classifiedluxurygoods
luxurygoods 时间:2021-05-24 阅读:()
BrandjackingIndexSpecialEditionLuxuryGoodsContentsExecutiveSummary3KeyFindings3HowFraudstersDriveTrafc5RoguesGallery7Summary9Methodology&Background9Glossary10SpecialEdition-LuxuryGoodsBrandjackingIndexE-commercesitesellingsuspiciousbagsgeneratesmorethanfivemillionvisitsannually3BrandjackingIndex:2010-SpecialEditionExecutiveSummaryEveryonewantsabargain,butwhenitcomestobuyingluxuryhandbagsandotherpremiumgoodsonline,thedealsareoftentoogoodtobetrue.
Giventhelureofthesebrands,however,itisnosurprisethatweb-savvypurveyorsofsuspiciousgoodslureonlineshopperstotheirsites.
Whatissurprising,however,istheamountofonlinetrafficgeneratedbythesescammers:visitstosuspicioussitesnumbernearlyhalfthetrafficgeneratedbythelegitimatedotcomsites.
InthisspecialeditionoftheBrandjackingIndex,welookatonlinebrandabusesintheluxuryconsumergoodssector.
Itisn'taprettypicture,despitethesmoothbutteryleatherexteriorthatmanyoftherealhandbagsoffer.
Tocompleteouranalysis,weexaminedecommercesites,business-to-business(B2B)tradingsitesandpaidsearchadvertisingforfivespecificluxurygoodsbrandsfrommajorEuropeandesignhouses.
KeyFindingsWefoundthatpurveyorsofsuspectedcounterfeitgoodsareveryvisibleacrosstheInternet,andtheyarealsoverygoodatgeneratingtraffic.
Throughvarioussearchenginemarketingtechniques,thebadguysattractatleast120millionvisitorsannuallytotheirecommercesites.
Thisfigurerepresentsalmosthalfthetrafficattractedbythelegitimatedotcomsitesforthosebrands.
Aswithotherindustriesthatwehaveexamined,wefoundthatcybersquatting—themisleadingpracticeofincludingabrandnamewithinthedomainnameit-self—ispopularintheluxurysector.
Weidentifiedmorethan1,200websitesthatcontainoneofthefiveluxurybrandsinourstudy.
Noneofthosewebsiteshadanyrightstothatbrand,and,thus,hadnorighttousethebrandinthedomainname.
Therearethousandsmoredomainnamesthatdon'tcontainanybrandnamesbutpurporttobelegitimateonlinelocationssellingrealgoods.
However,thesesites,too,arestockedfullofsuspiciousgoods.
Onesite,handbagcom.
com,sellsnothingbuthandbagsofsuspiciousprovenance.
""Sellersofsuspectedfakesareadeptatdrivingwebtraffic.
Suspiciousgoodsonline,studyoffiveluxurybrands4BrandjackingIndex:2010-SpecialEditionSearchengineadvertisingisanotherimportantinvestmentthatgeneratestraffictothesesitesandtheadvertisersdon'talways'playbytherules'.
Weidenti-fiedmorethan50differentvendorswhopurchasedkeywordsinvolvingthefivebrandnamesinourstudy.
Usingbrandedkeywordstodrivetraffictositesofferingcounterfeitorpiratedgoodsisagainsttherulesateachofthe'bigthree'searchengines.
However,thesearchenginesdonotpreventormonitorthistypeofbe-havior.
Instead,thebrandmustinitiateactionwiththesearchenginestoremovetheoffendingads.
Questionablequalityisn'tlimitedtotheretailsector,either.
Whenitcomestothewholesalesupplychain,wefoundalmost4,000sellersofsuspiciousgoodsonbusiness-to-business(B2B)exchangesitesforjustthesefivebrandnames.
Thesesellersgeneratedalmost12,000listingsforsuspiciousgoodson12B2Bexchangesandoftenadvertisetheabilitytosupplyuptothousands—andsome-timesmillions—ofpiecesperyear.
