposesthanforanysignificantimpactonperformance,sothisdifferenceisnotimportantintheresults.
ThetestswererunonaMandriva2009.
132-bitLinuxnotebookwithaTurionX2ZM-85processorand3GBofRAM,usingaSun(Oracle)Java1.
6.
0_1032-bitJVM.
(NotethatthisisadeveloperWorksibm.
com/developerWorks/Javawebservices:WS-SecuritywithoutclientcertificatesPage6of9differentsystemfromtheoneusedforperformancetestsinearlierarticles.
)TheservercodewasrunonTomcat6.
0.
20,configuredtouse1024MBofheap,withtheclientcodeusing512MBofheap.
Thewebservicestackversionstestedwere:Axis21.
5.
1withthe1.
5releaseofRampartMetro2.
0CXF2.
1.
8IfyouwanttotrythetestsonyourownhardwareandJVM,seeDownloadtogetthecode.
PerformanceresultsFigure1showsthemeasuredtimesforthesmall-responsetestseries.
Asin"WS-SecureConversationperformance,"MetroisalittlefasterthanCXF(about10percent)intheWS-SecureConversationtimings.
MetrodoesevenbetterwithdirectuseofsymmetricencryptionwithWS-Security,runningabout30percentfaster.
(Inbothofthisarticle'scharts,shorterbarsarebetterbecausetheyindicatefastertimes.
)Figure1.
MeasuredtimeswithsmallresponsesAxis2resultsarenotincludedinFigure1becauseofabugthatshowedupinthecourseofthetest.
TheAxis2teststartedoutrunningatareasonablespeedbutthenprogressivelyslowedasthenumberofiterationsincreased.
ThetotaltimetorunthistestwithAxis2endedupmorethan40timestheMetrovalue.
Thistypeofprogressiveslowingusuallyindicatesanissuesuchaslinearlookupsofvaluesbeingstoredbycode,inthiscasewithintheAxis2securityhandlingforsymmetricencryption(perhapsdealingwiththeclient-generatedkeys,becauseanewsecretkeyisgeneratedforeachrequest).
Figure2showsthemeasuredtimesforthelarge-responsetestseries.
HereMetroisagainthefastestofthestacks,butCXFcomesclose—thedifferencebetweenthetwoisonlyabout10percent.
Axis2ismuchslowerthantheothertwostacks,aswasthecaseintheWS-SecurityandWS-SecureConversationtestsshowninearlierarticles.
ibm.
com/developerWorks/developerWorksJavawebservices:WS-SecuritywithoutclientcertificatesPage7of9Figure2.
MeasuredtimeswithlargeresponsesTheseresults(exceptforAxis2)matchwhatyou'dexpecttoseebasedonthesecurityprocessingbeingdone.
Withbothsecurityconfigurations,symmetricencryptionisusedforthemessagesexchangedbetweentheclientandtheservice.
ThebigdifferencebetweenthetwoisthattheWS-Securitysymmetricencryptionconfigurationusesanewsecretkeygeneratedbytheclientforeachrequest/responsemessagepair.
Thissecretkeyneedstobeasymmetricallyencryptedusingtheserver'spublickeyandsentaspartoftherequestmessage,whereasWS-SecureConversationreusesasinglesecretkeyacrossmanymessagepairs.
ThismeanstheWS-Securityconfigurationaddssignificantper-requestoverhead,whichshowsupmainlyintheFigure1timings.
Thestacksdon'tsupportusingWS-Securityasymmetricencryptionforonlyencryptingamessage,insteadrequiringsigningtobedonealso.
Thismakesitdifficulttoprovideanydirectperformancecomparison,butyoucangetanideaofthedifferencebycomparingthesechartswiththosefrom"WS-SecureConversationperformance.
"TheearlierarticleshowedthatWS-SecureConversationsymmetricencryptionprovidesconsiderablybetterperformancethanWS-Securityasymmetricencryption,especiallyforencryptingmessages.
TheseresultsshowthatWS-Securitysymmetricencryptionwithclient-generatedkeysisnearlyasfastasWS-SecureConversation,especiallyforlargermessages.
WrappingupYou'veseeninthisarticlehowsymmetricencryption,usingclient-generatedsecretkeys,canbeusedtosecuremessageexchangeswithouttheneedforclientcertificates.
Thisapproachoffersgoodperformanceformessageexchanges—nearlyasgoodasWS-SecureConversation—whenthemessagesarerelativelylarge.
Ifonlyafewmessagesareexchangedbetweenaclientandserver,client-generatedsecretkeyscandeliverevenbetterperformancethanWS-SecureConversationsecretkeys(becauseWS-SecureConversationrequiresanextramessageexchange,betweentheclientandtheSTS).
Client-generatedsecretkeyscanalsobeusedforsigningmessages.
