Hardware腾讯rom
腾讯rom 时间:2021-01-29 阅读:()
IntegrityMeasurementbasedonTrustedComputingYimingLi1,a,HaiheBa2,bandJiangchunRen3,c1CollegeofComputer,NationalUniversityofDefenseTechnology,Changsha,Hunan410073,China2CollegeofComputer,NationalUniversityofDefenseTechnology,Changsha,Hunan410073,China3CollegeofComputer,NationalUniversityofDefenseTechnology,Changsha,Hunan410073,Chinaaemail:jason.
24@qq.
com,bemail:bahaihe@hotmail.
com,cemail:wwwrjc@163.
comKeywords:TrustedComputing;IntegrityMeasurement;RemoteAttestationAbstract.
Withtherapiddevelopmentofmoderninformationtechnology,moreandmorepeoplebelievethattheprotectionofhardwareequipmentmustbeenhancedinordertoimprovethesecuritycapabilitiesofcomputerinformationsystemsbetter.
Trustedcomputingimprovethetrustworthinessofsystemthroughthesecurechipfromhardwarelevel,usingthetrustedroot,chainoftrust,trustedmodeltoensuretheintegrityofthesystem,andexpandsthetrustedchaintoapplicationlayer,ensuresthecredibilityofsoftwarethroughmeasurementandverificationtechnology.
Inthispaper,wewillintroducerelatedhotresearchaboutintegritymeasurement.
IntroductionTheideaoftrustedcomputingderivedfromsuccessfulmanagementexperienceinhumansociety,thatis,eachcountryhasastablerootoftrust,andbuildtrustchainsecuritymechanismbasedonit,whichisresponsibleforthemanagementandimplementationofthenationallevelsofassessment.
However,atpresent,hasnotyetformedaunifieddefinitionontrust.
TrustedComputingGroup(TCG)definedatrustedentity'sbehaviorisalwaysintheexpectedway,toachievethedesiredgoal,thencallthisentityistrusted[1,2].
Asystemistrustediftheoperationorprocedureofcomponentsinvolvedinthecomputingispredicableinanyconditions,andcanprotectagainstvirusesandphysicaldisturbance,definedbyInternationalOrganizationforStandardization/InternationalElectroTechnicalCommission(ISO/IEC).
Measurethetrustworthinessofcomputingsystems,andstoremeasurementsecurely;provideattestationreportwhenremoteobjectaskedforsystem'strustworthiness,thismechanismreferredto"Measure-Storage-Report"mechanism.
Thismechanismdoesnotonlyensurethetrustworthinessofthetrustedcomputingsystem,butalsohavetheabilitytoprovidetrustedproofoutward.
Rootoftrustisthebasispointoftrustedcomputersystem,thereare3trustedrootsoftrustedcomputingplatform,whichisRootofTrustforMeasurement(RTM),RootofTrustforStorage(RTS)andRootofTrustforReport(RTR).
Theyarethetrustedbasepointsofcomputersystem,measurementofplatformandstorageofplatformseparately.
AsshowninFig1,chainoftrustreflects"Measure-Storage-Report"mechanismwell,thatis,measurethetrustworthinessofcomputingplatform,storemeasurementvalueandprovideattestationreport.
Chainoftrustisthetechnicalimplementationoftrustmeasurementmodel,toextendtrustrelationshipfromrootoftrusttoentirecomputingplatform.
Usinganiterativecalculationofhashvalue,whichisconnectingpresentvaluewithnewvalue,andthencalculatehashvalueasanewmeasurement.
Aftermeasurementandstorage,providingattestationreportwhentheremoteentityasked.
ThismechanismiscalledRemoteAttestation.
BIOSBootSectorOSBIOSBootBlockApplicationNetworkHardwareROMMainMemoryTrustModelMeasureStoreReportLogRootofTrustRTSRTRFig.
1.
ChainoftrustmodelIntegrityMeasurementbasedonStaticRootofTrustMeasurementApplicationintegritymeasurementandverificationneedtoprovewhetherthetrustworthinessoflocalcomputingsystemisinlinewiththepredictionofbothlocalandremoteauthenticator.
a.
Binary-basedEarlyintegritymeasurementandverificationismainlyaboutintegritymeasurementofbinarycodeimage,softwareconfiguration.
