自己的怎样才能让别人查不到自己的ip地址(How to let others can not find their IP address)
怎样才能让别人查不到自己的ip地址How to let others can notfind their IP address
ARP principle: a machine A to send the message to the host B,will query the local ARP cache table, to find the B address ofthe IP corresponding to the MAC address, it will be datatransmission. If not found, broadcast A, a ARP request message(carrying the host A' s IP address Ia - physical address Pa) ,requesting the IP address of Ib host B, and answering thephysical address Pb. All hosts on the Internet, including theB, receive the ARP request, but only the host B recognizes itsown IP address and sends back a ARP response message to the Ahost. This includes the B address of the MAC, and the local ARPcache is updated after the A receives the B response. The datais then sent using this MAC address (with the MAC addressappended by the network card) . Therefore, the ARP table of thelocal cache is the basis for the local network flow, and thecache is dynamic.
The ARP protocol does not receive the ARP response only whenthe ARP request is sent. When the computer receives the ARPresponse packet, it updates the local ARP cache and stores theIP and MAC addresses in the ARP cache. Therefore, when a machinein the LAN B to send A ARP response a forgery, and if thisresponse is B to C posing as the IP address forgery, C, IP, andMAC address is fake, then when A receives the ARP response Bforged, will update the local the ARP cache, so in A it seemsC IP address has not changed, but it is not the original oneMAC address. Because the LAN network flow is not carried outaccording to the IP address, but is transmitted according tothe MAC address. So the forged MAC address was changed to a
nonexistent MAC address on A, which would cause the network tofail and cause A to fail to pass Ping through C! This is a simpleARP spoofing.
2. , the network law enforcement officer is using thisprinciple!
In the network to a law enforcement official, to restrict themachine online, just click the"card"menu"permissions, selectthe card number or click on the list of users in the card row,select" permission"from the menu in the dialog box to restrictthe user' s permissions. For an unregistered network card, youcan limit its on-line: as long as the set of all known users(Registration) , the network card default permissions toprohibit on-line, you can stop all unknown network card on-line.With these two functions, users can be restricted to theinternet. The principle is to pass the ARP spoofing to theattack computer, a false gateway IP address corresponding toMAC, so that it can not find the gateway' s real MAC address,so that it can prohibit its access to the internet.
3. , modify the MAC address, break the blockade of the networklaw enforcement off icer
According to the above analysis, it is not difficult to drawa conclusion that as long as the MAC address is modified, wecan cheat the scanning of the Internet law enforcement officersoas toachieve the goal of breaking through the blockade. Hereis how to modify the MAC address of the network card:In the run of the start menu, enter regedit, open the registry
editor, and expand the registry to: HKEY_LOCAL_
MACHINE/System/CurrentControl
Set/Control/Class/{4D36E972-E325-11CE-BFC1-08002BE10318} key, 000000010002 sub branch in DriverDesc in the searchkey (if you have more than one card, there are 00010002. . . . . .here is keeping on your card information, the DriverDesccontent is the card information description, such as my cardis Intel 210
41, based, Ethernet, Controller) here, suppose your networkcard is in the 0000 child key.
Add a string under the 0000 child key, named NetworkAddress.The key value is the modified MAC address, which requires 12consecutive 16 hexadecimal numbers. Then, in the NDI/paramsunder the "0000" sub key, a new subkey called NetworkAddressis added. Under the subkey, a string called default is added,and the key value is the modified MAC address.
Under the child key of the NetworkAddress, continue toestablish a string called ParamDesc, which acts as thespecified Network
Description of Address,
Its value is "MAC Address"". Then open the network neighbor"attribute", double-click the network cardwill finda"senior"setting, the existence of MAC Address under the new
"NetworkAddress" option, it is for you to join in the registry,then as long as the MAC address can be modified.
Close the registry, restart, and your network card address hasbeen changed. Open the property of the network neighbor anddouble-click the corresponding network card entry to find anadvanced setting item of MAC Address for modifying the MACaddress directly.