TheaveragesellingpriceontheB2Bexchang-esforthesegoodsisalittlemorethan$100,oronaverage80%belowtheretailpricesofgenuinemerchandise.
Inadditiontothee-commercesitesandB2Bexchanges,weidentifiedmorethan1,400suspectcounterfeitsellerson10business-to-consumer(B2C)exchanges,includingauctionsitesandclassifiedadsites.
Thesesellersgeneratedalmost3,600additionallistings.
Thedistributionofthesesellersistrulyglobalaswell,with55%ofthesellerslocatedinNorthAmerica,29%inAsiaPacificand16%throughoutEurope.
TheaveragesellingpriceforthesegoodsacrossallB2Csitesisalittlemorethan$300,oronaverage,45%belowtheretailpricesoftherealmerchandise.
Asummaryofourfindingsisshownbelow.
""Suspicioussitesgeneratedalmosthalfthetrafficoflegitimatesites.
Commonwayscustomersfindbrandsviasearch""Suspectedcounter-feiterssiphonactualprospectsawayfrom'therealdeal'.
5BrandjackingIndex:2010-SpecialEditionHowFraudstersDriveTrafficTheoperatorsofthesesitesaresophisticated,andusethesamepromotionalmethodsthatlegitimateonlinemarketersusetoattractvisitors.
Threeofthemostcommonmethodsusedtofindwebsitesare:Directnavigation,typingthedomainnameintothebrowser.
Organicsearch,selectingasitefromthenaturalsearchresultsorsearchengineresultspage(SERP);searchengineoptimization(SEO)isakeytechniqueusedbylegitimatesitestoincreasetheirplacementontheSERP.
Paidsearchads,selectingasitefromasponsoredadshownontheSERPasaresultoftheadvertiserpurchasingkeywordstogeneraterelevantads.
Howfraudstersstealsearchtraffic""Legitimateluxurymarketersarecom-petingwithsuspect-edcounterfeitersforwebtraffic.
6BrandjackingIndex:2010-SpecialEditionFraudstersexploitthesemethodsbytakingadvantageoflegitimatebrandnamesandinteractivemarketingtechniquestostealtraffic:Cybersquatting,thepracticeofabusingtrademarkswithinthedomainnamesystem.
Scammersregisterdomainnamesthatincludewell-knownbrands,suchas"guccioutlet.
com",andintercepttrafficsearchingforthelegitimatebrand.
BlackhatSEO,acollectionoftechniques,includingcybersquatting,toincreasesiterankings.
Additionaltechniquesincludeusingtheactualbrandinpagetitlesandmetatagsaswellashavingalargenumberofinboundlinks.
Thesetechniquesaredesignedtotrickthesearchenginesintothinkingsitesarelegitimateattheexpenseoftheactualbrandedsite.
Paidsearchscams,thepracticeofbuyingbrandedkeywordstogenerateadsforsitesofferingsuspectedcounterfeitgoods.
Thispracticeinterceptstrafficmeantforthelegitimatesitesanddrivesupthecostforpurchasingbrandedkeywordsfortherightfulbrandoraffiliatedresellers.
Cybersquattedsitesellscompetitivebrands,tooPaidsearchscamexploitingapopularluxurybrand7BrandjackingIndex:2010-SpecialEditionAsearchforseasonalsalesofaleadingluxurybrandgeneratedaclearexampleofapaidsearchscam,withthefollowingadontheSERP.
Theadinturnledtoacybersquattedsitesellingsuspectedcounterfeitgoods.
RoguesGalleryThesesitesappearprofessionallyproducedandgenerateappreciabletraffic.
Thisexampleofasitewithacybersquattednamesellssuspiciousqualitygoodsfromawidevarietyofluxurylabels.
Thesitegeneratesvisitsinexcessof400,000peryear.
BlackhatSEOtechniquesdrivesubstantialtrafficattheexpenseofthelegitimatebrandBulkmanufacturersofsuspiciousgoodsuseB2Bexchangesitestopromotetheirbusiness8BrandjackingIndex:2010-SpecialEditionInthisexample,blackhatSEOtechniquesdrivesignificanttraffic,withthesiteattracting3.