ThatusingTPMsignatureandlogofintegritymeasurementtoprovetheintegritystatusofsoftware.
Thismethodrequiresplatformmorestringent,isnotflexibleenough,therearetwodisadvantages:(1)Privacy.
IntegritymeasurementbasedonbinaryneedsTPMsignature,andcontainschainoftrust,exposingtheconfigurationinformationofplatform,provideabreakthroughtohostiletosomeextent,sothatlocalcomputingsystemismorevulnerabletovariousattacks.
(2)Difficulttoupdate.
Chainoftrustinvolvingmultiplesystemcomponents,theinformationandversiondifferentfromeachother.
Systemupdatelikelytocausetheintegrityinformationisdifficulttoverify.
IBMhasdesignedandimplementedIMA(IntegrityMeasureArchitecture)3basedonTCGspecifications,measureanintegrityintheorderfromrootoftrust,BIOS,bootsector,OStoapplications,progressivemeasureandtrustlevelbylevel.
Thismethodisabletodetectcurrentoperatingstatusofsystem,whichcouldfindpossibletampering.
IMAmeasurementmodulehasbeenusedasapartofLinuxsecuritymechanisms,andarewidelyusedinavarietyofpracticalapplications.
b.
Property-basedToovercometheshortcomingsofbinaryauthentication,Haldarproposedsemanticremoteauthenticationscheme[4],usingatrustedvirtualmachinetoverifycertainsemanticpropertiesofprogram,achievingacomplexanddynamicintegritymeasurementofadvancedapplicationprograminaplatform-independentway;ChenfromHPLabsproposedtheproperty-basedremoteattestation,convertedbinaryattestationtoproperty-basedattestationbyusingthemainfunctionsofTCG,solvedissueslikesensitiveinformationleakageandupdatedifficultycausedbybinarymeasurement,andselectedatrustedthirdpartyastheissuerofproperty-configurationcertificate.
TheauthenticationmethodbasedonpropertyproposedbySadeghietal.
[5]isabletoestablishmappingbetweenpropertiesandplatformconfigurationsbyreportingplatform'sproperties,andestablishingpropertiesbytrustedcertificateauthority.
Binary-basedmeasurementmechanismprovidesbasicprotectionfortheintegrityofsystemsandapplications,butthereisahugeapplicationlimitations,especiallyinthesystemwithmultipleversionsofmodules;property-basedintegritymeasurementcanovercomethelimitationofbinary-basedintegritymeasurement,playaneffectiveroleinthebinaryimagewithsamepropertybutdifferenthashes,thespecificdifferencesisshowninTable1.
Table1.
ComparisonbetweendifferenttypesofintegritymeasurementBinary-basedProperty-basedObjectsExecutablebinarycodePropertyofplatformTypicalSystemsIMA[3],PRIMA[6]PBA[7],CPBA[8]PrivacyMayleakprivacyProtectprivacyEffectsLowefficiencyPracticalandscalableIntegrityMeasurementbasedonDynamicRootofTrustMeasurementThemeasurementaboveisIMAintegritymeasurementarchitecturebasedonStaticRootofTrustMeasurement,measureintegrityonlywhensystemstartup,cannotguaranteetheintegrityoftheprocess.
Tomakeupfortheseshortcomings,TCG1.
2specification[9]definesanewmechanism:verifythestartupprocessbyDynamicRootofTrustMeasurement(DRTM).
Intel'sTXT(TrustExecutionTechnology)[10]andAMD'sSVM(SecureVirtualMachineExtension)[11]arebothusingDRTMasunderlyingtrustmechanism.
ThedynamicestablishingprocessoftrustedenvironmentbasedonDRTMisknownasLateLaunchinTCG1.
2specification,toguaranteeatrustedstartupofavirtualmachinemanager.
BIND[12]proposedbyCarnegieMellonUniversityisfine-grainedsecuritycertificationservicefordistributedsystems,byusingTPM-basedmeasurementandsignaturemechanism,insertameasurepointineachprocessandprotectrunningprocessbyusingsecurekernelbasedonAMDsecurecoprocessor,toachievedynamicmeasurementsoftrustedprocesses.