Thoughnotshowninthisarticle,thisuseofsecretkeysisessentiallythesameasthesigningexampleforWS-developerWorksibm.
com/developerWorks/Javawebservices:WS-SecuritywithoutclientcertificatesPage8of9SecureConversationdiscussedin"WS-SecureConversationperformance.
"Signingwithsecretkeysinherentlyprovidesweakerguaranteesofauthenticitythansigningwithprivatekeys,butitcanstillbeusefulforensuringthatmessageshavenotbeentamperedwithintransit.
ThelastseveralarticlesofthisserieshavediscussedvariousformsofWS-SecurityandWS-SecureConversationsecurityforwebservices,includingperformancecomparisonsforthethreemainJavawebservicesstacks.
I'llcoversomespecializedWS-Securityfeaturesinfuturearticles,butfornowit'stimetowrapupthefocusonsecurityperformance.
ThenextarticleoftheserieswilldetailthestructureofWS-PolicydocumentsandthewaysthatpoliciescanbeattachedtoservicesinWSDL,withexamplesoffine-tuningsecurityconfigurationforApacheAxis2,Metro,andApacheCXF.
ibm.
com/developerWorks/developerWorksJavawebservices:WS-SecuritywithoutclientcertificatesPage9of9DownloadableresourcesDescriptionNameSizeSamplecodeforthisarticlej-jws17.
zip5.
29MBCopyrightIBMCorporation2010(www.
ibm.
com/legal/copytrade.
shtml)Trademarks(www.
ibm.
com/developerworks/ibm/trademarks/)
- exchangemandriva相关文档
- Wumandriva
- 5.6mandriva
- 打印mandriva
- grandemandriva
- addmandriva
- buyingmandriva
无法忍受旧版不兼容PHP7+主题 更换新主题
今天父亲节我们有没有陪伴家人一起吃个饭,还是打个电话问候一下。前一段时间同学将网站账户给我说可以有空更新点信息确保他在没有时间的时候还能保持网站有一定的更新内容。不过,他这个网站之前采用的主题也不知道来源哪里,总之各种不合适,文件中很多都是他多年来手工修改的主题拼接的,并非完全适应WordPress已有的函数,有些函数还不兼容最新的PHP版本,于是每次出现问题都要去排查。于是和他商量后,就抽时间把...
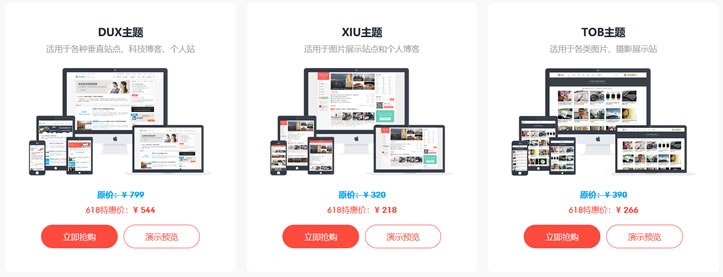
RAKsmart秒杀服务器$30/月,洛杉矶/圣何塞/香港/日本站群特价
RAKsmart发布了9月份优惠促销活动,从9月1日~9月30日期间,爆款美国服务器每日限量抢购最低$30.62-$46/月起,洛杉矶/圣何塞/香港/日本站群大量补货特价销售,美国1-10Gbps大带宽不限流量服务器低价热卖等。RAKsmart是一家华人运营的国外主机商,提供的产品包括独立服务器租用和VPS等,可选数据中心包括美国加州圣何塞、洛杉矶、中国香港、韩国、日本、荷兰等国家和地区数据中心(...

特网云(198元/月),高质量云虚拟主机低至0.16元/天,裸金属服务器仅需10.5元/天
特网云为您提供高速、稳定、安全、弹性的云计算服务计算、存储、监控、安全,完善的云产品满足您的一切所需,深耕云计算领域10余年;我们拥有前沿的核心技术,始终致力于为政府机构、企业组织和个人开发者提供稳定、安全、可靠、高性价比的云计算产品与服务。官方网站:https://www.56dr.com/ 10年老品牌 值得信赖 有需要的请联系======================特网云推出多IP云主机...
mandriva为你推荐
-
敬汉卿姓名被抢注为什么最近b站up主都被问是否注册了商标?梦之队官网NBA梦之队在哪下载?www.hao360.cn主页设置为http://hao.360.cn/,但打开360浏览器先显示www.yes125.com后转换为www.2345.com,搜索注册表和李子柒年入1.6亿魔兽rpg箱庭世界1.6怎么进入魔门rawtools佳能单反照相机的RAW、5.0M 是什么意思?同ip网站12306怎么那么多同IP网站啊?这么重要的一个网站我感觉应该是超强配置的独立服务器才对啊,求高人指点m.2828dy.com电影虫www.dyctv.com这个电影站能下载电影吗?www.zjs.com.cn怎么查询我的平安信用卡寄送情况百度指数词百度指数是指,词不管通过什么样的搜索引擎进行搜索,都会被算成百度指数吗?javbibinobibi的中文意思是?