3millionvisitsannually.
Thissiteusesacombinationoftechniques—cybersquatting,includingthebrandnameinthemetatagsandpagetitle,aswellaslargenumbersofinboundlinks.
Thesetechniquespropelthesitetoanumberonepositioninorganicsearchfortheterm'LouisVuittononsale'.
Bulkmanufacturersofquestionable-qualitybrandedgoodsaresimilarlyadeptatshowcasingtheircapabilities.
ThisB2Bexchangesitelistingclaimsthemanufacturercansupplymorethan52,000unitsannuallyfor$10to$15periteminlotsofuptoathousandpieces.
9BrandjackingIndex:2010-SpecialEditionSummaryTheamountoftrafficflowingtositesofferingsuspiciousluxurygoodsisstartlingandspeaksasmuchtoconsumerdemandasitdoestotheinteractivemarketingsavvyofsiteoperators.
Whileit'sdebatablethatthepersonwhopurchasesa$100fakehandbagisanactualcustomerfortherealitem,thefactthatsuspicioussitespromotingthesefiveluxurybrandsgeneratemorethan120millionvisitsannuallyindicatesthatactualprospectsarebeingsiphonedawayfrom'therealdeal'bysuspectedcounterfeiters.
Ifeven10%ofthosevisitsrepresentvalidcustomerprospectsforluxuryproducts,then12millionvisitsperyeararebeingledawayfromtheirdesireddestination—andinteractivemarketersintheluxurysegmentarepayingthepriceinlostsales.
Tomakemattersworse,thelegitimateluxurymarketersarecompetingagainstcounterfeiterstopurchasetheirownbrandsaskeywords,drivingupthecostsoflegitimateonlinemarketingcampaignsandimpact-ingcampaignmetricsandROI.
Astheluxurysegment—andluxurybuyers—continuetoembracetheInternet,it'svitalthattheindustrytakesaimatonlinecounterfeiters,paidsearchscamsandotherformsofonlinebrandabuseinordertoreapthefullestreturnfromtheirpreciousbrandsandcarefullycultivatedimages.
MethodologyandBackgroundTheBrandjackingIndexisproducedbyMarkMonitorandanalyzestrendsandstatisticsaboutbrandabuseonlineaswellasanecdotalinformationaboutthebusinessandtechnicalmethodsusedbybrandjackers.
ThecornerstoneoftheBrandjackingIndexisthevolumeofpublicdataanalyzedbyMarkMonitorusingthecompany'sproprietaryalgorithms.
Noneofthisdatacontainsproprietarycustomerinformation.
ThisspecialeditionoftheBrandjackingIndexdrewconclusionsbasedondatafrommajorsearchengines,onlinemarketplaces,WhoisrecordsandAlexatrafficestimates.
10BrandjackingIndex:2010-SpecialEditionGlossaryBrandjacking–Tohijackabrandtodeceiveordivertattention;oftenusedinabusiveorfraudulentactivitiesdevisedforgainattheexpenseofthegoodwill,brandequityandcustomertrustofactualbrandowners.
BlackHatSEO–Theuseofbrands,slogansortrademarkslocatedinvisibletext,hiddentext,metatagsandtitleinordertomanipulatesearchenginerankingssothatthebrandjacker'ssitecangainamorefavorablesearchengineplacement.
Cybersquatting–Thepracticeofabusingtrademarkswithinthedomainnamesystem.
DomainKiting–Theprocesswherebydomainsareregisteredanddroppedwithinthefive-dayICANNgraceperiod,andthenregisteredagainforanotherfivedays.
Kitingadomainletstheregistrantgainthebenefitofownershipwithouteverpayingforthedomain.
eCommerceContent–Websitescontainingaspecifiedbrandthatappearsinvisibletext,hiddentext,metatagsortitleinconjunctionwithothersitecontentthatindicatesonlinesalesarebeingtransactedonthesite.