BernhardKauer[13]analyzedtrustedcomputingsystembasedonStaticRootofTrustMeasurement(SRTM)indetail,pointedoutthesecurityvulnerabilitiesofthisRTM,andproposedasafeopeningloaderOSLO,transferredrootoftrustfromSRTMtoDRTMbyusingAMD'sskinitinstruction,narrowedthetrustedcomputingbaseofapplicationandweakenedtheattacksagainstTPMandBIOS.
CarnegieMellonUniversityCylablaboratorydesignedTrustVisor[14]basedonvirtualmachinemonitor,whichprovidesmemoryisolation,DMAprotectionandseveralvirtualTPMinterfaces(suchasSeal/UnSeal,Extend,Quote,etc.
),asaresult,notonlyprotectsuser'ssecuresensitivecodebutalsoreducestheimpactofDRTMforrunningefficiency.
UnlikeSRTM,DRTMisabletostartatanytimeandberepeatedanynumberoftimes.
ThereareagreatdifferencebetweenchainoftrustbasedonSRTMandDRTM,thespecificcomparisonasshowninTable2.
Table2.
ComparisonbetweendifferentchainsoftrustDRTM-basedSRTM-basedConfigurationTPM/TCMchipTPM/TCMchip,CPUsupportedspecialinstructionProtectionNospecialhardwareprotectionDisableDMAandinterruptConstructiontimeOnlywhensystempowerupAnytimewhensystemisrunningTrustedcomputingbaseRTM,BIOS,bootsector,OSandupperlayerapplicationSpecialinstructionsinIntelandAMDConclusionSecurityandtrustworthinessofcurrentservicesfocusedonprotectionofmessagelayer,trustedcomputingandsecurityserviceshasnotformedaneffectiveinteraction,italsomakesthecurrentinformationsystemfaceenormouschallenges.
Thispaperdescribestheservicesandsecuritytechnologies,trustedcomputingbase,staticmeasurementtechniquesofprogram,behaviorandsomeprinciplesandtechniquesoftraditionaltrustedcomputing,introducesthelatestdevelopmentoftrustedcomputingtechnology,comparingtheadvantagesanddisadvantagesofvarioustechniques.
References[1]TrustedComputingGroup(TCG).
http://www.
trustedcomput-inggroup.
org.
[2]ModuleTP.
MainSpecification,Level2,Version1.
2,Revision116(2011)[J].
[3]R.
Sailer,X.
Zhang,etal.
DesignandimplementationofaTCG-basedintegritymeasurementarchitecture.
Proceedingsofthe13thUsenixSecuritySymposium,August2004,pp.
223-238.
[4]V.
Haldar,D.
Chandra,etal.
,SemanticRemoteAttestation-VirtualMachineDirectedApproachtoTrustedComputing.
Proc.
ofthe3rdVirtualMachineResearchandTechnologySymposium,2004,pp.
29-41.
[5]R.
Sadeghi,etal.
,Property-basedattestationforcomputingplatforms:caringaboutproperties,notmechanisms.
ProcoftheNewSecurityParadigmsWorkshop,2004,pp.
67-77.
[6]T.
Jaeger,R.
Sailer,etal.
,PRIMA:Policy-ReducedIntegrityMeasurementArchitecture.
Proc.
ofACMSymposiumonAccessControlModelsandTechnologies,2006,pp.
19-28.
[7]ChenL,LandfermannR,LhrH,etal.
Aprotocolforproperty-basedattestation[C]//ProceedingsofthefirstACMworkshoponScalabletrustedcomputing.
ACM,2006:7-16.
[8]YuQin,DengguoFeng.
Remoteattestationbasedoncomponentproperty[J].
JournalofSoftware,2009,20(6):1625-1641.
[9]TCG.
PCclientspecifictpminterfacespecification.
Version1.
2,revision1.
00.
http://www.
trustedcomputinggroup.
org,July2005.
[10]Inteltrustedexecutiontechnologymledevelopersguide.
http://www.
intel.
com/technology.
[11]AMD64virtualization:Securevirtualmachinearchitecturereferencemanual.
AMDPublicationNo.
33047rev.
3.
01,May2005.
[12]ElaineShi,AdrianPerrig,LeendertVanDoorn.
