DASpastebin
pastebin 时间:2021-04-04 阅读:()
YARA:AnIntroductionJune25,2014BostonAndreasSchusterImportantRemarks-Readthisfirst!
Thishands-ontutorialwillcoveradvancedtopics.
IfyoustillhavetowriteyourfirstYARArule,thistutorialwillnotbehelpfulatall.
Thisslidedeckissplitintwoparts:Thefirstpartcoverssomebasicconcepts.
YoushouldalreadyhavewrittensomeYARArulesonyourownandappliedsomeofthesetechniquesanumberoftimesbeforecomingtoclass.
However,thevirtualmachineimage(seebelow)includesthematerialsforthebasicexercises,too,soyoucanworkonthematyourownpace.
Thesecondpart,startingfromtheAdvancedTopics"tileslide,willbecoveredinourtutorial.
PleasedownloadtheVMwareimagefromhttp://r.
forens.
is/bos1st/.
Ensureyourenvironmentworksproperlybeforecomingtoclass.
LogisticsAgendaMorningsessionWritingYARArulesBuildingrulesbasedonmagicnumbersMemoryanalysiswithVolatilityandYARAIntroductionIntroductionWhatisYARAThepatternmatchingswissknifeformalwareresearchers(andeveryoneelse)"HostedonGitGubhttp://plusvic.
github.
io/yara/Patternmatching:strings(ASCII,UCS-2)regularexpressionsbinarypatterns(hexstrings)Classification:oninput:combinationofstringsonoutput:tags,metadataIntroductionWhatisYARArulemy_example:tag1tag2tag3{meta:description="Thisisjustanexample"thread_level=3in_the_wild=truestrings:$a={6A4068003000006A148D91}$b=/[0-9a-f]{32}/$c="UVODFRYSIHLNWPEJXQZAKCBGMT"condition:$aor($band$c)}IntroductionWhatYARAisNOTNotavirusscannerNotacorrelationengineNotabayesianclassifierNoartificalintelligence(AI)involvedIntroductionHowcanYARAhelpmeAbettergrep"Usecases:Findinginterestingentriesonpastebin.
com.
.
.
TriagedataPreprocessfilestodirectreverseengineeringeffortsIntegrateitintoyourprojects:ClibraryPythonbindingshttps://github.
com/plusvic/yara/tree/master/yara-pythonRubybindingshttps://github.
com/SpiderLabs/yara-rubyIntroductionHowcanYARAhelpmeYARArulesaresupportedbysecurityproductsandservicesFireEyeappliancesFidelisXPSRSAECATVolatilityThreadConnectthreatintelligenceexchangeVirusTotalIntelligence.
.
.
WritingYARARulesHelloWorld!
YourFirstYARARuleYourfirstYARAruleStartingtheVMStartVMLoginasusertraining",passwordistraining"training"alsoisyoursudopasswordYoumaywanttocustomizethekeyboardlayout:System>Preferences>KeyboardSelectLayouts"tabOpenaterminalwindowYourfirstYARAruleGettinghelp$yarausage:yara[OPTION].
.
.
[RULEFILE].
.
.
FILEoptions:-tprintrulestaggedasandignoretherest.
Canbeusedmorethanonce.
-iprintrulesnamedandignoretherest.
Canbeusedmorethanonce.
-nprintonlynotsatisfiedrules(negate).
-gprinttags.
-mprintmetadata.
-sprintmatchingstrings.
-d=defineexternalvariable.
-rrecursivelysearchdirectories.
-ffastmatchingmode.
-vshowversioninformation.
YourfirstYARAruleChecktheinstalledversionThereareslightdifferencesbetweenYARAversions1.
4to1.
7and2.
0,seehttp://code.
google.
com/p/yara-project/source/browse/trunk/ChangeLogandhttps://github.
com/plusvic/yara/commits/masterfordetailsUsermanualisin/yara/docofthisVMWhatversiondoestheVMprovide$yara-vYoushouldseetheresult:yara1.
6YourfirstYARAruleEditorsThefollowingeditorsareavailable:vim(withsimplesyntaxhighlighting)gvim(withGUIandsyntaxhighlighting)emacsgeditYourfirstYARAruleAminimalistrulecd/yara/Lab_1Createafilenamedhello.
yara"withthefollowingcontents:ruleHello_World{condition:true}Nowletthecomputergreetyou:$yarahello.
yara/yara/malware/somefile.
txtYourfirstYARArulePassingexternaldatatoYARAReviewthefilegreeting.
yararuleGoodMorning{condition:hour=4}Nowpassdifferentvaluesforhour"totheruleset:$yara-dhour=8greeting.
yara/yara/malware/somefile.
txtGoodMorning/yara/files/somefile.
txt$yara-dhour=20greeting.
yara/yara/malware/somefile.
txtGoodEvening/yara/files/somefile.
txtWhathappenswhenyoupassastring(e.
g.
noon")ornovalueatallIdentifyExecutableFilesIdentifyexecutablefilesAsimplespecificationforPEfilesTask:TofindanyfilesinPortableExecutable(PE")formatSimplespecification:FilemustcontainthestringsMZ"andPE"000000004d5a90000300000004000000ffff0000|MZ.
00000010b8000000000000004000000000000000000000200000000000000000000000000000000000000030000000000000000000000000c8000000000000400e1fba0e00b409cd21b8014ccd215468L.
!
Th|0000005069732070726f6772616d2063616e6e6f|isprogramcanno|00000060742062652072756e20696e20444f5320|tberuninDOS|000000706d6f64652e0d0d0a2400000000000000|mode.
0000008065cd43c721ac2d9421ac2d9421ac2d94|e.
C.
0000009021ac2c9425ac2d94e2a3709424ac2d94p.
$.
-.
|000000a0c9b3269423ac2d945269636821ac2d94Rich!
.
-.
|000000b000000000000000000000000000000000000000c00000000000000000504500004c010300PE.
.
L.
.
.
|IdentifyexecutablefilesRuleskeletoncd/yara/Lab_2Createanewfile,namedexecutable.
yara"Startwithablankrule:rulePE_file{}IdentifyexecutablefilesAddingstringsNowaddthetwostrings:rulePE_file{strings:$mz="MZ"$pe="PE"}Note:Stringsarecase-sensitivebydefault!
IdentifyexecutablefilesAddingtheconditionAportableexecutablefileMUSTcontainbothstrings.
So,addthepropercondition:rulePE_file{strings:$mz="MZ"$pe="PE"condition:$mzand$pe}Testyourrulefile:$yara-rexecutable.
yara/yara/malwareIdentifyexecutablefilesRefiningtheconditionMoreconstraints:MZ"atoffset0UInt32atoffset0x3cpointstoPE"Refineyourconditionsection:condition:($mzat0)and($peat(uint32(0x3c)))Testyourrulefileagain:$yara-rexecutable.
yara/yara/malwareIdentifyexecutablefilesThefinalruleThisishowyourruleshouldlooklike:rulePE_file{!
strings:!
!
$mz="MZ"!
!
$pe="PE"!
condition:!
!
($mzat0)and!
!
($peat(uint32(0x3c)))}Obfuscation:MoveSingleByteObfuscation:MoveSingleByteCanyouspottheregistrykeyname00415393C645CC53C645CD6FC645CE66C645CF74.
E.
S.
E.
o.
E.
f.
E.
t004153A3C645D077C645D161C645D272C645D365.
E.
w.
E.
a.
E.
r.
E.
e004153B3C645D45CC645D54DC645D669C645D763.
E.
\.
E.
M.
E.
i.
E.
c004153C3C645D872C645D96FC645DA73C645DB6F.
E.
r.
E.
o.
E.
s.
E.
o004153D3C645DC66C645DD74C645DE5CC645DF57.
E.
f.
E.
t.
E.
\.
E.
W004153E3C645E069C645E16EC645E264C645E36F.
E.
i.
E.
n.
E.
d.
E.
o004153F3C645E477C645E573C645E65CC645E743.
E.
w.
E.
s.
E.
\.
E.
C00415403C645E875C645E972C645EA72C645EB65.
E.
u.
E.
r.
E.
r.
E.
e00415413C645EC6EC645ED74C645EE56C645EF65.
E.
n.
E.
t.
E.
V.
E.
e00415423C645F072C645F173C645F269C645F36F.
E.
r.
E.
s.
E.
i.
E.
o00415433C645F46EC645F55CC645F652C645F775.
E.
n.
E.
\.
E.
R.
E.
u00415443C645F86E.
E.
nObfuscation:MoveSingleByteFindtheopcodefor0xc6FRAUNHOFER-INSTITUTFRKOMMUNIKATION,INFORMATIONSVERARBEITUNGUNDERGONOMCONDITIONALLOOPXCHGEAXEXCLUSIVEACCESSCONDITIONALREPETITIONSIZEOVERRIDESEGMENTOVERRIDEJccROL/ROR/RCL/RCR/SHL/SHR/SAL/SARx86OpcodeStructureandInstructionOverview0123456789ABCDEF0123456789ABCDEF0120123456789ABCDEFADDADCANDXORINCDECORSBBSUBCMPPUSHPOPPUSHIMULPUSHPUSHADPOPADESPUSHSSESPOPSSCSPUSHDSIMULESSEGMENTOVERRIDESSNOPTESTXCHGMOVREGINSOUTSBOUNDARPLCSSEGMENTOVERRIDEDSLEAPOPMOVSREGJOJNOJBJNBJEJNEJBEJAJSJNSJPEJPOJLJGEJLEJGFSGSOPERANDSIZEADDRESSSIZEDAAAAADASAASPOPDSADD/ADC/AND/XOROR/SBB/SUB/CMPCWDCDQCALLFWAITPUSHFDPOPFDSAHFLAHFMOVEAXMOVMOVSCMPSTESTSTOSLODSSCASSHIFTIMMSHIFT1SHIFTCLRETNMOVIMMRETFAAMAADLESLDSINT3INTIMMINTOIRETDENTERLEAVESALCXLATFPULOOPNZLOOPZLOOPJECXZINIMMOUTIMMJMPJMPFJMPSHORTINDXOUTDXLOCKICEBPHLTCMCTEST/NOT/NEG[i]MUL/[i]DIVCLCSTCCLISTICLDSTDINCDECINC/DECCALL/JMPPUSHTWOBYTEREPNEREPE{L,S}LDT{L,S}TRVER{R,W}{L,S}GDT{L,S}IDT{L,S}MSWLMOVCRDTSCRDJOJNOSETOSETNOSCPLPOPFSPUSHFSCMPXCHGXADDWRMSRMOVSREGArithmeticGeneralOpcodeStructureAddressingCALL1st2nd1st2ndSource:Extractfromx86OpcodeStructureandInstructionOverview"byDanielPlohmann,FraunhoferFKIEObfuscation:MoveSingleByteReadthemanualpageforMOVINSTRUCTIONSETREFERENCE,A-MOpcodeInstructionOp/En64-BitModeCompat/LegModeDescriptionREX.