The MAC address is also called a physical address, a hardwareaddress, or a link address. It is written inside the hardwarewhen it is produced by the network device manufacturer. Theaddress and the network that has nothing to do with this addressboth hardware (such as cards, hubs, routers) access to thenetwork where it will have the same MAC address, MAC addresswill not be changed, can not be set by the user. The MAC addressis usually expressed as a decimal number between 16 and 12, thenumber of 16 m each of the 2 separated by a colon, such as:
08:00:20:0A:8C:6D is an MAC address, the first 6 hexadecimalnumber 16, 08:00:20 represents the network hardwaremanufacturer' s serial number, it is allocated by IEEE, and then3 hexadecimal number 16 0A:8C:6D represents a network productthe manufacturer made (such as card serial number) . Eachnetwork manufacturer must ensure that each Ethernet device itmanufactures has the same first three bytes and different threebytes later. This ensures that eachEthernet device in the worldhas a unique MAC address.
In addition, the principle of network law enforcement officeris to send a computer to the MAC address of the false gatewayIP address through ARP spoofing, so that it can not find the
real MAC address of the gateway. Therefore, as long as we modifythe mapping from IP to MAC, the ARP spoofing of the networkadministrator fails and breaks the restriction of breakingthrough it. You can Ping the gateway in advance and then usethe ARP-a command to get the MAC address of the gateway. Finally,you can map the IP address of the gateway and its MAC addresswith the ARP -s IP card MAC address command.
4. find the one that makes you unable to access the InternetAfter removing the network administrator' s blockade, we can useArpkiller' s "Sniffer killer" to scan the entire LAN IP section,and then f ind the "promiscuous" mode of the computer, you canfind each other. The specific method is: run Arpkiller (Figure
2) , and then click the "Sniffer monitoring tool", in the"Sniffer killer" window, enter the start and end of the testIP (Figure 3) , click "start testing" on it.
When the test is complete, if the corresponding IP is a greenicon, the IP is in normal mode, and if it is a red hat, the cardis in promiscuous mode. It' s our goal, that this guy is messingwith cyber law enforcement officials.
While scanning, I'm in promiscuous mode, and I can' t countmyself in it!
It' s up to you to deal with each other when you find him. Forexample, you can use the Internet law enforcement officer toblock the other party
- 自己的怎样才能让别人查不到自己的ip地址(How to let others can not find their IP address)相关文档
- 自己的怎样才能让别人查不到自己的IP地址
- 显示IP地址、主机名互查(测试命令详解)
- 粘贴ip地址查寻示范图
- ip查地址如何通过IP知道地址
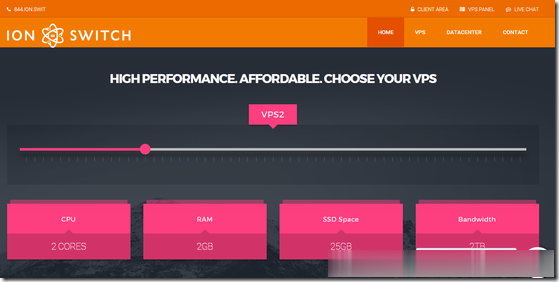
IonSwitch:$1.75/月KVM-1GB/10G SSD/1TB/爱达荷州
IonSwitch是一家2016年成立的国外VPS主机商,部落上一次分享的信息还停留在2019年,主机商提供基于KVM架构的VPS产品,数据中心之前在美国西雅图,目前是美国爱达荷州科德阿伦(美国西北部,西接华盛顿州和俄勒冈州),为新建的自营数据中心。商家针对新数据中心运行及4号独立日提供了一个5折优惠码,优惠后最低1GB内存套餐每月仅1.75美元起。下面列出部分套餐配置信息。CPU:1core内存...
90IDC-香港云主机,美国服务器,日本KVM高性能云主机,创建高性能CLOUD只需60秒即可开通使用!
官方网站:点击访问90IDC官方网站优惠码:云八五折优惠劵:90IDCHK85,仅适用于香港CLOUD主机含特惠型。活动方案:年付特惠服务器:CPU均为Intel Xeon两颗,纯CN2永不混线,让您的网站更快一步。香港大浦CN2測速網址: http://194.105.63.191美国三网CN2測速網址: http://154.7.13.95香港购买地址:https://www.90idc.ne...