FalseAssociation–Thepracticeofusingaspecifiedbrandortrademarkinwebcontenttoimplyarelationshipwithacompanyorbrandwherenoneexists.
OffensiveContent–Websitescontainingaspecifiedbrandthatappearsinvisibletext,hiddentext,metatagsortitleinconjunctionwithpornographic,onlinegamingorhatecontent.
PaidSearchScams–Occurwhenabrandisusedwithoutpermission,withinapaidsearchscenariotodrivewebtraffictoacompetitiveorillicitsite.
Phishing–Criminaluseofemailtodiverttraffictowebsitesinordertofraudulentlyacquireusernames,passwords,creditcarddetailsandotherpersonalinformation.
Theemailandwebsitesusedintheseoperationsemploy"socialengineering"techniquestotrickusersintobelievingtheyareinteractingwithabusinessororganizationthattheytrust.
RockPhishing–Amethodofphishingfirstimplementedbythe'rock'phishgangthatutilizesmultiplelayersofredundantinfrastructuretoincreasethedifficultyofshuttingdowntheattack.
Otherphishersarenowusingthesetacticsaswell.
AboutMarkMonitorMarkMonitor,thegloballeaderinenterprisebrandprotection,offerscomprehensivesolutionsandservicesthatsafeguardbrands,reputationandrevenuefromonlinerisks.
Withend-to-endsolutionsthataddressthegrowingthreatsofonlinefraud,brandabuseandunauthorizedchannels,MarkMonitorenablesasecureInternetforbusinessesandtheircustomers.
Thecompany'sexclusiveaccesstodatacombinedwithitspatentedreal-timeprevention,detectionandresponsecapabilitiesprovidewide-rangingprotectiontotheever-changingonlinerisksfacedbybrandstoday.
Formoreinformation,pleasevisitwww.
markmonitor.
com.
MorethanhalftheFortune100trustMarkMonitortoprotecttheirbrandsonline.
Seewhatwecandoforyou.
MarkMonitor,Inc.
U.
S.
(800)745-9229Europe:+44(0)2078401300www.
markmonitor.
com2010MarkMonitorInc.
Allrightsreserved.
MarkMonitorandBrandjackingIndexareregisteredtrademarksofMarkMonitorInc.
Allothertrademarksincludedhereinarethepropertyoftheirrespectiveowners.
Boise|SanFrancisco|WashingtonD.
C.
|NewYork|London|Frankfurt
Giventhelureofthesebrands,however,itisnosurprisethatweb-savvypurveyorsofsuspiciousgoodslureonlineshopperstotheirsites.
Whatissurprising,however,istheamountofonlinetrafficgeneratedbythesescammers:visitstosuspicioussitesnumbernearlyhalfthetrafficgeneratedbythelegitimatedotcomsites.
InthisspecialeditionoftheBrandjackingIndex,welookatonlinebrandabusesintheluxuryconsumergoodssector.
Itisn'taprettypicture,despitethesmoothbutteryleatherexteriorthatmanyoftherealhandbagsoffer.
Tocompleteouranalysis,weexaminedecommercesites,business-to-business(B2B)tradingsitesandpaidsearchadvertisingforfivespecificluxurygoodsbrandsfrommajorEuropeandesignhouses.
KeyFindingsWefoundthatpurveyorsofsuspectedcounterfeitgoodsareveryvisibleacrosstheInternet,andtheyarealsoverygoodatgeneratingtraffic.
Throughvarioussearchenginemarketingtechniques,thebadguysattractatleast120millionvisitorsannuallytotheirecommercesites.
Thisfigurerepresentsalmosthalfthetrafficattractedbythelegitimatedotcomsitesforthosebrands.
Aswithotherindustriesthatwehaveexamined,wefoundthatcybersquatting—themisleadingpracticeofincludingabrandnamewithinthedomainnameit-self—ispopularintheluxurysector.
Weidentifiedmorethan1,200websitesthatcontainoneofthefiveluxurybrandsinourstudy.
Noneofthosewebsiteshadanyrightstothatbrand,and,thus,hadnorighttousethebrandinthedomainname.