BIND:AFine-grainedAttestationServiceforSecureDistributedSystem.
Proc.
oftheIEEESymposiumonS&P,2005,pp.
154-168.
[13]KauerB.
OSLO:ImprovingthesecurityofTrustedComputing[C]//ProceedingsoftheUSENIXSecuritySymposium.
2007,24(25):173.
[14]McCuneJM,LiY,QuN,etal.
TrustVisor:EfficientTCBreductionandattestation[C]//SecurityandPrivacy(SP),2010IEEESymposiumon.
IEEE,2010:143-158.
24@qq.
com,bemail:bahaihe@hotmail.
com,cemail:wwwrjc@163.
comKeywords:TrustedComputing;IntegrityMeasurement;RemoteAttestationAbstract.
Withtherapiddevelopmentofmoderninformationtechnology,moreandmorepeoplebelievethattheprotectionofhardwareequipmentmustbeenhancedinordertoimprovethesecuritycapabilitiesofcomputerinformationsystemsbetter.
Trustedcomputingimprovethetrustworthinessofsystemthroughthesecurechipfromhardwarelevel,usingthetrustedroot,chainoftrust,trustedmodeltoensuretheintegrityofthesystem,andexpandsthetrustedchaintoapplicationlayer,ensuresthecredibilityofsoftwarethroughmeasurementandverificationtechnology.
Inthispaper,wewillintroducerelatedhotresearchaboutintegritymeasurement.
IntroductionTheideaoftrustedcomputingderivedfromsuccessfulmanagementexperienceinhumansociety,thatis,eachcountryhasastablerootoftrust,andbuildtrustchainsecuritymechanismbasedonit,whichisresponsibleforthemanagementandimplementationofthenationallevelsofassessment.
However,atpresent,hasnotyetformedaunifieddefinitionontrust.
TrustedComputingGroup(TCG)definedatrustedentity'sbehaviorisalwaysintheexpectedway,toachievethedesiredgoal,thencallthisentityistrusted[1,2].
Asystemistrustediftheoperationorprocedureofcomponentsinvolvedinthecomputingispredicableinanyconditions,andcanprotectagainstvirusesandphysicaldisturbance,definedbyInternationalOrganizationforStandardization/InternationalElectroTechnicalCommission(ISO/IEC).
Measurethetrustworthinessofcomputingsystems,andstoremeasurementsecurely;provideattestationreportwhenremoteobjectaskedforsystem'strustworthiness,thismechanismreferredto"Measure-Storage-Report"mechanism.
Thismechanismdoesnotonlyensurethetrustworthinessofthetrustedcomputingsystem,butalsohavetheabilitytoprovidetrustedproofoutward.
Rootoftrustisthebasispointoftrustedcomputersystem,thereare3trustedrootsoftrustedcomputingplatform,whichisRootofTrustforMeasurement(RTM),RootofTrustforStorage(RTS)andRootofTrustforReport(RTR).
Theyarethetrustedbasepointsofcomputersystem,measurementofplatformandstorageofplatformseparately.
AsshowninFig1,chainoftrustreflects"Measure-Storage-Report"mechanismwell,thatis,measurethetrustworthinessofcomputingplatform,storemeasurementvalueandprovideattestationreport.
Chainoftrustisthetechnicalimplementationoftrustmeasurementmodel,toextendtrustrelationshipfromrootoftrusttoentirecomputingplatform.
Usinganiterativecalculationofhashvalue,whichisconnectingpresentvaluewithnewvalue,andthencalculatehashvalueasanewmeasurement.
Aftermeasurementandstorage,providingattestationreportwhentheremoteentityasked.
ThismechanismiscalledRemoteAttestation.
BIOSBootSectorOSBIOSBootBlockApplicationNetworkHardwareROMMainMemoryTrustModelMeasureStoreReportLogRootofTrustRTSRTRFig.
1.
ChainoftrustmodelIntegrityMeasurementbasedonStaticRootofTrustMeasurementApplicationintegritymeasurementandverificationneedtoprovewhetherthetrustworthinessoflocalcomputingsystemisinlinewiththepredictionofbothlocalandremoteauthenticator.
a.