W+A3MOVmoffs64*,RAXDValidN.
E.
MoveRAXto(offset).
B0+rbMOVr8,imm8EValidValidMoveimm8tor8.
REX+B0+rbMOVr8***,imm8EValidN.
E.
Moveimm8tor8.
B8+rwMOVr16,imm16EValidValidMoveimm16tor16.
B8+rdMOVr32,imm32EValidValidMoveimm32tor32.
REX.
W+B8+rdMOVr64,imm64EValidN.
E.
Moveimm64tor64.
C6/0MOVr/m8,imm8FValidValidMoveimm8tor/m8.
REX+C6/0MOVr/m8***,imm8FValidN.
E.
Moveimm8tor/m8.
C7/0MOVr/m16,imm16FValidValidMoveimm16tor/m16.
C7/0MOVr/m32,imm32FValidValidMoveimm32tor/m32.
REX.
W+C7/0MOVr/m64,imm32FValidN.
E.
Moveimm32signextendedto64-bitstor/m64.
NOTES:*Themoffs8,moffs16,moffs32andmoffs64operandsspecifyasimpleoffsetrelativetothesegmentbase,where8,16,32and64refertothesizeofthedata.
Theaddress-sizeattributeoftheinstructiondeterminesthesizeoftheoffset,either16,32or64bits.
Obfuscation:MoveSingleByteFindtheregisterandaddressingmodefor0x45INSTRUCTIONFORMATTable2-2.
32-BitAddressingFormswiththeModR/MByter8(/r)r16(/r)r32(/r)mm(/r)xmm(/r)(Indecimal)/digit(Opcode)(Inbinary)REG=ALAXEAXMM0XMM00000CLCXECXMM1XMM11001DLDXEDXMM2XMM22010BLBXEBXMM3XMM33011AHSPESPMM4XMM44100CHBPEBPMM5XMM55101DHSIESIMM6XMM66110BHDIEDIMM7XMM77111EffectiveAddressModR/MValueofModR/MByte(inHexadecimal)[EAX][ECX][EDX][EBX][--][--]1disp322[ESI][EDI]00000001010011100101110111000102030405060708090A0B0C0D0E0F101112131415161718191A1B1C1D1E1F202122232425262728292A2B2C2D2E2F303132333435363738393A3B3C3D3E3F[EAX]+disp83[ECX]+disp8[EDX]+disp8[EBX]+disp8disp8[EBP]+disp8[ESI]+disp8[EDI]+disp801000001010011100101110111404142434445464748494A4B4C4D4E4F505152535455565758595A5B5C5D5E5F606162636465666768696A6B6C6D6E6F707172737475767778797A7B7C7D7E7F[EAX]+disp32[ECX]+disp32[EDX]+disp32[EBX]+disp32disp3210000001010011100808182838488898A8B8C909192939498999A9B9CA0A1A2A3A4A8A9AAABACB0B1B2B3B4B8B9BABBBCObfuscation:MoveSingleByteRevealthestringSinglebyteMOVesareacommontechniquetoobfuscatestrings.
0000:00415393mov[ebp+SubKey],'S';C645CC530000:00415397mov[ebp+SubKey+1],'o';C645CD6F0000:0041539Bmov[ebp+SubKey+2],'f';C645CE660000:0041539Fmov[ebp+SubKey+3],'t';C645CF740000:004153A3mov[ebp+SubKey+4],'w';C645D0770000:004153A7mov[ebp+SubKey+5],'a';C645D1610000:004153ABmov[ebp+SubKey+6],'r';C645D2720000:004153AFmov[ebp+SubKey+7],'e';C645D3650000:004153B3mov[ebp+SubKey+8]C645D45C0000:004153B7mov[ebp+SubKey+9],'M'!
;C645D54D0000:004153BBmov[ebp+SubKey+0Ah],'i'!
;C645D6690000:004153BFmov[ebp+SubKey+0Bh],'c'!
;C645D7630000:004153C3mov[ebp+SubKey+0Ch],'r'!
;C645D8720000:004153C7mov[ebp+SubKey+0Dh],'o'!
;C645D96F0000:004153CBmov[ebp+SubKey+0Eh],'s'!
;C645DA730000:004153CFmov[ebp+SubKey+0Fh],'o'!
;C645DB6F0000:004153D3mov[ebp+SubKey+10h],'f'!
;C645DC660000:004153D7mov[ebp+SubKey+11h],'t'!
;C645DD74Obfuscation:MoveSingleByteDevelopasignatureSignature:0xC60x45isaconstant(opcodeandr/m8)disp8(index)isvariable,butrestrictedtoasinglebytethecharacter(imm8)isvariable,butalsorestrictedtoasinglebytePattern:C645C645C645.
.
.
Obfuscation:MoveSingleByteCreateandtestyoursignaturecd/yara/Lab_2Createafilenamedobfuscation.
yara"andasignaturesingle_byte_mov"Addthepatternasastring.
Note:hexstringsareenclosedincurlybraces.
Addthepropercondition.
Testyoursignature:$yara-robfuscation.
yara/yara/malwareHowmanyfilescontainatleastoneobfuscatedstringObfuscation:MoveSingleByteCreateandtestyoursignatureThisishowyourrulefileshouldlooklike:rulesingle_byte_mov{strings:$a={c645c645c645}condition:$a}Obfuscation:MoveSingleByteImproveyoursignaturePatternusingwildcards:C645C645C645Patternusingjumps:C645[2]C645[2]C645Jumpsare:easiertoreadandmaintainflexible,variableinlength:[n-m]Obfuscation:MoveSingleByteImproveyoursignatureModifyyoursignaturetousejumpsinsteadofmulti-bytewildcardsTestyoursignatureagain.
ArethereanydifferencesCanyoutellthenumberofobfuscatedstrings(notfiles!
)fromtheoutputBonusquestion:IfyouknowPCREwell,thenrewritethepatterntomatchthewholeobfuscatedstring.
(see/yara/doc/yara/pcre.
txtforasyntaxrefresher)Issueyara-s-robfuscation.
yara/yara/malwareHowmanyobfuscatedstringsarethereObfuscation:MoveSingleByteImproveyoursignatureAgain,thisishowyourruleshouldlooklike:rulesingle_byte_mov{strings:$a={c645[2]c645[2]c645}condition:$a}Obfuscation:MoveSingleByteBonusquestionAndhereistheanswertothebonusquestion:rulesingle_byte_mov3{strings:$a=/(\xc6\x45.
.
){3,}/condition:$a}Countofmatchingstrings:$yara-s-robfuscation.
yara/yara/malware/antivirus.
exe|wc-l4Thefirstlineisthematchingrule(andfilename),sotheansweris:3stringswereobfuscated"MagicNumbersMagicnumbersGeneralapproachLookforconstantsthatareimportantforanalgorithmThelonger,thebetter(reducesfalsepositives!
)Examples:staticsubstitutionbox(s-box)ofDESMD5initandtransformconstantspolynomialforCyclicRedundancyCheckBeawareofendianessissues0x1234canbestoredas0x120x34or0x340x12Considerbreakinguplongnumbers,loadingintodifferentregisters,optimizationsbycompilerMagicnumbersARandomNumberGeneratorLinearCongruentialGenerator(LCG)xn+1=(axn+c)modmPierreL'Ecuyer:Tablesoflinearcongruentialgeneratorsofdifferentsizesandgoodlatticestructure(1999)http://dimsboiv.
uqac.
ca/Cours/C2012/8INF802_Hiv12/ref/paper/RNG/TableLecuyer.
pdfWilliamH.
Press:Numericalrecipes:theartofscientificcomputing"(3rded.
,2007),Chapter7MagicnumbersTheRNGofPoisonIvy0000:00000DA5rand_init:0000:00000DA5leaesi,[ebp+base];seedwithCPUtickcounter0000:00000DABrdtsc0000:00000DADxchgeax,edx0000:00000DAExorecx,ecx0000:00000DB00000:00000DB0rand_loop:;LCGx:=(x*2891336453+1)mod2^320000:00000DB0imuleax,28913364530000:00000DB6addeax,10000:00000DB9mov[esi+ecx*4+8D9h],eax0000:00000DC0addecx,10000:00000DC3cmpecx,340000:00000DC6jbshortrand_loopMagicnumbersCamellia'smagicconstantscd/yara/Lab_3Thereyou'llfindacopyofRFC3713,whichspecifiestheCamelliaencryptionalgorithm.
Reviewthespecificationandtrytofindgoodmagicnumbers.
DoNOTeventrytounderstandthealgorithm!
Youareexplicitlyallowed(andencouraged)tocollaboratewithyourneighbours!
Statethemagicnumber(orpagenumber,variablename,etc.
)MagicnumbersCamellia'smagicconstantsWriteoneormultiplerulestocheckforyourmagicnumber(s)Testyourrule(s)on/yara/malware,asbeforeWhatfile(s)arelikelytocontaintheCamelliaalgorithmMemoryAnalysisMemoryanalysisVirtualandphysicalmemoryexplorer.
exesol.
exephysicalmemorypagefileMemoryanalysisScanningphysicalmemoryadvantages:fastbestcoverage(youmaywanttoscanthepagefile,too)disadvantages:memoryfragmentationcanbreakyoursignaturessearchhitscan'tbeattributedtoaprocessMemoryanalysisScanningvirtualmemoryadvantages:attributioniseasydefragmentedmemoryimagedisadvantages:slowdoesnotcoverunallocated(free")memoryMemoryanalysisProposedmethod1.