Therearethousandsmoredomainnamesthatdon'tcontainanybrandnamesbutpurporttobelegitimateonlinelocationssellingrealgoods.
However,thesesites,too,arestockedfullofsuspiciousgoods.
Onesite,handbagcom.
com,sellsnothingbuthandbagsofsuspiciousprovenance.
""Sellersofsuspectedfakesareadeptatdrivingwebtraffic.
Suspiciousgoodsonline,studyoffiveluxurybrands4BrandjackingIndex:2010-SpecialEditionSearchengineadvertisingisanotherimportantinvestmentthatgeneratestraffictothesesitesandtheadvertisersdon'talways'playbytherules'.
Weidenti-fiedmorethan50differentvendorswhopurchasedkeywordsinvolvingthefivebrandnamesinourstudy.
Usingbrandedkeywordstodrivetraffictositesofferingcounterfeitorpiratedgoodsisagainsttherulesateachofthe'bigthree'searchengines.
However,thesearchenginesdonotpreventormonitorthistypeofbe-havior.
Instead,thebrandmustinitiateactionwiththesearchenginestoremovetheoffendingads.
Questionablequalityisn'tlimitedtotheretailsector,either.
Whenitcomestothewholesalesupplychain,wefoundalmost4,000sellersofsuspiciousgoodsonbusiness-to-business(B2B)exchangesitesforjustthesefivebrandnames.
Thesesellersgeneratedalmost12,000listingsforsuspiciousgoodson12B2Bexchangesandoftenadvertisetheabilitytosupplyuptothousands—andsome-timesmillions—ofpiecesperyear.
TheaveragesellingpriceontheB2Bexchang-esforthesegoodsisalittlemorethan$100,oronaverage80%belowtheretailpricesofgenuinemerchandise.
Inadditiontothee-commercesitesandB2Bexchanges,weidentifiedmorethan1,400suspectcounterfeitsellerson10business-to-consumer(B2C)exchanges,includingauctionsitesandclassifiedadsites.
Thesesellersgeneratedalmost3,600additionallistings.
Thedistributionofthesesellersistrulyglobalaswell,with55%ofthesellerslocatedinNorthAmerica,29%inAsiaPacificand16%throughoutEurope.
TheaveragesellingpriceforthesegoodsacrossallB2Csitesisalittlemorethan$300,oronaverage,45%belowtheretailpricesoftherealmerchandise.
Asummaryofourfindingsisshownbelow.
""Suspicioussitesgeneratedalmosthalfthetrafficoflegitimatesites.
Commonwayscustomersfindbrandsviasearch""Suspectedcounter-feiterssiphonactualprospectsawayfrom'therealdeal'.
5BrandjackingIndex:2010-SpecialEditionHowFraudstersDriveTrafficTheoperatorsofthesesitesaresophisticated,andusethesamepromotionalmethodsthatlegitimateonlinemarketersusetoattractvisitors.
Threeofthemostcommonmethodsusedtofindwebsitesare:Directnavigation,typingthedomainnameintothebrowser.
Organicsearch,selectingasitefromthenaturalsearchresultsorsearchengineresultspage(SERP);searchengineoptimization(SEO)isakeytechniqueusedbylegitimatesitestoincreasetheirplacementontheSERP.
Paidsearchads,selectingasitefromasponsoredadshownontheSERPasaresultoftheadvertiserpurchasingkeywordstogeneraterelevantads.
Howfraudstersstealsearchtraffic""Legitimateluxurymarketersarecom-petingwithsuspect-edcounterfeitersforwebtraffic.
6BrandjackingIndex:2010-SpecialEditionFraudstersexploitthesemethodsbytakingadvantageoflegitimatebrandnamesandinteractivemarketingtechniquestostealtraffic:Cybersquatting,thepracticeofabusingtrademarkswithinthedomainnamesystem.
Scammersregisterdomainnamesthatincludewell-knownbrands,suchas"guccioutlet.
com",andintercepttrafficsearchingforthelegitimatebrand.