Binary-basedEarlyintegritymeasurementandverificationismainlyaboutintegritymeasurementofbinarycodeimage,softwareconfiguration.
ThatusingTPMsignatureandlogofintegritymeasurementtoprovetheintegritystatusofsoftware.
Thismethodrequiresplatformmorestringent,isnotflexibleenough,therearetwodisadvantages:(1)Privacy.
IntegritymeasurementbasedonbinaryneedsTPMsignature,andcontainschainoftrust,exposingtheconfigurationinformationofplatform,provideabreakthroughtohostiletosomeextent,sothatlocalcomputingsystemismorevulnerabletovariousattacks.
(2)Difficulttoupdate.
Chainoftrustinvolvingmultiplesystemcomponents,theinformationandversiondifferentfromeachother.
Systemupdatelikelytocausetheintegrityinformationisdifficulttoverify.
IBMhasdesignedandimplementedIMA(IntegrityMeasureArchitecture)3basedonTCGspecifications,measureanintegrityintheorderfromrootoftrust,BIOS,bootsector,OStoapplications,progressivemeasureandtrustlevelbylevel.
Thismethodisabletodetectcurrentoperatingstatusofsystem,whichcouldfindpossibletampering.
IMAmeasurementmodulehasbeenusedasapartofLinuxsecuritymechanisms,andarewidelyusedinavarietyofpracticalapplications.
b.
Property-basedToovercometheshortcomingsofbinaryauthentication,Haldarproposedsemanticremoteauthenticationscheme[4],usingatrustedvirtualmachinetoverifycertainsemanticpropertiesofprogram,achievingacomplexanddynamicintegritymeasurementofadvancedapplicationprograminaplatform-independentway;ChenfromHPLabsproposedtheproperty-basedremoteattestation,convertedbinaryattestationtoproperty-basedattestationbyusingthemainfunctionsofTCG,solvedissueslikesensitiveinformationleakageandupdatedifficultycausedbybinarymeasurement,andselectedatrustedthirdpartyastheissuerofproperty-configurationcertificate.
TheauthenticationmethodbasedonpropertyproposedbySadeghietal.
[5]isabletoestablishmappingbetweenpropertiesandplatformconfigurationsbyreportingplatform'sproperties,andestablishingpropertiesbytrustedcertificateauthority.
Binary-basedmeasurementmechanismprovidesbasicprotectionfortheintegrityofsystemsandapplications,butthereisahugeapplicationlimitations,especiallyinthesystemwithmultipleversionsofmodules;property-basedintegritymeasurementcanovercomethelimitationofbinary-basedintegritymeasurement,playaneffectiveroleinthebinaryimagewithsamepropertybutdifferenthashes,thespecificdifferencesisshowninTable1.
Table1.
ComparisonbetweendifferenttypesofintegritymeasurementBinary-basedProperty-basedObjectsExecutablebinarycodePropertyofplatformTypicalSystemsIMA[3],PRIMA[6]PBA[7],CPBA[8]PrivacyMayleakprivacyProtectprivacyEffectsLowefficiencyPracticalandscalableIntegrityMeasurementbasedonDynamicRootofTrustMeasurementThemeasurementaboveisIMAintegritymeasurementarchitecturebasedonStaticRootofTrustMeasurement,measureintegrityonlywhensystemstartup,cannotguaranteetheintegrityoftheprocess.
Tomakeupfortheseshortcomings,TCG1.
2specification[9]definesanewmechanism:verifythestartupprocessbyDynamicRootofTrustMeasurement(DRTM).
Intel'sTXT(TrustExecutionTechnology)[10]andAMD'sSVM(SecureVirtualMachineExtension)[11]arebothusingDRTMasunderlyingtrustmechanism.
ThedynamicestablishingprocessoftrustedenvironmentbasedonDRTMisknownasLateLaunchinTCG1.
2specification,toguaranteeatrustedstartupofavirtualmachinemanager.
BIND[12]proposedbyCarnegieMellonUniversityisfine-grainedsecuritycertificationservicefordistributedsystems,byusingTPM-basedmeasurementandsignaturemechanism,insertameasurepointineachprocessandprotectrunningprocessbyusingsecurekernelbasedonAMDsecurecoprocessor,toachievedynamicmeasurementsoftrustedprocesses.