ObtainphysicalmemorydumpandpagefilesuspendVMandcopy.
vmemfileoruseamemorydumper,likewin32ddmount.
vmdkusingyourtoolofchoiceorextractpagefilefromlivesystemusingFTKImager2.
UseVolatilitytoscaneachvirtualaddressspaceorthekerneladdressspace3.
UseYARAtoscanpagefileandmemorydumpinordertocoverunallocatedandpagedmemoryareas.
MemoryanalysisUsingVolatilitySpecializedyarascan"commandOption-YbuildsYARAruleonthefly,acceptseitherstring,hexorregularexpression$vol.
py-fmemory.
imgyarascan-Y"rm6.
org"$vol.
py-fmemory.
imgyarascan-Y"rm6.
org"-W$vol.
py-fmemory.
imgyarascan-Y"/[0-9a-fA-F]{32}/"$vol.
py-fmemory.
imgyarascan-Y"{c645[2]c645[2]c645}"Option-yreadsYARArulesfromafileOption-KsearchesthekerneladdressspaceinsteadofprocessaddressspacesOption-psearchesonlytheaddressspaceofprocessidentifiedbyitsPIDOption-DdumpsresponsivememoryareastodiskMemoryanalysisHandson:Step1cd/yara/Lab_4Datatoanalyze:memory.
dmpisaphysicalmemorydumpobtainedfromWindowsXPSP2pagefile.
syswascopiedoffthephysicaldisk"usingFTKImagerRulesets:dyndns.
yara:namesofwell-knownDynamicDNSzonescamellia.
yara:magicnumbersofCamelliaencryptionalgorithmMemoryanalysisHandson:Step2SearchallprocessaddressspacesforartifactsoftheCamelliaencryptionalgorithm.
TakeanoteoftheresponsivePIDsBonus:CanyoufindanytracesofCamelliainkernelmemoryMemoryanalysisHandson:Step2training@ubuntu:/yara/Lab_4$vol.
py-fmemory.
dmpyarascan-ycamellia.
yaraVolatileSystemsVolatilityFramework2.
2Rule:Camellia_SigmaOwner:Processsvchost.
exePid10800x5d10c764a09e667f3bcc908bb67ae8584caa73b2.
.
f.
;.
.
.
.
z.
XL.
s.
0x5d10c774c6ef372fe94f82be54ff53a5f1d36f1c.
.
7/.
O.
.
T.
S.
.
.
o.
0x5d10c78410e527fade682d1db05688c2b3e6c1fd.
.
'.
.
h-.
.
V.
.
.
.
.
.
0x5d10c7945d83c7088b4424308b9811010000ff90].
.
.
.
D$0.
.
.
.
.
.
.
.
.
.
.
Rule:Camellia_tablesOwner:Processsvchost.
exePid11160x2010cc8710102020101030300000202000001010.
.
.
.
.
.
00.
.
.
.
.
.
.
.
0x2010cc973030000020201010202000003030558b00.
00U.
0x2010cca7ec56518b75088b9ed10800008b8ed508.
VQ.
u.
0x2010ccb700008b9433d90800008b8433dd080000.
.
.
.
3.
.
.
.
.
.
3.
.
.
.
Rule:Camellia_SigmaOwner:Processexplorer.
exePid14000x01380764a09e667f3bcc908bb67ae8584caa73b2.
.
f.
;.
.
.
.
z.
XL.
s.
0x01380774c6ef372fe94f82be54ff53a5f1d36f1c.
.
7/.
O.
.
T.
S.
.
.
o.
0x0138078410e527fade682d1db05688c2b3e6c1fd.
.
'.
.
h-.
.
V.
.
.
.
.
.
0x013807945d83c7088b4424308b9811010000ff90].
.
.
.
D$0.
.
.
.
.
.
.
.
.
.
.
MemoryanalysisHandson:Step2Infectedprocesses:svchost.
exePID1080svchost.
exePID1116VMwareService.
exePID1652explorer.
exePID1400IEXPLORE.
EXEPID464MemoryanalysisHands-on:Step3SearchthekerneladdressspaceforDynDNSnamesanddumptheresultstodisk.
MemoryanalysisHands-on:Step3training@ubuntu:/yara/Lab_4$mkdirdumptraining@ubuntu:/yara/Lab_4$vol.
py-fmemory.
dmpyarascan-ydyndns.
yara-Ddump/VolatileSystemsVolatilityFramework2.
2Rule:DynDNS_freeOwner:Processwinlogon.
exePid6240x7f77861e72006d0036002e006f00720067000000r.
m.
6.
.
.
o.
r.
g.
.
.
0x7f77862e3ef400000000108b85a00000000000000x7f77863e000000000000000000000000000000000x7f77864e00000000000000000000000000000000Rule:DynDNS_freeOwner:Processservices.
exePid6680x004d09c272006d0036002e006f00720067000000r.
m.
6.
.
.
o.
r.
g.
.
.
0x004d09d200002f000000dc591e00200000001000.
.
/.
.
.
.
Y.
.
.
.
.
.
.
.
0x004d09e200000200040014000000000000001c000x004d09f2000000000000cc4ad892646f6d61696e.
.
.
.
.
.
.
J.
.
domain.
.
.
training@ubuntu:/yara/Lab_4$lsdump/process.
0x80fa53c0.
0x4d09c2.
dmpprocess.
0xff492750.
0x1e617a.
dmpprocess.
0xff4f1c38.
0x7cb25edb.
dmpprocess.
0xff578a18.
0x5cb901af.
dmpprocess.
0x80fa53c0.
0x4d0a03.
dmpprocess.
0xff492750.
0x1e6d37.
dmpprocess.
0xff4f1c38.
0x7cb25ef2.
dmpprocess.
0xff578a18.
0x5cb90d00.
dmpprocess.
0xff492750.
0x170198.
dmpprocess.
0xff492750.
0x1e761e.
dmpprocess.
0xff4f1c38.
0x7cf25edb.
dmpprocess.
0xff580a98.
0x1c5b27.
dmp.
.
.
ConclusionConclusionStringsTextmakeuseofmodifiers:nocase,fullword,ascii,wideHexmakeuseofwildcardsandjumpsPerlcompatibleregularexpressionsConclusionConditionSets2of($a,$b,$c)anyofthemallofthemCountnumberofstringmatches:#stringIteratorfor"Offsets:atoffsetentrypointAccessrawbytes:int8.
.
int32,uint8.
.
uint32Keepyourrulessimple,referenceotherrulesConclusionMetadataDefinemetadatastringintegerbooleanExamples:weight(countofmatchingbits)architecturealgorithmendianessUse-m"commandlineoptiontodisplaymetadataConclusionMaintainasetofrulesOne-file-to-keep-them-alldoesn'tworkwellRefactoryourruleswriterulesforeachcommonexpression(primitives")separatefilesbytopic,makeuseofinclude"Rulemodifiers:global"makesruleaprerequisiteforallotherrules(e.
g.
PEheadercheck)private"suppressesoutputMakeuseoftagsand-t"commandlineoptiontoselectrulesmytagscommonlyreflectmetadataConclusionMoreinformationYARAmanualsandwikiathttp://code.
google.
com/p/yara-project/MalwareAnalyst'sCookbookChapter3:identifypackerssnifferdetectionmalwarecapabilitiesChapter7:XORde-obfuscationYARADaemonifyouneedtorunmanyquerieswiththesameruleset(savescompiletime!
)https://github.
com/jaimeblasco/AlienvaultLabs/tree/master/yaradConclusionShareyourknowledge!
ForumdedicatedtothediscussionandsharingofYARArulesRepositoryonGitHubWebservicetotestnewrules,scananddownloadmalwareFoundedandmoderatedbyMilaParkourandAndreDiMino(DeepEndResearch)Membershipisvetted(sendapplicationfromyourprofessionalemailaddress)Activeparticipationisexpectedandrequired.
Fordetails,pleaseseehttp://www.
deependresearch.
org/2012/08/yara-signature-exchange-google-group.
htmlThankyouforyourattention!
AndreasSchustera.
schuster@yendor.
nethttp://computer.
forensikblog.
de/YARA:AdvancedTopicsJune25,2014BostonAndreasSchusterLogisticsAgendaLogisticsandremarksHands-on:Matchingonmachinecode14:30-15:00BreakHands-on:ParsingthePEheaderRemarksontransitionfromv1.
xtov2.
x17:00EndLogisticsCoursewareEvaluationformYARACheatSheetParticipationinhands-onexercisesrequiresLabVMImageonUSBthumbdrives(pleasereturnassoonasyou'redone!
)VMware{Player,Workstation,Fusion}VirtualBoxmaywork,too(untested!
)1.
Createnewmachine2.
SelectRAM(512MB)3.
Selectexistingdisk"andpointto.
vmdkLogisticsStartingtheVMStartVMLoginasusertraining",passwordistraining"training"alsoisyoursudopasswordYoumaywanttocustomizethekeyboardlayout:System>Preferences>KeyboardSelectLayouts"tabOpenaterminalwindowLogisticsMaterialsintheVMDocumentation(in/yara/doc):Intel64andIA-32ArchitecturesSoftwareDeveloper'sManualx86OpcodeStructureandInstructionOverviewbyDanielPlohmannPEformatdescriptionPerlCompatibleRegularExpressionManualYARACheatSheetYARAv1.
6User'sManualLogisticsMaterialsintheVMExercises:/yara/Lab_1.
.
.
/yara/Lab_6/yara/Labs_restore.
zip:archivedlabmaterialsincasesomethinggoeswrong/yara/malware:livemalwareSlidedeckWARNING!
Virtualmachineimagecontainslivemalwaresamples.
DonotextractandexposetoMicrosoftWindows(oranemulator).