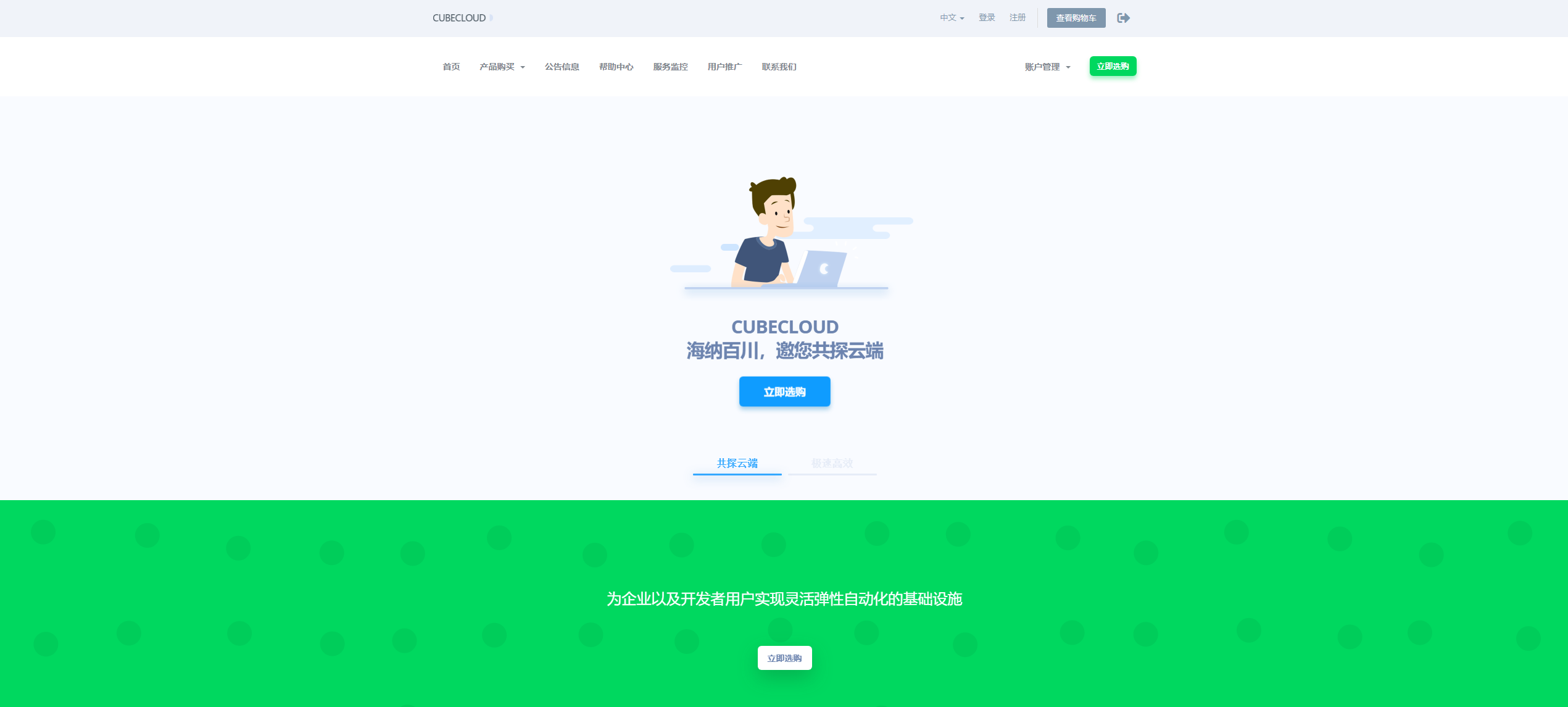
CUBECLOUD:香港服务器、洛杉矶服务器、全场88折,69元/月
CUBECLOUD(魔方云)成立于2016年,亚太互联网络信息中心(APNIC)会员,全线产品均为完全自营,专业数据灾备冗余,全部产品均为SSD阵列,精品网络CN2(GIA) CU(10099VIP)接入,与当今主流云计算解决方案保持同步,为企业以及开发者用户实现灵活弹性自动化的基础设施。【夏日特促】全场产品88折优惠码:Summer_2021时间:2021年8月1日 — 2021年8月8日香港C...
-
刷网站权重如何提高网站权重和流量51自学网站推荐一个好一点的自学网站,关于网站建设的。快速美白好方法有什么快速美白的好办法吗?镜像文件是什么什么是文件镜像?什么是镜像文件?iphone越狱后怎么恢复苹果手机越狱后怎么恢复开机滚动条怎么减少开机滚动条?ejb开发EJB是啥玩意了ios系统ios系统和安卓系统对比起来有什么优点和缺点?小米手柄小米手柄怎么用?qq等级表QQ等级列表