BernhardKauer[13]analyzedtrustedcomputingsystembasedonStaticRootofTrustMeasurement(SRTM)indetail,pointedoutthesecurityvulnerabilitiesofthisRTM,andproposedasafeopeningloaderOSLO,transferredrootoftrustfromSRTMtoDRTMbyusingAMD'sskinitinstruction,narrowedthetrustedcomputingbaseofapplicationandweakenedtheattacksagainstTPMandBIOS.
CarnegieMellonUniversityCylablaboratorydesignedTrustVisor[14]basedonvirtualmachinemonitor,whichprovidesmemoryisolation,DMAprotectionandseveralvirtualTPMinterfaces(suchasSeal/UnSeal,Extend,Quote,etc.
),asaresult,notonlyprotectsuser'ssecuresensitivecodebutalsoreducestheimpactofDRTMforrunningefficiency.
UnlikeSRTM,DRTMisabletostartatanytimeandberepeatedanynumberoftimes.
ThereareagreatdifferencebetweenchainoftrustbasedonSRTMandDRTM,thespecificcomparisonasshowninTable2.
Table2.
ComparisonbetweendifferentchainsoftrustDRTM-basedSRTM-basedConfigurationTPM/TCMchipTPM/TCMchip,CPUsupportedspecialinstructionProtectionNospecialhardwareprotectionDisableDMAandinterruptConstructiontimeOnlywhensystempowerupAnytimewhensystemisrunningTrustedcomputingbaseRTM,BIOS,bootsector,OSandupperlayerapplicationSpecialinstructionsinIntelandAMDConclusionSecurityandtrustworthinessofcurrentservicesfocusedonprotectionofmessagelayer,trustedcomputingandsecurityserviceshasnotformedaneffectiveinteraction,italsomakesthecurrentinformationsystemfaceenormouschallenges.
Thispaperdescribestheservicesandsecuritytechnologies,trustedcomputingbase,staticmeasurementtechniquesofprogram,behaviorandsomeprinciplesandtechniquesoftraditionaltrustedcomputing,introducesthelatestdevelopmentoftrustedcomputingtechnology,comparingtheadvantagesanddisadvantagesofvarioustechniques.
References[1]TrustedComputingGroup(TCG).
http://www.
trustedcomput-inggroup.
org.
[2]ModuleTP.
MainSpecification,Level2,Version1.
2,Revision116(2011)[J].
[3]R.
Sailer,X.
Zhang,etal.
DesignandimplementationofaTCG-basedintegritymeasurementarchitecture.
Proceedingsofthe13thUsenixSecuritySymposium,August2004,pp.
223-238.
[4]V.
Haldar,D.
Chandra,etal.
,SemanticRemoteAttestation-VirtualMachineDirectedApproachtoTrustedComputing.
Proc.
ofthe3rdVirtualMachineResearchandTechnologySymposium,2004,pp.
29-41.
[5]R.
Sadeghi,etal.
,Property-basedattestationforcomputingplatforms:caringaboutproperties,notmechanisms.
ProcoftheNewSecurityParadigmsWorkshop,2004,pp.
67-77.
[6]T.
Jaeger,R.
Sailer,etal.
,PRIMA:Policy-ReducedIntegrityMeasurementArchitecture.
Proc.
ofACMSymposiumonAccessControlModelsandTechnologies,2006,pp.
19-28.
[7]ChenL,LandfermannR,LhrH,etal.
Aprotocolforproperty-basedattestation[C]//ProceedingsofthefirstACMworkshoponScalabletrustedcomputing.
ACM,2006:7-16.
[8]YuQin,DengguoFeng.
Remoteattestationbasedoncomponentproperty[J].
JournalofSoftware,2009,20(6):1625-1641.
[9]TCG.
PCclientspecifictpminterfacespecification.
Version1.
2,revision1.
00.
http://www.
trustedcomputinggroup.
org,July2005.
[10]Inteltrustedexecutiontechnologymledevelopersguide.
http://www.
intel.
com/technology.
[11]AMD64virtualization:Securevirtualmachinearchitecturereferencemanual.
AMDPublicationNo.
33047rev.
3.
01,May2005.
[12]ElaineShi,AdrianPerrig,LeendertVanDoorn.