MatchingonMachineCodeObjectiveDuringthishands-onlab,youwilllearnaworkflowtograduallyimproveyourruleshowtobuildbinarysignaturesthatmatchonx86machinecodehowtoorganizearepositorybasedonacategorizationbyYARAhowtoconsolidaterulesAboutthemalwaresamplescd/yara/Lab_5Directoryincoming"holdsseveralnewmalwaresamplesforustoanalyze.
AllsamplesarebackdoorsbelongingtotheHoardy/Vilsel/Phindolp/Ke3changfamily.
Youroveralltaskistocategorizethesesamplesbasedontheirdecryptionroutine.
Forselectedsamplesyouwillfindsomedisassemblylistings.
ThefirstdecryptionroutineDisassemblyofsample44efa4accc42aa55d7843ec69161c8ca:.
text:00401723decrypt:.
text:004017238945E8mov[ebp+0BB4h+var_BCC],eax.
text:004017263BC7cmpeax,edi.
text:004017287D18jgeshortend.
text:0040172A8A88F0E84000movcl,buffer[eax].
text:0040173032C8xorcl,al.
text:004017322AC8subcl,al.
text:0040173480E95Asubcl,5Ah.
text:004017378888F0E84000movbuffer[eax],cl.
text:0040173D83C001addeax,1.
text:00401740EBE1jmpshortdecryptThefirstdecryptionroutineCreatearulefilenamedhoardy.
yara".
CreateaYARArulewhichmatchesonthebytesthataretypesetinboldletters(seepreviouspage).
Nameyourrulecrypto1"andtagitascategory".
Namethestring$crypto1",too.
Tryyourruleonallthesamplesinincoming".
HowmanysamplesmatchyourruleFindtheKnownUnknowns"Thereareknownknowns;therearethingsweknowthatweknow.
Thereareknownunknowns;thatistosaytherearethingsthat,wenowknowwedon'tknow.
Buttherearealsounknownunknowns–therearethingswedonotknowwedon'tknow.
—UnitedStatesSecretaryofDefense,DonaldRumsfeld(2002-02-12)FindtheKnownUnknowns"Createarulenamedunknown".
ThisruleshallmatchonallsamplesthatareNOTdetectedbyrulecrypto1".
Remember:Aruledoesnothavetocontainastrings"section.
Arulecanreferbacktorulesdefinedearlier.
ExploringtheUnknowns"Wepickoneoftheunknown"samples,e.
g.
026936afbbbdd9034f0a24b4032bd2f8anddisassembleit:.
text:004033A1decrypt:.
text:004033A13BC3cmpeax,ebx.
text:004033A37D18jgeshortend.
text:004033A58A88C0E54000movcl,buffer[eax].
text:004033AB32C8xorcl,al.
text:004033AD2AC8subcl,al.
text:004033AF80E97Csubcl,7Ch.
text:004033B28888C0E54000movbuffer[eax],cl.
text:004033B883C001addeax,1.
text:004033BBEBE4jmpshortdecryptComparesamples026936afbbbdd9034f0a24b4032bd2f8and44efa4accc42aa55d7843ec69161c8ca.
Whydoesrulecrypto1"notmatchWhathaschangedExploringtheUnknowns"Createarulenamedcrypto2"withtagcategory"thatmatchesonthedecryptionroutineofsample44efa4accc42aa55d7843ec69161c8ca.
HowmanysamplesaredetectedbythisruleUpdateyourruleunknown".
WhatsamplesarestillnotidentifiedExploringtheUnknowns"Repeatthisworkflow,untilallsamplesareaccountedfor.
Createrulecrypto3"fromdisassemblyofsample057cb5a62199afbb49a98b3a93f2149dCreaterulecrypto4"fromdisassemblyofsample072af79bb2705b27ac2e8d61a25af04bCreaterulecrypto5"fromdisassemblyofsample4c46abe77c752f21a59ee03da0ad5011Attachthetagcategory"toalloftheserules.
Organizeyourrepositoryrepo"isyour-stillempty-repository.
training@ubuntu:/yara/Lab_5$ls-lRrepo/repo/:total20drwxr-xr-x2trainingtraining40962014-01-2000:02crypto1drwxr-xr-x2trainingtraining40962014-01-2000:02crypto2drwxr-xr-x2trainingtraining40962014-01-2000:02crypto3drwxr-xr-x2trainingtraining40962014-01-2000:02crypto4drwxr-xr-x2trainingtraining40962014-01-2000:02crypto5repo/crypto1:total0repo/crypto2:total0.
.
.
Yournextjobistopopulateyourrepositorywiththenewsamplesfromtheincoming"directory.
OrganizeyourrepositoryWelimitYARA'soutputtorulestaggedwithcategory":training@ubuntu:/yara/Lab_5$yara-r-tcategoryhoardy.
yaraincomingcrypto2incoming/1ae06edd0ea2df734e357698bcdf8f30crypto5incoming/4c46abe77c752f21a59ee03da0ad5011crypto2incoming/5ee64f9e44cddaa7ed11d752a149484d.
.
.
Ashellone-linerthenmoves/copies/linksthefilesintotheirproperdirectory:training@ubuntu:/yara/Lab_5$whilereadCATEGORYFILE;\docp${FILE}repo/${CATEGORY}/;\done$${PROBE};\RULE=`mktemp.
/yaratemp.
XXXXXX`||exit1;\printf'probe'>$${PROBE};\printf'ruletest{condition:true}'>$${RULE};\$(YARA)$${RULE}$${PROBE}1>$(NULL)2>$(NULL);GOOD=$$;\echo'ruletest{condition:invalid_keyword}'>$$RULE;\$(YARA)$${RULE}$${PROBE}1>$(NULL)2>$(NULL);FAIL=$$;\if[$$GOOD-eq$$FAIL];\then\printf"Fatal:unabletodetectbrokenrules.
\n"1>&2;\echo"127";\else\echo$${GOOD};\fi;\rm$${PROBE}$${RULE};)MigrationfromYARAv1tov2BooleanshortcutevaluationBooleanshorcutevaluationmissinginv2.
Example:RuleensuresthatitdealswithaPEfile,thendoessomecomputationalexpesiveprocessing(e.
g.
nestedloops)condition:uint16(0)==0x5a4danduint16(uint32(0x3c))==0x4550andfor2iin(0.
.
(uint16(uint32(@section[1]+20)+0xc)-1)):(foranyof($name_*):($at((uint32(uint32(@section[1]+20)+0x10+8*i)&0x7fffffff)+uint32(@section[1]+20))))Worksinv1,butmaytakeinsanelylongtimeinv2!
MigrationfromYARAv1tov2Customregexenginev1.
6:PCREv1.
7:PCREorRE2v2.
0:customregexenginenomorebackreferencese.
g.
noPOSIXcharacterclassese.
g.
[:space:]Benefit:Thenewengineisfasterthananyofthestandardlibraries.
MigrationfromYARAv1tov2Regexgreediness$catrule.
yararuletest{strings:$re=/[a-zA-Z]+/condition:$re}$catdata.
txtThisisatestMigrationfromYARAv1tov2Regexgreediness$yara-vyara1.
6(rev:129)$yara-srule.
yaradata.
txttestdata.
txt0x0:$re:ThisisatestMigrationfromYARAv1tov2Regexgreediness$yara-vyara1.
7(rev:167)$yara-srule.
yaradata.
txttestdata.
txt0x0:$re:Thisisatest0x1:$re:hisisatest0x2:$re:isisatest0x3:$re:sisatest0x4:$re:isatest0x5:$re:isatest0x6:$re:satest0x7:$re:atest0x8:$re:atest0x9:$re:test0xa:$re:test0xb:$re:est0xc:$re:stSolutionsAPDFwithalltheexercisesandsolutions(slideswitharedbar)willbeavailablefromMondayJune30,2014athttp://r.
forens.
is/first2014solOrsendmeanemailata.
schuster@yendor.
netThankyouforyourattention!
AndreasSchustera.
schuster@yendor.
nethttp://computer.
forensikblog.
de/
Thishands-ontutorialwillcoveradvancedtopics.
IfyoustillhavetowriteyourfirstYARArule,thistutorialwillnotbehelpfulatall.
Thisslidedeckissplitintwoparts:Thefirstpartcoverssomebasicconcepts.
YoushouldalreadyhavewrittensomeYARArulesonyourownandappliedsomeofthesetechniquesanumberoftimesbeforecomingtoclass.
However,thevirtualmachineimage(seebelow)includesthematerialsforthebasicexercises,too,soyoucanworkonthematyourownpace.
Thesecondpart,startingfromtheAdvancedTopics"tileslide,willbecoveredinourtutorial.
PleasedownloadtheVMwareimagefromhttp://r.
forens.
is/bos1st/.
Ensureyourenvironmentworksproperlybeforecomingtoclass.
LogisticsAgendaMorningsessionWritingYARArulesBuildingrulesbasedonmagicnumbersMemoryanalysiswithVolatilityandYARAIntroductionIntroductionWhatisYARAThepatternmatchingswissknifeformalwareresearchers(andeveryoneelse)"HostedonGitGubhttp://plusvic.
github.
io/yara/Patternmatching:strings(ASCII,UCS-2)regularexpressionsbinarypatterns(hexstrings)Classification:oninput:combinationofstringsonoutput:tags,metadataIntroductionWhatisYARArulemy_example:tag1tag2tag3{meta:description="Thisisjustanexample"thread_level=3in_the_wild=truestrings:$a={6A4068003000006A148D91}$b=/[0-9a-f]{32}/$c="UVODFRYSIHLNWPEJXQZAKCBGMT"condition:$aor($band$c)}IntroductionWhatYARAisNOTNotavirusscannerNotacorrelationengineNotabayesianclassifierNoartificalintelligence(AI)involvedIntroductionHowcanYARAhelpmeAbettergrep"Usecases:Findinginterestingentriesonpastebin.
com.
.
.