BlackhatSEO,acollectionoftechniques,includingcybersquatting,toincreasesiterankings.
Additionaltechniquesincludeusingtheactualbrandinpagetitlesandmetatagsaswellashavingalargenumberofinboundlinks.
Thesetechniquesaredesignedtotrickthesearchenginesintothinkingsitesarelegitimateattheexpenseoftheactualbrandedsite.
Paidsearchscams,thepracticeofbuyingbrandedkeywordstogenerateadsforsitesofferingsuspectedcounterfeitgoods.
Thispracticeinterceptstrafficmeantforthelegitimatesitesanddrivesupthecostforpurchasingbrandedkeywordsfortherightfulbrandoraffiliatedresellers.
Cybersquattedsitesellscompetitivebrands,tooPaidsearchscamexploitingapopularluxurybrand7BrandjackingIndex:2010-SpecialEditionAsearchforseasonalsalesofaleadingluxurybrandgeneratedaclearexampleofapaidsearchscam,withthefollowingadontheSERP.
Theadinturnledtoacybersquattedsitesellingsuspectedcounterfeitgoods.
RoguesGalleryThesesitesappearprofessionallyproducedandgenerateappreciabletraffic.
Thisexampleofasitewithacybersquattednamesellssuspiciousqualitygoodsfromawidevarietyofluxurylabels.
Thesitegeneratesvisitsinexcessof400,000peryear.
BlackhatSEOtechniquesdrivesubstantialtrafficattheexpenseofthelegitimatebrandBulkmanufacturersofsuspiciousgoodsuseB2Bexchangesitestopromotetheirbusiness8BrandjackingIndex:2010-SpecialEditionInthisexample,blackhatSEOtechniquesdrivesignificanttraffic,withthesiteattracting3.
3millionvisitsannually.
Thissiteusesacombinationoftechniques—cybersquatting,includingthebrandnameinthemetatagsandpagetitle,aswellaslargenumbersofinboundlinks.
Thesetechniquespropelthesitetoanumberonepositioninorganicsearchfortheterm'LouisVuittononsale'.
Bulkmanufacturersofquestionable-qualitybrandedgoodsaresimilarlyadeptatshowcasingtheircapabilities.
ThisB2Bexchangesitelistingclaimsthemanufacturercansupplymorethan52,000unitsannuallyfor$10to$15periteminlotsofuptoathousandpieces.
9BrandjackingIndex:2010-SpecialEditionSummaryTheamountoftrafficflowingtositesofferingsuspiciousluxurygoodsisstartlingandspeaksasmuchtoconsumerdemandasitdoestotheinteractivemarketingsavvyofsiteoperators.
Whileit'sdebatablethatthepersonwhopurchasesa$100fakehandbagisanactualcustomerfortherealitem,thefactthatsuspicioussitespromotingthesefiveluxurybrandsgeneratemorethan120millionvisitsannuallyindicatesthatactualprospectsarebeingsiphonedawayfrom'therealdeal'bysuspectedcounterfeiters.
Ifeven10%ofthosevisitsrepresentvalidcustomerprospectsforluxuryproducts,then12millionvisitsperyeararebeingledawayfromtheirdesireddestination—andinteractivemarketersintheluxurysegmentarepayingthepriceinlostsales.
Tomakemattersworse,thelegitimateluxurymarketersarecompetingagainstcounterfeiterstopurchasetheirownbrandsaskeywords,drivingupthecostsoflegitimateonlinemarketingcampaignsandimpact-ingcampaignmetricsandROI.
Astheluxurysegment—andluxurybuyers—continuetoembracetheInternet,it'svitalthattheindustrytakesaimatonlinecounterfeiters,paidsearchscamsandotherformsofonlinebrandabuseinordertoreapthefullestreturnfromtheirpreciousbrandsandcarefullycultivatedimages.
MethodologyandBackgroundTheBrandjackingIndexisproducedbyMarkMonitorandanalyzestrendsandstatisticsaboutbrandabuseonlineaswellasanecdotalinformationaboutthebusinessandtechnicalmethodsusedbybrandjackers.