BIND:AFine-grainedAttestationServiceforSecureDistributedSystem.
Proc.
oftheIEEESymposiumonS&P,2005,pp.
154-168.
[13]KauerB.
OSLO:ImprovingthesecurityofTrustedComputing[C]//ProceedingsoftheUSENIXSecuritySymposium.
2007,24(25):173.
[14]McCuneJM,LiY,QuN,etal.
TrustVisor:EfficientTCBreductionandattestation[C]//SecurityandPrivacy(SP),2010IEEESymposiumon.
IEEE,2010:143-158.
- Hardware腾讯rom相关文档
- 投标腾讯rom
- rysrc腾讯rom
- 关注"ahsydwks"微信公众号回复"题库"可获得海量习题
- 2014年软件产品登记名单(8月第二批)
- TubeMQ:腾讯开源的万亿级分布式消息中间件
- Xo腾讯rom
Sharktech10Gbps带宽,不限制流量,自带5个IPv4,100G防御
Sharktech荷兰10G带宽的独立服务器月付319美元起,10Gbps共享带宽,不限制流量,自带5个IPv4,免费60Gbps的 DDoS防御,可加到100G防御。CPU内存HDD价格购买地址E3-1270v216G2T$319/月链接E3-1270v516G2T$329/月链接2*E5-2670v232G2T$389/月链接2*E5-2678v364G2T$409/月链接这里我们需要注意,默...
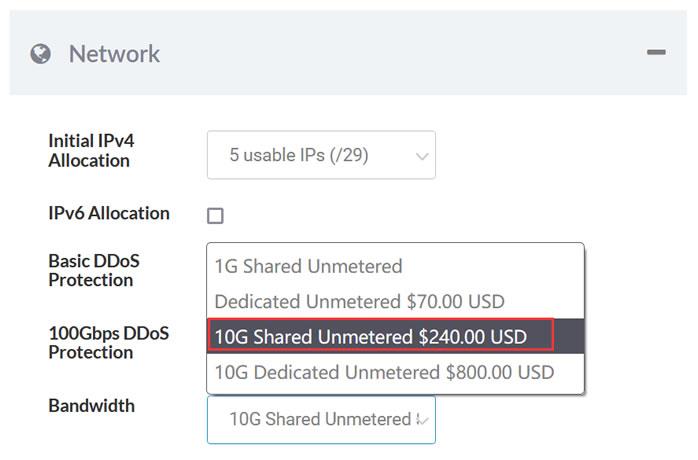
RAKsmart推出7.59美元/月,云服务器产品Cloud Server,KVM架构1核1G内存40G硬盘1M带宽基础配置
近期RAKsmart上线云服务器Cloud Server产品,KVM架构1核1G内存40G硬盘1M带宽基础配置7.59美元/月!RAKsmart云服务器Cloud Server位于美国硅谷机房,下单可选DIY各项配置,VPC网络/经典网络,大陆优化/精品网线路,1-1000Mbps带宽,支持Linux或者Windows操作系统,提供Snap和Backup。RAKsmart机房是一家成立于2012年...
#推荐# cmivps:全场7折,香港不限流量VPS,支持Windows系统
cmivps香港VPS带来了3个新消息:(1)双向流量改为单向流量,相当于流量间接扩大一倍;(2)Hong Kong 2T、Hong Kong 3T、Hong Kong 无限流量,这三款VPS开始支持Windows系统,如果需要中文版Windows系统请下单付款完成之后发ticket要求官方更改即可;(3)全场7折年付、8折月付优惠,优惠码有效期一个月!官方网站:https://www.cmivp...
腾讯rom为你推荐
-
锦天城和君合哪个好和君智业和三人禾哪个公司的营销做的好三国游戏哪个好玩三国游戏 什么最好玩?海克斯皮肤哪个好联盟海克斯科技和抽皮肤哪个合适百度空间登录百度空间怎么登陆q空间登录腾讯qq空间登陆飞信空间登录移动飞信客户端怎么登陆???辽宁联通网上营业厅网联通宽带好不好用辽宁联通营业厅辽宁移动网上营业厅进入办法qq网盘在哪里QQ网盘在哪??????dns服务器设置怎么修改dns服务器