TriagedataPreprocessfilestodirectreverseengineeringeffortsIntegrateitintoyourprojects:ClibraryPythonbindingshttps://github.
com/plusvic/yara/tree/master/yara-pythonRubybindingshttps://github.
com/SpiderLabs/yara-rubyIntroductionHowcanYARAhelpmeYARArulesaresupportedbysecurityproductsandservicesFireEyeappliancesFidelisXPSRSAECATVolatilityThreadConnectthreatintelligenceexchangeVirusTotalIntelligence.
.
.
WritingYARARulesHelloWorld!
YourFirstYARARuleYourfirstYARAruleStartingtheVMStartVMLoginasusertraining",passwordistraining"training"alsoisyoursudopasswordYoumaywanttocustomizethekeyboardlayout:System>Preferences>KeyboardSelectLayouts"tabOpenaterminalwindowYourfirstYARAruleGettinghelp$yarausage:yara[OPTION].
.
.
[RULEFILE].
.
.
FILEoptions:-tprintrulestaggedasandignoretherest.
Canbeusedmorethanonce.
-iprintrulesnamedandignoretherest.
Canbeusedmorethanonce.
-nprintonlynotsatisfiedrules(negate).
-gprinttags.
-mprintmetadata.
-sprintmatchingstrings.
-d=defineexternalvariable.
-rrecursivelysearchdirectories.
-ffastmatchingmode.
-vshowversioninformation.
YourfirstYARAruleChecktheinstalledversionThereareslightdifferencesbetweenYARAversions1.
4to1.
7and2.
0,seehttp://code.
google.
com/p/yara-project/source/browse/trunk/ChangeLogandhttps://github.
com/plusvic/yara/commits/masterfordetailsUsermanualisin/yara/docofthisVMWhatversiondoestheVMprovide$yara-vYoushouldseetheresult:yara1.
6YourfirstYARAruleEditorsThefollowingeditorsareavailable:vim(withsimplesyntaxhighlighting)gvim(withGUIandsyntaxhighlighting)emacsgeditYourfirstYARAruleAminimalistrulecd/yara/Lab_1Createafilenamedhello.
yara"withthefollowingcontents:ruleHello_World{condition:true}Nowletthecomputergreetyou:$yarahello.
yara/yara/malware/somefile.
txtYourfirstYARArulePassingexternaldatatoYARAReviewthefilegreeting.
yararuleGoodMorning{condition:hour=4}Nowpassdifferentvaluesforhour"totheruleset:$yara-dhour=8greeting.
yara/yara/malware/somefile.
txtGoodMorning/yara/files/somefile.
txt$yara-dhour=20greeting.
yara/yara/malware/somefile.
txtGoodEvening/yara/files/somefile.
txtWhathappenswhenyoupassastring(e.
g.
noon")ornovalueatallIdentifyExecutableFilesIdentifyexecutablefilesAsimplespecificationforPEfilesTask:TofindanyfilesinPortableExecutable(PE")formatSimplespecification:FilemustcontainthestringsMZ"andPE"000000004d5a90000300000004000000ffff0000|MZ.
00000010b8000000000000004000000000000000000000200000000000000000000000000000000000000030000000000000000000000000c8000000000000400e1fba0e00b409cd21b8014ccd215468L.
!
Th|0000005069732070726f6772616d2063616e6e6f|isprogramcanno|00000060742062652072756e20696e20444f5320|tberuninDOS|000000706d6f64652e0d0d0a2400000000000000|mode.
0000008065cd43c721ac2d9421ac2d9421ac2d94|e.
C.
0000009021ac2c9425ac2d94e2a3709424ac2d94p.
$.
-.
|000000a0c9b3269423ac2d945269636821ac2d94Rich!
.
-.
|000000b000000000000000000000000000000000000000c00000000000000000504500004c010300PE.
.
L.
.
.
|IdentifyexecutablefilesRuleskeletoncd/yara/Lab_2Createanewfile,namedexecutable.
yara"Startwithablankrule:rulePE_file{}IdentifyexecutablefilesAddingstringsNowaddthetwostrings:rulePE_file{strings:$mz="MZ"$pe="PE"}Note:Stringsarecase-sensitivebydefault!
IdentifyexecutablefilesAddingtheconditionAportableexecutablefileMUSTcontainbothstrings.
So,addthepropercondition:rulePE_file{strings:$mz="MZ"$pe="PE"condition:$mzand$pe}Testyourrulefile:$yara-rexecutable.
yara/yara/malwareIdentifyexecutablefilesRefiningtheconditionMoreconstraints:MZ"atoffset0UInt32atoffset0x3cpointstoPE"Refineyourconditionsection:condition:($mzat0)and($peat(uint32(0x3c)))Testyourrulefileagain:$yara-rexecutable.
yara/yara/malwareIdentifyexecutablefilesThefinalruleThisishowyourruleshouldlooklike:rulePE_file{!
strings:!
!
$mz="MZ"!
!
$pe="PE"!
condition:!
!
($mzat0)and!
!
($peat(uint32(0x3c)))}Obfuscation:MoveSingleByteObfuscation:MoveSingleByteCanyouspottheregistrykeyname00415393C645CC53C645CD6FC645CE66C645CF74.
E.
S.
E.
o.
E.
f.
E.
t004153A3C645D077C645D161C645D272C645D365.
E.
w.
E.
a.
E.
r.
E.
e004153B3C645D45CC645D54DC645D669C645D763.
E.
\.
E.
M.
E.
i.
E.
c004153C3C645D872C645D96FC645DA73C645DB6F.
E.
r.
E.
o.
E.
s.
E.
o004153D3C645DC66C645DD74C645DE5CC645DF57.
E.
f.
E.
t.
E.
\.
E.
W004153E3C645E069C645E16EC645E264C645E36F.
E.
i.
E.
n.
E.
d.
E.
o004153F3C645E477C645E573C645E65CC645E743.
E.
w.
E.
s.
E.
\.
E.
C00415403C645E875C645E972C645EA72C645EB65.
E.
u.
E.
r.
E.
r.
E.
e00415413C645EC6EC645ED74C645EE56C645EF65.
E.
n.
E.
t.
E.
V.
E.
e00415423C645F072C645F173C645F269C645F36F.
E.
r.
E.
s.
E.
i.
E.
o00415433C645F46EC645F55CC645F652C645F775.
E.
n.
E.
\.
E.
R.
E.
u00415443C645F86E.
E.
nObfuscation:MoveSingleByteFindtheopcodefor0xc6FRAUNHOFER-INSTITUTFRKOMMUNIKATION,INFORMATIONSVERARBEITUNGUNDERGONOMCONDITIONALLOOPXCHGEAXEXCLUSIVEACCESSCONDITIONALREPETITIONSIZEOVERRIDESEGMENTOVERRIDEJccROL/ROR/RCL/RCR/SHL/SHR/SAL/SARx86OpcodeStructureandInstructionOverview0123456789ABCDEF0123456789ABCDEF0120123456789ABCDEFADDADCANDXORINCDECORSBBSUBCMPPUSHPOPPUSHIMULPUSHPUSHADPOPADESPUSHSSESPOPSSCSPUSHDSIMULESSEGMENTOVERRIDESSNOPTESTXCHGMOVREGINSOUTSBOUNDARPLCSSEGMENTOVERRIDEDSLEAPOPMOVSREGJOJNOJBJNBJEJNEJBEJAJSJNSJPEJPOJLJGEJLEJGFSGSOPERANDSIZEADDRESSSIZEDAAAAADASAASPOPDSADD/ADC/AND/XOROR/SBB/SUB/CMPCWDCDQCALLFWAITPUSHFDPOPFDSAHFLAHFMOVEAXMOVMOVSCMPSTESTSTOSLODSSCASSHIFTIMMSHIFT1SHIFTCLRETNMOVIMMRETFAAMAADLESLDSINT3INTIMMINTOIRETDENTERLEAVESALCXLATFPULOOPNZLOOPZLOOPJECXZINIMMOUTIMMJMPJMPFJMPSHORTINDXOUTDXLOCKICEBPHLTCMCTEST/NOT/NEG[i]MUL/[i]DIVCLCSTCCLISTICLDSTDINCDECINC/DECCALL/JMPPUSHTWOBYTEREPNEREPE{L,S}LDT{L,S}TRVER{R,W}{L,S}GDT{L,S}IDT{L,S}MSWLMOVCRDTSCRDJOJNOSETOSETNOSCPLPOPFSPUSHFSCMPXCHGXADDWRMSRMOVSREGArithmeticGeneralOpcodeStructureAddressingCALL1st2nd1st2ndSource:Extractfromx86OpcodeStructureandInstructionOverview"byDanielPlohmann,FraunhoferFKIEObfuscation:MoveSingleByteReadthemanualpageforMOVINSTRUCTIONSETREFERENCE,A-MOpcodeInstructionOp/En64-BitModeCompat/LegModeDescriptionREX.
W+A3MOVmoffs64*,RAXDValidN.
E.
MoveRAXto(offset).
B0+rbMOVr8,imm8EValidValidMoveimm8tor8.
REX+B0+rbMOVr8***,imm8EValidN.
E.
Moveimm8tor8.
B8+rwMOVr16,imm16EValidValidMoveimm16tor16.
B8+rdMOVr32,imm32EValidValidMoveimm32tor32.
REX.
W+B8+rdMOVr64,imm64EValidN.
E.
Moveimm64tor64.
C6/0MOVr/m8,imm8FValidValidMoveimm8tor/m8.
REX+C6/0MOVr/m8***,imm8FValidN.
E.
Moveimm8tor/m8.
C7/0MOVr/m16,imm16FValidValidMoveimm16tor/m16.
C7/0MOVr/m32,imm32FValidValidMoveimm32tor/m32.
REX.
W+C7/0MOVr/m64,imm32FValidN.
E.
Moveimm32signextendedto64-bitstor/m64.
NOTES:*Themoffs8,moffs16,moffs32andmoffs64operandsspecifyasimpleoffsetrelativetothesegmentbase,where8,16,32and64refertothesizeofthedata.
Theaddress-sizeattributeoftheinstructiondeterminesthesizeoftheoffset,either16,32or64bits.
Obfuscation:MoveSingleByteFindtheregisterandaddressingmodefor0x45INSTRUCTIONFORMATTable2-2.