ThecornerstoneoftheBrandjackingIndexisthevolumeofpublicdataanalyzedbyMarkMonitorusingthecompany'sproprietaryalgorithms.
Noneofthisdatacontainsproprietarycustomerinformation.
ThisspecialeditionoftheBrandjackingIndexdrewconclusionsbasedondatafrommajorsearchengines,onlinemarketplaces,WhoisrecordsandAlexatrafficestimates.
10BrandjackingIndex:2010-SpecialEditionGlossaryBrandjacking–Tohijackabrandtodeceiveordivertattention;oftenusedinabusiveorfraudulentactivitiesdevisedforgainattheexpenseofthegoodwill,brandequityandcustomertrustofactualbrandowners.
BlackHatSEO–Theuseofbrands,slogansortrademarkslocatedinvisibletext,hiddentext,metatagsandtitleinordertomanipulatesearchenginerankingssothatthebrandjacker'ssitecangainamorefavorablesearchengineplacement.
Cybersquatting–Thepracticeofabusingtrademarkswithinthedomainnamesystem.
DomainKiting–Theprocesswherebydomainsareregisteredanddroppedwithinthefive-dayICANNgraceperiod,andthenregisteredagainforanotherfivedays.
Kitingadomainletstheregistrantgainthebenefitofownershipwithouteverpayingforthedomain.
eCommerceContent–Websitescontainingaspecifiedbrandthatappearsinvisibletext,hiddentext,metatagsortitleinconjunctionwithothersitecontentthatindicatesonlinesalesarebeingtransactedonthesite.
FalseAssociation–Thepracticeofusingaspecifiedbrandortrademarkinwebcontenttoimplyarelationshipwithacompanyorbrandwherenoneexists.
OffensiveContent–Websitescontainingaspecifiedbrandthatappearsinvisibletext,hiddentext,metatagsortitleinconjunctionwithpornographic,onlinegamingorhatecontent.
PaidSearchScams–Occurwhenabrandisusedwithoutpermission,withinapaidsearchscenariotodrivewebtraffictoacompetitiveorillicitsite.
Phishing–Criminaluseofemailtodiverttraffictowebsitesinordertofraudulentlyacquireusernames,passwords,creditcarddetailsandotherpersonalinformation.
Theemailandwebsitesusedintheseoperationsemploy"socialengineering"techniquestotrickusersintobelievingtheyareinteractingwithabusinessororganizationthattheytrust.
RockPhishing–Amethodofphishingfirstimplementedbythe'rock'phishgangthatutilizesmultiplelayersofredundantinfrastructuretoincreasethedifficultyofshuttingdowntheattack.
Otherphishersarenowusingthesetacticsaswell.
AboutMarkMonitorMarkMonitor,thegloballeaderinenterprisebrandprotection,offerscomprehensivesolutionsandservicesthatsafeguardbrands,reputationandrevenuefromonlinerisks.
Withend-to-endsolutionsthataddressthegrowingthreatsofonlinefraud,brandabuseandunauthorizedchannels,MarkMonitorenablesasecureInternetforbusinessesandtheircustomers.
Thecompany'sexclusiveaccesstodatacombinedwithitspatentedreal-timeprevention,detectionandresponsecapabilitiesprovidewide-rangingprotectiontotheever-changingonlinerisksfacedbybrandstoday.
Formoreinformation,pleasevisitwww.
markmonitor.
com.
MorethanhalftheFortune100trustMarkMonitortoprotecttheirbrandsonline.
Seewhatwecandoforyou.
MarkMonitor,Inc.
U.
S.
(800)745-9229Europe:+44(0)2078401300www.
markmonitor.
com2010MarkMonitorInc.
Allrightsreserved.
MarkMonitorandBrandjackingIndexareregisteredtrademarksofMarkMonitorInc.
Allothertrademarksincludedhereinarethepropertyoftheirrespectiveowners.
Boise|SanFrancisco|WashingtonD.