32-BitAddressingFormswiththeModR/MByter8(/r)r16(/r)r32(/r)mm(/r)xmm(/r)(Indecimal)/digit(Opcode)(Inbinary)REG=ALAXEAXMM0XMM00000CLCXECXMM1XMM11001DLDXEDXMM2XMM22010BLBXEBXMM3XMM33011AHSPESPMM4XMM44100CHBPEBPMM5XMM55101DHSIESIMM6XMM66110BHDIEDIMM7XMM77111EffectiveAddressModR/MValueofModR/MByte(inHexadecimal)[EAX][ECX][EDX][EBX][--][--]1disp322[ESI][EDI]00000001010011100101110111000102030405060708090A0B0C0D0E0F101112131415161718191A1B1C1D1E1F202122232425262728292A2B2C2D2E2F303132333435363738393A3B3C3D3E3F[EAX]+disp83[ECX]+disp8[EDX]+disp8[EBX]+disp8disp8[EBP]+disp8[ESI]+disp8[EDI]+disp801000001010011100101110111404142434445464748494A4B4C4D4E4F505152535455565758595A5B5C5D5E5F606162636465666768696A6B6C6D6E6F707172737475767778797A7B7C7D7E7F[EAX]+disp32[ECX]+disp32[EDX]+disp32[EBX]+disp32disp3210000001010011100808182838488898A8B8C909192939498999A9B9CA0A1A2A3A4A8A9AAABACB0B1B2B3B4B8B9BABBBCObfuscation:MoveSingleByteRevealthestringSinglebyteMOVesareacommontechniquetoobfuscatestrings.
0000:00415393mov[ebp+SubKey],'S';C645CC530000:00415397mov[ebp+SubKey+1],'o';C645CD6F0000:0041539Bmov[ebp+SubKey+2],'f';C645CE660000:0041539Fmov[ebp+SubKey+3],'t';C645CF740000:004153A3mov[ebp+SubKey+4],'w';C645D0770000:004153A7mov[ebp+SubKey+5],'a';C645D1610000:004153ABmov[ebp+SubKey+6],'r';C645D2720000:004153AFmov[ebp+SubKey+7],'e';C645D3650000:004153B3mov[ebp+SubKey+8]C645D45C0000:004153B7mov[ebp+SubKey+9],'M'!
;C645D54D0000:004153BBmov[ebp+SubKey+0Ah],'i'!
;C645D6690000:004153BFmov[ebp+SubKey+0Bh],'c'!
;C645D7630000:004153C3mov[ebp+SubKey+0Ch],'r'!
;C645D8720000:004153C7mov[ebp+SubKey+0Dh],'o'!
;C645D96F0000:004153CBmov[ebp+SubKey+0Eh],'s'!
;C645DA730000:004153CFmov[ebp+SubKey+0Fh],'o'!
;C645DB6F0000:004153D3mov[ebp+SubKey+10h],'f'!
;C645DC660000:004153D7mov[ebp+SubKey+11h],'t'!
;C645DD74Obfuscation:MoveSingleByteDevelopasignatureSignature:0xC60x45isaconstant(opcodeandr/m8)disp8(index)isvariable,butrestrictedtoasinglebytethecharacter(imm8)isvariable,butalsorestrictedtoasinglebytePattern:C645C645C645.
.
.
Obfuscation:MoveSingleByteCreateandtestyoursignaturecd/yara/Lab_2Createafilenamedobfuscation.
yara"andasignaturesingle_byte_mov"Addthepatternasastring.
Note:hexstringsareenclosedincurlybraces.
Addthepropercondition.
Testyoursignature:$yara-robfuscation.
yara/yara/malwareHowmanyfilescontainatleastoneobfuscatedstringObfuscation:MoveSingleByteCreateandtestyoursignatureThisishowyourrulefileshouldlooklike:rulesingle_byte_mov{strings:$a={c645c645c645}condition:$a}Obfuscation:MoveSingleByteImproveyoursignaturePatternusingwildcards:C645C645C645Patternusingjumps:C645[2]C645[2]C645Jumpsare:easiertoreadandmaintainflexible,variableinlength:[n-m]Obfuscation:MoveSingleByteImproveyoursignatureModifyyoursignaturetousejumpsinsteadofmulti-bytewildcardsTestyoursignatureagain.
ArethereanydifferencesCanyoutellthenumberofobfuscatedstrings(notfiles!
)fromtheoutputBonusquestion:IfyouknowPCREwell,thenrewritethepatterntomatchthewholeobfuscatedstring.
(see/yara/doc/yara/pcre.
txtforasyntaxrefresher)Issueyara-s-robfuscation.
yara/yara/malwareHowmanyobfuscatedstringsarethereObfuscation:MoveSingleByteImproveyoursignatureAgain,thisishowyourruleshouldlooklike:rulesingle_byte_mov{strings:$a={c645[2]c645[2]c645}condition:$a}Obfuscation:MoveSingleByteBonusquestionAndhereistheanswertothebonusquestion:rulesingle_byte_mov3{strings:$a=/(\xc6\x45.
.
){3,}/condition:$a}Countofmatchingstrings:$yara-s-robfuscation.
yara/yara/malware/antivirus.
exe|wc-l4Thefirstlineisthematchingrule(andfilename),sotheansweris:3stringswereobfuscated"MagicNumbersMagicnumbersGeneralapproachLookforconstantsthatareimportantforanalgorithmThelonger,thebetter(reducesfalsepositives!
)Examples:staticsubstitutionbox(s-box)ofDESMD5initandtransformconstantspolynomialforCyclicRedundancyCheckBeawareofendianessissues0x1234canbestoredas0x120x34or0x340x12Considerbreakinguplongnumbers,loadingintodifferentregisters,optimizationsbycompilerMagicnumbersARandomNumberGeneratorLinearCongruentialGenerator(LCG)xn+1=(axn+c)modmPierreL'Ecuyer:Tablesoflinearcongruentialgeneratorsofdifferentsizesandgoodlatticestructure(1999)http://dimsboiv.
uqac.
ca/Cours/C2012/8INF802_Hiv12/ref/paper/RNG/TableLecuyer.
pdfWilliamH.
Press:Numericalrecipes:theartofscientificcomputing"(3rded.
,2007),Chapter7MagicnumbersTheRNGofPoisonIvy0000:00000DA5rand_init:0000:00000DA5leaesi,[ebp+base];seedwithCPUtickcounter0000:00000DABrdtsc0000:00000DADxchgeax,edx0000:00000DAExorecx,ecx0000:00000DB00000:00000DB0rand_loop:;LCGx:=(x*2891336453+1)mod2^320000:00000DB0imuleax,28913364530000:00000DB6addeax,10000:00000DB9mov[esi+ecx*4+8D9h],eax0000:00000DC0addecx,10000:00000DC3cmpecx,340000:00000DC6jbshortrand_loopMagicnumbersCamellia'smagicconstantscd/yara/Lab_3Thereyou'llfindacopyofRFC3713,whichspecifiestheCamelliaencryptionalgorithm.
Reviewthespecificationandtrytofindgoodmagicnumbers.
DoNOTeventrytounderstandthealgorithm!
Youareexplicitlyallowed(andencouraged)tocollaboratewithyourneighbours!
Statethemagicnumber(orpagenumber,variablename,etc.
)MagicnumbersCamellia'smagicconstantsWriteoneormultiplerulestocheckforyourmagicnumber(s)Testyourrule(s)on/yara/malware,asbeforeWhatfile(s)arelikelytocontaintheCamelliaalgorithmMemoryAnalysisMemoryanalysisVirtualandphysicalmemoryexplorer.
exesol.
exephysicalmemorypagefileMemoryanalysisScanningphysicalmemoryadvantages:fastbestcoverage(youmaywanttoscanthepagefile,too)disadvantages:memoryfragmentationcanbreakyoursignaturessearchhitscan'tbeattributedtoaprocessMemoryanalysisScanningvirtualmemoryadvantages:attributioniseasydefragmentedmemoryimagedisadvantages:slowdoesnotcoverunallocated(free")memoryMemoryanalysisProposedmethod1.
ObtainphysicalmemorydumpandpagefilesuspendVMandcopy.
vmemfileoruseamemorydumper,likewin32ddmount.
vmdkusingyourtoolofchoiceorextractpagefilefromlivesystemusingFTKImager2.
UseVolatilitytoscaneachvirtualaddressspaceorthekerneladdressspace3.
UseYARAtoscanpagefileandmemorydumpinordertocoverunallocatedandpagedmemoryareas.
MemoryanalysisUsingVolatilitySpecializedyarascan"commandOption-YbuildsYARAruleonthefly,acceptseitherstring,hexorregularexpression$vol.
py-fmemory.
imgyarascan-Y"rm6.
org"$vol.
py-fmemory.
imgyarascan-Y"rm6.
org"-W$vol.
py-fmemory.
imgyarascan-Y"/[0-9a-fA-F]{32}/"$vol.
py-fmemory.
imgyarascan-Y"{c645[2]c645[2]c645}"Option-yreadsYARArulesfromafileOption-KsearchesthekerneladdressspaceinsteadofprocessaddressspacesOption-psearchesonlytheaddressspaceofprocessidentifiedbyitsPIDOption-DdumpsresponsivememoryareastodiskMemoryanalysisHandson:Step1cd/yara/Lab_4Datatoanalyze:memory.
dmpisaphysicalmemorydumpobtainedfromWindowsXPSP2pagefile.
syswascopiedoffthephysicaldisk"usingFTKImagerRulesets:dyndns.
yara:namesofwell-knownDynamicDNSzonescamellia.
yara:magicnumbersofCamelliaencryptionalgorithmMemoryanalysisHandson:Step2SearchallprocessaddressspacesforartifactsoftheCamelliaencryptionalgorithm.
TakeanoteoftheresponsivePIDsBonus:CanyoufindanytracesofCamelliainkernelmemoryMemoryanalysisHandson:Step2training@ubuntu:/yara/Lab_4$vol.
py-fmemory.
dmpyarascan-ycamellia.
yaraVolatileSystemsVolatilityFramework2.
2Rule:Camellia_SigmaOwner:Processsvchost.
exePid10800x5d10c764a09e667f3bcc908bb67ae8584caa73b2.
.
f.
;.
.
.
.
z.
XL.
s.
0x5d10c774c6ef372fe94f82be54ff53a5f1d36f1c.
.
7/.
O.
.
T.
S.
.
.
o.
0x5d10c78410e527fade682d1db05688c2b3e6c1fd.
.
'.
.
h-.
.
V.
.
.
.
.
.
0x5d10c7945d83c7088b4424308b9811010000ff90].
.
.
.
D$0.
.
.
.
.
.
.
.
.
.
.
Rule:Camellia_tablesOwner:Processsvchost.
exePid11160x2010cc8710102020101030300000202000001010.
.
.
.
.
.
00.
.
.
.
.
.
.
.
0x2010cc973030000020201010202000003030558b00.
00U.
0x2010cca7ec56518b75088b9ed10800008b8ed508.
VQ.
u.
0x2010ccb700008b9433d90800008b8433dd080000.
.
.
.
3.
.
.
.
.
.
3.
.
.
.
Rule:Camellia_SigmaOwner:Processexplorer.
exePid14000x01380764a09e667f3bcc908bb67ae8584caa73b2.
.
f.
;.
.
.
.
z.
XL.
s.
0x01380774c6ef372fe94f82be54ff53a5f1d36f1c.
.
7/.
O.
.
T.
S.
.
.
o.
0x0138078410e527fade682d1db05688c2b3e6c1fd.
.
'.
.
h-.
.
V.
.
.
.
.
.
0x013807945d83c7088b4424308b9811010000ff90].
.
.
.
D$0.
.
.
.
.
.
.
.
.
.
.
MemoryanalysisHandson:Step2Infectedprocesses:svchost.
exePID1080svchost.
exePID1116VMwareService.
exePID1652explorer.
exePID1400IEXPLORE.
EXEPID464MemoryanalysisHands-on:Step3SearchthekerneladdressspaceforDynDNSnamesanddumptheresultstodisk.
MemoryanalysisHands-on:Step3training@ubuntu:/yara/Lab_4$mkdirdumptraining@ubuntu:/yara/Lab_4$vol.
py-fmemory.
dmpyarascan-ydyndns.
yara-Ddump/VolatileSystemsVolatilityFramework2.
2Rule:DynDNS_freeOwner:Processwinlogon.
exePid6240x7f77861e72006d0036002e006f00720067000000r.
m.
6.
.
.
o.
r.
g.
.
.
0x7f77862e3ef400000000108b85a00000000000000x7f77863e000000000000000000000000000000000x7f77864e00000000000000000000000000000000Rule:DynDNS_freeOwner:Processservices.
exePid6680x004d09c272006d0036002e006f00720067000000r.
m.
6.
.
.
o.
r.
g.
.
.
0x004d09d200002f000000dc591e00200000001000.
.
/.
.
.
.
Y.
.
.
.
.
.
.
.
0x004d09e200000200040014000000000000001c000x004d09f2000000000000cc4ad892646f6d61696e.
.
.
.
.
.
.
J.
.
domain.
.
.
training@ubuntu:/yara/Lab_4$lsdump/process.
0x80fa53c0.
0x4d09c2.
dmpprocess.
0xff492750.
0x1e617a.
dmpprocess.
0xff4f1c38.
0x7cb25edb.
dmpprocess.
0xff578a18.
0x5cb901af.
dmpprocess.
0x80fa53c0.
0x4d0a03.
dmpprocess.
0xff492750.
0x1e6d37.
dmpprocess.
0xff4f1c38.
0x7cb25ef2.
dmpprocess.
0xff578a18.
0x5cb90d00.
dmpprocess.
0xff492750.
0x170198.
dmpprocess.
0xff492750.
0x1e761e.
dmpprocess.
0xff4f1c38.
0x7cf25edb.
dmpprocess.
0xff580a98.
0x1c5b27.
dmp.
.
.
ConclusionConclusionStringsTextmakeuseofmodifiers:nocase,fullword,ascii,wideHexmakeuseofwildcardsandjumpsPerlcompatibleregularexpressionsConclusionConditionSets2of($a,$b,$c)anyofthemallofthemCountnumberofstringmatches:#stringIteratorfor"Offsets:atoffsetentrypointAccessrawbytes:int8.
.
int32,uint8.
.
uint32Keepyourrulessimple,referenceotherrulesConclusionMetadataDefinemetadatastringintegerbooleanExamples:weight(countofmatchingbits)architecturealgorithmendianessUse-m"commandlineoptiontodisplaymetadataConclusionMaintainasetofrulesOne-file-to-keep-them-alldoesn'tworkwellRefactoryourruleswriterulesforeachcommonexpression(primitives")separatefilesbytopic,makeuseofinclude"Rulemodifiers:global"makesruleaprerequisiteforallotherrules(e.
g.
PEheadercheck)private"suppressesoutputMakeuseoftagsand-t"commandlineoptiontoselectrulesmytagscommonlyreflectmetadataConclusionMoreinformationYARAmanualsandwikiathttp://code.
google.
com/p/yara-project/MalwareAnalyst'sCookbookChapter3:identifypackerssnifferdetectionmalwarecapabilitiesChapter7:XORde-obfuscationYARADaemonifyouneedtorunmanyquerieswiththesameruleset(savescompiletime!
)https://github.
com/jaimeblasco/AlienvaultLabs/tree/master/yaradConclusionShareyourknowledge!
ForumdedicatedtothediscussionandsharingofYARArulesRepositoryonGitHubWebservicetotestnewrules,scananddownloadmalwareFoundedandmoderatedbyMilaParkourandAndreDiMino(DeepEndResearch)Membershipisvetted(sendapplicationfromyourprofessionalemailaddress)Activeparticipationisexpectedandrequired.
Fordetails,pleaseseehttp://www.
deependresearch.
org/2012/08/yara-signature-exchange-google-group.
htmlThankyouforyourattention!
AndreasSchustera.
schuster@yendor.
nethttp://computer.
forensikblog.
de/YARA:AdvancedTopicsJune25,2014BostonAndreasSchusterLogisticsAgendaLogisticsandremarksHands-on:Matchingonmachinecode14:30-15:00BreakHands-on:ParsingthePEheaderRemarksontransitionfromv1.
xtov2.
x17:00EndLogisticsCoursewareEvaluationformYARACheatSheetParticipationinhands-onexercisesrequiresLabVMImageonUSBthumbdrives(pleasereturnassoonasyou'redone!
)VMware{Player,Workstation,Fusion}VirtualBoxmaywork,too(untested!
)1.
Createnewmachine2.
SelectRAM(512MB)3.
Selectexistingdisk"andpointto.
vmdkLogisticsStartingtheVMStartVMLoginasusertraining",passwordistraining"training"alsoisyoursudopasswordYoumaywanttocustomizethekeyboardlayout:System>Preferences>KeyboardSelectLayouts"tabOpenaterminalwindowLogisticsMaterialsintheVMDocumentation(in/yara/doc):Intel64andIA-32ArchitecturesSoftwareDeveloper'sManualx86OpcodeStructureandInstructionOverviewbyDanielPlohmannPEformatdescriptionPerlCompatibleRegularExpressionManualYARACheatSheetYARAv1.
6User'sManualLogisticsMaterialsintheVMExercises:/yara/Lab_1.
.
.
/yara/Lab_6/yara/Labs_restore.
zip:archivedlabmaterialsincasesomethinggoeswrong/yara/malware:livemalwareSlidedeckWARNING!
Virtualmachineimagecontainslivemalwaresamples.
DonotextractandexposetoMicrosoftWindows(oranemulator).
MatchingonMachineCodeObjectiveDuringthishands-onlab,youwilllearnaworkflowtograduallyimproveyourruleshowtobuildbinarysignaturesthatmatchonx86machinecodehowtoorganizearepositorybasedonacategorizationbyYARAhowtoconsolidaterulesAboutthemalwaresamplescd/yara/Lab_5Directoryincoming"holdsseveralnewmalwaresamplesforustoanalyze.
AllsamplesarebackdoorsbelongingtotheHoardy/Vilsel/Phindolp/Ke3changfamily.
Youroveralltaskistocategorizethesesamplesbasedontheirdecryptionroutine.
Forselectedsamplesyouwillfindsomedisassemblylistings.
ThefirstdecryptionroutineDisassemblyofsample44efa4accc42aa55d7843ec69161c8ca:.
text:00401723decrypt:.
text:004017238945E8mov[ebp+0BB4h+var_BCC],eax.
text:004017263BC7cmpeax,edi.
text:004017287D18jgeshortend.
text:0040172A8A88F0E84000movcl,buffer[eax].
text:0040173032C8xorcl,al.
text:004017322AC8subcl,al.
text:0040173480E95Asubcl,5Ah.
text:004017378888F0E84000movbuffer[eax],cl.
text:0040173D83C001addeax,1.
text:00401740EBE1jmpshortdecryptThefirstdecryptionroutineCreatearulefilenamedhoardy.
yara".
CreateaYARArulewhichmatchesonthebytesthataretypesetinboldletters(seepreviouspage).
Nameyourrulecrypto1"andtagitascategory".
Namethestring$crypto1",too.
Tryyourruleonallthesamplesinincoming".
HowmanysamplesmatchyourruleFindtheKnownUnknowns"Thereareknownknowns;therearethingsweknowthatweknow.
Thereareknownunknowns;thatistosaytherearethingsthat,wenowknowwedon'tknow.
Buttherearealsounknownunknowns–therearethingswedonotknowwedon'tknow.
—UnitedStatesSecretaryofDefense,DonaldRumsfeld(2002-02-12)FindtheKnownUnknowns"Createarulenamedunknown".
ThisruleshallmatchonallsamplesthatareNOTdetectedbyrulecrypto1".
Remember:Aruledoesnothavetocontainastrings"section.
Arulecanreferbacktorulesdefinedearlier.
ExploringtheUnknowns"Wepickoneoftheunknown"samples,e.
g.