C.
|NewYork|London|Frankfurt
- classifiedluxurygoods相关文档
- 炫耀luxurygoods
- violenceluxurygoods
- 讲座luxurygoods
- riseluxurygoods
- Indaudaluxurygoods
- quotedluxurygoods
咖啡主机22元/月起,美国洛杉矶弹性轻量云主机仅13元/月起,高防云20G防御仅18元/月
咖啡主机怎么样?咖啡主机是一家国人主机销售商,成立于2016年8月,之前云服务器网已经多次分享过他家的云服务器产品了,商家主要销售香港、洛杉矶等地的VPS产品,Cera机房 三网直连去程 回程CUVIP优化 本产品并非原生地区本土IP,线路方面都有CN2直连国内,机器比较稳定。咖啡主机目前推出美国洛杉矶弹性轻量云主机仅13元/月起,高防云20G防御仅18元/月;香港弹性云服务器,香港HKBN CN...

FBICDN,0.1元解决伪墙/假墙攻击,超500 Gbps DDos 防御,每天免费流量高达100G,免费高防网站加速服务
最近很多网站都遭受到了伪墙/假墙攻击,导致网站流量大跌,间歇性打不开网站。这是一种新型的攻击方式,攻击者利用GWF规则漏洞,使用国内服务器绑定host的方式来触发GWF的自动过滤机制,造成GWF暂时性屏蔽你的网站和服务器IP(大概15分钟左右),使你的网站在国内无法打开,如果攻击请求不断,那么你的网站就会是一个一直无法正常访问的状态。常规解决办法:1,快速备案后使用国内服务器,2,使用国内免备案服...
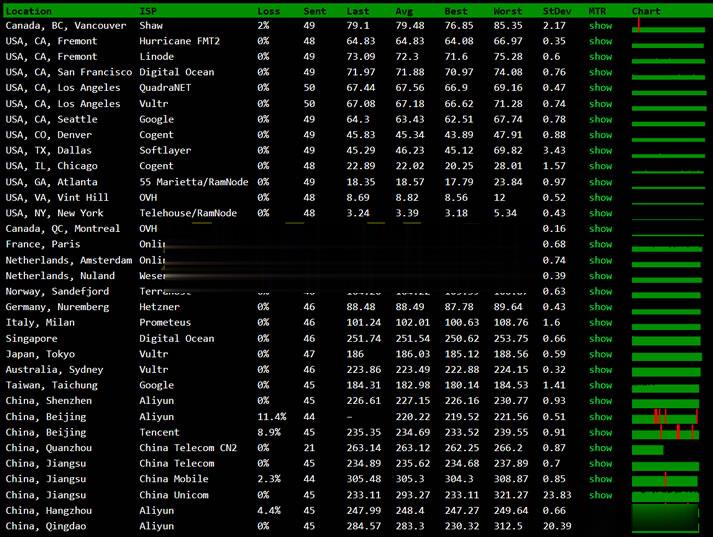
BuyVM商家4个机房的官方测试IP地址和测速文件
BuyVM 商家算是有一些年头,从早年提供低价便宜VPS主机深受广大网友抢购且也遭到吐槽的是因为审核账户太过于严格。毕竟我们国内的个人注册账户喜欢账户资料乱写,毕竟我们看英文信息有些还是比较难以识别的,于是就注册信息的时候随便打一些字符,这些是不能通过的。前几天,我们可以看到BUYVM商家有新增加迈阿密机房,而且商家有提供大硬盘且不限制流量的VPS主机,深受有一些网友的喜欢。目前,BUYVM商家有...
luxurygoods为你推荐
-
psbAchrome路由器itunes支持ipadipad上网ipad上网速度很慢怎么回事?win7telnetwindows7的TELNET服务在哪里开启啊fusionchartsfusioncharts怎么生成图片至excel联通iphone4联通iphone4合约win7关闭135端口win7系统怎么关闭135端口?网上很多方法都不好用!csshackcss常见的hack方法有哪些bitchina《绝对计划》蓝野明写的 我们的曲子 谁有啊?录音也行呵 谢谢啦!~~