026936afbbbdd9034f0a24b4032bd2f8anddisassembleit:.
text:004033A1decrypt:.
text:004033A13BC3cmpeax,ebx.
text:004033A37D18jgeshortend.
text:004033A58A88C0E54000movcl,buffer[eax].
text:004033AB32C8xorcl,al.
text:004033AD2AC8subcl,al.
text:004033AF80E97Csubcl,7Ch.
text:004033B28888C0E54000movbuffer[eax],cl.
text:004033B883C001addeax,1.
text:004033BBEBE4jmpshortdecryptComparesamples026936afbbbdd9034f0a24b4032bd2f8and44efa4accc42aa55d7843ec69161c8ca.
Whydoesrulecrypto1"notmatchWhathaschangedExploringtheUnknowns"Createarulenamedcrypto2"withtagcategory"thatmatchesonthedecryptionroutineofsample44efa4accc42aa55d7843ec69161c8ca.
HowmanysamplesaredetectedbythisruleUpdateyourruleunknown".
WhatsamplesarestillnotidentifiedExploringtheUnknowns"Repeatthisworkflow,untilallsamplesareaccountedfor.
Createrulecrypto3"fromdisassemblyofsample057cb5a62199afbb49a98b3a93f2149dCreaterulecrypto4"fromdisassemblyofsample072af79bb2705b27ac2e8d61a25af04bCreaterulecrypto5"fromdisassemblyofsample4c46abe77c752f21a59ee03da0ad5011Attachthetagcategory"toalloftheserules.
Organizeyourrepositoryrepo"isyour-stillempty-repository.
training@ubuntu:/yara/Lab_5$ls-lRrepo/repo/:total20drwxr-xr-x2trainingtraining40962014-01-2000:02crypto1drwxr-xr-x2trainingtraining40962014-01-2000:02crypto2drwxr-xr-x2trainingtraining40962014-01-2000:02crypto3drwxr-xr-x2trainingtraining40962014-01-2000:02crypto4drwxr-xr-x2trainingtraining40962014-01-2000:02crypto5repo/crypto1:total0repo/crypto2:total0.
.
.
Yournextjobistopopulateyourrepositorywiththenewsamplesfromtheincoming"directory.
OrganizeyourrepositoryWelimitYARA'soutputtorulestaggedwithcategory":training@ubuntu:/yara/Lab_5$yara-r-tcategoryhoardy.
yaraincomingcrypto2incoming/1ae06edd0ea2df734e357698bcdf8f30crypto5incoming/4c46abe77c752f21a59ee03da0ad5011crypto2incoming/5ee64f9e44cddaa7ed11d752a149484d.
.
.
Ashellone-linerthenmoves/copies/linksthefilesintotheirproperdirectory:training@ubuntu:/yara/Lab_5$whilereadCATEGORYFILE;\docp${FILE}repo/${CATEGORY}/;\done$${PROBE};\RULE=`mktemp.
/yaratemp.
XXXXXX`||exit1;\printf'probe'>$${PROBE};\printf'ruletest{condition:true}'>$${RULE};\$(YARA)$${RULE}$${PROBE}1>$(NULL)2>$(NULL);GOOD=$$;\echo'ruletest{condition:invalid_keyword}'>$$RULE;\$(YARA)$${RULE}$${PROBE}1>$(NULL)2>$(NULL);FAIL=$$;\if[$$GOOD-eq$$FAIL];\then\printf"Fatal:unabletodetectbrokenrules.
\n"1>&2;\echo"127";\else\echo$${GOOD};\fi;\rm$${PROBE}$${RULE};)MigrationfromYARAv1tov2BooleanshortcutevaluationBooleanshorcutevaluationmissinginv2.
Example:RuleensuresthatitdealswithaPEfile,thendoessomecomputationalexpesiveprocessing(e.
g.
nestedloops)condition:uint16(0)==0x5a4danduint16(uint32(0x3c))==0x4550andfor2iin(0.
.
(uint16(uint32(@section[1]+20)+0xc)-1)):(foranyof($name_*):($at((uint32(uint32(@section[1]+20)+0x10+8*i)&0x7fffffff)+uint32(@section[1]+20))))Worksinv1,butmaytakeinsanelylongtimeinv2!
MigrationfromYARAv1tov2Customregexenginev1.
6:PCREv1.
7:PCREorRE2v2.
0:customregexenginenomorebackreferencese.
g.
noPOSIXcharacterclassese.
g.
[:space:]Benefit:Thenewengineisfasterthananyofthestandardlibraries.
MigrationfromYARAv1tov2Regexgreediness$catrule.
yararuletest{strings:$re=/[a-zA-Z]+/condition:$re}$catdata.
txtThisisatestMigrationfromYARAv1tov2Regexgreediness$yara-vyara1.
6(rev:129)$yara-srule.
yaradata.
txttestdata.
txt0x0:$re:ThisisatestMigrationfromYARAv1tov2Regexgreediness$yara-vyara1.
7(rev:167)$yara-srule.
yaradata.
txttestdata.
txt0x0:$re:Thisisatest0x1:$re:hisisatest0x2:$re:isisatest0x3:$re:sisatest0x4:$re:isatest0x5:$re:isatest0x6:$re:satest0x7:$re:atest0x8:$re:atest0x9:$re:test0xa:$re:test0xb:$re:est0xc:$re:stSolutionsAPDFwithalltheexercisesandsolutions(slideswitharedbar)willbeavailablefromMondayJune30,2014athttp://r.
forens.
is/first2014solOrsendmeanemailata.
schuster@yendor.
netThankyouforyourattention!
AndreasSchustera.
schuster@yendor.
nethttp://computer.
forensikblog.
de/
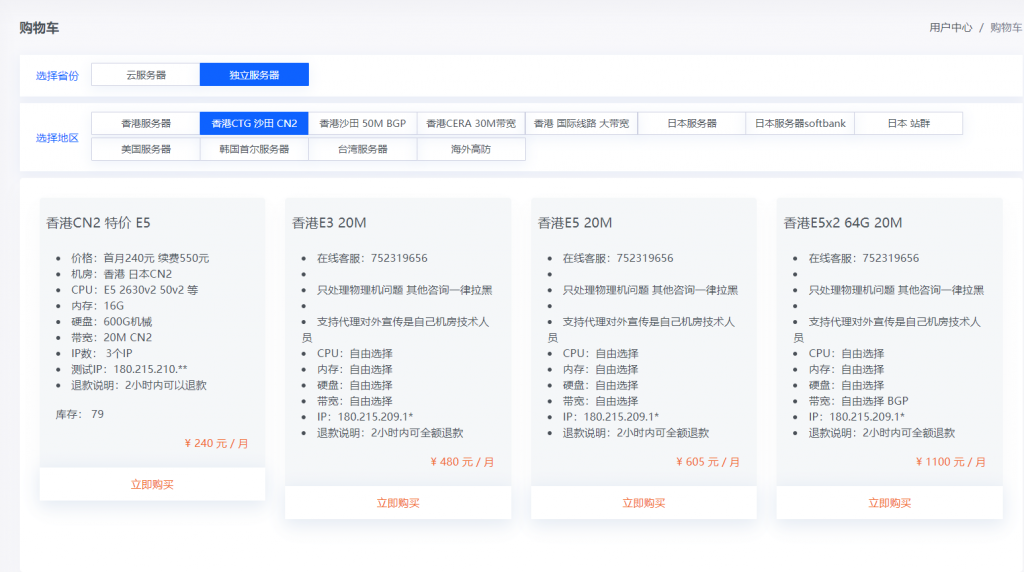
DiyVM:499元/月香港沙田服务器,L5630*2/16G内存/120G SSD硬盘/5M CN2线路
DiyVM是一家成立于2009年的国人主机商,提供的产品包括VPS主机、独立服务器租用等,产品数据中心包括中国香港、日本大阪和美国洛杉矶等,其中VPS主机基于XEN架构,支持异地备份与自定义镜像,VPS和独立服务器均可提供内网IP功能。商家VPS主机均2GB内存起步,三个地区机房可选,使用优惠码后每月69元起;独立服务器开设在香港沙田电信机房,CN2线路,自动化开通上架,最低499元/月起。下面以...
819云(240元)香港CN2 日本CN2 物理机 E5 16G 1T 20M 3IP
819云是我们的老熟人了,服务器一直都是稳定为主,老板人也很好,这次给大家带来了新活动,十分给力 香港CN2 日本CN2 物理机 E5 16G 1T 20M 3IP 240元0官方网站:https://www.819yun.com/ 特惠专员Q:442379204套餐介绍套餐CPU内存硬盘带宽IP价格香港CN2 (特价)E5 随机分配16G1T 机械20M3IP240元/月日本CN2 (...
弘速云香港VPSVPS线路有CN2+BGP、CN2 GIA,KVM虚拟化架构,裸金属月付564元
弘速云怎么样?弘速云是创建于2021年的品牌,运营该品牌的公司HOSU LIMITED(中文名称弘速科技有限公司)公司成立于2021年国内公司注册于2019年。HOSU LIMITED主要从事出售香港vps、美国VPS、香港独立服务器、香港站群服务器等,目前在售VPS线路有CN2+BGP、CN2 GIA,该公司旗下产品均采用KVM虚拟化架构。可联系商家代安装iso系统。点击进入:弘速云官方网站地址...

pastebin为你推荐
-
网罗设计计算机网络设计主要干什么小度商城小度分期靠谱吗?咏春大师被ko八极拳大师真的被咏春叶问打败了吗?八极咏春比优劣如何?谢谢.地图应用手机地图软件那么多,都不知道用哪个好了?留学生认证留学生服务中心认证内容和范围?比肩工场比肩接踵的意思rawtools闪迪32Gsd卡,无法格式化,显示只有30M,并且是raw格式。如何恢复?丑福晋八阿哥胤禩有几个福晋 都叫啥名儿呀www.zjs.com.cn怎么查询我的平安信用卡寄送情况www.ijinshan.com桌面上多了一个IE图标,打开后就链接到009dh.com这个网站,这个图标怎么删掉啊?